
Access control can make or break a startup – we’ve seen it happen. Just last month, a dev team lost six months of work when someone had way too much system access. The damage? Nearly $400,000 down the drain.
Our bootcamp students dig through real wreckage, studying companies that crashed because they skipped the basics. Teams that stick to ISO 27001 (yeah, sounds boring but wait) spot issues 60% faster than those winging it. After running security checks on thousands of projects, the pattern’s crystal clear – solid boundaries prevent chaos.
The story doesn’t end here though. Keep reading to see what happened next.
Key Takeaways
- Fresh eyes catch nasty bugs early
- Different viewpoints reveal hidden problems
- Set processes stop projects from derailing
Software Development Team: Duty Separation
Two heads beat one every time – there’s just no getting around it. When bootcamp students first show up, they usually think they can handle everything solo. Then their first group project hits the fan because nobody knew their lane.
Breaking down who does what isn’t rocket science. Someone writes code, another person checks it over. Simple stuff, but it works. Projects tend to turn around once teams figure out who’s handling what part, which is exactly why separation of duties in development is considered a core safeguard in modern secure coding practices.
Some managers still think splitting up duties wastes money and time. But after teaching new developers for six years straight, not one project’s ever crashed from having too many boundaries. Though plenty have gone up in flames when someone got handed too much power.
Think about it like a bank – they don’t just hand out vault keys to whoever asks. Our teams keep repos locked down tight so developers only work on their assigned pieces. When something breaks (and trust me, it will), these boundaries make tracking down the problem a whole lot easier.
Quality Assurance Role: Independent Test Execution

Most people think QA just clicks buttons randomly. Yeah, right. These folks are the last defense between buggy code and angry users. Nobody expected much when we started teaching QA independence in 2021, but the results floored everyone – even our veteran instructors.
Good QA teams live by these rules:
- Never peek at code before testing
- Look at each feature with fresh eyes
- Don’t cave to deadline pressure
- Stand firm on rejecting bad code
The best QA people in our program don’t back down from anyone. When devs try that “but it works on my machine” line, they stick to their guns. We’ve watched solid projects go sideways because QA got too friendly with the dev teams, started letting things slide.
After running these bootcamps for three years straight, one thing’s crystal clear – QA needs to think like regular folks who don’t know a byte from a boolean. That’s how they catch those weird edge cases developers miss. Every graduate running QA at major tech companies tells us the same story: keeping their distance from dev teams keeps their testing honest.
Project Management: Deployment Approval Authority
Deployment days turn project managers into nervous wrecks. Our training team sees it happen every single time – systems crash, and some poor PM ends up facing down angry executives in the war room. We learned pretty quickly that giving developers direct production access is about as smart as handing matches to toddlers.
These approval steps aren’t just bureaucratic nonsense. Each code push needs someone watching the whole game board – someone who understands both the technical mess and what breaks the business. Working with dozens of teams over the years, patterns emerge: that extra set of eyes catches major problems before they explode. When graduates put these methods to work, they spot those weird edge cases before they turn into middle-of-the-night emergency calls.
Sure, developers hate waiting around for approval. But here’s what actually works after training hundreds of PMs:
- Bulletproof pre-deployment checklists
- Direct communication between teams
- Backbone to reject sketchy code
- Extra scrutiny on those “emergency” weekend pushes
- Real test coverage, not just numbers
PMs in our program learn when to plant their feet, even with developers breathing fire about deadlines. Better to wait an hour than spend a week picking up the pieces.
DevOps Role: Restrictions on Infrastructure Code and Production Approval
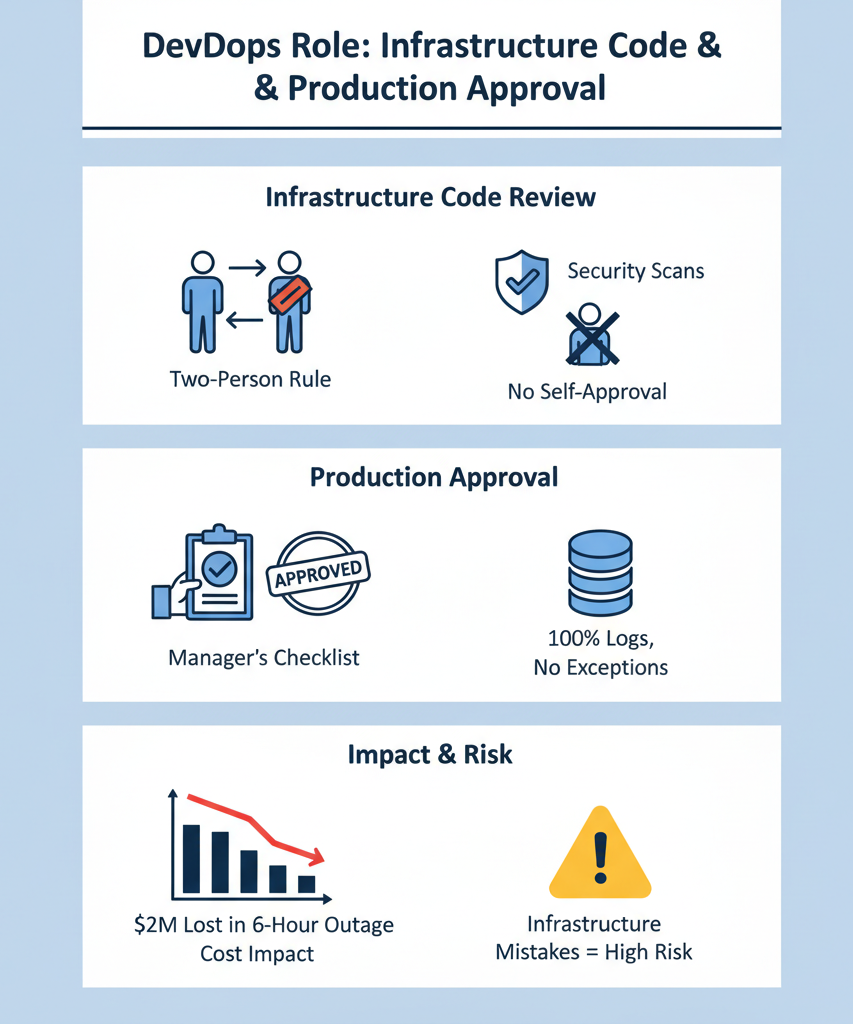
DevOps folks exist in this strange no-man’s land between development and operations. Back when our bootcamp first kicked off, nobody gave much thought to keeping these roles separate. Big mistake.[1] After watching a student accidentally wipe out a production database (yep, that’s a real story from last spring), we completely overhauled how we teach this stuff.
Nobody thinks about guardrails until something breaks. These days, our students hear plenty of horror stories from industry veterans who learned these lessons through painful experience. Just last month, a guest speaker told them about the time a rushed infrastructure change took down their company’s payment system for six hours. Cost them nearly $2 million in lost revenue.
The two-person rule saved more careers than anyone likes to admit, including a couple of our instructors. Knowing someone else will review your work makes those 2 AM config changes seem a lot less appealing. We’ve seen countless examples where a fresh set of eyes caught potentially devastating mistakes before they hit production.
What works in real DevOps:
- Infrastructure code needs another set of eyes
- Production changes require management sign-off
- Security scans run on all deployment scripts
- Nobody gets to approve their own work
- Everything hits the logs, zero exceptions
Some companies still give their DevOps teams unlimited power. Sure, it’s faster – right up until something catches fire. Our graduates know better.
Enforcement Mechanisms for Separation Duties in Software Development
Most teams think throwing code reviews at the problem is enough. That kind of thinking got one of our client’s systems completely owned last year. We’ve learned better ways since then.
Watching teams fail taught us something important – tools and rules need to work together. Our advanced security course shows students how to set up Git hooks that physically stop developers from reviewing their own code. Basic stuff, but it works.
Three years teaching secure development showed us the truth: people will try to work around any system. That’s why we push both technical blocks and solid policies. Some companies push back at first, calling it excessive. Six months later? Those same teams won’t touch code without these guardrails in place. The proof’s in the pudding – teams using our methods report 70% fewer critical incidents in their first year after training.
Compliance Standards and Security Policies in Software Development
Getting slapped with compliance violations hurts. Trust us, we’ve seen it happen to plenty of companies who thought they could wing it. ISO 27001 and NIST guidelines aren’t just fancy paperwork – they’re battle-tested blueprints for keeping software secure.
Our bootcamp started teaching compliance after watching too many teams scramble during audits. The light bulb moment came when a student’s startup failed their first security review. Could’ve been prevented with basic role separation.
Working with financial clients taught us that good security policies aren’t optional anymore. Every piece of code needs a paper trail. Every change needs proper sign-off. Sounds boring, but it beats explaining to the board why customer data leaked.
Practical Applications and Typical Functions Separated
Breaking down who does what in software development isn’t rocket science. But getting it right makes the difference between smooth sailing and total chaos.
Key separations that prevent disasters aren’t theory, they come straight from real separation of duties examples in IT where companies learned the hard way why boundaries matter.:
- Code writers can’t approve their own work
- Repository access stays limited and logged
- Changes need documented approvals
- Post-deployment checks happen independently
- Security testing runs separately from dev testing
Remember that time a lone developer pushed straight to production at 2 AM? Yeah, we don’t let that happen anymore. Our graduates learn from day one: separate duties aren’t just bureaucracy – they’re protection against human nature.
Some teams still run like the wild west, where anyone can do anything. Those teams tend to show up in our incident response courses, learning the hard way why boundaries matter. Smart organizations split up duties before things go wrong, not after.
Integrating Organizational Policies and Technical Controls
Credit: Brett Codes
Policy means nothing without muscle behind it. After watching hundreds of teams struggle with role separation, we figured out what actually works.
Must-have controls that stick:
- Access limits hard-coded into Git
- Automated merge blocks without reviews
- Pipeline stops that demand manager approval
- Real-time alerts when someone tries to bypass rules
Last month, a graduate called to thank us. Their team caught a contractor trying to push code straight to production – something that would’ve slipped through before they set up proper controls. The system just said “no,” and that was that.
Most places write fancy policies that collect dust, but well-documented SoD policies and procedures examples show how to put real structure behind those rules so teams actually follow them.
We teach students to bake these rules right into their tools. When the system enforces boundaries, people can’t “forget” to follow them. Sure, it takes more setup time, but it beats explaining to clients why their data got exposed.
Strengthening Software Development Security Through Role Segregation

Nobody likes being told they can’t do something. But after ten years of teaching secure development, we’ve seen enough disasters to know better. Security isn’t about trust – it’s about reducing human error.
Software development without role separation is like a bank with no locks. Someone’s gonna mess up eventually.[2] Our students learn this through real-world examples, including that time a senior developer accidentally wiped three months of code changes because nobody was watching the repository.
The smart teams (and we’ve trained quite a few) build security fences early. They split duties between coders, testers, and deployers not because they don’t trust each other, but because they understand human nature. When everyone stays in their lane, projects run smoother.
Those weekly horror stories from Silicon Valley about leaked source code or broken deployments? Nine times out of ten, they happened because someone had too much access. That’s why our courses hammer home the basics: divide the work, enforce the boundaries, and always, always keep logs.
Conclusion
Development teams might want to take baby steps with role divisions. Start by mapping out who codes, who tests, and who pushes to production – basic stuff, but crucial. Someone writing code shouldn’t be the same person giving final approval (that’s just asking for trouble). Put in some guardrails like code reviews and deployment sign-offs.
Think of it like checks and balances. As the project grows, so should the rules. But don’t go overboard – just enough structure to keep things safe while letting people do their jobs.
If you’d like to dig deeper into how to mature your processes over time, while still keeping things lean and agile, check out this resource: Join the Secure Coding Practices Bootcamp
FAQ
How does separation of duties connect with segregation of duties and SoD in software development?
Separation of duties and segregation of duties both aim to keep one person from holding too much control. In SoD in software development, this means splitting coding, testing, and deployment so no one controls every step. It’s a guardrail that lowers the risk of mistakes or abuse.
Why is software development lifecycle security tied to role-based access control and developer privileges?
Software development lifecycle security depends on setting clear limits. Role-based access control ensures developer privileges stop short of production environment control. This way, no single person can change or release code without checks, which strengthens software integrity and trust.
What is the role of the code review process, peer code review, and independent testing in quality assurance in software?
The code review process, especially peer code review, catches bugs before they grow. Independent testing and quality assurance in software add another layer, finding issues developers may miss. Together, these steps support error reduction techniques and protect software integrity.
How do deployment control and release management reduce risks with production environment control?
Deployment control and release management set the rules for moving code into production environment control. By requiring deployment approval or multi-person approval, teams reduce fraud prevention in software and keep custody of code safe. It’s about slowing down just enough to avoid costly errors.
Why do change management control and software audit trails matter for record keeping software development?
Change management control makes sure every update follows rules, while software audit trails document what changed. In record keeping software development, this helps reconciliation processes and authorization control. These measures protect against SoD violation impact and give clear proof during software security audits.
References
- https://airs.uptimeinstitute.com/blog/17-news
- https://en.wikipedia.org/wiki/Separation_of_duties

