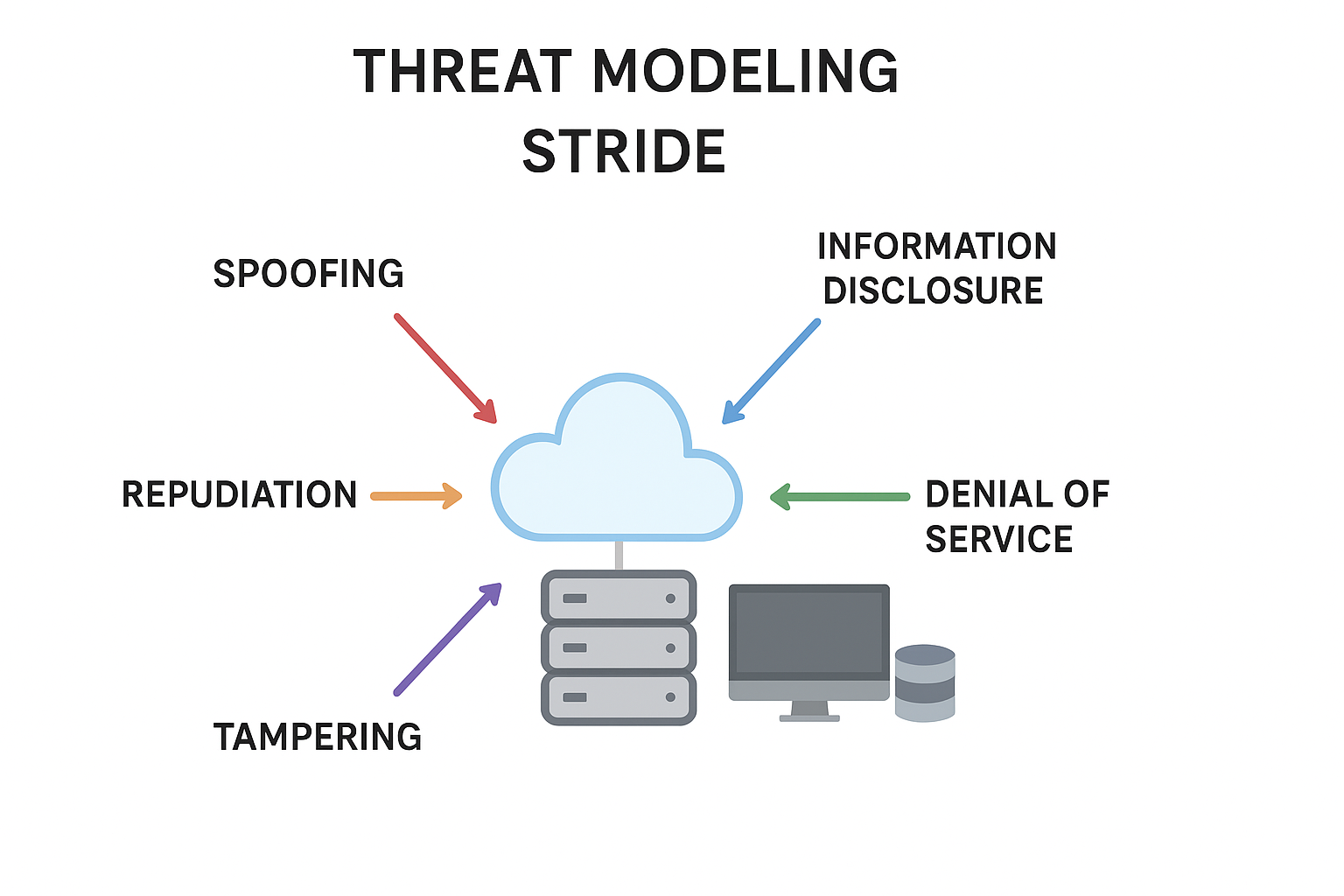
Software security boils down to one key method: STRIDE threat modeling. Our training team has found it’s the single best way to catch potential risks before they snowball into major issues. Six main categories, from plain old spoofing to dangerous privilege elevations, make up the STRIDE framework that developers rely on.
Every day, we see how mixing STRIDE analysis with solid security practices helps teams build better defenses, it’s what we teach in our bootcamps. Check out the real cases and practical fixes we’ve gathered from years of helping developers lock down their code.
Key Takeaways
- STRIDE breaks down cybersecurity threats into six categories for clear, focused threat assessment.
- Implementing mitigation strategies early, especially through secure coding, significantly reduces risks.
- Practical examples like online banking show how STRIDE guides defenses such as multi-factor authentication and cryptography.
Why Threat Modeling Matters
Threat modeling is like the first step in building a house; you want to know where the cracks might appear before laying the foundation. Cybersecurity threats can range from data theft to system downtime, and ignoring them is asking for trouble. Understanding basic threat modeling techniques early helps teams establish a strong foundation in secure coding and overall risk prioritization.
Consider threat modeling as your security weather forecast. You wouldn’t set out on a trip without checking the storm warnings. Likewise, assessing threats ahead means you stay prepared.
- Proactive threat identification helps avoid data breaches and service disruptions.
- Early mitigation reduces the attack surface and strengthens your security posture.
- It aligns your security efforts with compliance and risk management goals.
Understanding these points helps us realize why STRIDE is a valuable framework. Recent data shows that almost 70 % of applications contain at least one vulnerability after five years in production, proving how unaddressed flaws tend to pile up over time when secure coding and proactive threat modeling aren’t applied early. (1)
Our experience shows that combining STRIDE threat modeling with diligent secure coding practices is crucial, ensures continuous assessment and mitigation of vulnerabilities, protecting your software from evolving threats.
What is STRIDE?
STRIDE is a threat modeling framework created by Microsoft to systematically identify security weaknesses in software. The name stands for six types of threats: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
We think of STRIDE as a tool that forces you to think from an attacker’s viewpoint but with the goal of building better defenses. This approach encourages a structured look at software components and how they might be attacked.
STRIDE is valuable because it provides a clear checklist of threat categories, making threat assessment less abstract and more actionable. It’s especially effective when integrated with secure coding practices, which we always prioritize to reinforce defenses from the start.
Understanding the STRIDE Categories
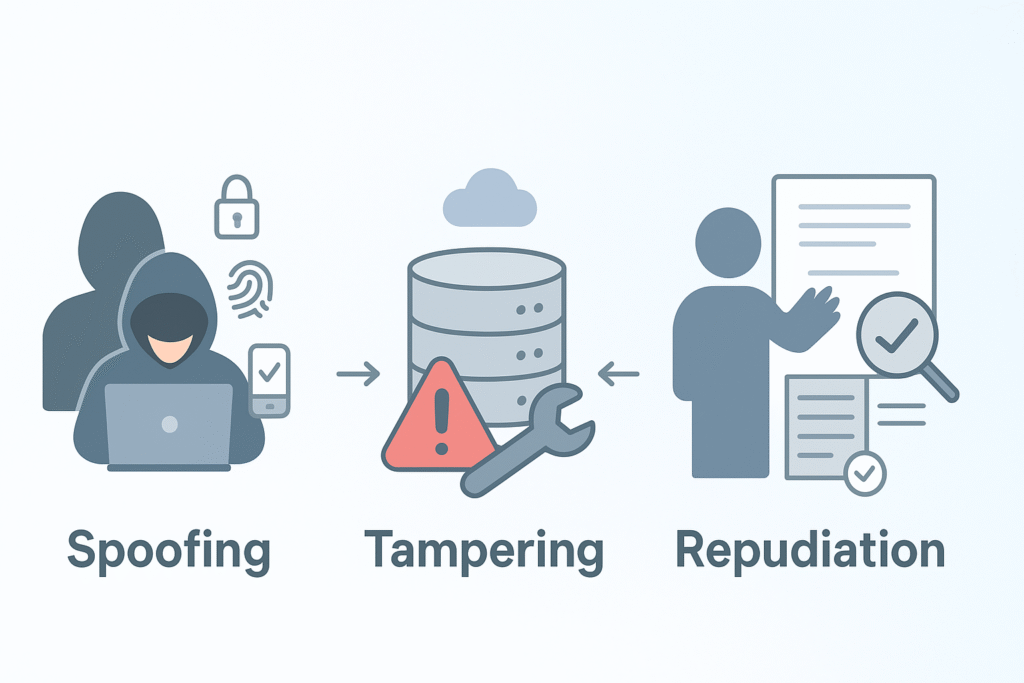
Spoofing
Spoofing involves someone pretending to be another user or system to gain unauthorized access. Imagine an attacker stealing credentials and logging in as a legitimate user.
When we handle authentication, we never rely on passwords alone. Multi-factor authentication is a must. It’s like having a second lock on the door, something you know and something you have.
- Spoofing threats highlight the need for strong identity verification.
- Implementing multi-factor authentication reduces the risk.
- Secure coding helps ensure authentication mechanisms are resistant to bypass.
Tampering
Tampering is the unauthorized modification of data or code. An attacker might change a database record or alter code during transmission.
We treat tampering like someone messing with the locks or the wiring in a building. To counter this, we use cryptographic signatures to protect data integrity, ensuring that any unauthorized changes are detectable.
- Tampering threatens data integrity and trustworthiness.
- Cryptography provides a way to verify data hasn’t been altered.
- Secure coding prevents injection vulnerabilities that could allow tampering.
Repudiation
Repudiation happens when users deny their actions because no evidence or logs exist to prove otherwise. For instance, a user might deny making a transaction.
Logging and auditing are crucial here. We maintain detailed records of user actions. Without these, it’s like trying to remember who ate the last cookie, impossible to prove.
- Repudiation risks undermine accountability.
- Audit logs provide non-repudiation by recording actions.
- Secure coding ensures logs are tamper-resistant and comprehensive.
Information Disclosure
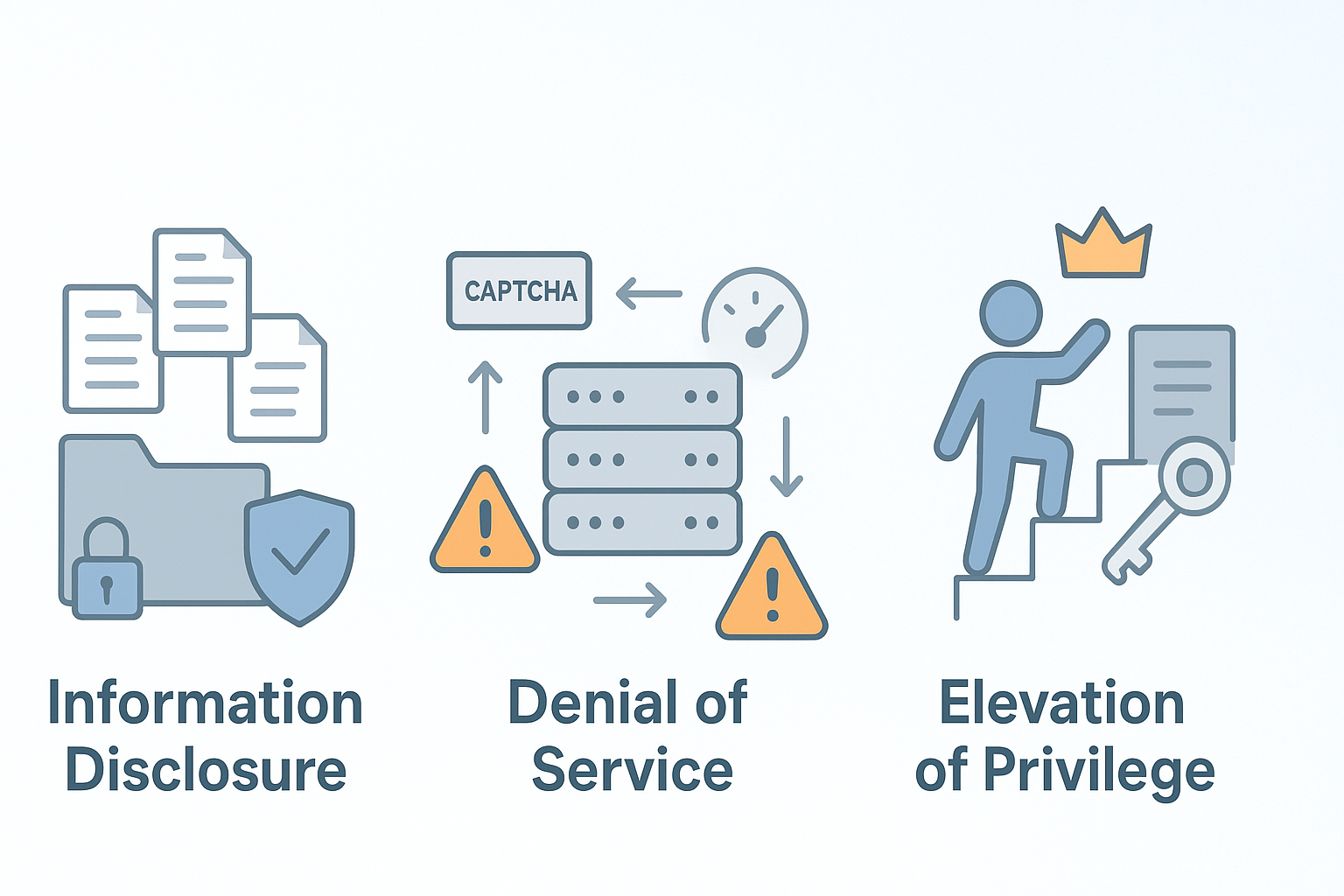
Information disclosure is exposing sensitive data to unauthorized parties. This could be a leak of user passwords or personal details.
Encryption is our frontline defense. We encrypt sensitive data both at rest and in transit to maintain confidentiality. Leaving data unprotected is like leaving your diary open for anyone to read.
- Protecting data confidentiality is essential.
- Encryption ensures sensitive information remains private.
- Secure coding guards against leaks via secure input validation and output encoding.
Denial of Service (DoS)
Denial of Service attacks overwhelm resources so legitimate users can’t access them. Picture a traffic jam on the internet, blocking real visitors.
We’ve seen login pages flooded with fake attempts. Rate limiting and CAPTCHA verification help us keep the traffic manageable.
- DoS attacks threaten availability.
- Rate limiting and CAPTCHA reduce attack impact.
- Secure coding avoids resource exhaustion by efficient code design.
Elevation of Privilege
Elevation of privilege occurs when a user gains higher access than authorized. For example, a regular user exploiting a bug to become an admin.
We apply the principle of least privilege rigorously. Users only get access they absolutely need. Secure coding practices help by eliminating vulnerabilities that allow privilege escalation.
- Preventing unauthorized privilege increases security.
- Least privilege limits damage if an account is compromised.
- Code reviews and testing catch privilege escalation paths.
Applying STRIDE: A Step-by-Step Guide
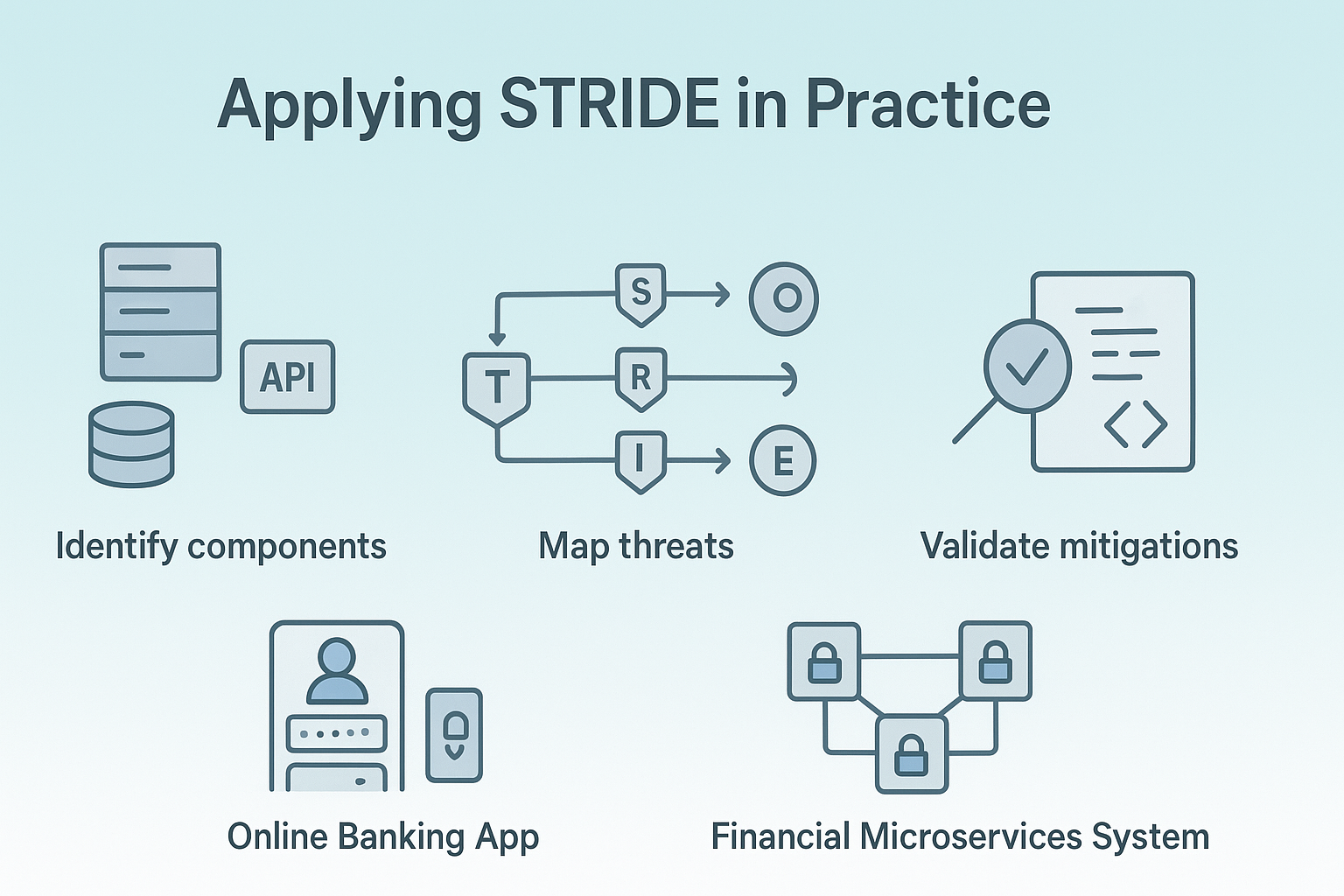
The process of applying STRIDE is like conducting a thorough security audit. Here’s how we approach it:
- Identify system components like databases, APIs, and authentication services.
- Map threats to these components using threat modeling for developers to visualize data flows and system boundaries.
- Develop mitigation strategies based on threat categories.
- Validate mitigations through security testing and code reviews.
This systematic approach helps us cover all bases and reduces security vulnerabilities early. The need for this kind of structured assessment keeps growing , in the first half of 2025 alone, 23,667 new CVEs were published, marking a 16 % increase from 2024. Attackers actively exploited 161 of them, and 42 % already had public proof-of-concepts, showing how quickly vulnerabilities are weaponized once discovered. (2)
STRIDE Threat Modeling: Real-World Examples
Credit: Computing & Coding
Online Banking Application
In one project, we examined an online banking app to identify STRIDE threats:
- Spoofing: Attackers might try stolen credentials.
- We enforced multi-factor authentication to verify users.
- Tampering: Modifying transaction amounts was a concern.
- Cryptographic signatures protected transaction data.
- Denial of Service: Flooding login attempts could block users.
- Rate limiting and CAPTCHA kept the system responsive.
These examples showed us the practical side of STRIDE and how secure coding practices supported each defense layer.
Financial Microservices System
In a microservices setup, identity spoofing between services was a major threat. Implementing mutual TLS helped us authenticate services reliably.
This scenario also taught us about the importance of secure communication and encryption to protect data flows.
STRIDE Summary Table
| Category | Definition | Threat Example | Mitigation Strategy |
| Spoofing | Unauthorized impersonation | Stolen credentials | Multi-factor authentication |
| Tampering | Unauthorized modification of data/code | Altering database records | Cryptographic signatures |
| Repudiation | Ability to deny actions | User denying a transaction | Audit logs |
| Information Disclosure | Exposing sensitive information | Leaking user passwords | Encryption |
| Denial of Service | Making resources unavailable | Flooding login attempts | Rate limiting, CAPTCHA |
| Elevation of Privilege | Gaining higher access rights than authorized | Normal user becoming admin | Principle of least privilege |
STRIDE Implementation Checklist
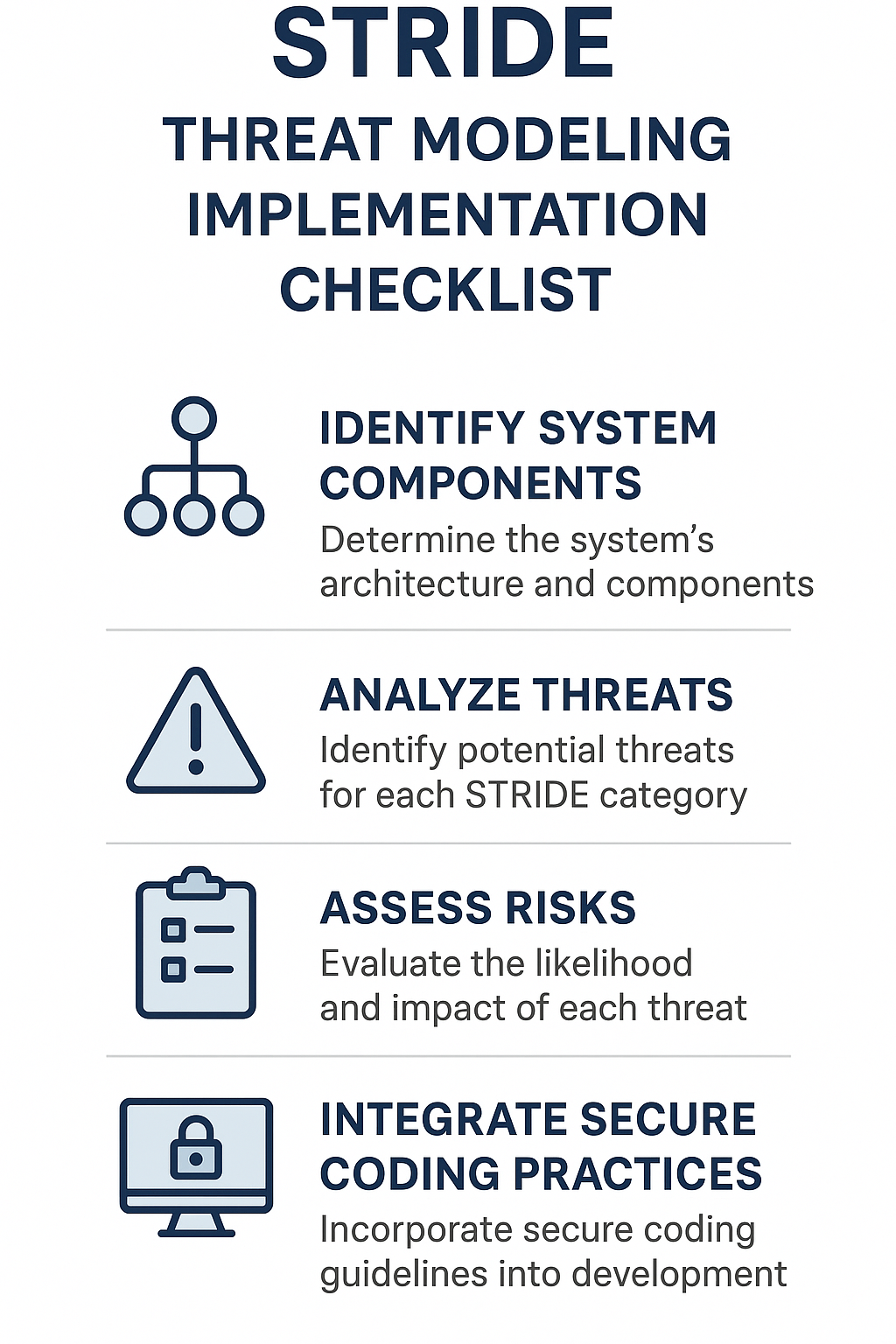
Before wrapping up, here’s a handy checklist for applying STRIDE effectively:
- Identify critical system components and data flows.
- Analyze each component against STRIDE threat categories.
- Prioritize threats based on risk and impact.
- Integrate secure coding practices for threat mitigation.
- Use logging and auditing to cover repudiation.
- Conduct penetration testing and security assessments.
- Update threat models regularly as the system evolves.
FAQ
What is STRIDE threat modeling, and why is it important?
STRIDE threat modeling helps teams spot and reduce cybersecurity threats early. It breaks down risks into spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege. By using this framework, developers can strengthen software security, improve threat assessment, and design systems that resist attack vectors before they cause damage.
How does STRIDE address software security vulnerabilities?
Each STRIDE category points to different security vulnerabilities. Spoofing and tampering show flaws in authentication and data integrity, while repudiation and information disclosure highlight weak logging and encryption. Denial of service and elevation of privilege focus on access control and system availability. Together, they guide secure design and better risk management decisions.
What’s an example of STRIDE in real-world applications?
In a banking app, spoofing might mean identity spoofing through phishing, while tampering could involve data tampering during transactions. Repudiation risks appear when there’s no auditing or non-repudiation control. Information disclosure could expose sensitive data, and denial-of-service attacks might block access. STRIDE helps prevent these software threats through secure coding and testing.
How does STRIDE fit within a broader cybersecurity framework?
STRIDE works well with risk analysis, secure software development lifecycle, and penetration testing. It complements other security controls like firewalls, multi-factor authentication, and secure communication. By aligning STRIDE with a cybersecurity framework, organizations strengthen threat mitigation, improve threat detection, and maintain a stronger overall security posture.
How can teams use STRIDE to improve ongoing threat mitigation?
Teams can integrate STRIDE during design reviews, security testing, and vulnerability analysis. Mapping threat scenarios to security policies and controls supports continuous threat identification and risk reduction. When combined with security awareness and incident response, STRIDE builds a culture of secure access, better logging, and smarter cybersecurity strategy.
Conclusion
Our experience shows that STRIDE threat modeling combined with diligent secure coding practices is the best way to build resilient software. It’s not just about ticking boxes; it’s about thinking like an attacker to better protect your users and data. By embedding security into the development lifecycle and continuously assessing threats, you reduce vulnerabilities and improve your cybersecurity posture.
If you haven’t started using STRIDE or secure coding methods yet, now is the time. Protecting your software means protecting your reputation and your users. Remember, threats evolve, but so can your defenses, one secure line of code at a time.
Join the Secure Coding Practices Bootcamp to gain hands-on experience in building secure applications from day one.
References
- https://www.getastra.com/blog/security-audit/cyber-security-vulnerability-statistics/
- https://www.recordedfuture.com/research/h1-2025-malware-and-vulnerability-trends

