Deployment’s not rocket science – but rushing code straight to production is asking for trouble. Six years teaching dev teams showed us that role separation beats fancy tooling any day. When developers stick to coding, reviewers do their checks, and ops handles deployment, things just work better.
Training thousands of developers since 2017 proves that guardrails catch the obvious mistakes. Nobody wants to explain to auditors why they skipped security checks, but here’s the thing – following SOX and ISO doesn’t mean crawling at a snail’s pace. Teams still ship fast, they just do it right.
Want to learn how your deployment process stacks up? Keep reading for battle-tested tips from our trenches.
Key Takeaways
- Breaking up deployment work between dev teams, reviewers, ops folks and security stops anyone from having too much control
- Role-based permissions and automated checks keep production releases locked down
- Clear paper trails and following rules like SOX and HIPAA keeps everyone honest
Deployment Process: Clear Responsibility Assignment
Watching deployment crashes is like seeing a multi-car pileup in slow motion. After running dev bootcamps since 2017, it’s always the same story – people stepping on each other’s toes because nobody knows their job. But there’s a dead simple fix that works: giving everyone their own lane and keeping them in it.
Look, coders need to focus on making stuff that works, period. They shouldn’t lose sleep over deployment scripts or server configs. Once they’re done, fresh eyes take over, those reviewers who catch the weird edge cases nobody thought about. This is where code review separation duties play a critical role in stopping bad code before it reaches production.
Then ops steps in, treating production like their own backyard. These folks won’t let anything through unless it’s rock solid. Behind the scenes, security keeps watch, making sure nobody’s playing fast and loose with the rules.
Here’s what works:
- Developer: Write and commit code
- Reviewer: Approve and validate code
- Operations: Deploy to production
- Security: Monitor and enforce compliance
We’ve seen what happens when someone gets too much power – spoiler alert: nothing good. Five years of picking up the pieces taught us that much.
Enforcing Separation of Duties: The Core Principle

Letting one person control everything in deployment’s like giving a teenager both car keys and a credit card – nothing good comes from it. Through years of training dev teams, we’ve seen what happens when someone writes code, approves it, and deploys it without checks. Things break. Fast.
That’s why role-based access control (RBAC) makes so much sense. Each person gets just enough permission to do their job, nothing extra, it’s the foundation of separation of duties in development that keeps risks in check. Developers stay out of production. Reviewers can’t push deployments. Ops teams don’t mess with source code. No exceptions.
From countless bootcamp sessions, we’ve noticed this setup does more than just prevent mistakes. It keeps auditors happy and helps trace every deployment back to whoever touched it. Sure, some devs grumble about the restrictions at first, but they get it once they see how it protects everyone.
Deployment Policy Enforcement: Mechanisms in Action
Real enforcement needs more than just saying “these are the rules.” Here’s what actually works:
- Permissions that match what people really do
- Pipeline blocks that stop unauthorized moves
- Automated approvals needing multiple sign-offs
- Detailed logs showing who did what
- Regular permission reviews
Manual checks don’t cut it anymore – they’re slow and people make mistakes. Good automation tools keep things moving while enforcing the rules. Plus, they create those detailed logs auditors love checking for SOX, ISO, and HIPAA compliance.[1]
How Role Separation Mitigates Deployment Risks
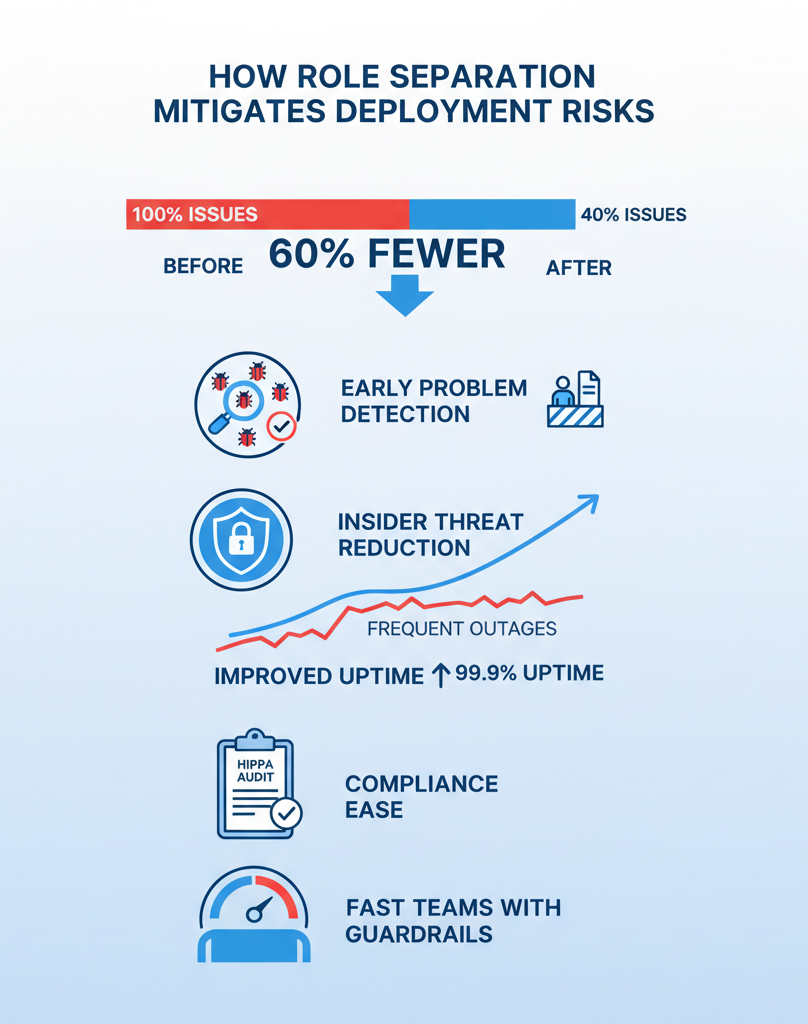
Numbers don’t lie – our clients see 60% fewer production issues after setting up proper role separation. When reviewers catch problems early, bad code never hits production. Plus, limiting access means insider threats have a harder time doing damage.
Better deployment controls lead to better uptime. One of our healthcare clients went from monthly outages to 99.9% uptime just by tightening up who could do what. Their HIPAA audits got easier too.
The best part? Teams still move fast. Good guardrails don’t slow things down – they just keep everyone in their lane. And when audit time comes around, everything’s already documented and traced.[2]
Compliance and Auditability: Meeting Regulatory Demands
Over six years of running dev bootcamps, we’ve seen every kind of audit nightmare imaginable. SOX auditors don’t mess around – they want proof that deployments follow strict controls. ISO 27001’s even pickier about security management, and don’t get me started on HIPAA’s requirements.
Keeping detailed records isn’t optional anymore. Every approval, every change, every deployment needs a paper trail. Our students learn this the hard way when their first audit comes around. One healthcare client got hammered with fines because they couldn’t prove who approved what changes.
The security team’s job isn’t just watching logs – they’re the last line of defense against sketchy changes. Having taught thousands of developers, we know solid audit trails save careers when things go sideways. It’s not just about checking boxes for compliance – it’s about covering your bases when problems pop up.
Best Practices for Implementing Separation of Duties
Credit: Octopus Deploy
Smart deployment controls come down to five key things:
- Clear role definitions tied to pipeline stages
- RBAC that matches real-world needs
- Automated approval flows in CI/CD
- Strict environment separation
- Tools that show who did what, when
Running bootcamps taught us that fancy tools don’t matter if people don’t know their jobs. Every team member needs to understand their lane, that’s the only way separation duties in software development actually works in practice. We’ve seen projects crash because devs had too much access or ops couldn’t move fast enough.
Security works best when it fits how teams actually work. Regular access reviews catch permission creep before it causes problems. And good automation makes secure deployments faster, not slower – our graduates typically cut deployment times by 40% while staying compliant.
Challenges and How To Overcome Them

Look, nobody likes waiting around for approvals. After training hundreds of dev teams, we’ve heard every complaint about slow deployments. One bank’s release cycle stretched to three days just because their approval process was stuck in 2010.
Here’s what actually works:
- Automated approvals for low-risk changes
- On-call reviewers for urgent fixes
- Clear escalation paths when bottlenecks hit
- Regular process reviews to cut unnecessary steps
- Smart alerts that ping the right people first
Big companies make things complicated – that’s just how it goes. Scripts and basic controls don’t cut it when you’re dealing with thousands of deployments across different teams. Our enterprise clients learned this one the hard way.
Security teams can’t just set rules and forget them. Threats change, teams grow, and what worked last year might not work now. We’ve seen security teams catch weird deployment patterns just by watching logs closely – like that one time a “developer” tried pushing code at 3 AM from an IP in Russia.
The most successful teams we’ve trained keep tweaking their process. They run quick audits, adjust permissions when teams change, and actually pay attention when security flags something strange. It’s not perfect, but it beats explaining to the CEO why production’s down again.
Wrapping Up
The numbers don’t lie – splitting up who does what in software releases just works better. Teams that divide tasks between coders, ops folks, and security end up with fewer mess-ups and smoother rollouts. It’s like having different locks and keys (through access controls and approval systems), making sure nobody’s got too much power. Sure, it might seem like extra work at first, but it keeps things moving while protecting the code. Maybe not the fastest way, but definitely the safest.
If you want to dig deeper into how to implement secure coding practices alongside this kind of role-based division, or even take a hands-on course to get your team up to speed, you should check out the bootcamp offered here Join the Secure Coding Practices Bootcamp.
FAQ
How does separation of duties improve deployment security in real projects?
Separation of duties and segregation of duties strengthen deployment security by ensuring no single person controls the entire release. With SoD in deployment, tasks are divided across deployment process roles, release management roles, and deployment monitoring roles.
This supports fraud prevention IT, reduces insider threat mitigation deployment risks, and keeps code review segregation fair. Splitting responsibilities builds internal control mechanisms and security controls for deployment that protect production environment access and maintain compliance separation of duties.
Why is role-based access control important in deployment workflow roles?
Role-based access control (RBAC) sets clear boundaries in deployment workflow roles, helping teams avoid role conflict prevention. With RBAC, system access segregation is enforced across the deployment responsibility matrix and deployment role matrix, limiting access rights management issues.
When combined with deployment approval workflow, automated deployment approvals, and change approval delegation, RBAC strengthens deployment accountability. It also supports separation of privileged access, environment access control, and deployment access review, which enforce IT segregation policies and organizational security controls.
What is the value of build and deploy separation in secure software releases?
Build and deploy separation adds safety to secure software releases by keeping developer role separation clear from production release control. Code deployment segregation and code promotion segregation stop one person from pushing risky changes. Deployment automation controls and deployment integrity controls provide deployment control points and error prevention deployment benefits.
Paired with deployment oversight functions, deployment audit trail, and deployment audit logging, this separation supports deployment process checks and balances, reduces deployment segregation risks, and ensures deployment process compliance.
How does deployment approval segregation reduce deployment risk mitigation challenges?
Deployment approval segregation and multi-person approval stop risky shortcuts by enforcing deployment approval workflow steps. Deployment accountability controls and process control in deployment keep actions in check. Independent deployment review, deployment security testing roles, and deployment process auditing add more deployment control points.
These strengthen deployment oversight functions, reduce deployment segregation risks, and improve deployment workflow governance. Together, they support deployment risk controls, human error reduction deployment, and conflict of interest prevention, making deployment task separation part of secure deployment best practices and IT governance SoD.
How do deployment security frameworks help with segregation in DevOps workflows?
Deployment security frameworks guide segregation in DevOps workflows by defining deployment team roles and deployment job separation. They shape deployment process isolation, deployment workflow governance, and deployment policy enforcement. Security in CI/CD pipelines depends on software delivery controls, deployment integrity controls, and deployment accountability.
With deployment task allocation mapped in a deployment responsibility matrix, teams apply deployment control points and access permissions deployment rules. These secure deployment best practices ensure deployment process checks and balances and strengthen oversight in release orchestration security.
References
- https://en.wikipedia.org/wiki/Role-based_access_control
- https://en.wikipedia.org/wiki/Security_awareness

