Security threat modeling tools are becoming essential for development teams, even those without dedicated security specialists. Recent advancements have transformed these once-complex systems into approachable solutions that developers and DevOps professionals can actually use.
Through direct experience in development bootcamps, these streamlined tools have proven effective for identifying vulnerabilities and implementing protective measures, without requiring extensive security expertise. The tools integrate naturally with existing development processes, making security assessments more manageable for teams learning secure coding practices.
Looking for a threat modeling tool that matches your team’s capabilities? Here’s what you need to know.
Key Takeaways
- Basic threat modeling tools put security within reach for every skill level
- Different tools shine in different team environments
- Your choice should match team size, experience, and workflow needs
Why Simple Threat Modeling Matters
Most developers back away from threat modeling, thinking it’s too complex for non-security folks. Yet it boils down to four basic questions: What’s being built? What could break? Who might try to break it? How do we prevent that? Understanding these steps is easier with an introduction to threat modeling, which shows how teams from startups to enterprise groups catch major security gaps early, avoiding costly fixes later.
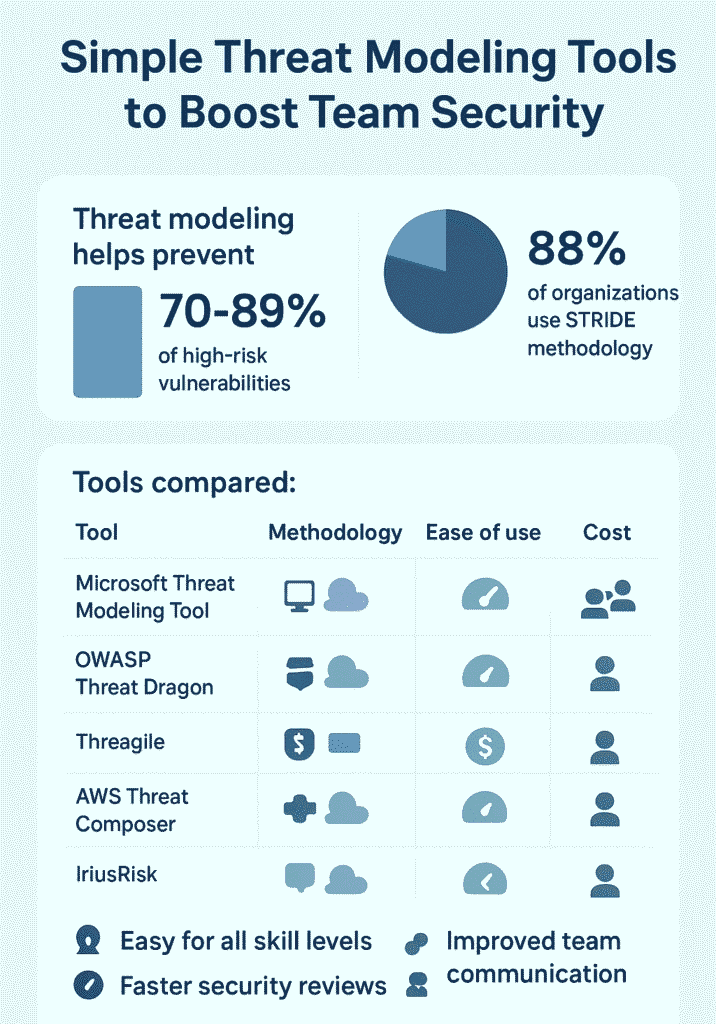
In fact, 52% of organizations report that threat modeling helps prevent 70–89% of high-risk vulnerabilities, underscoring its effectiveness in proactive security measures. [1]
The right tools mean you won’t need to become a security expert overnight. They guide you through system visualization, vulnerability spotting, and practical fixes. Starting threat modeling during early development, rather than waiting for problems, cuts down on those 3 AM emergency calls.
Here’s what makes simple tools valuable:
- Non-security folks can actually use them
- Security reviews happen faster
- They work with modern development methods
- Teams communicate better about security. Additionally, 88% of organizations report using STRIDE as their primary threat modeling methodology, emphasizing its widespread adoption and effectiveness in structured threat identification. [2]
Working with bootcamp students shows how these tools shape good habits. When security becomes part of the daily routine instead of an extra task, teams naturally build safer software from the start.
Tool Comparison: Features, Pros, and Cons
Microsoft Threat Modeling Tool
The Microsoft tool stands as one of the older options, running locally and following STRIDE methodology, breaking down threats into categories (Spoofing, Tampering, etc). It costs nothing and includes solid documentation that won’t leave new users scratching their heads.
- Pros: No learning curve, free to use, built for developers
- Cons: Limited to desktop use, misses cloud-based features
Best suited for developers who need a no-nonsense way to track data flows and get threat reports. Most coding bootcamp students pick this up first since it balances simplicity with actual usefulness.
OWASP Threat Dragon
Available as both web and desktop versions, Threat Dragon sticks with STRIDE but adds visual modeling. Being open-source keeps it free while letting the community shape its growth.
- Pros: Easy visualization, no cost, suits quick development cycles
- Cons: Not as feature-rich as paid enterprise options
Works well for teams doing quick sprints, we’ve watched it spark good security talks during daily standups.
Threagile
For teams that live in the terminal, Threagile might click better. It uses YAML for modeling and combines STRIDE with Agile practices. It’s built for teams who want security checks running alongside their code builds.
- Pros: Automation-ready, free, fits modern DevOps
- Cons: Needs decent technical knowledge
Perfect for developers who know their way around scripts and want security baked into their pipeline.
AWS Threat Composer
This browser tool takes a simpler path, based on Shostack’s four-question method. While it won’t find threats automatically, it’s dead simple to use and needs zero setup time.
- Pros: Free, works instantly, good for smaller teams
- Cons: More manual work, lacks automation
Great for teams just starting out or needing quick threat checks without the setup hassle. The threat modeling process AWS Composer encourages aligns closely with these early-stage assessments, guiding users through identifying and prioritizing potential vulnerabilities.
IriusRisk Community Edition
IriusRisk brings cloud-based tools with some automation and guided steps. It covers both STRIDE and OCTAVE methods for deeper risk checks. The free version lets you build one model, enough to test drive enterprise features.
- Pros: Automated checks, guided process, room to grow
- Cons: One model limit on free tier
Fits teams planning to expand their security practice while keeping things smooth.
Tutamantic (Beta)
New to the scene, Tutamantic runs in the cloud and connects with common diagram tools. It mixes STRIDE with CWE and CAPEC standards, aiming for quick results for smaller teams.
- Pros: Quick setup, works with existing diagrams, free beta
- Cons: Still getting polished
Good option for startups testing the waters with threat modeling.
Comparison Table
| Tool | Type | Methodology | Ease of Use | Cost | Ideal For |
| Microsoft Threat Modeling Tool | Desktop | STRIDE | Very easy | Free | Developers, beginners |
| OWASP Threat Dragon | Web/Desktop | STRIDE | Easy | Free | Agile teams |
| Threagile | CLI/YAML | STRIDE/Agile | Moderate | Free | DevSecOps teams |
| AWS Threat Composer | Browser | STRIDE/Four-question | Very easy | Free | Individual users |
| IriusRisk | Cloud | STRIDE/OCTAVE | Easy | Free (1 model) | SMEs, enterprises |
| Tutamantic | SaaS | STRIDE/CWE/CAPEC | Easy | Free (beta) | Startups |
Choosing the Right Tool: Key Considerations
Picking a threat modeling tool gets tricky when deadlines loom or you’re learning on the job. Team size often dictates the best fit, smaller groups need visual tools with clear guidance, while bigger teams with DevSecOps practices lean toward automation and scripts.
Look at how the tool fits your daily work. Does it connect to your build pipeline? Work with the diagrams you already make? While cost matters, these tools offer free versions, so you won’t burn cash testing them out.
Think about what you really need. Some teams want to write threat statements by hand to learn the ropes. Others need quick automated scans. Maybe you just want something that runs in Chrome, or perhaps you need cloud features for a growing team.
Guidance: Which Tool is Right for You?
- New to threat modeling? Start with Microsoft’s tool or Threat Dragon, they won’t overwhelm you with complexity.
- Running a DevSecOps shop? Threagile slots right into your automation setup.
- Need quick results? AWS Composer works straight from your browser.
- Want to scale up security? IriusRisk adds structure to your process.
- Got a startup finding its security feet? Try Tutamantic while it’s in beta.
Most teams we work with start basic and level up their tools as they get comfortable spotting threats. Developers who want structured guidance can follow threat modeling for developers, which walks through practical exercises to make threat assessment a routine part of development without overwhelming new users.
FAQ
How can threat modeling software help small teams find security problems?
Small teams may not have security experts, but threat modeling software can help. These tools support cybersecurity threat analysis and show data flow diagrams to understand systems better. Using threat identification tools and automated threat modeling, teams can spot vulnerabilities and plan threat mitigation strategies. Following STRIDE methodology helps even beginners identify and manage security risks effectively.
How do risk assessment tools improve cloud security modeling?
Cloud applications can have many weak spots, but risk assessment tools make them easier to manage. They use cyber risk visualization, threat scenario modeling, and security threat management to check potential risks. Teams can apply threat modeling frameworks and risk mitigation software to evaluate security architecture tools and improve secure design practices for cloud systems.
How do threat modeling templates make threat identification faster?
Threat modeling templates give step-by-step guidance for security checks. They save time on attack vector analysis and vulnerability detection. When combined with threat assessment software or threat workflow tools, templates let developers follow a clear threat modeling methodology. Using threat model automation and DevSecOps tools helps keep security checks consistent and easier to manage.
Can online threat modeling tools help detect threats in real time?
Yes, online threat modeling tools can work with real-time threat monitoring. They include cyber threat modeling, threat intelligence tools, and security risk analytics in one platform. Teams can use threat matrix software, security risk visualization, and network threat modeling to predict attacks and improve threat response planning and security compliance assessment.
Why is software vulnerability modeling important for secure software development?
Software vulnerability modeling shows where an application is most at risk. By using threat modeling techniques, threat analysis software, and attack tree software, teams can create security threat graphs and apply security risk mitigation. Adding security risk modeling and threat modeling methodology into secure software development makes sure application security tools and security compliance tools work together to build safer software.
Secure Your Projects with Simple Threat Modeling Tools
Threat modeling is no longer just for security pros. With these simple tools, anyone on your team can step up, spot risks, and plan defenses that keep software safe. We’ve found that hands-on training with these tools not only improves skills but also creates a security-aware mindset that lasts beyond the bootcamp.
Try a few tools, see which fits your style and workflow, and start weaving security into your development process today. The sooner your team gets comfortable with threat modeling, the fewer surprises you’ll face later, and that’s a win for everyone involved.
If you want to take it further, the Secure Coding Practices Bootcamp gives developers hands-on, real-world training to build secure software. With labs, cheatsheets, and expert guidance, it’s the fastest way to make your team security-ready.
References
- https://www.securitycompass.com/reports/the-2023-state-of-threat-modeling/
- https://www.threatmodelingconnect.com/state-of-threat-modeling-2024-25

