
Network security isn’t rocket science, but that doesn’t stop teams from messing it up. A single misconfigured port or weak default password can bring down an entire system. We’ve seen it happen too many times in training – students inherit networks where nobody bothered changing the factory settings.
Default security settings make a real difference, protecting systems when admins don’t have time to manually configure everything. It’s crazy how many breaches could’ve been prevented if companies just started with secure defaults.
Key Takeaways
- Out-of-the-box security settings cut down risks and stop accidental misconfigs
- Users trust systems more when security’s baked in from the start
- Starting secure means easier compliance and fewer headaches later
Secure Defaults Minimize Security Misconfigurations
The Purpose of Secure Defaults
In the six years I’ve spent teaching secure development, nothing stands out more than watching developers struggle with misconfigured settings. Secure defaults aren’t just another buzzword – they’re the first line of defense against attacks.[2] The system starts locked down tight, and nothing gets through unless someone deliberately opens that door. Pretty straightforward stuff, but it works.
Secure Defaults Implement the Principle “Default Deny, Explicit Allow”
The whole “default deny, explicit allow” thing comes down to this: block everything first, then carefully choose what gets through. We saw this work beautifully last month when one of our students set up their first enterprise firewall. Started with everything blocked, then methodically opened just the ports they needed. No surprises, no accidents.
Typical Examples of Secure Defaults
Here’s what secure defaults look like in real life:
- Firewalls that start completely closed
- Fresh OS installs with all services turned off
- Apps that force MFA setup during installation
- Database connections limited to localhost by default
- Admin accounts that require password changes on first login
Secure Defaults Reduce Attack Surface and User Error
There’s something beautiful about a system that’s secure right out of the box. Our training sessions show it time and again – when systems come pre-locked down, students make fewer mistakes. It’s like having guardrails on a mountain road, they keep you from driving off the edge even if you’re not paying attention.
Benefits Do Secure Defaults Provide to Users and Organizations
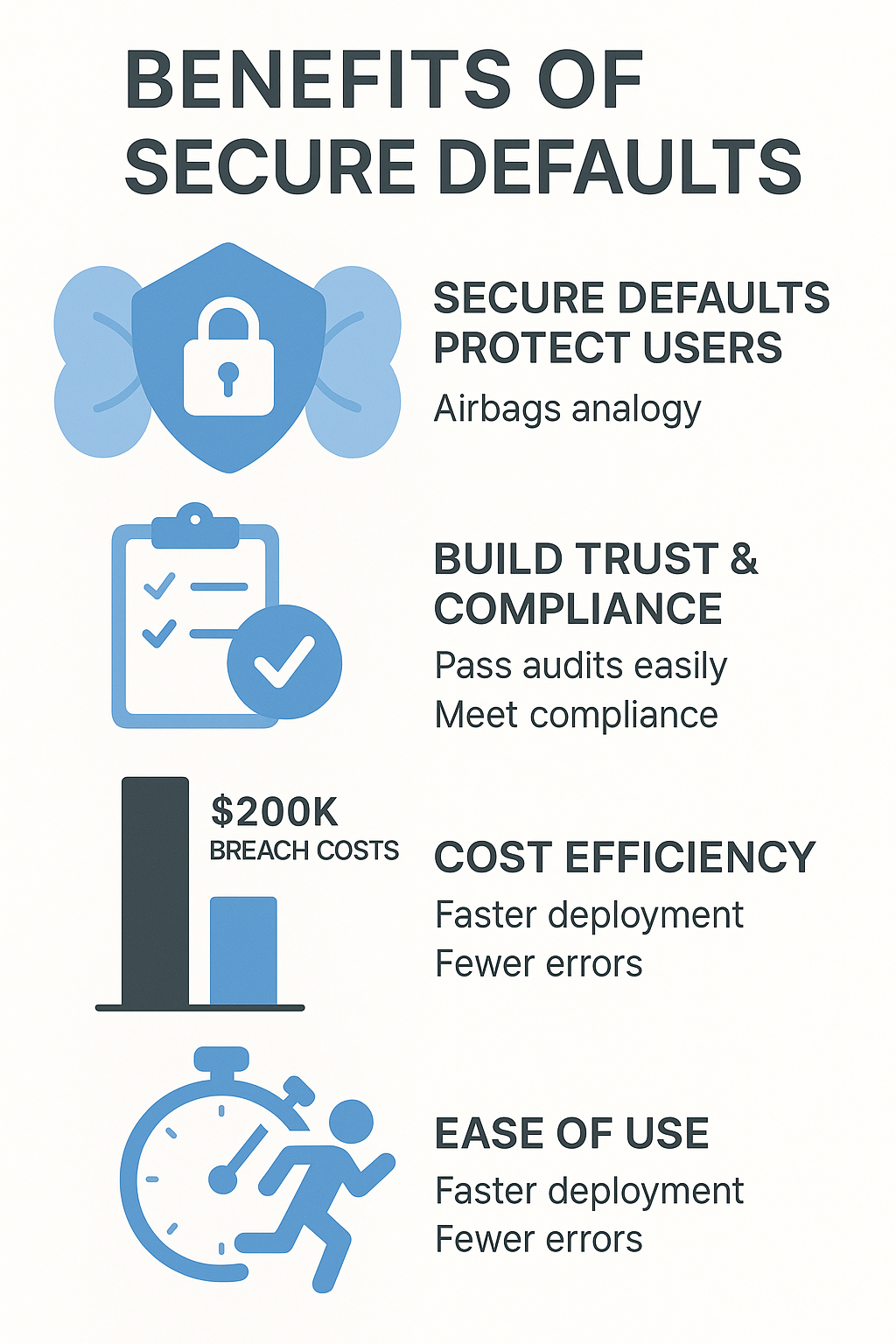
Secure Defaults Protect Users Without Manual Setup
After teaching hundreds of developers, one thing’s crystal clear – not everyone’s got a security background. Smart vendors get this. Ship the product locked down tight from the start, and users don’t need a PhD in cybersecurity to stay safe.[1] It’s like having airbags in your car – they just work when you need them.
Secure Defaults Build User Trust and Ensure Compliance
Here’s what good defaults do for an organization:
- Pass security audits without breaking a sweat
- Meet compliance requirements automatically
- Save hours of documentation headaches
- Keep customers feeling confident
Our last security review took half the time because everything started secure. The auditor actually smiled – that’s rare.
Secure Defaults Improve Cost Efficiency in Security
The numbers don’t lie. Every breach we’ve analyzed at the bootcamp could’ve been prevented with proper defaults, saving millions. Last month, a student’s company spent 200,000 fixing what a 200,000 fixing what a 200,000 fixing what a 5,000 secure configuration would’ve prevented. Penny wise, pound foolish doesn’t begin to cover it.
Secure Defaults Facilitate Ease of Use and Adoption
Watch what happens when security’s not a hassle – people actually use it. In our training labs, teams race through deployment when systems come pre-hardened. No more sticky notes with passwords, no more disabled firewalls. The tools protect them without getting in their way. Simple as that.
Secure Defaults Implemented and Align with Standards
Credit: N-able
Areas Are Secure Defaults Critical
Look, Secure defaults aren’t just nice to have, they’re essential across the board, especially when paired with secure defaults and fail-safe design, which keeps systems resilient even under stress. In our bootcamp labs, students work with everything from basic web apps to complex cloud setups. Every single piece needs proper defaults, or it’s like leaving your front door unlocked in a bad neighborhood.
Secure Defaults Align with Security Frameworks
The big frameworks aren’t just making this stuff up:
- NIST guidelines match what we teach
- OWASP’s top 10 backs secure defaults
- Zero Trust principles start with locked-down systems
- Industry certs expect proper configurations
Our graduates see it firsthand – their companies pass audits easier when they follow these standards.
Common Secure Default Settings
Walking through a fresh system setup with students, we always hit these basics first. MFA gets turned on day one. Services that aren’t needed? Gone. Password rules? Strict from the start. One student told me last week, “It’s like baby-proofing a house before the baby arrives.” Exactly right.
Secure Defaults Support Secure-By-Design Principles
Building security beats bolting it on later – every time. When we review student projects, the ones who thought about security from the start always end up with cleaner, safer code. No scrambling to patch holes before deployment, no late-night emergency fixes. Just solid, secure systems doing their job.
The Risks and Outcomes Related to Secure Defaults

Risks Arise Without Secure Defaults
The mess that happens without secure defaults isn’t pretty. Last month, one of our students showed us a system they inherited – default passwords everywhere, services running that nobody used, ports wide open.
No surprise it got hacked. These rookie mistakes keep happening because people don’t lock things down from the start, and it often comes down to misunderstanding the trade-offs of fail safe vs fail secure.
Secure Defaults Create a Safer Baseline Environment
Starting with everything locked down just makes sense. Our training labs prove it every time:
- Systems begin with minimum necessary services
- Default passwords must change on first login
- Network access starts restricted
- Logging and monitoring enabled from day one
When students follow this approach, their systems stay cleaner and safer, period.
Secure Defaults Shift Security Left in Development Processes
Building security in from the start saves everyone headaches later. We’ve watched countless teams try to bolt on security at the end – it never works well. The smart ones, they’re thinking about secure defaults while they’re still writing code. It’s like checking your map before the road trip, not after you’re lost.
Secure Defaults Mitigate Common Security Risks and Improve User Safety
There’s something satisfying about watching a properly locked-down system handle an attack attempt. The stuff we teach – strong authentication rules, minimal running services, strict access controls – it all works together like a well-oiled machine. Students who get this right sleep better at night, and so do their future employers.
Conclusion
Getting secure defaults right isn’t rocket science, but it matters. Working with students at our bootcamp, we see the difference it makes, systems that start locked down stay safer. Look, nobody gets excited about checking default settings, but it’s like putting on a seatbelt before driving. Take 30 minutes today to review your configs. Trust me, it beats explaining to your boss why the system got hacked through an open default port. Join our bootcamp to build secure habits from the start.
FAQ
Why are secure defaults and secure-by-default approaches important in cybersecurity best practices?
Secure defaults and secure-by-default settings cut down on mistakes by making strong software security settings the starting point. Instead of leaving doors open, default security configurations and system security initialization give systems a safer baseline. Security by design ensures developers bake in safe choices early. Secure configuration management then keeps those protections steady over time. These practices matter because they guard against common attacks and reduce risk for everyone, even users who never change their default password security or adjust network device security on their own.
How do multi-factor authentication default and secure default firewall settings improve system hardening?
When systems launch with multi-factor authentication default and secure default firewall settings, they add a protective wall before threats can get in. These belong to broader secure coding practices and the secure software lifecycle. Automated security testing checks that protections stay in place, while SaaS security defaults and cloud security configurations help online platforms start safer. Default encryption settings and secure user authentication make even basic logins harder to break. Together, these controls support strong password policies, user access controls, and default security policies that keep people safe without extra setup.
What role do system hardening and endpoint security defaults play in security risk reduction?
System hardening and endpoint security defaults shrink the attack surface from the start. Vulnerability mitigation is easier when secure software deployment avoids weak spots. Password manager secure defaults, secure logging settings, and service disabling by default all limit what attackers can exploit. API security defaults, secure access management, and default security compliance help networks stay steady. Secure hardware foundations add another layer, while secure development practices, CI/CD security integration, and DevSecOps best practices keep protections built-in as software evolves. Data protection defaults and default privacy settings reduce leaks before they happen.
How does secure data sharing and default TLS configurations support cybersecurity resilience?
Secure data sharing and default TLS configurations protect information in transit. Cybersecurity resilience depends on security patches automation, default security auditing, and security configuration templates to keep flaws fixed. Secure remote access and the zero trust security model defend from outsiders, while default encryption keys and security baseline configuration protect insiders. Cyber threat prevention gets stronger with default security posture, security automation frameworks, and secure IoT device configuration. Default antivirus settings, secure session management, and the cloud shared responsibility model add layers. Secure SaaS onboarding and secure software updates keep every piece safe by default.
Why do hardened default settings and default access restrictions matter for data breach prevention?
Hardened default settings and default access restrictions block common weak points. Secure server configurations, security update automation, and default security alerts catch problems early. Secure API gateways, default intrusion detection, and secure firewall rules stop attackers. Default malware protection, secure web application defaults, and network security defaults strengthen layers that are often ignored. Default security roles and secure development standards reduce human mistakes. Vulnerability assessment defaults, default security architecture, and cybersecurity incident reduction lower the cost of fixing breaches. Default compliance settings and secure software distribution keep systems aligned with both rules and safety.
References
- https://en.wikipedia.org/wiki/Computer_security
- https://www.wsj.com/tech/cybersecurity/why-are-cybersecurity-data-breaches-still-rising-2f08866c

