Developers often neglect security until after a breach occurs, we’ve watched it happen too many times. Our team has spent years training developers to weave security directly into system design, not bolt it on later. The fundamentals haven’t changed much: careful threat assessment, restricted access controls, and secure coding habits still form the bedrock.
Yet modern threats keep evolving, pushing systems in new ways. Many breaches trace back to configuration or design oversights that a robust security architecture might have mitigated. At our bootcamp, developers learn battle-tested approaches for building resilient systems that stay secure under pressure. Ready to develop with security-first mindset? Let’s explore how.
Key Takeaways
- Secure coding practices form the foundation of any secure design architecture, reducing vulnerabilities early.
- Frameworks like TOGAF and SABSA help integrate security aligned with business objectives and risk management.
- Core principles such as least privilege, defense in depth, and encryption guide the creation of resilient systems.
The Importance of Secure Design
Security often gets tacked on as an afterthought. But this approach leaves systems vulnerable to exploits that could have been prevented. We’ve learned this the hard way through incidents where security gaps caused data loss and downtime. According to studies, around 60% of breaches involve known but unpatched vulnerabilities or design oversights. (1)
Integrating security from the start saves time, reduces costs, and builds trust with users. It also means fewer surprises later when compliance audits or penetration tests reveal glaring flaws. We emphasize secure coding practices because they’re the first line of defense in minimizing vulnerabilities before systems go live.
Embedding these practices early is vital to a strong secure design principles overview, ensuring safety is built in from day one.
What is Secure Design Architecture?
Secure design architecture means embedding security principles, controls, and best practices directly into the design of systems, applications, and networks. (2) Its purpose is simple: minimize vulnerabilities and protect sensitive data throughout the system lifecycle.
Why does this matter? Because a system designed without security in mind is like building a house without locks or alarms. It invites threats, both external and internal, that can compromise data confidentiality, integrity, and availability.
Secure Design Architecture Frameworks
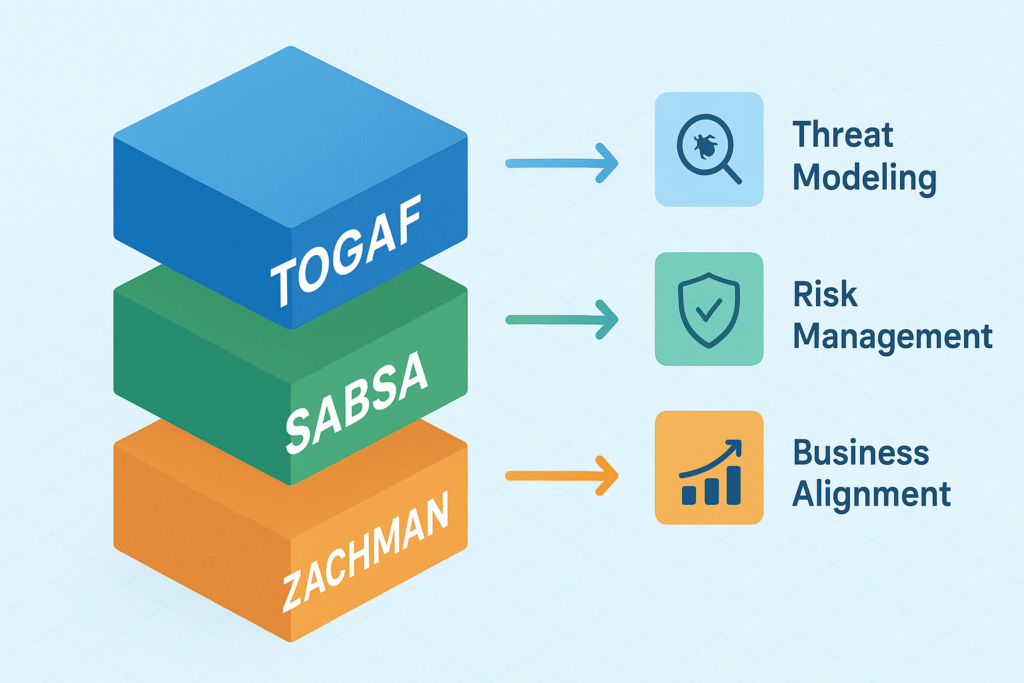
We often turn to well-established frameworks to guide secure architecture development. These frameworks offer structured approaches that help us build security in from the ground up.
TOGAF (The Open Group Architecture Framework)
TOGAF integrates security into most phases of architecture development. It encourages early threat modeling, enforces least privilege access, and supports continuous monitoring to spot anomalies fast. This framework promotes a holistic view, ensuring security is not isolated but part of the entire ecosystem.
Start by incorporating threat modeling workshops during initial design sprints to identify risks early.
SABSA (Sherwood Applied Business Security Architecture)
SABSA aligns security architecture tightly with business objectives. It focuses on risk management and integrates security across all business processes. We appreciate SABSA because it drives risk-based decisions rather than checkbox compliance, making security relevant and practical.
Use SABSA to map business risks directly to security controls, ensuring every measure has a clear purpose.
Zachman Framework
Though broader than just security, Zachman’s multiple perspectives cover all organizational aspects, including security. This comprehensive coverage helps avoid blind spots by looking at architecture through different lenses, from business goals to technical implementation.
Apply Zachman’s views to ensure security considerations are present at every organizational level.
Core Principles of Secure Design
Credit: Tom Olzak
After frameworks, it’s the core principles that really shape secure systems. These principles align closely with the core principles of secure system design that emphasize minimizing permissions and layering protections to reduce risk.
Threat Modeling
Identifying threats early isn’t just a checklist item, it’s a mindset. We find that incorporating threat modeling at the design phase helps avoid costly redesigns later. It involves thinking like an attacker and anticipating where systems might fail.
Use tools and templates to document potential threats and mitigation strategies collaboratively.
This approach complements a thorough secure design review checklist, which guides teams to verify access controls, defaults, and threat coverage systematically.
Least Privilege
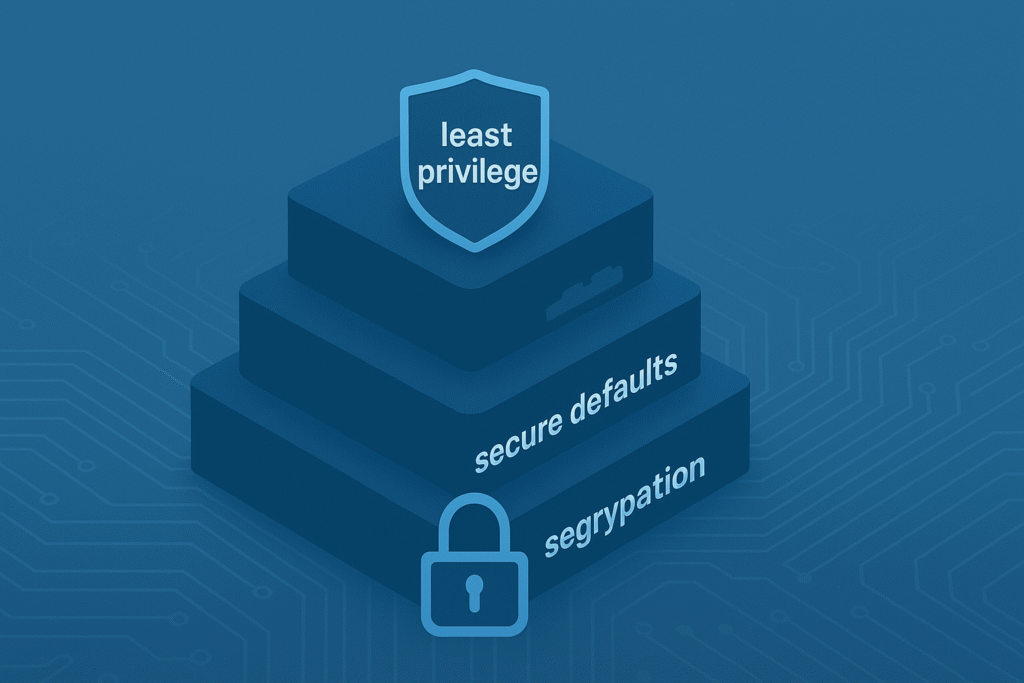
Giving users and systems only the access they absolutely need reduces the attack surface. We regularly audit permissions to prevent privilege creep, which can open doors to exploitation.
Implement role-based access control (RBAC) and review it periodically.
Defense in Depth
Relying on a single security control is risky. Instead, layering controls, firewalls, multifactor authentication, encryption, monitoring, creates multiple hurdles for attackers.
Combine network segmentation with secure authentication to limit lateral movement.
Secure Defaults
Systems configured securely out-of-the-box prevent common mistakes. We avoid default passwords, open ports, or permissive settings that invite trouble.
Fail Securely
When failures happen, systems must fail in a way that does not expose vulnerabilities. For example, if a service crashes, it should deny access rather than open it unintentionally.
Segmentation and Isolation
Separating critical components and sensitive data limits risk spread. We have seen how network segmentation can contain breaches and protect vital assets.
Encryption Everywhere
Encrypting data at rest and in transit is non-negotiable. Strong cryptography combined with careful key management ensures data confidentiality and integrity.
Identity and Access Management (IAM)
Robust IAM practices ensure proper authentication, authorization, and auditing. We integrate multifactor authentication and continuous monitoring to keep access secure and traceable.
Secure Design Patterns and Strategies for Applications
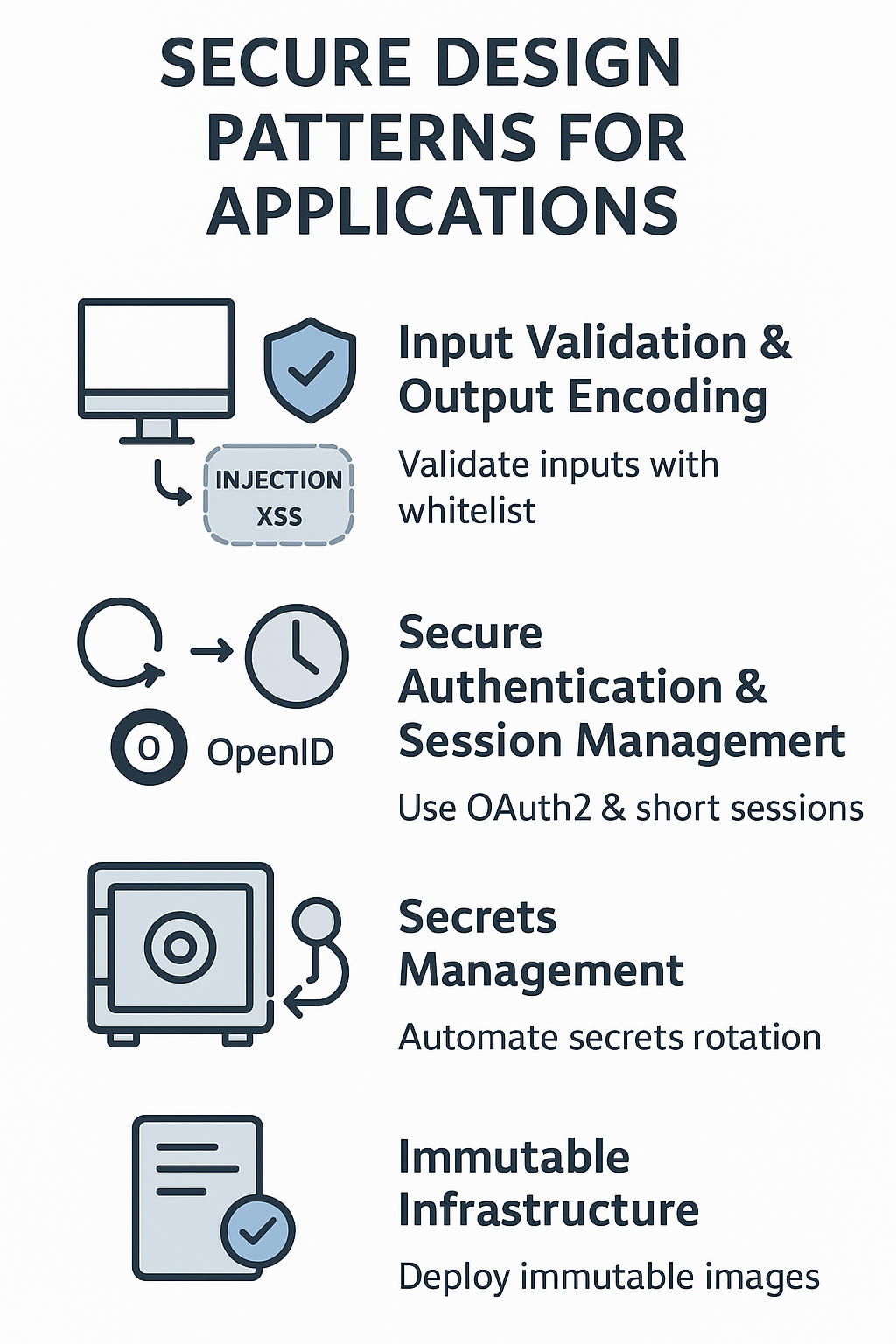
Concrete strategies help translate principles into code and configurations.
Input Validation and Output Encoding
Validating every input at both client and server prevents injection attacks that exploit unchecked data. Output encoding ensures data is safely rendered to avoid cross-site scripting.
Adopt a whitelist approach for input validation to accept only known good data.
Secure Authentication and Session Management
Using industry standards such as OAuth2 and OpenID Connect avoids the pitfalls of custom-built authentication, which often introduces flaws. Secure session management protects against hijacking and replay attacks.
Implement short session lifetimes combined with refresh tokens to balance security and usability.
Secrets Management
Hardcoding credentials or keys is a recipe for disaster. Instead, we use centralized vaults and rotate secrets regularly to minimize exposure.
Automate secret injection during deployment to avoid manual handling.
Immutable Infrastructure
Deploying version-controlled, pre-approved system images helps prevent configuration drift and unauthorized changes. This approach boosts consistency and security.
Continuous Monitoring
Designing systems for ongoing assessment lets us detect and respond to incidents swiftly. SIEM integration and automated alerts ensure visibility around the clock.
FAQ
What is secure design and how does it shape modern security architecture?
Secure design means planning systems to resist attacks from the start, not patching later. It blends security architecture, risk management, and secure coding. Using principles like least privilege, defense in depth, and threat modeling, teams prevent weaknesses before deployment. This proactive design mindset helps organizations build safer, more reliable digital environments.
How do frameworks like TOGAF security and the SABSA framework guide secure system design?
Frameworks such as TOGAF security, SABSA framework, and Open Security Architecture provide structured methods to connect business goals with technical controls. They emphasize security by design, risk assessment, and security governance. Following these frameworks helps teams apply consistent security policies, validate controls, and ensure compliance across every stage of secure system design.
Why are principles like defense in depth and secure defaults vital in secure software development?
Defense in depth and secure defaults make systems resilient when one layer fails. Combining network segmentation, firewall configuration, and intrusion prevention limits damage. Secure defaults reduce misconfiguration risks. Together with vulnerability management and patch management, these principles ensure security patterns protect data confidentiality, integrity, and availability from evolving threats.
How do identity and access management and zero trust architecture improve data security?
Identity and access management, paired with zero trust architecture, uses multifactor authentication, authorization, and separation of duties to verify every user and device. This model assumes no implicit trust. Combined with secure authentication protocols, encryption, and secure session management, it protects data flow, prevents privilege escalation, and strengthens secure network design overall.
What practices support continuous monitoring and effective incident response?
Continuous monitoring tracks vulnerabilities through SIEM integration, secure logging, and audit trails. When incidents occur, rapid response depends on clear security policies and automation. Practices like security orchestration, secure configuration management, and endpoint security reduce risks. These measures uphold data integrity and availability while improving overall security compliance and validation.
Conclusion
From our experience, secure design is a continuous process, not a one-time task. It requires collaboration across teams, early integration of secure coding practices, and a firm commitment to principles like least privilege and defense in depth. Frameworks like TOGAF and SABSA provide useful blueprints but real security comes from persistent application and vigilance.
When you embed security from the start, you reduce costly patches, improve compliance, and most importantly, protect your users and data from harm.
If you’re building or managing systems, invest the time early to adopt secure design architecture principles. You’ll thank yourself later when incidents are fewer and easier to manage.
For a practical next step, review your current design approach and identify where secure coding can be reinforced. Engage your team in threat modeling exercises and ensure you have least privilege controls in place. Over time, these efforts compound into a resilient security posture you can rely on.
For a hands-on way to build this capability, join the Secure Coding Practices Bootcamp, a two-day, expert-led program that turns developers into secure builders through practical, real-world coding sessions.
References
- https://www.itgovernance.co.uk/blog/would-you-know-if-your-organisation-had-suffered-a-data-breach
- https://keystonecorp.com/cybersecurity/it-security-architecture-frameworks-best-practices-phases

