
Small attack surfaces make a huge difference in cyber defense. Anyone who’s spent time in the trenches knows this truth – the fewer ways in, the better the odds of keeping attackers out. A training bootcamp’s experience has shown that it’s not just about plugging holes, we’ve got to stay on top of every access point. That means taking stock of what’s there, throwing out the junk, and keeping a close eye on who gets in. Constant vigilance doesn’t sound exciting, but it works.
Key Takeaways
- Map out every piece of hardware, software, and login point – you can’t protect what you don’t know about
- Cut the fat: kill unused services, shut down open ports, lock down system settings
- Stay on guard with tight access rules, watch everything closely, keep patches current
Constitutes the Attack Surface in an Organization
Security pros see it every day – the attack surface isn’t just one thing staring you in the face. Through years of running security checks at our bootcamp, we’ve found it’s more like a web of vulnerabilities. There’s the obvious stuff: computers, software, networks. Then there’s the sneaky parts: old programs nobody remembers, passwords left unchanged, ports sitting wide open for no good reason.
Some weak spots jump right out during audits, like exposed servers and routers that need attention. Others lurk in the background – that ancient version of Windows nobody bothered to update, Each piece has its own risk factors – is it running outdated code? Missing patches? Using real authentication?
Risk scoring changed everything for our security assessments. That database holding customer data with basic encryption? Way more critical than the printer in accounting. Numbers don’t lie – putting hard values on risks lets teams know exactly where to focus first. Been there, fixed that.
Analyze and Assess the Attack Surface Effectively
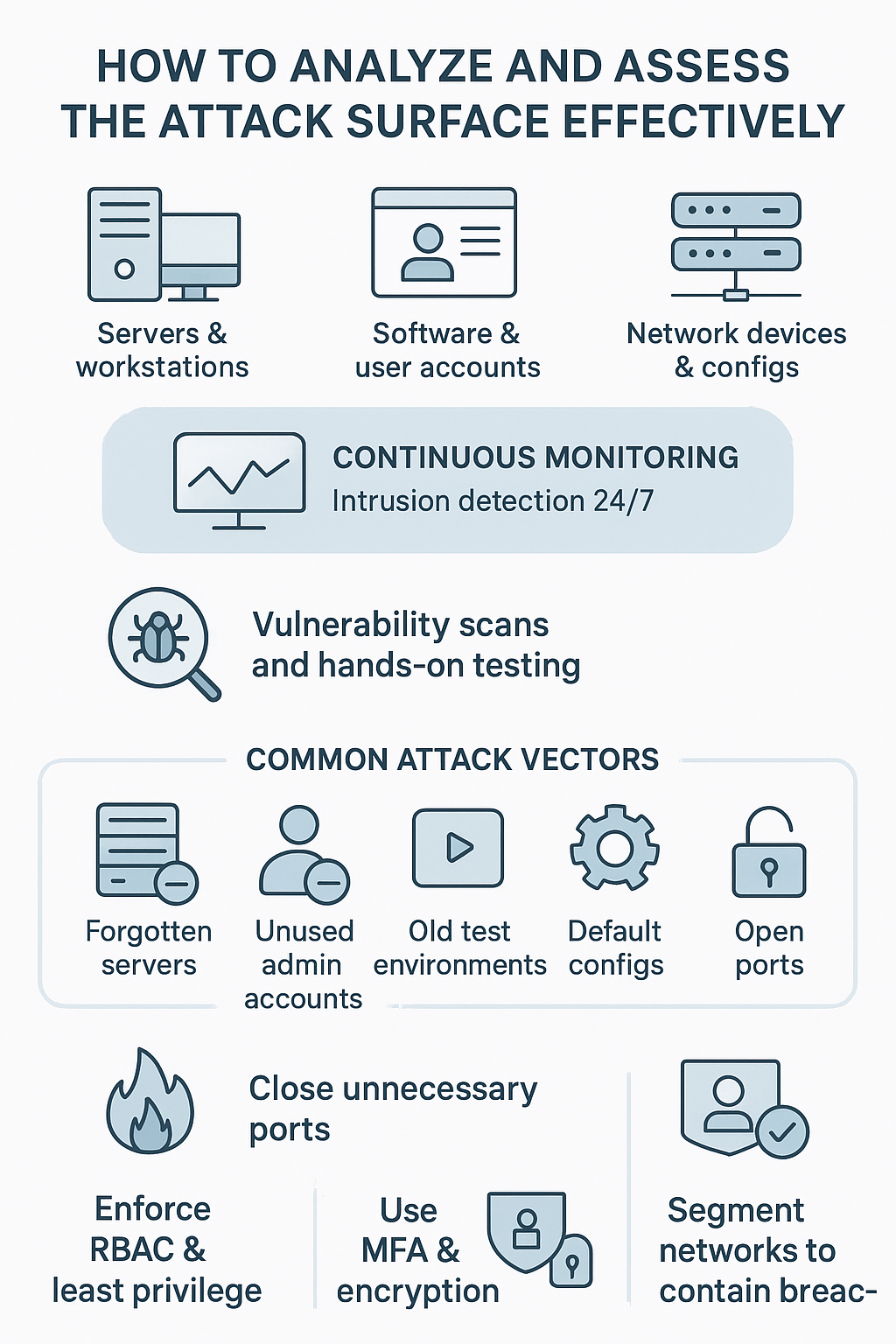
Getting a handle on security starts with knowing what’s actually out there. Here’s what every organization needs to track:
- Every server and workstation on the network
- Software running on each system
- Active user accounts and their privileges
- Network devices and their configurations
Playing “what if” with threats sounds paranoid, but it works. The team spends hours thinking like attackers, poking at weak spots, running vulnerability scans. Sometimes it’s automated tools doing the heavy lifting, other times it’s hands-on testing for misconfigured settings or outdated software that’s asking for trouble.
Nobody likes surprises in security. That’s why we’re always watching, always testing. New bugs show up, patches roll out (sometimes breaking things), people switch roles. Having those intrusion detection systems running 24/7 catches the weird stuff before it becomes a problem.
Methods Eliminate or Reduce Unnecessary Attack Vectors
The best defense? Getting rid of stuff you don’t need, and applying proven attack surface reduction techniques that strip away weak points before attackers can exploit them. Common problems we see in every audit:
- Forgotten servers running ancient software
- Unused service accounts with admin rights
- Old test environments nobody remembered to remove
- Default configurations nobody bothered to change
Those network ports sitting open drive security folks crazy. Each one’s like a window left unlocked. Setting up tight firewall rules takes time, and yeah, sometimes people complain when their “emergency backup” port gets closed. But that’s the point – if it’s not essential, it’s gone.
System lockdown isn’t exciting work, but it matters. Ditching those factory passwords, setting up proper configs, turning off fancy features nobody uses. Our students learn quickly that change control isn’t just paperwork – it keeps systems from slowly drifting into dangerous territory.
Restrict and Control Access to Minimize Exposure
Access control is where security often succeeds or fails. We adopted role-based access control (RBAC) combined with the principle of least privilege (PoLP) to ensure users and applications only get the permissions absolutely necessary. This reduces the risk of accidental or malicious misuse.
Strong authentication mechanisms, especially multi-factor authentication (MFA), add another layer of defense. Even if passwords are compromised, the additional verification step stops many attacks. Encryption of sensitive data, both at rest and in transit, ensures that even if data is intercepted or accessed, it remains protected.[1]
Network segmentation and micro-segmentation limit the damage if an attacker breaches one part of the network. By isolating subnets and controlling communication between workloads, lateral movement becomes harder. This isolation buys time to detect and respond before attackers reach critical systems.
Continuous Monitoring and Patch Management Play
We quickly learned that minimizing the attack surface is not a one-time project. Continuous monitoring is essential. Intrusion detection systems and security information and event management (SIEM) tools help spot suspicious activity early, before damage occurs.
Alongside monitoring, timely patch management is a must. Vulnerabilities in software are discovered constantly. Delaying updates opens a window for attackers. Our team established strict policies and automation where possible to ensure rapid patch application.
The zero trust model underpins this approach: assume no implicit trust, whether inside or outside the network. Every access request must be verified, and access granted only on necessity and identity confirmation.[2]
We also found that training employees on phishing, social engineering, and cyber hygiene reduces the human attack surface. People are often the weakest link, so regular awareness programs help close that gap.
Asset Management Support Attack Surface Reduction
Credit: a cybersecurity training resource
Keeping an up-to-date asset inventory is the foundation of attack surface management, especially when it comes to reducing application attack surface across systems that run business-critical software. We tag and track each device and application through its lifecycle, knowing exactly what’s active, deprecated, or retired.
Regular configuration reviews help us maintain security benchmarks and detect unauthorized changes. Configuration drift, when systems slowly move away from secure baselines, can open backdoors. Detecting this early through tools and audits is vital.
When changes do occur, incident response plans kick in to investigate and remediate quickly. Asset management, combined with configuration control, ensures we don’t lose track of our security posture over time.
Implement a Holistic Multi-Layered Approach to Minimize Attack Surface
From our experience, no single measure works alone. Minimizing the attack surface demands a coordinated, multi-layered strategy grounded in attack surface reduction best practices that guide every step of the process. Identification, elimination, restriction, and continuous monitoring must all work together.
We set up feedback loops to reassess and improve processes regularly, adapting to new threats and technologies. Lining up security rules with what the company can handle and the laws it must follow makes the work clear and useful. It keeps people from doing extra steps that don’t matter and makes sure the real risks are covered.
Automation and orchestration streamline routine tasks like patching, scanning, and access reviews. This lets the team focus on more complex threats and strategic improvements.
When these layers work side by side, there are fewer weak spots for attackers to find. At the same time, the company becomes tougher and better able to bounce back from trouble.
Conclusion
Minimizing your attack surface is a continuous challenge but one worth the effort. Start by knowing what you have, cut out what you don’t need, limit who can do what, and keep watching. Security isn’t static, and neither should your approach be.
Keep adapting, keep tightening, and you’ll reduce the openings attackers can exploit. If you haven’t already, consider running a full attack surface audit today. It’s the first step toward making your defenses a lot harder to breach. Join our Attack Surface Audit Bootcamp
FAQ
How does attack surface reduction help with cyberattack prevention and improve security posture?
Attack surface reduction is about shrinking the number of ways an attacker can break in. When fewer doors are open, cyberattack prevention gets easier. A smaller digital attack surface makes it tougher for hackers to move around. Pairing this with a strong security posture, like regular patch management, software updates, and firewall configuration, keeps defenses sharp. It’s not about being perfect, but about cutting down risks and making attacks harder to pull off.
What role do vulnerability assessment, threat modeling, and risk prioritization play in minimizing network vulnerability?
Vulnerability assessment shows the weak spots. Threat modeling helps picture how attackers might strike. Risk prioritization tells you what to fix first. Together, they create a clear picture of network vulnerability. This makes it easier to build a smart cybersecurity strategy. By combining patch management, anomaly detection, and intrusion detection with regular asset inventory, you can tackle the biggest threats before they cause real harm.
How do physical attack surface, digital attack surface, and human attack surface connect in reducing exposure to threats?
The digital attack surface covers servers, apps, and cloud systems. The physical attack surface involves hardware, offices, and devices. The human attack surface deals with phishing, weak passwords, and social engineering defense. Each one can open doors for attackers. Using multi-factor authentication, security awareness training, and phishing prevention shrinks the human attack surface. Adding endpoint security, encrypted communication, and secure system configuration helps reduce both digital and physical attack surfaces.
Why are zero trust security, least privilege access, and identity and access management key for remote access security?
Zero trust security works on the idea of “never trust, always verify.” Least privilege access makes sure people only get the access they truly need. Identity and access management helps track and enforce those rules. When combined with remote access security measures like VPN technology, user privilege review, and remote user verification, you limit insider threat risks and improve breach prevention. These steps close security gaps that attackers often exploit.
How do network segmentation, micro-segmentation, and internal network isolation reduce threat exposure?
Network segmentation and micro-segmentation break networks into smaller zones so attackers can’t move freely. Internal network isolation takes this further by walling off sensitive areas. Together, these approaches drive threat exposure reduction. Add intrusion detection, port management, and access control policies to block common attack vectors. With endpoint protection, malware defense, and strong firewall configuration, you limit lateral movement inside systems and improve overall operational resilience.
What practices support secure coding, application security, and third-party vulnerability management?
Secure coding and application security stop problems before they start. Strong web form validation and SQL injection prevention close loopholes in apps. Secure uploads and data anonymization also protect sensitive files. When using outside vendors, third-party vulnerability management helps catch weak spots. Pair that with SSL encryption, HTTPS enforcement, client certificate authentication, and IP restrictions to keep data safe. Regular software lifecycle management and legacy software management also play a big role.
Why do patch management, vulnerability patching, and software hardening matter for system safety?
Hackers often target unpatched systems. Patch management and vulnerability patching close those gaps before attackers get in. Software hardening and system hardening techniques reduce weaknesses that linger in old code or unused features. Redundant services removal and configuration management also cut down unnecessary risks. Adding data encryption, secure cloud configuration, and digital asset protection strengthens defense. These steps are basic cyber hygiene habits that boost business continuity and operational resilience.
How do incident response planning and security monitoring help with threat actor defense?
Even with the best defenses, things can go wrong. Incident response planning lays out what to do if there’s a breach. Security monitoring, anomaly detection, and intrusion detection help spot attacks early. This builds operational resilience and keeps business continuity in place. Pairing these with data loss prevention, attack vector management, insider threat mitigation, and secure system configuration creates a strong line of threat actor defense. The goal is quick recovery, not just prevention.
References
- https://en.wikipedia.org/wiki/D._Richard_Kuhn
- https://en.wikipedia.org/wiki/Security_awareness

