
Secure systems don’t begin with advanced firewalls or costly add-ons, they start with secure defaults and fail-safe design. From the very first setup, technology should be locked down, not left wide open. And when things inevitably go wrong, systems must fail in ways that protect rather than expose.
These two fundamentals often get overlooked, yet they determine whether weaknesses stay hidden or turn into disasters. Developers who build with these principles create environments that are safer by design, not by chance.
Keep reading to learn why secure defaults and fail-safe design are the backbone of real security.
Key Takeaways
- When systems start up in their safest state, we’re less likely to see security mistakes turn into breaches.
- Things break – that’s just reality. Good design means systems lock down tight when failures happen.
- These aren’t just fancy ideas – they’re the building blocks our students need to create systems people can trust.
Fail Safe vs Fail Secure: Understanding the Difference

A lot of developers get tripped up on fail safe vs fail secure, and yeah, it matters more than you’d think. The fail-safe approach puts people first: when something breaks, the system defaults to keeping everyone safe. Picture those emergency exit doors that unlock automatically during power outages.[1]
Security-first thinking works differently. A fail-secure setup keeps things locked down no matter what goes wrong. Think of bank vault doors – they stay locked even if the power dies, though there’s always some backup way to get people out safely.
Working with our students, we’ve seen this play out in real security setups. Last month’s data center project showed why this stuff matters: their system kept unauthorized folks out during a major crash, while still giving the ops team a way to bolt if needed. These aren’t just textbook concepts – they’re real-world problems we tackle every day.
The Importance of Secure Defaults
Look at any major breach in the last five years – chances are it started with something basic, like factory settings that nobody bothered to change.
Our security bootcamp students learn this lesson fast: systems need to ship locked down tight from the start, and that’s where understanding the importance of secure defaults really comes in. No open doors, no easy passwords, no “we’ll fix it later” mindset.
Last month, we walked through a manufacturing plant where cheap IoT sensors were basically saying “hack me” to anyone who looked. Default passwords still active, every port wide open – rookie mistakes that could’ve brought the whole place down. Just switching to secure defaults cut their risk by half.
The real fix isn’t pushing users to figure out security settings – most folks don’t have time for that anyway. Smart developers (the ones we’re training) build security in from the start.
Implementing Fail Safe Defaults
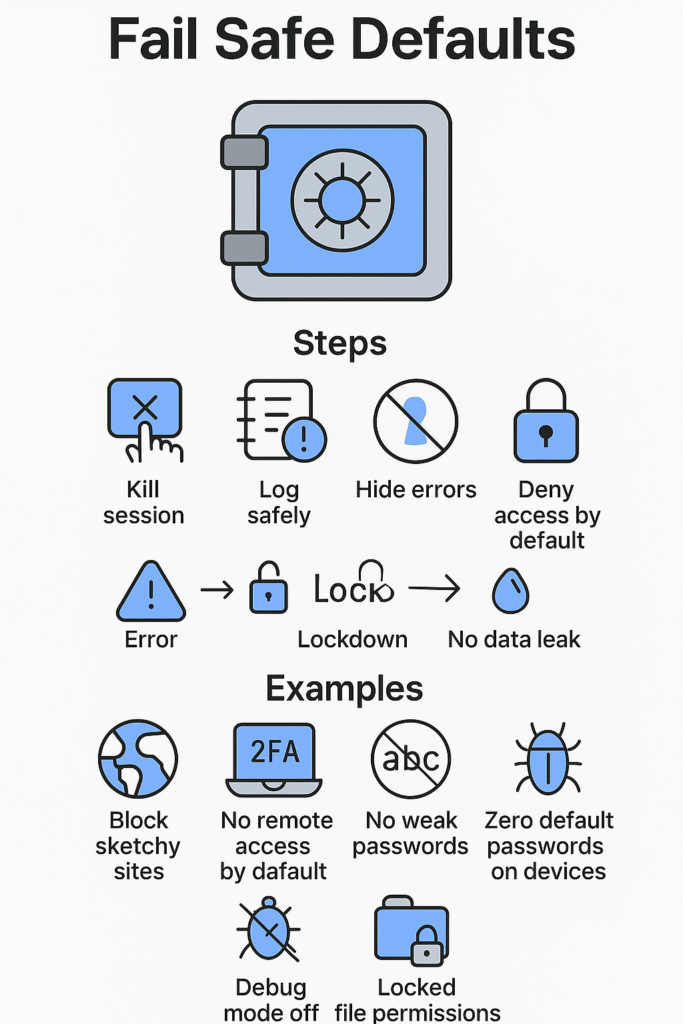
Look, systems mess up – it’s just part of the game. But what happens next? That’s where fail-safe defaults come in. After watching thousands of student projects in our bootcamp labs, we’ve learned that every single error needs to trigger an immediate lockdown. No exceptions.
Picture this: You’re building an authentication system. Something weird happens during login – maybe the database connection drops, or someone’s trying something funky with the input. What does your code do? Here’s what we teach:
- Kill the session immediately
- Log everything (but nothing sensitive)
- Never show detailed errors to users
- Default to “access denied” until proven otherwise
Last week, one of our students nailed it perfectly in their final project. Their payment API hit a glitch during processing – instead of letting the transaction hang or possibly double-charge, everything locked down tight. Zero data leaked, no money lost, clean failure state.
This stuff isn’t rocket science – it’s about building systems that know how to fail gracefully. When things go wrong (and trust me, they will), your code needs to act like that bank vault door: slam shut, stay shut, no questions asked. Every system we help build follows this rule: if you’re not 100% sure it’s safe, assume it isn’t.
Secure Default Configurations Examples
Real security isn’t complicated – it’s about getting the basics right every time. Here’s what that looks like:
- Web browsers that straight-up block sketchy sites
- Computers that say “nope” to remote access unless you specifically allow it
- Two-factor auth that’s just part of the deal for admin accounts
- Systems that refuse to accept “password123”
- Network gear that ships with zero default passwords
- Production servers with debug modes killed
- File permissions locked down tight from day one
These aren’t just random rules – they’re hard lessons learned from watching system after system get owned because somebody thought “default settings are probably fine.” They’re not fine, and our job is making sure tomorrow’s developers know better.
Principles of Secure by Default
When developers build systems with security as an afterthought, they’re asking for trouble. Secure by default is grounded in foundational security principles, safety woven right into the code’s DNA from day one, not patched in later when things go wrong.
Here’s what makes a system truly secure by default:
- Gets to the root of security problems instead of slapping band-aids on symptoms
- Makes security feel natural to users, not like pulling teeth
- Ships with safe settings out of the box – no PhD required
- Adapts to new threats as they pop up (because they always do)
The approach works by:
- Locking down unnecessary features and ports
- Setting strict access controls automatically
- Running with minimal privileges by default
- Using encryption everywhere possible
- Keeping audit logs without users having to think about it
Good security doesn’t mean making things harder to use. It’s about smart defaults that protect users without getting in their way. And it definitely doesn’t rely on keeping attackers in the dark – because that’s just asking to get burned.
Some folks might push back against disabled features or extra steps, but that’s way better than explaining to the boss why customer data’s showing up on the dark web. Security that’s built-in beats bolt-on every time.
Plus, when systems come pre-hardened, there’s less chance of human error – which we all know is usually where things fall apart. The best security’s the kind users don’t even notice.
Avoiding Insecure Default Settings
Every week brings news of another company getting hacked because someone forgot to change a password from “admin1234.” It’s like leaving your front door wide open and hoping nobody walks in – except the whole internet can see that door.
The biggest security holes usually come from these out-of-the-box settings that nobody bothered to fix:
- Factory-set passwords that might as well be “password123”
- Services running that nobody needs (but hackers love)
- File permissions so loose everything’s basically public
- Encryption either missing or stuck in the 1990s
- Debug modes spitting out enough info to make an attacker’s day
Smart teams catch these problems by:
- Running automated security checks before anything goes live
- Making security reviews part of their deployment checklist
- Setting up monitoring to catch when things drift from secure settings
- Getting their teams trained on what to look for
Even experienced admins sometimes miss these basics, thinking “nobody would bother attacking us.” But automated bots don’t care who you are – they just scan for easy targets. And those default settings? They’re usually the first thing these bots check.
A solid secure-settings audit might take an extra day up front, but that beats spending weeks cleaning up after a breach. And with the right tools checking things automatically, there’s really no excuse for leaving those digital doors unlocked.
Designing Fail Safe Mechanisms
When things go wrong in complex systems, they tend to go wrong in spectacular ways. That’s why smart engineers spend as much time planning for failure as they do for success.
Key elements of fail-safe design include:
- Running “what-if” scenarios for every possible failure point
- Building systems that naturally return to safe states
- Making sure humans can step in when automation fails
- Testing failure modes before they happen in real life
The best fail-safe systems think through scenarios like:
- Power outages hitting at the worst possible moment
- Network connections dropping during critical operations
- Hardware giving up right when you need it most
- Multiple components failing at once
Take those cooling valves in industrial equipment – they’re designed to open up when power dies, because a hot machine’s way worse than a stopped one. Same thing with good software: when something breaks, it should fail in a way that doesn’t make things worse.
Every new feature needs this kind of thinking baked in from the start. It’s not just about keeping things running – it’s about making sure they stop running the right way when they have to. And yeah, sometimes that means adding manual controls that seem old-school, but they’re lifesavers when everything else goes dark.
The real trick is testing these failure modes without actually breaking anything important. That’s where simulation and careful planning come in.
Benefits of a Secure Default Posture
Getting security right from the start might take extra work, but it’s like building a house on solid ground – everything’s easier after that. When systems come pre-hardened against attacks, everyone sleeps better at night.
The payoff shows up in several ways:
- Way fewer places for attackers to poke around
- Users don’t have to be security experts to stay safe
- Customers actually trust the system to protect their data
- Auditors spend less time finding problems
- New releases roll out faster with fewer security holdups
Good defaults mean:
- Less time spent fixing preventable problems
- Fewer emergency patches in the middle of the night
- Smaller chance of ending up in the news for the wrong reasons
Almost every major breach in the past few years started with something basic – a default password here, an open port there. The cleanup costs millions, but the fix would’ve taken minutes if someone had caught it early.
Systems with solid security defaults just work better. They’re like well-oiled machines that keep running while others stumble. Sure, they might seem strict at first, but that’s way better than explaining to the CEO why customer data’s showing up where it shouldn’t.
And when something does go wrong (because something always does), good defaults mean the problem stays small and fixable instead of turning into a company-ending disaster.
Frameworks and Audits for Secure Default Settings
Credit: Ned in The Cloud
Every decent security standard these days puts secure-by-default front and center, and there’s a good reason for that. When systems come pre-hardened, there’s less chance of someone messing up the basics.
Modern security frameworks focus on:
- Automated scans that catch weak spots before attackers do
- Regular permission checks to spot who’s got access to what
- Multi-factor auth everywhere it matters
- Getting rid of features nobody uses (but could get hacked)
- Changing up passwords and keys before they get stale
The smart teams don’t just run these checks once and call it done. They build them right into their development process, so every new piece of code gets the same treatment. It’s like having a security guard that never sleeps.
When something does go wrong (and something always does), good defaults mean the damage stays contained. Instead of attackers getting the run of the place, they’re stuck in one small corner.
Sure, keeping up with all this takes work. But it’s way easier than explaining to the board why customer data’s all over the internet. Plus, most of it can run automatically while developers focus on building new features.[2]
The real trick isn’t just setting things up right – it’s keeping them that way. That’s where continuous monitoring comes in, catching drift before it becomes a problem.
Auditing Insecure Default Configurations

Security’s a bit like cooking – leave something unattended too long and it starts to spoil. Even the best-configured systems drift towards chaos if nobody’s watching, and that’s where solid auditing saves the day.
Common weak spots that regular checks catch:
- Ports left open that shouldn’t be (happens more than you’d think)
- Password rules that somehow got relaxed
- Users with way more access than they need
- Security features switched off for “just a minute” that turned into forever
Smart security teams set up automated scans that look for:
- Configuration changes that don’t match the baseline
- New services popping up without approval
- Permission changes that nobody authorized
- Security tools that stopped running
Nobody means to let things slip, but between updates, patches, and the daily grind, settings start to drift. One admin makes an exception for a deadline, another tweaks something for a quick fix, and pretty soon the secure defaults are anything but.
That’s why the best places run these audits like clockwork – daily, weekly, monthly checks that catch problems while they’re still small. Mix in some good training so people understand why these checks matter, and you’ve got a recipe for keeping things locked down tight.
And yeah, sometimes these scans feel like overkill, but they’re way cheaper than dealing with a breach because somebody forgot to close a port.
Conclusion
Security isn’t some bolt-on feature – it’s built right into the bones of good systems. Our students learn this on day one: lock everything down at startup, and make sure things fail safely when they break. After training hundreds of developers, we’ve seen how this approach stops problems before they start.
Want better security? Start by checking your defaults and building safety nets into your code. Trust me – when things go wrong (and they will), you’ll be glad you did. Join our Secure Coding Bootcamp
FAQ
What are secure defaults and why do they matter in secure system design?
Secure defaults give systems a safe starting point so users don’t need to change settings to stay safe. With secure default configurations, default secure settings, secure default posture, and secure baseline settings, systems block weak spots early. This approach cuts down the chance of security misconfiguration, insecure default settings, or risky gaps. A good secure system design builds on secure by design principles, secure by default frameworks, and secure by default software to protect users from the start without expert setup.
How does fail safe design work compared to the fail secure principle?
Fail safe design and the fail secure principle handle breakdowns in different ways. The fail safe defaults principle keeps people safe by using fail safe mechanisms like fail safe fallback, fail safe error handling, fail safe password policies, or even fail safe exit doors. The fail secure principle locks down data with fail secure fallback, fail secure password policies, fail secure logging, fail secure firewalls, and fail secure data protection. When comparing fail secure vs fail safe, both reduce risk but with different trade-offs depending on what matters most.
What are examples of fail safe vs fail secure in real systems?
Real examples show how fail safe vs fail secure locks, fail safe vs fail secure examples, and fail safe industrial systems differ from fail secure security systems. Fail safe access control, fail safe authorization, and fail safe industrial control focus on letting people exit safely or keeping power running. Fail secure access control, fail secure authorization, and fail secure encryption defaults protect secrets by locking them tight. Fail safe defaults in IoT and fail secure defaults in IoT, plus fail safe safety systems and fail secure security systems, show how systems react to failure.
How do secure by default practices reduce risks from security misconfiguration?
Secure by default means starting with safe choices. This includes secure default network settings, secure default firewall rules, secure default encryption, secure default API configurations, secure default authentication, and secure default VPN settings. Secure device configurations, secure software defaults, secure hardware defaults, and secure default logging also help. With secure by default software, secure by design software development, secure by default in apps, and secure by design principles, the system avoids audit insecure default configuration and other weak points that create security risk default settings.
Why are secure default password policies and least privilege principle important?
Secure default password policies build strong protection, while fail safe password policies or fail secure password policies add safety during failures. The least privilege principle, default deny access, default security controls, and default secure user permissions keep accounts locked unless access is truly needed. Secure default encryption, fail safe encryption defaults, fail secure encryption defaults, and secure system fallback protect data in motion. Secure integration defaults, default secure cloud configuration, secure cloud defaults, and secure configuration management also reduce security risk default settings that threaten systems.
What benefits come from secure defaults and fail safe design together?
Secure defaults benefits include fewer chances of security misconfiguration, stronger secure default firewall rules, safer secure default authentication, and more trust in secure default API configurations. Fail safe design benefits appear when fail safe fallback, fail safe authorization, fail safe product design, and fail safe application design reduce harm during breakdowns. Fail secure design benefits are clear too: fail secure authorization, fail secure logging, fail secure encryption defaults, and fail secure application design keep data safe. Secure defaults statistics show that mixing both strategies improves safety without adding too much friction.
References
- https://en.wikipedia.org/wiki/Fail-safe
- https://mitsloan.mit.edu/ideas-made-to-matter/mit-report-details-new-cybersecurity-risks

