
Security teams face chaos when their systems get too complex. We’ve seen it firsthand in our bootcamps, overloaded tools, messy configurations, and endless manual checks create gaps where bugs sneak in. Through years of training developers, our team learned that simple, solid coding practices build stronger defenses than fancy tools ever could.
Most security breakdowns happen because teams juggle too many moving parts. Cutting back on unnecessary tools and letting automation handle routine tasks means fewer slip-ups. Want to learn how to streamline your security without losing control? Keep reading.
Key Takeaways
- Secure coding practices build simplicity and reduce vulnerabilities from the start.
- Consolidating and automating security tools streamlines monitoring and response.
- Prioritizing critical assets and standardizing configurations minimize exposure and errors.
The High Cost of Complexity in Security
Complexity in security systems is like a fog that clouds vision. When so many tools, policies, and configurations get piled together, it’s easy to lose track of what’s really happening. This often leads to blind spots, those unseen vulnerabilities where attackers slip in unnoticed. We’ve seen firsthand how misconfigurations are a leading cause of breaches.
For example, a recent incident in one of our projects showed how an overlooked open port, a tiny detail, led to weeks of investigation and costly damage control. Over time, teams learn that the real enemy of security isn’t just hackers, it’s unchecked complexity itself, which breeds confusion and weakens even the strongest defenses.
Multiple disconnected tools create fragmented security data. Teams struggle to correlate alerts, often ignoring critical warnings amid noise. Complexity increases human error; the more complicated the setup, the easier it is to slip up. This isn’t just theory, studies show a significant percentage of breaches stem from misconfigured systems or overlooked security gaps.
- Complexity reduces visibility and increases attack surface.
- Misconfiguration and human error rise with complexity.
- Breach costs soar when security systems are tangled and hard to manage.
Simplifying here isn’t just nice to have, it’s a must for any organization serious about cybersecurity.
Strategies for Simplifying Secure Systems
Credits: Semiconductor Engineering
Security by Design: Building Simplicity from the Start
We’ve found that integrating security early, right from the design phase, is the most effective way to keep things simple. Secure coding practices are our go-to foundation. Writing code with security in mind from the beginning means fewer vulnerabilities later. (1) That’s because complex fixes or patches often add layers of complication. Teams that embrace simplicity in security from the ground up discover how vital it is to focus only on what truly matters, proving the importance of simplicity in preventing unnecessary risks before they appear.
Secure system design means thinking about least privilege access, identity and access management, and secure configuration management from day one. It’s easier to prevent problems than to untangle them afterward. When developers are trained to follow secure coding standards, the whole system benefits, there’s less risk, and security teams spend less time firefighting.
- Embeds security in development lifecycle.
- Reduces vulnerabilities before deployment.
- Avoids costly, complex fixes later.
Consolidation of Security Tools: Streamlining for Efficiency
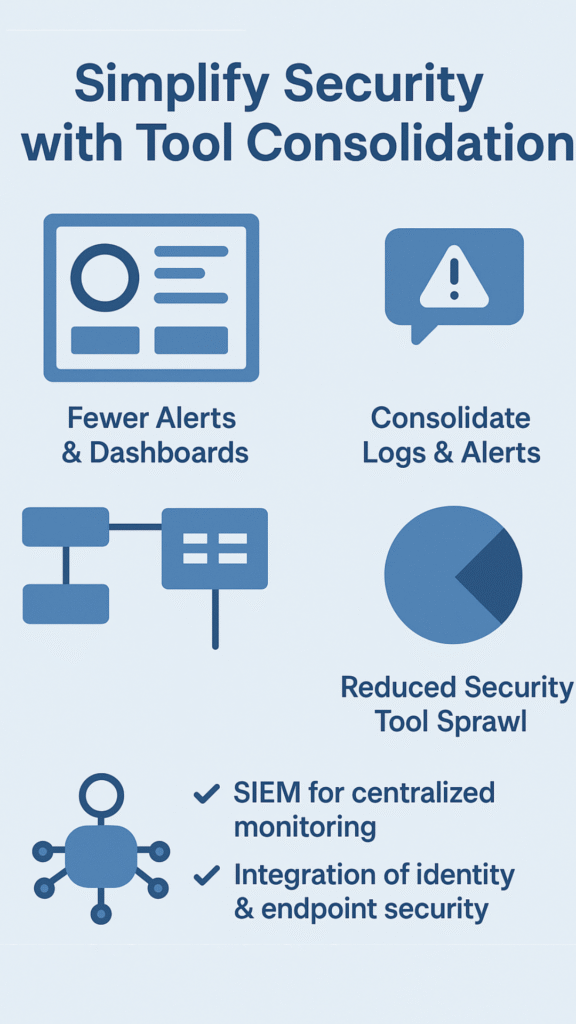
Trying to manage a dozen different security tools is a headache. Each tool generates its own alerts and logs, making it a challenge to get a clear picture. What we do is consolidate security logs and alerts into centralized platforms. This approach improves security visibility and cuts down management overhead.
Security tool consolidation means fewer dashboards, less switching between systems, and a quicker response to incidents. It also reduces security tool sprawl, which is a major cause of complexity. Our experience shows that when teams work with integrated platforms, they can automate workflows and streamline security operations effectively.
Some practical ways to consolidate include:
- Centralizing security monitoring with SIEMs.
- Integrating identity and access management with endpoint security.
- Rationalizing vendors to reduce overlapping tools.
This doesn’t mean buying the most expensive solution, but rather choosing tools that play well together and support automation.
Minimizing the Attack Surface: Reducing Exposure
Less is often more when it comes to security features. If a system has unnecessary applications, open ports, or enabled protocols, it creates more opportunities for attackers. We always recommend streamlining systems to essentials only.
Disabling unused services and closing unneeded ports reduces the attack surface. It’s a straightforward way to lessen vulnerabilities and simplify security monitoring. When things are stripped down to what’s necessary, it’s easier to enforce security policies and spot anomalies.
For example, in one project we helped, removing legacy systems and unused software reduced the workload for patching and vulnerability management significantly.
Standardization: Leveraging Industry Best Practices
Standard configurations and protocols reduce the risk of human error. When everyone follows the same rules, systems become more predictable and easier to manage. We encourage using benchmarks like CIS for system hardening and standardizing security architectures.
Security architecture standardization simplifies compliance and security governance. It also helps with security lifecycle management because updates and audits become routine rather than ad hoc.
- Follows recognized security standards.
- Minimizes custom, error-prone configurations.
- Makes audits and compliance easier.
Automation: Reducing Manual Processes and Errors
Manual security processes are slow and error-prone. Automation, in contrast, speeds up threat detection and incident response, and reduces human error. We leverage automation to streamline security workflows, from patching to security event correlation.
Automated threat hunting and continuous security monitoring enable security teams to focus on real threats instead of drowning in alerts. Automating security updates also improves patching efficiency, closing vulnerabilities faster.
Automation doesn’t replace human judgment but supports it with faster, consistent actions. For instance, automating multi-factor authentication and identity management helps enforce secure access control reliably.
Training and Awareness: Empowering Users
Even the best systems fail if users aren’t aware of security risks. Regular training and awareness programs reduce human error by helping people recognize threats and follow best practices. We run phishing simulations and security workshops to keep everyone sharp.
Educating teams empowers them to handle security tools better and follow security policy enforcement. It’s a low-cost way to strengthen your security posture and cut down on careless mistakes.
Prioritization: Focusing on Critical Assets
Not all assets deserve the same level of protection. Prioritizing critical systems helps allocate security resources more effectively. We recommend identifying key assets and focusing defenses there.
This avoids overcomplicating security by trying to protect everything equally. Risk-based security decisions reduce security overhead and improve cyber resilience. Prioritization also guides vulnerability management and security patching efforts toward what matters most.
Benefits of a Simplified Security Approach
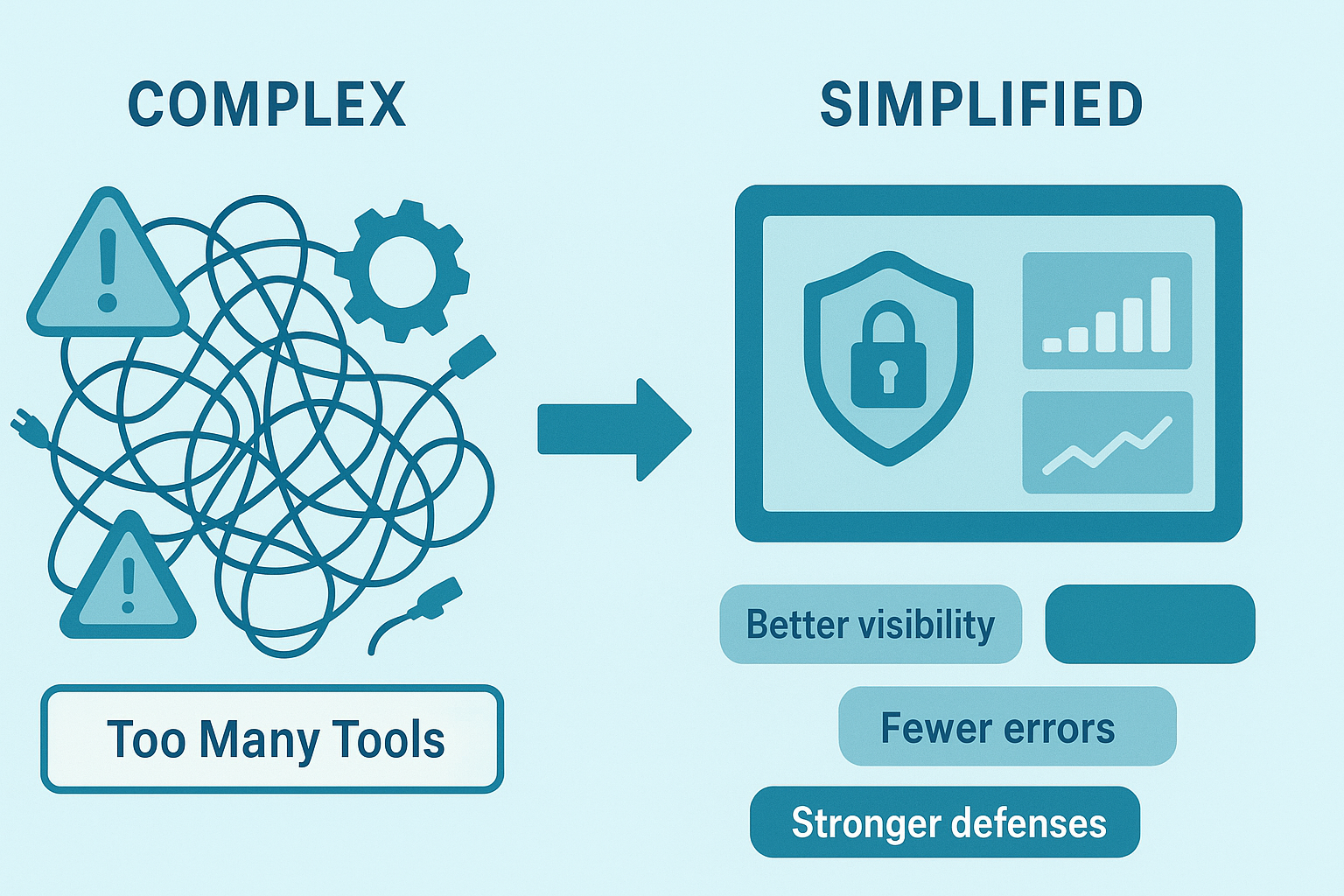
Simplifying secure systems brings several tangible benefits:
- Better visibility into security events and system health.
- Lower risk of misconfigurations and human errors.
- Easier, more efficient security management and updates.
- Improved security operations center efficiency.
- Enhanced resilience against cyber threats.
- Cost savings from avoiding redundant tools and complexity, many organizations report tool-sprawl leads to slower detection times and higher costs. (2)
These outcomes reflect what a well-structured simple security design can achieve, clarity, control, and resilience without unnecessary complication. Our teams noticed that after adopting these simplification strategies, incident response times improved, and the volume of false positives dropped. Security monitoring simplification made a big difference for workload balance.
Practical Steps to Reduce Complexity Secure Systems
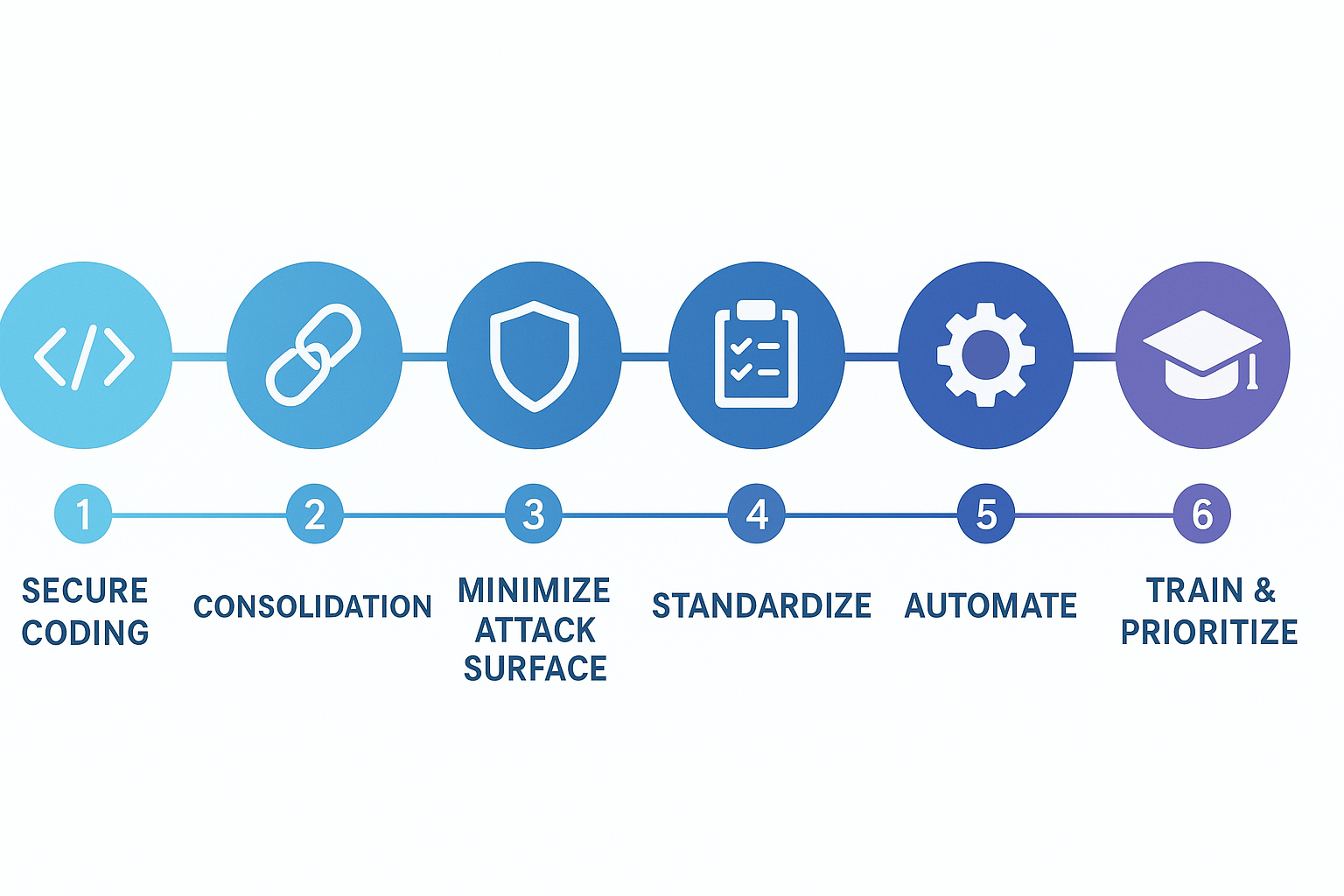
- Start with secure coding practices and secure system design principles.
- Consolidate your security tools and centralize monitoring.
- Minimize attack surfaces by disabling unnecessary services.
- Standardize configurations and enforce consistent policies.
- Automate repetitive security tasks like patching and threat detection.
- Train users regularly to reduce human errors.
- Prioritize security efforts based on risk and asset criticality.
FAQ
How does security complexity reduction help organizations stay safer?
Security complexity reduction helps by making systems easier to understand and control. When teams simplify security architecture and streamline security operations, they can spot problems faster and fix them before attackers do. It also improves security visibility and reduces human error in security, making defenses more reliable and easier to manage long-term.
What’s the best way to simplify security architecture without losing protection?
To simplify security architecture, focus on security tool consolidation and centralized security management. Combine tools that overlap, reduce security tool sprawl, and standardize secure system design. Using security architecture standardization and security policy simplification ensures every part of your setup works together smoothly, improving security governance and cyber resilience.
How can automation improve cybersecurity simplification strategies?
Security automation can boost threat detection automation, automate security updates, and speed up security incident response. Automated threat hunting and continuous security monitoring reduce human error and improve security patching efficiency. These steps help minimize vulnerabilities and simplify encryption management while keeping your security operations center efficiency high.
What are practical ways to reduce attack surface and misconfiguration risks?
Start with secure access control, least privilege access, and strong identity and access management. Simplify endpoint security and secure configuration management to reduce attack surface. Network segmentation, reduce legacy systems, and security lifecycle management all help reduce misconfiguration. These cybersecurity best practices lead to better risk-based security and stronger cyber risk reduction.
How can companies make cybersecurity easier to manage every day?
Companies can use IT infrastructure simplification, security vendor consolidation, and security workflow optimization. Simplify identity management, use AI in cybersecurity for threat intelligence automation, and apply secure design principles. Regular security training and awareness programs support staff, while security process automation and security compliance simplification help manage security risks efficiently.
Conclusion
Reducing complexity in secure systems isn’t about cutting corners, it’s about thoughtful design and practical steps that make security both manageable and effective. By prioritizing secure coding practices, consolidating tools, and automating where possible, organizations can shrink attack surfaces and strengthen their security posture with less effort and fewer headaches.
If you’re ready to simplify your security strategy and build stronger defenses, consider joining the Secure Coding Practices Bootcamp. The program trains developers to create secure software through hands-on, real-world coding, no jargon, just practical skills. Designed by experts, it covers essentials like the OWASP Top 10, input validation, authentication, encryption, and dependency management.
Whether for teams or individuals, this two-day course (available live online or in person) includes labs, replays, cheatsheets, and certification. It’s a clear path toward greater visibility, fewer mistakes, and stronger protection, starting from the code itself.
References
- https://arxiv.org/abs/2412.11121
- https://www.techradar.com/pro/security-tool-bloat-is-the-new-breach-vector

