
Software breaches hit most dev teams at the worst times, often due to basic oversights. Our secure coding bootcamp sees it happen repeatedly, teams rushing features without considering attack vectors. That’s where threat modeling comes in. By spotting weak points early during development, teams dodge costly fixes and potential data leaks.
Through our workshops, we’ve watched developers transform their approach by working security measures into their coding workflow. The process requires thinking like hackers, but it works. Keep reading as we break down practical ways to weave threat modeling into your dev cycle.
Key Takeaways
- Threat modeling helps identify cybersecurity threats early by analyzing attack vectors and system vulnerabilities.
- Secure coding practices, combined with threat modeling, form the foundation for mitigating risks and strengthening software security.
- Using structured methodologies like STRIDE and PASTA guides clear risk assessment and prioritization for better security controls.
Why Threat Modeling Matters
Cyber attacks aren’t slowing down. Studies say cybercrime damages will hit $10.5 trillion annually by 2025. In fact, the average cost of a single data breach in 2024 was about US $4.88 million. (1) That’s not just numbers, it’s real businesses losing data and trust every day. Threat modeling is the proactive step to catch threats before they exploit your system.
When you think about it, it’s kind of like locking your doors before someone tries to break in. We’ve seen how teams who prioritize threat modeling in SDLC reduce costly breaches and keep their security architecture tighter. It’s not just IT’s job either. Business impact is huge. Losing customer data or downtime can shatter reputations and profits.
What is Threat Modeling?
Threat modeling is a structured process that lets you imagine how your system could be attacked. It helps you identify who might target you, known as threat agents, and the possible attack vectors they might use. Understanding this helps define security requirements and build defenses tailored to your specific risks.
At its core, threat modeling means building a mental map of your system’s attack surface, system vulnerabilities, and data flows. From PwC’s 2024 Global Digital Trust Insights survey: the proportion of businesses that experienced a data breach of more than US $1 million increased from 27% to 36%. (2)
We use tools like data flow diagrams to visualize how information moves, which spots are most vulnerable. This clarity helps everyone, developers, security teams, stakeholders, speak the same language.
The benefits have been clear in our experience. Early identification of risks means we can focus resources on what really matters. It improves communication and aligns teams on security goals. It’s a foundation, not a one-off task.
Key Steps in Threat Modeling: A TL;DR Summary
| Step | Description |
| 1. Define Scope | Identify the system, application, or process to be analyzed. |
| 2. Identify Threats | Brainstorm potential threats based on attacker motivations and vulnerabilities. |
| 3. Assess Risks | Analyze the impact of identified threats and existing/needed security controls. |
| 4. Prioritize & Document | Prioritize threats based on risk level and create mitigation plans. |
Step 1: Define the Scope (What Are We Working On?)
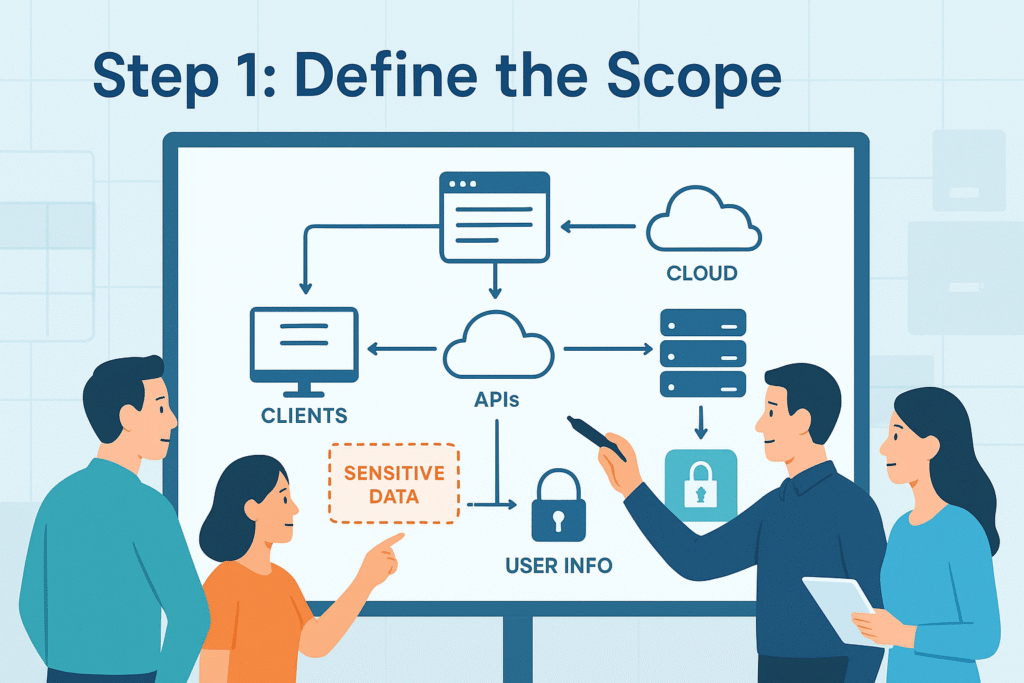
Understanding your system’s boundaries is the first step. Whether it’s a single web app or a complex network, you need to know what you’re protecting. Drawing data flow diagrams helps visualize how data moves between components, revealing critical assets and sensitive info.
We often start with a web application handling user data. Visualizing its modules, databases, and external services clarifies where the attack surface lies. Without this clear scope, threat identification becomes guesswork.
- Identify components: servers, clients, APIs.
- Map data flow: where data enters, moves, and is stored.
- Pinpoint sensitive information: personal data, credentials.
This sets the stage for identifying threats accurately.
Step 2: Identify Threats (What Can Go Wrong?)
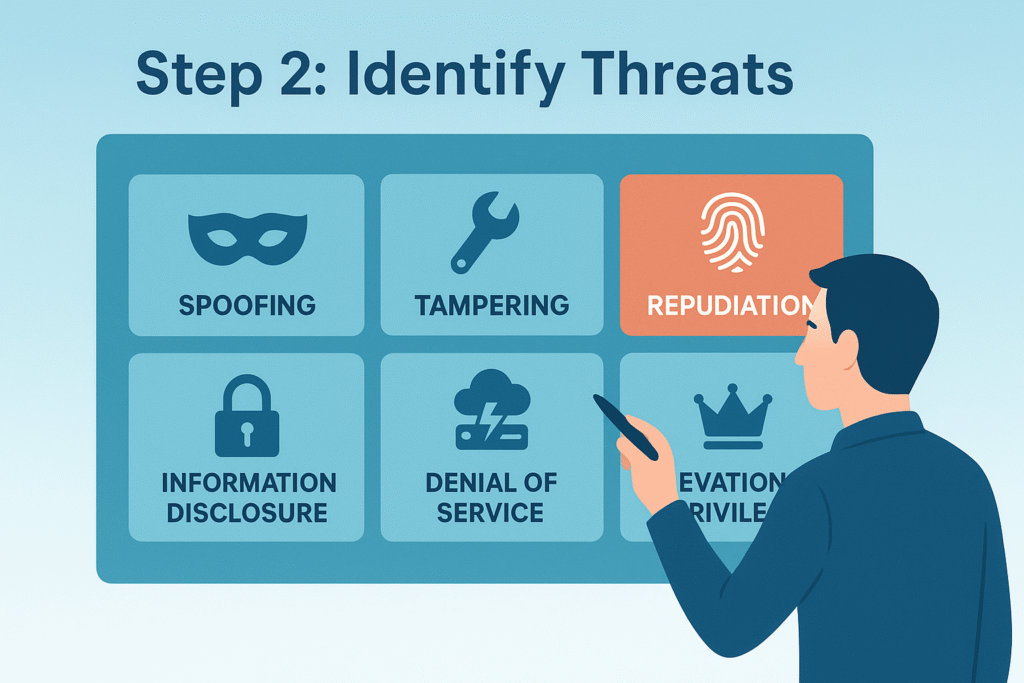
Here’s where mindset shifts to the attacker’s perspective. Using structured brainstorming methods like STRIDE threat modeling, you list potential threats:
- Spoofing: pretending to be someone else.
- Tampering: altering data or code.
- Repudiation: denying performed actions.
- Information Disclosure: leaking sensitive data.
- Denial of Service: disrupting availability.
- Elevation of Privilege: gaining unauthorized access.
In practice, we see threats like SQL injection or cross-site scripting come up often. But it’s not just about common vulnerabilities. Considering insider threats or cloud security threats broadens the picture.
We find that pairing this step with secure coding practices helps. When developers know which threats exist, they write code that anticipates and blocks attack vectors early on.
Step 3: Assess Risks and Mitigation Capabilities
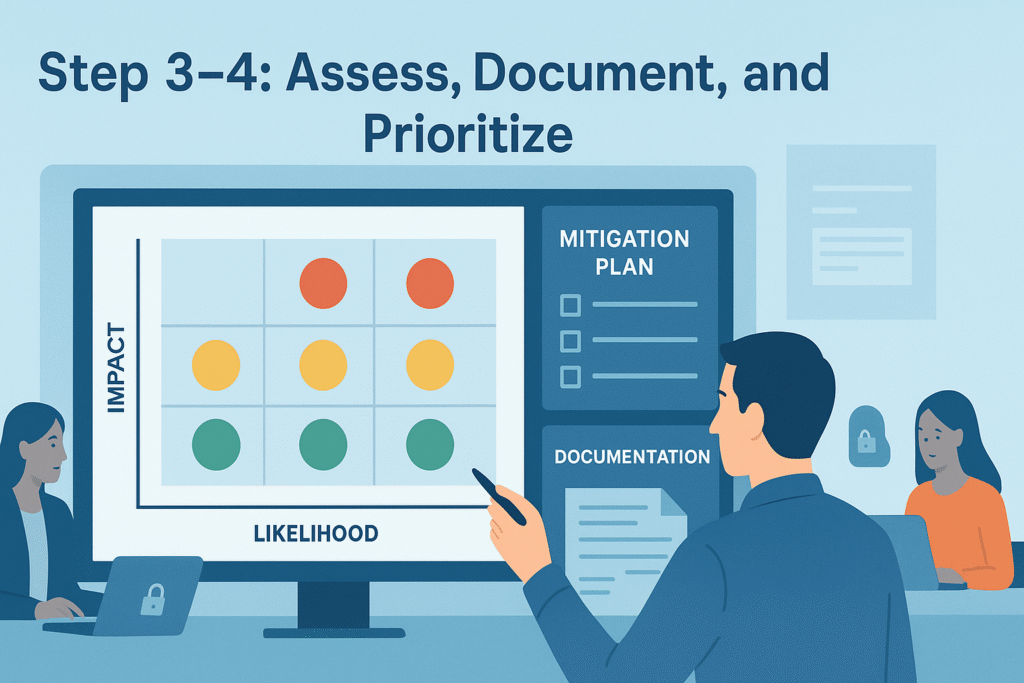
Not all threats are equal. Some might be highly unlikely or have low impact, others could cripple your system. Risk assessment weighs the likelihood and potential damage.
We look at:
- How vulnerable each threat is to exploitation.
- What security controls are already in place.
- What additional countermeasures we need.
For example, input validation is a simple yet effective control against injection attacks. It’s part of our secure software development approach. Vulnerability scanning tools assist in this phase, highlighting system vulnerabilities and attack surface weaknesses.
The goal is to create a prioritized list of threats that need urgent attention.
Step 4: Document and Prioritize Threats
Documentation isn’t glamorous but it’s essential. Writing down threat scenarios, risk levels, and mitigation strategies makes the threat model a living document.
Our team uses risk matrices to rank threats by severity and likelihood. This helps focus efforts on high-risk areas first. We also create threat model templates to keep things consistent across projects.
A thorough threat model report supports risk management by informing security audits and penetration testing plans. It’s a roadmap for ongoing security improvements.
Common Threat Modeling Methodologies

Different methodologies suit different needs:
- STRIDE is popular for categorizing threats into six clear types, making brainstorming systematic.
- PASTA focuses on aligning threat analysis with business objectives and risk-centric views.
- OCTAVE dives into organizational risk and assets rather than just technical aspects.
- Quantitative Threat Modeling uses data and metrics for risk quantification, helpful in large complex environments.
We like mixing STRIDE with elements of PASTA because it covers both technical and business perspectives. The key is picking what works for your team’s workflow.
How to Integrate Threat Modeling into Your Workflow
Credit: CyberSecurityTV
Threat modeling shouldn’t be a one-time checkbox. It works best when integrated early in the software development lifecycle (SDLC). That means starting during design and continuing through updates and patches.
Regularly revisiting and updating the threat model as systems evolve keeps security posture current. Collaboration between developers, security experts, and operations teams ensures everyone stays aligned.
Using threat modeling tools for developers can help document and visualize threats faster. But don’t let tools replace critical thinking. We always pair tools with team discussions and secure coding practices.
Making Threat Modeling Work for Your Team
From our experience, threat modeling is most effective when it becomes part of your team’s culture, not just a security team task. When developers understand why security matters, they write better code. When product owners see the business impact, they fund necessary controls.
Balancing secure coding with threat modeling creates a cycle of continuous improvement. We catch threats early, fix them in code, test, and learn. This reduces the attack surface and builds trust in the software.
FAQ
What are the first steps to start threat modeling effectively?
When getting started threat modeling, begin by understanding your system and mapping how information moves using data flow diagrams. This helps you spot attack vectors and system vulnerabilities early. Then, apply threat identification techniques like STRIDE methodology to find security threats and start shaping a secure design from day one.
How do I know which cybersecurity threats matter most?
You can use risk assessment and threat prioritization to rank cybersecurity threats by impact and likelihood. A simple risk evaluation helps you focus on the biggest risks first. Combine vulnerability analysis, threat intelligence, and business impact analysis to see how security threats could affect your software security or operations.
How can threat modeling fit into the software development process?
Integrate threat modeling into your secure software development or DevSecOps routine. Start early in design using threat modeling tools, and revisit them during updates. Include risk analysis, threat detection, and countermeasures planning in your workflow. This keeps your security posture strong and aligns your security requirements with real-world threats.
What methods can I use for structured threat analysis?
Use structured methodologies like STRIDE methodology or the PASTA framework for consistent threat analysis. These help you document threat scenarios, assess risk treatment options, and choose security controls. You can also explore attack trees, threat taxonomy, and threat modeling best practices to strengthen your threat management process.
How can I maintain and improve my threat models over time?
Treat threat modeling as a lifecycle, not a one-off task. Regular threat model review, security audit, and vulnerability scanning help catch new threats. Update your threat model documentation as the threat landscape evolves. Use insights from penetration testing, threat research, and cloud security threats to improve your security by design approach.
Conclusion
Getting started threat modeling might feel overwhelming at first. But it’s really about asking the right questions: What are we protecting? Who might attack? How do they do it? What can we do to stop them? Answering these helps keep your software safer, and your team more confident.
Take the first step by sketching your system’s data flows. Next, gather your team to brainstorm threats using STRIDE or your preferred method. Then assess risks honestly and plan your mitigations. Don’t forget to document everything, it’s your security compass.
The sooner you start, the better your chances of staying ahead of hackers. Keep secure coding front and center, we’ve found it to be the best defense paired with threat modeling. Your software’s security depends on the choices you make today.
Ready to strengthen your team’s secure coding skills? Join the Secure Coding Practices Bootcamp, a hands-on, expert-led course that helps developers master real-world techniques like input validation, secure authentication, encryption, and safe dependency management. In just two days, you’ll gain practical experience, labs, and certification to help you build safer software from day one.
References
- https://wp.table.media/wp-content/uploads/2024/07/30132828/Cost-of-a-Data-Breach-Report-2024.pdf
- https://www.pwc.com/bm/en/press-releases/pwc-2024-global-digital-trust-insights.html

