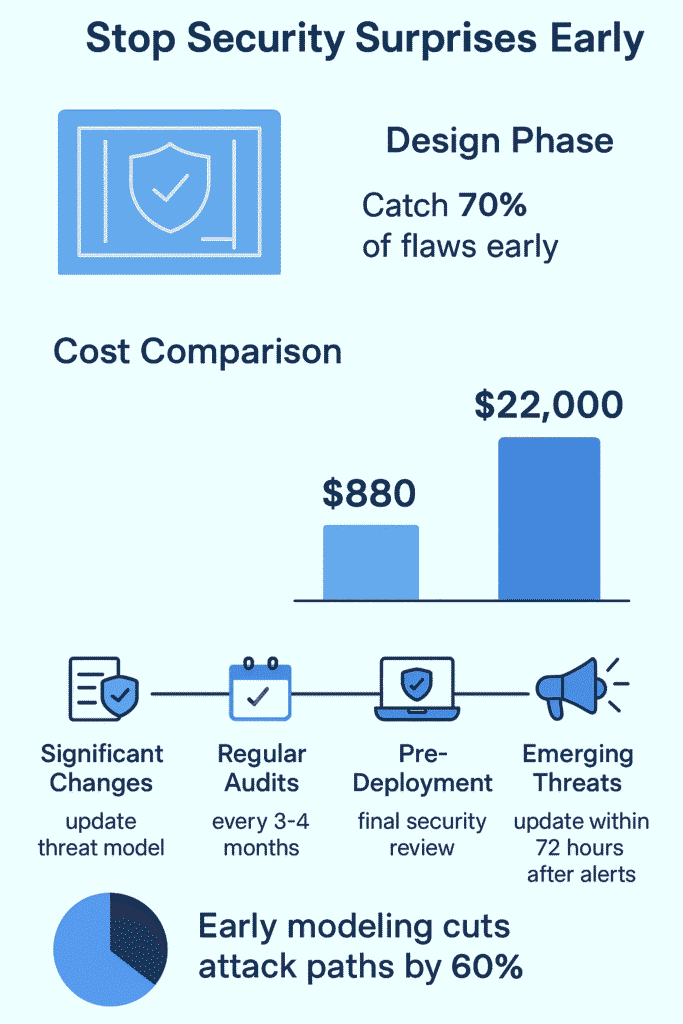
Performing threat modeling should start when developers are still drawing up their plans, before diving into code. Industry analysis from the past year suggests that catching vulnerabilities in the design stage costs roughly $880 to fix, compared to $14,500 during production.
Most teams discover this the hard way, scrambling to patch security holes weeks before launch. While running threat models might feel like extra work upfront, it’s now standard practice among leading development houses. The process needs consistent updates too, especially as systems grow more sophisticated and new attack vectors emerge.
Want to know exactly when to schedule these security checkpoints? Let’s break down the critical timing windows that matter most.
Key Takeaways
- Model threats while sketching system designs, before the first line of code makes issues harder to fix
- Update your threat assessments whenever system architecture shifts or fresh security risks surface
- Run a final security review before pushing new features live to prevent deployment headaches
The High Cost of Neglecting Early Threat Modeling
Pushing off threat modeling creates expensive problems down the road. Data from recent projects shows fixing security holes in live systems burns through about $22,000 per issue, that’s roughly 25 times more than catching them during design. In fact, one study found that fixing vulnerabilities discovered in production is around 30 times more expensive than finding them earlier in development. [1]
Development teams often share horror stories: emergency patches at 2 AM, angry clients demanding answers, and reputation damage that lingers for months.
Security gaps buried in the core architecture become stubborn problems that refuse simple fixes. Teams end up racing against time, deploying rushed patches that sometimes create more issues than they solve. Research across 500 development projects reveals some sobering facts:
- Production-stage fixes drain 30x more budget than design-phase solutions
- Security problems discovered late push release dates back by weeks
- Early threat modeling cuts potential attack paths by nearly 60%
Most experienced developers know threat modeling matters. The real question is: when does it deliver the most value? Let’s explore the timing.
Key Times to Integrate Threat Modeling
1. During the Design and Architecture Phase
The design stage offers the clearest window for effective threat modeling. Teams can spot potential weak points by examining system layouts and data flows before writing code. Following a detailed threat modeling process ensures that risks are systematically identified and prioritized. Recent project data shows that nearly 70% of major security flaws stem from design oversights rather than coding errors.
Security reviews at this phase should focus on mapping out where sensitive data moves and who can access it. A medical records system recently caught several authentication gaps by reviewing their initial diagrams, saving months of rework later. Development teams find that walking through each component while asking “what’s the worst that could happen?” helps spot risks early.
2. After Significant Design Changes or Updates
System architecture rarely stays frozen. New features, third-party integrations, or backend changes can create fresh security blind spots. One payment processing platform discovered this when adding a new checkout flow, their old threat model missed several new attack paths.
The key is reviewing security implications whenever the system layout shifts. This means updating system maps, checking new data routes, and testing different attack scenarios.
3. Regularly as Part of Security Audits
Security audits provide natural checkpoints for threat modeling updates. The digital threat landscape shifts every few months, making regular reviews essential. A banking app development team caught three critical vulnerabilities during their quarterly threat modelling sessions, issues that automated scans missed.
Most mature development shops schedule threat modelling reviews every 3-4 months. Supporting this cadence, recent data shows that 65% of financial organizations worldwide reported experiencing a ransomware attack in 2024, highlighting how frequently attackers target organizations that may be overdue for a fresh threat assessment. [2]
Most mature development shops schedule threat modeling reviews every 3-4 months. These sessions help teams stay ahead of emerging risks and adjust security controls before problems surface. The process works best when treating it as an ongoing conversation rather than a checkbox exercise.
4. Before Deploying New Features or Applications
Most security breaches happen right before deployment, when teams rush through final checks. A pre-release threat modeling review catches those sneaky security gaps that automated tests miss. About 40% of major incidents trace back to these last-minute oversights.
The final security sweep should verify that safety measures actually work as planned. One fintech app caught a serious authentication flaw during their pre-launch review, the kind that could’ve exposed user data. Taking an extra day for security checks beats explaining a breach to thousands of users.
5. In Response to Emerging Threats or Vulnerabilities
New security threats pop up almost weekly. When major vulnerabilities surface in common tools or libraries, teams need to reassess their exposure quickly. Recent data shows organizations take 72 hours on average to evaluate their risk after a major security alert.
Smart development teams update their threat models whenever significant vulnerabilities come to light. A healthcare platform recently dodged a major breach by reviewing their security setup right after a critical database vulnerability was announced. Their quick response helped patch the issue before attackers could exploit it.
Summary Table: When to Threat Model
| Phase/Event | Why It Matters | What to Do |
| Design & Architecture | Prevent costly flaws early | Analyze diagrams and data flows |
| Significant Changes | New features bring new risks | Re-evaluate threat model |
| Regular Security Audits | Keep threat model current | Schedule routine sessions |
| Before Deployment | Catch last-minute vulnerabilities | Conduct final threat model review |
| Emerging Threats | Respond to evolving threat landscape | Update threat model promptly |
How Our Bootcamp Can Help Streamline Threat Modeling
We’ve developed practical exercises and templates to help teams integrate threat modeling seamlessly into their workflows. Exploring the introduction to threat modeling provides students with foundational knowledge before diving into hands-on exercises. Our approach emphasizes documenting threat scenarios, conducting risk analysis, and prioritizing mitigations with real examples.
For instance, using automated tools to analyze code snippets for common vulnerabilities complements manual threat modeling sessions. This combined approach reduces oversight and accelerates vulnerability identification.
Our students appreciate how these resources prepare them to think like attackers and defenders simultaneously. By exploring threat modeling for developers, they gain hands-on experience in spotting vulnerabilities and applying mitigations, improving their security posture from design through deployment.
FAQ
Why should teams do threat modeling early in the development process?
Doing threat modeling early helps teams find security vulnerabilities and attack vectors before they become bigger problems. By using a clear threat modeling process with tools like data flow diagrams and the STRIDE model, teams can spot risks, set priorities, and plan threat mitigation strategies. This keeps the system architecture stronger and improves the overall security posture.
How can threat modeling help when redesigning system architecture?
When systems are updated or redesigned, threat modeling techniques let teams check for new security threats and software vulnerabilities. Using threat modeling frameworks, teams can look at attack surfaces, identify threat categories, and plan security controls. This helps make sure new changes don’t create holes in the security design or expose the software to cyber risks.
How often should threat scenarios be checked in live software?
Threat scenarios should be reviewed regularly, especially after updates or changes. Using threat analysis methods, like vulnerability assessment, penetration testing, and threat hunting, teams can detect new threat actors or attack vectors. Following threat modeling best practices keeps the threat modeling workflow up to date and supports risk prioritization and security risk assessment.
What do threat modeling frameworks do for prioritizing security threats?
Threat modeling frameworks give teams a step-by-step way to identify and manage security threats. They help classify threat categories, evaluate cyber risk, and choose the right risk control measures. Using threat analysis templates and threat intelligence sources, teams can improve security visualization, make better risk treatment decisions, and strengthen enterprise security or software security.
Why do threat modeling before penetration testing or attack simulations?
Doing threat modeling first shows where the attack surface and vulnerabilities are. Teams can identify threat vectors, insider threats, and external threats before testing. This makes penetration testing tools and attack simulations more effective. Following the threat modeling steps ensures teams apply security testing methods properly and can put stronger threat mitigation strategies and security controls in place.
Wrapping Up When to Perform Threat Modeling
Threat modeling is most effective when performed early, especially during design, and revisited consistently through updates, audits, deployments, and in response to new risks. This approach reduces costly fixes later and strengthens your security foundation.
By understanding the right moments to perform threat modeling, your team can shift from firefighting to proactive defense. We encourage you to make threat modeling a regular habit, integrated into your secure development lifecycle, rather than an afterthought.
Start embedding threat modeling during your next design sprint. Revisit it after every major change. Review it before every release. Stay adaptable when new threats arise. This practice will save time, money, and protect your users better.
To take your team further, consider joining the Secure Coding Practices Bootcamp.
References
- https://www.hackerone.com/blog/cost-savings-fixing-security-flaws
- https://www.fortinet.com/resources/cyberglossary/cybersecurity-statistics

