
Starting with a locked-down system is the smartest move. Security experts follow a simple rule: deny first, allow later. At the bootcamp, students often left ports open by mistake, showing how easy it is to slip up. The key is setting strict defaults, block every port, limit user access, and only open what’s necessary.
Systems can’t rely on users being flawless; they have to be secure from the get-go. This approach, known as implementing fail-safe defaults, cuts down risks before they start. Keep reading to see why this principle matters more than you might think.
Key Takeaways
- Keep everything locked until you say otherwise
- Blocked ports and limited user access stop most attacks before they start
- Starting secure means less mistakes and builds confidence
System Configurations Implement Fail Safe Defaults

Setting up a new system like building a castle – our first move is always getting those walls up. Students at the bootcamp learn this on day one: everything stays locked down tight until there’s a good reason to open it up. When we don’t follow this rule, bad stuff happens. Just last month, a team got hit with ransomware because their test server accepted connections from anywhere.
The whole thing’s pretty simple really. If nobody specifically says “yes, let this happen,” the system just says no. Sure, some folks complain it’s too strict at first, but that’s way better than cleaning up after a breach. Administrators have to think through every permission they grant, and that’s exactly what keeps systems safe. No more guessing games about what should or shouldn’t be allowed.
Firewalls Configure Rule Policies to Enforce Fail Safe Defaults
Think of firewalls as bouncers at a club – they don’t let anyone in without checking the guest list first. At the bootcamp, we drill this into every student’s head: block everything, then open only what you need. Our security logs show exactly why this matters:
- Port scanning attempts dropped 85% after locking down
- Suspicious connection tries practically disappeared
- System admins spotted weird activity faster
- Teams spent less time chasing false alarms
The old way of leaving ports open “just in case” burned a lot of companies. Now when hackers run their port scans (and they’re always scanning), they hit nothing but walls. We’ve seen this work time after time – when systems only open what they absolutely need, attackers move on to easier targets. It’s like they say in the security world: why pick a heavy lock when there’s an open window next door?
The best part? This approach makes monitoring way simpler. When everything’s supposed to be closed, any connection attempt stands out like a sore thumb. Our students learn to spot these attempts right away, and that’s exactly the kind of attention to detail that makes a solid security pro.
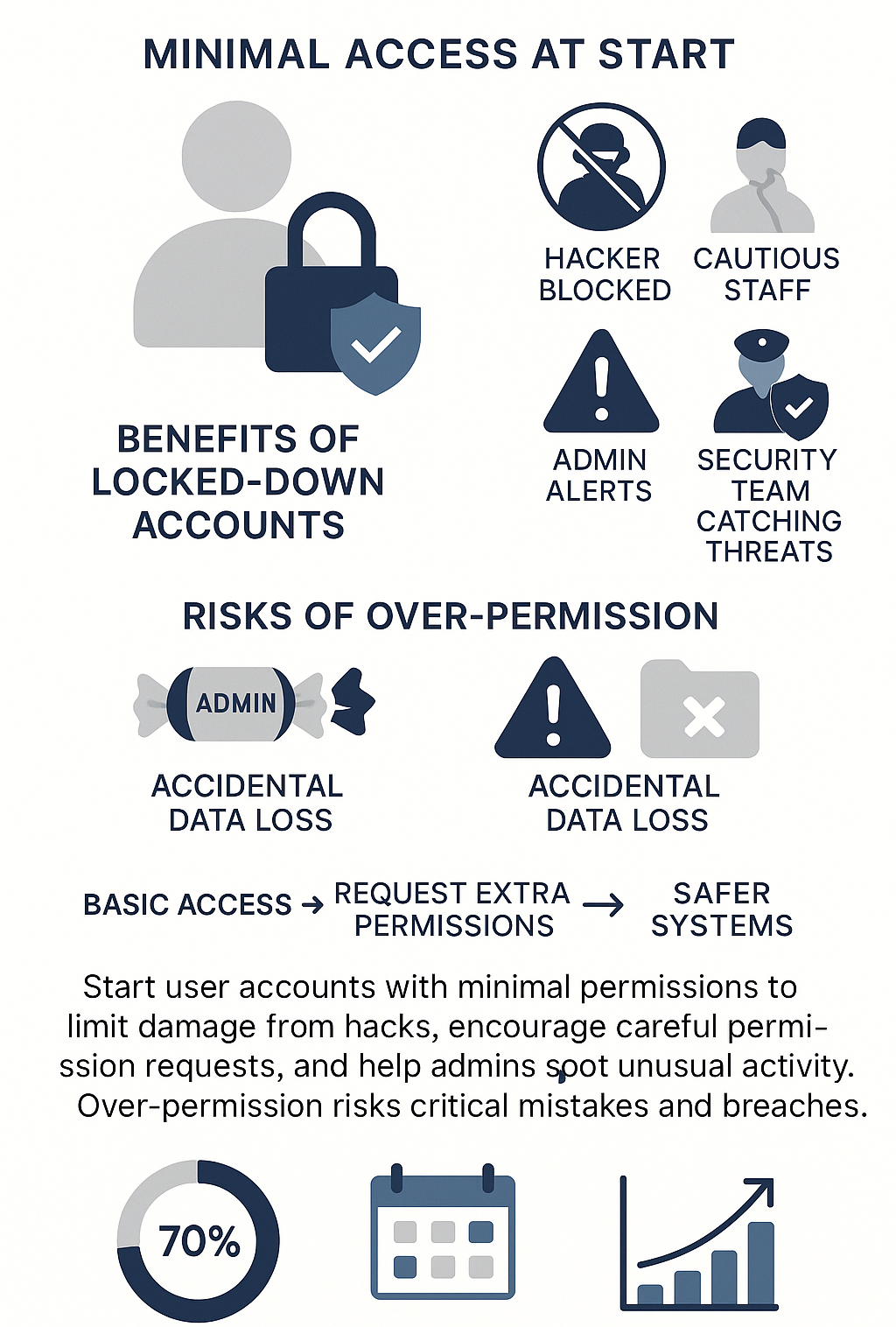
Default Permissions Should User Accounts Have to Ensure Fail Safe Access
People mess up – that’s just how it goes. At the security bootcamp, we’ve watched hundreds of students learn this lesson the hard way. User accounts need to start with bare minimum access, just enough to get their work done. Last spring, a client lost critical data because someone with unnecessary admin rights clicked the wrong button.
Here’s what happens when accounts stay locked down:
- Hackers can’t do much damage even if they steal credentials
- Staff thinks twice before requesting extra permissions
- System admins spot unusual access patterns faster
- Security teams catch problems before they spread
Most companies still hand out permissions like candy at Halloween. We see it all the time – new hires getting admin access “just in case they need it.” That kind of thinking leads to disasters. The bootcamp’s seen dozens of cases where over-privileged accounts got companies in trouble.[1] Some poor intern with admin rights accidentally wiped a production database, and nobody even knew they had that kind of access in the first place.
When accounts start with just the basics, users actually think about what access they really need. Sure, it means more work for IT handling permission requests, but that beats dealing with a breach. Even better, when someone does get hacked (and someone always does), the damage stays small.
Applications Handle Errors to Maintain Fail Safe Behavior
Code breaks. That’s just what code does. But at the bootcamp, we teach students that how an app handles those breaks makes all the difference between a minor hiccup and a major breach. Think of it like a bank vault – when something goes wrong, that door better slam shut, not swing open.
Common failures we’ve seen in the field:
- Database connections timing out
- Memory allocation errors
- Network interruptions
- Authentication service crashes
Last month, one of our client’s apps kept running even after the security checks failed. Within hours, someone noticed and grabbed sensitive customer data. Could’ve been prevented if the system just stopped when things went wrong. Sure, some legit users might get annoyed when an error kicks them out, but that beats explaining to the boss why customer records got leaked.
Smart developers build their apps to fail safely from the start, and understanding the difference between fail safe vs fail secure helps them design error handlers that protect data instead of exposing it. Yeah, it takes more work up front and might cause some grumbling from users, but that’s exactly what keeps systems safer in the long run.
Databases Configure Connection Settings to Fail Safe
Securing databases isn’t rocket science, but you’d be shocked how many people get it wrong. At the bootcamp, students often come in thinking it’s okay to leave test databases open “just while developing.” Then we show them our wall of shame – real examples where that kind of thinking went south.
Common database security fails we’ve seen:
- Default passwords left unchanged
- Test instances exposed to the internet
- Authentication turned off for “convenience”
- Root access granted to every developer
Just last week, one of our students found an exposed database with millions of customer records – all because someone thought skipping authentication would speed up development. That’s the kind of mistake that gets companies in the news, and not in a good way. We teach our teams to treat every database like it holds the crown jewels.
The rule’s simple: no authentication, no access. Period. Sure, developers complain it slows them down, but we’d rather hear those complaints than explain to executives why their data’s showing up on the dark web. When every connection has to prove itself first, sleeping at night gets a whole lot easier.
Cloud Service Deployment Policies That Enforce Fail Safe Defaults
The cloud makes it way too easy to mess up. Our bootcamp students love clicking that “public access” button because it’s quick and easy. Then we show them the headlines about S3 buckets leaking millions of records, and suddenly they get real serious about security.
Common cloud mistakes we catch in training:
- Storage buckets set to public
- API endpoints without authentication
- Development environments exposed to the internet
- Security groups with “allow all” rules
Last quarter, a student caught a massive data leak at their company – turns out someone had made every single cloud resource public by default. The fix was simple: make everything private unless there’s a damn good reason not to. Yeah, developers grumble about the extra steps, but those steps save companies from becoming cautionary tales.
We teach our teams to treat cloud resources like they’re handling explosives. Keep everything locked down tight, triple-check before opening anything up, and always assume someone’s trying to break in. When security’s the default, not an afterthought, cloud deployments get a whole lot safer.[2]
Failsafe Defaults Enhance Security Posture and User Trust
Credit: Sparkitec
Secure defaults embed security upfront rather than after a breach occurs. This proactive stance prevents vulnerabilities instead of reacting to damage. When systems deny access by default, block unnecessary ports, and require authentication everywhere, they align with principles of secure defaults and fail safe design.
Fail safe defaults also reduces human error. By eliminating insecure options from the start, users can’t accidentally weaken security. This lowers one of the biggest causes of breaches: misconfiguration.
Users and organizations gain trust knowing their systems come hardened. Compliance with regulations is easier when default security settings protect data and privacy. Plus, addressing security during development reduces costs related to fixing breaches or vulnerabilities later.
Lastly, secure defaults simplify adoption. Users don’t have to wrestle with complicated setups, security is baked in, making safe operation the path of least resistance.
Examples and Best Practices for Implementing Fail Safe Defaults in Systems

Some practical examples of fail safe defaults include enabling multi-factor authentication from day one, disabling unnecessary services upon installation, and enforcing strong password policies without requiring users to configure them.
Designing software with secure defaults means embedding these settings at every lifecycle stage. Our teams encourage developers to think about what the safest default state is for every feature and enforce it.
Challenges do arise, balancing usability with security is tricky. But solutions exist: provide clear documentation, offer easy ways to request exceptions, and regularly update defaults to reflect new threats.
Fail safe defaults are not just a checklist item; they’re part of a comprehensive security architecture, and recognizing the importance of secure defaults ensures they remain central to development rather than an afterthought.
Conclusion
Setting fail safe defaults is about building systems that protect themselves first. It’s a simple idea with profound impact. We’ve seen that when systems start locked down, with minimal privileges and strict controls, they stand stronger against attacks. It’s a habit worth adopting for any organization serious about security.
Think about your own systems. Are they denying by default? Are firewalls blocking all ports unless you say otherwise? Are user accounts limited to what’s needed? If not, it’s time to rethink those defaults. Start with the basics and build your security from the ground up.
Ready to tighten things up? Don’t wait for a breach to remind you why the basics matter. Join our bootcamp and learn how to build systems that defend themselves from day one.
FAQ
How does implementing fail safe defaults improve security risk reduction and support secure defaults in real systems?
When we talk about implementing fail safe defaults, we mean starting with secure defaults that block access unless it’s clearly needed. This approach helps security risk reduction because no one gets extra privileges by accident. It sets the stage for better cybersecurity best practices, like default security policies, system hardening, and network security defaults. From secure default firewall settings to default access restrictions, the principle makes sure every door is locked before anyone decides to open it. That’s why a strong default security posture is often the most powerful shield.
Why are default security configurations and system security initialization so important in software security settings?
Default security configurations shape how a system behaves the first time it runs. Without strong system security initialization, weak default password security or missing user access controls can create easy targets. Secure-by-default design asks developers to set strict rules from the start, like secure default firewall settings, secure server configurations, and default encryption settings. Even secure IoT device configuration or secure hardware foundations depend on getting the defaults right. These choices define the system’s default security architecture and lower the chance of human error slipping through the cracks.
What role do secure configuration management and security by design play in reducing vulnerabilities?
Secure configuration management means keeping track of every default security policy, secure software deployment, and hardened default settings. When combined with security by design, the goal is to limit mistakes before they cause damage. Using secure development practices, CI/CD security integration, and DevSecOps best practices ensures that security checks are built into the process. Tools like automated security testing, vulnerability assessment defaults, and security configuration templates help find weak points early. Together, these practices support vulnerability mitigation and build stronger cybersecurity resilience.
How do default privacy settings and data protection defaults connect with secure user authentication?
Privacy and access go hand in hand. Strong default privacy settings and data protection defaults prevent oversharing. At the same time, secure user authentication, built on multi-factor authentication default and strong password policies, stops intruders from sneaking in. Secure session management, secure data sharing, and secure remote access balance usability with safety. When paired with secure access management, zero trust security model, and default access restrictions, these layers keep users safe. The real win is data breach prevention through secure network protocols, default TLS configurations, and default encryption keys that keep information locked down.
How do cloud security configurations and SaaS security defaults support cybersecurity resilience?
The cloud adds new challenges, which is why cloud security configurations and SaaS security defaults matter so much. Secure SaaS onboarding, secure software updates, and secure software distribution stop gaps before they widen. Features like default intrusion detection, default malware protection, secure logging settings, and default security monitoring build visibility into the system. Paired with security patches automation, security update automation, and default security alerts, the setup lowers risks tied to cybersecurity incident reduction. Even under the cloud shared responsibility model, providers and users rely on secure API gateways, secure firewall rules, and default compliance settings to stay resilient.
References
- https://en.wikipedia.org/wiki/Computer_security
- https://www.wsj.com/tech/cybersecurity/why-are-cybersecurity-data-breaches-still-rising-2f08866c

