
Security isn’t a patch job. At our dev training bootcamp, we’ve seen hundreds of teams scramble to fix vulnerabilities after deployment, a stressful, costly mess that rarely works out. Think of it like building a house: you wouldn’t wait until after construction to add the locks and alarm system. The real solution? Bake security right into the blueprint.
We teach our students that early integration goes beyond just writing secure code. It reshapes how development teams collaborate and think about protection from day one. Over the past decade, we’ve guided organizations to spot risks before they become problems. Ready to learn the practical steps? Read on.
Key Takeaways
- Cuts down costly late fixes and breach risks.
- Aligns security with functionality and business goals.
- Builds stronger, more trustworthy systems from the ground up.
The High Cost of Late-Stage Security
There’s a scene that tends to repeat itself in many organizations: a software project is almost ready to launch, and suddenly the security team discovers a gaping hole. Panic ensues. Developers scramble to patch, testers rush back to recheck, and budgets spiral out of control. I’ve seen this happen more times than I care to count. It’s not just frustrating, it’s shockingly expensive.
A recent study put the average cost of a data about US $4.88 million (2024 global average) (1), and late-stage fixes add a significant chunk to that number. Why? Because vulnerabilities found late can mean rewriting code, rearchitecting systems, or even halting launches. Plus, there’s the damage to reputation, customer trust, and regulatory penalties. In one case, a client had to delay a product launch for months due to last-minute security flaws that could have been caught during design. That delay alone cost them millions.
Waiting to integrate security also means your attack surface grows unchecked. Systems get more complex over time, and each component adds potential weaknesses. If security isn’t part of the original blueprint, it’s like building a castle on sand.
- Research indicates defects found late in development (or production) can cost up to 15-30× more than if addressed early. (2)
- Breaches damage brand reputation for years.
- Lost customer trust takes a long time to rebuild.
The takeaway? The cost of ignoring security early isn’t just financial. It’s also about lost opportunities and credibility.
Defining Early Security Integration
What Is Security by Design?
Security by design is the idea that security isn’t something you tack on later. Instead, it’s sewn into every stitch of your system’s fabric. From the moment the first line of code is planned, security guides decisions. For us at MSSP Security, it means thinking about who might attack, how they might break in, and then building walls, traps, and alarms right into the architecture.
Think of it like building a house. You don’t wait until after it’s built to put in locks or an alarm system. You plan the security features from the start, reinforced doors, secure windows, maybe even a fence, so the house is safe no matter what.
Core Principles Explained
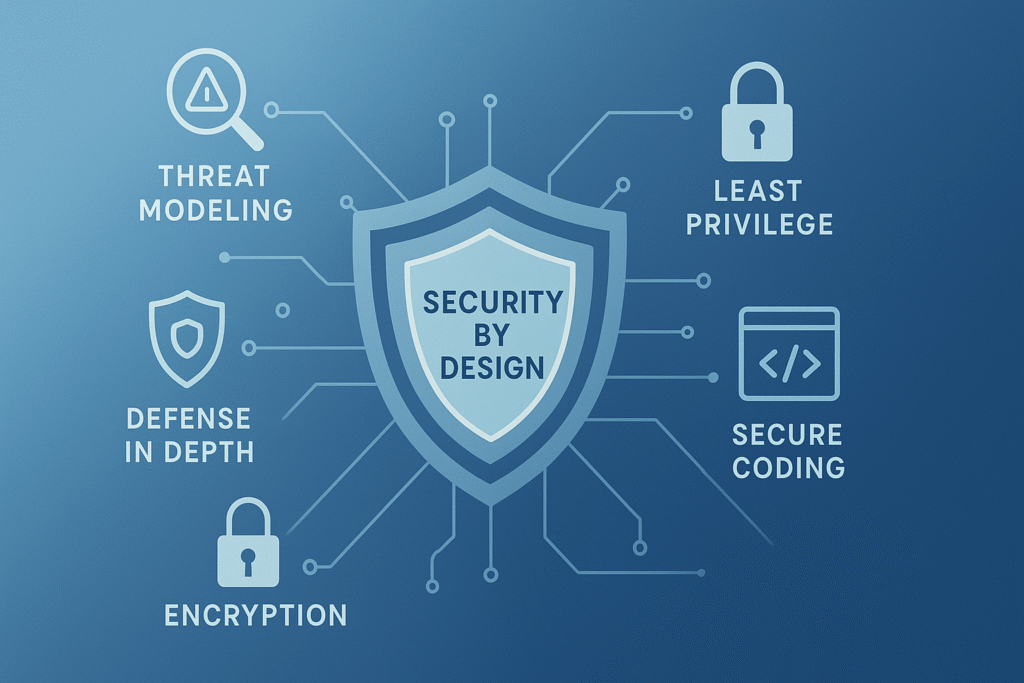
Threat modeling is the first step. You sit down with your team and ask: Who might want to break in? What parts of the system are most attractive? What tools or methods could they use? This isn’t guesswork; it’s a structured analysis that reveals your system’s weak spots early.
Next, security requirements must be crystal clear and measurable. What exactly needs protecting? User credentials, sensitive data, system availability? These goals should be as important as any functional feature like user interface or performance.
Secure architecture minimizes the attack surface by enforcing least privilege, only giving users and components the minimum access they need. Defense in depth means layering multiple security controls so if one fails, others still protect the system. For instance, segmenting networks or isolating sensitive components, ideas rooted in secure design principles that keep systems resilient from the start.
Secure coding practices go beyond writing code that works, they prevent common pitfalls like injection flaws or buffer overflows. Regular code reviews and automated scans catch mistakes before they become vulnerabilities.
Risk assessment is continuous. New features, design choices, or third-party components can introduce fresh risks, so you prioritize what to fix based on potential impact.
Security testing is not a single step but a process. Static and dynamic code analysis, penetration testing, black box and gray box testing, all uncover hidden vulnerabilities before release. And protecting user data through encryption and privacy by design principles keeps sensitive information safe.
- Threat modeling to identify risks early.
- Clear, measurable security requirements.
- Designing architecture with least privilege and defense in depth.
- Secure coding standards and automated code scanning.
- Continuous risk assessment and security testing.
- User data protection via encryption and privacy by design.
💡 Pro Tip: Document every security decision and reasoning during design. It’s a lifesaver for audits and future improvements.
Step-by-Step Integration into SDLC
Credits: Drupal Austria
Planning and Requirements
Security isn’t just a checkbox. When we start working with clients, we insist on defining security requirements alongside functional ones. This means talking openly about threats, compliance needs, and business impacts, not just technology. The earlier the security team is involved, the better aligned the project is.
💡 Pro Tip: Include security experts from day one to ensure security goals match business objectives.
Design Phase
Here you create the secure architecture patterns. It’s where you decide how components interact, which parts get separated, and how access controls work. Threat modeling sessions help identify design flaws before a single line of code appears. These architectural choices often reflect secure design patterns that strengthen both usability and long-term protection.
💡 Pro Tip: Use architectural risk analysis to spot and fix design weaknesses early.
Development Phase
Developers follow secure coding standards to avoid common vulnerabilities. We recommend code reviews and pair programming to keep security in check. Automating code scans with tools that catch injection flaws, buffer overflows, and insecure API calls speeds up this process. It’s a safety net that complements human oversight.
💡 Pro Tip: Automate code scanning early and often to catch issues before they become costly.
Testing Phase
Security testing is ongoing, not just at the end. Static code analysis spots errors in code syntax and logic. Dynamic analysis tests running applications for vulnerabilities. Penetration testing simulates real attacks, often revealing subtle weaknesses automated tools miss. Black box testing tests from an external attacker’s perspective, while gray box testing mixes insider knowledge for a more thorough probe.
💡 Pro Tip: Simulate attacks to uncover vulnerabilities that automated scans might overlook.
Deployment Phase
Deployment isn’t the finish line. Secure configuration, patch management, and continuous monitoring ensure systems stay protected. Incident response plans help teams act swiftly when things go wrong. We often stress that a good incident response plan is as important as prevention, because breaches can still happen.
💡 Pro Tip: Implement an incident response plan to minimize breach impact and recover quickly.
Benefits of Proactive Security

Reduced Breach Likelihood
When security is baked into design, attack surfaces shrink. Least privilege and defense in depth mean breaches don’t cascade. Our clients have reported fewer incidents and faster detection thanks to these practices, clear proof that applying secure software design principles delivers measurable results over time.
Enhanced Compliance
Early integration helps meet regulations like HIPAA, GDPR, and PCI DSS without last-minute scrambling. Documented security decisions and controls make audits smoother.
Increased Customer Trust
Customers notice when their data is handled responsibly. Security by design isn’t just protection, it’s a statement of commitment that builds loyalty.
Optimized Costs
The money saved on avoiding emergency patches, breach investigations, and regulatory fines is huge. Early fixes cost a fraction of late-stage remediation.
Implementation Strategies

Training and Education
We prioritize training developers and architects on security principles. Understanding why things matter leads to better choices and fewer mistakes.
Automated Tools
Security tools integrated into development environments catch issues early. They don’t replace expertise but make it easier to maintain standards.
Collaboration
Security and development teams must communicate regularly. We facilitate workshops and joint reviews to keep everyone aligned.
Security Checkpoints
Setting security milestones at SDLC phases makes problems visible early. It encourages accountability and steady progress.
Documentation
Keeping detailed records of security decisions, controls, and testing results ensures knowledge isn’t lost and supports compliance.
FAQ
What does secure by design really mean in everyday projects?
Secure by design and security by design mean building protection into systems from day one. Teams plan for threat modeling, least privilege, and defense in depth instead of adding fixes later. By using secure architecture, clear security requirements, and privacy by design, organizations reduce the attack surface and improve long-term data protection.
How does threat modeling help shrink the attack surface?
Threat modeling maps out who might attack and how, so teams can close weak spots early. It supports economy of mechanism and separation of duties, keeping systems simple and safer. Combined with open design, input validation, encryption, and multi-factor authentication, it turns risk assessment into a proactive step, not a last-minute panic.
Why are secure coding practices and continuous security testing important?
Secure coding practices, code review, and static or dynamic code analysis stop vulnerabilities before release. Continuous security testing, like penetration testing, black box testing, and gray box testing, keeps software strong. Using secure libraries, secure frameworks, and component security checks makes every update safer while helping meet compliance and security policies.
How can teams stay prepared with an incident response plan?
Even with strong security controls, issues happen. A clear incident response plan and solid vulnerability management help teams act fast. Logging and monitoring, anomaly detection, and intrusion detection guide quick fixes. Secure configuration, patch management, and backup strategies ensure business continuity, disaster recovery, and secure communication when threats appear.
What helps maintain trust after deployment?
Trust comes from ongoing security governance. Secure network design, security automation, and endpoint security reduce everyday risks. Using encryption for data encryption at rest and data encryption in transit keeps privacy intact. Strong authentication, authorization, and access control, backed by security frameworks, cryptography, key management, and zero trust principles, protect users long-term.
Conclusion
From our vantage point at MSSP Security, integrating security design early isn’t a passing trend, it’s the foundation of resilient, trustworthy systems. It involves more than technology; it requires changing how teams think about security, treating it as equal to functionality. Threat modeling, least privilege, continuous testing, and incident readiness all come together to build defenses that last.
If you want your systems to avoid the chaos and costs of late-stage security surprises, start by embedding security into your design and development from day one. It’s practical, cost-effective, and the best way to protect users and business alike.
Ready to put this into practice? Join the Secure Coding Practices Bootcamp, a hands-on, expert-led course designed to help developers build secure software from the start.
References
- https://www.hackerone.com/blog/cost-savings-fixing-security-flaws
- https://www.embroker.com/blog/cost-of-a-data-breach/

