These two ideas still confuse the heck out of most devs in the field. Defense in depth isn’t just throwing more security tools at a problem – we see this misconception daily in our secure coding bootcamps. It’s about building security from the ground up: clean code, teammate reviews, and backup plans for when things go wrong.
Layered security’s more cut and dry, though. Stack up tech barriers like firewalls and data encryption. Our students often mix these concepts up at first, but defense in depth’s really the master plan while layered security’s just one piece of the puzzle.
Key Takeaways
- Defense in depth runs deep – from how code’s written to what happens when things break
- When (not if) systems crash, defense in depth keeps the wheels turning while layered security just adds extra roadblocks
- Think of layered security as one chapter in defense in depth’s bigger story – it’s the tech stuff, while defense in depth covers the whole security picture
What is Defense in Depth in Cybersecurity?
Most newbies show up thinking they need the latest security gadgets. Not even close. Teaching developers since 2018 has shown us that implementing defense in depth spreads way beyond tools, it’s baked into how teams write code and control system access.
Theory doesn’t stick. Real learning hits when students see everything click together – from basic code reviews to monitoring system health, even trusting those gut-level “something’s not right” moments. Simple fixes beat fancy vendor solutions nine times out of ten.[1]
The lightbulbs really start going off during week three of bootcamp. Students discover how classic firewalls mesh with modern app security, add some two-factor authentication, and suddenly the whole picture comes together. We’ve watched hundreds of devs transform into security champions just by staying alert and following their instincts.
What is Layered Security and Its Tactical Focus?
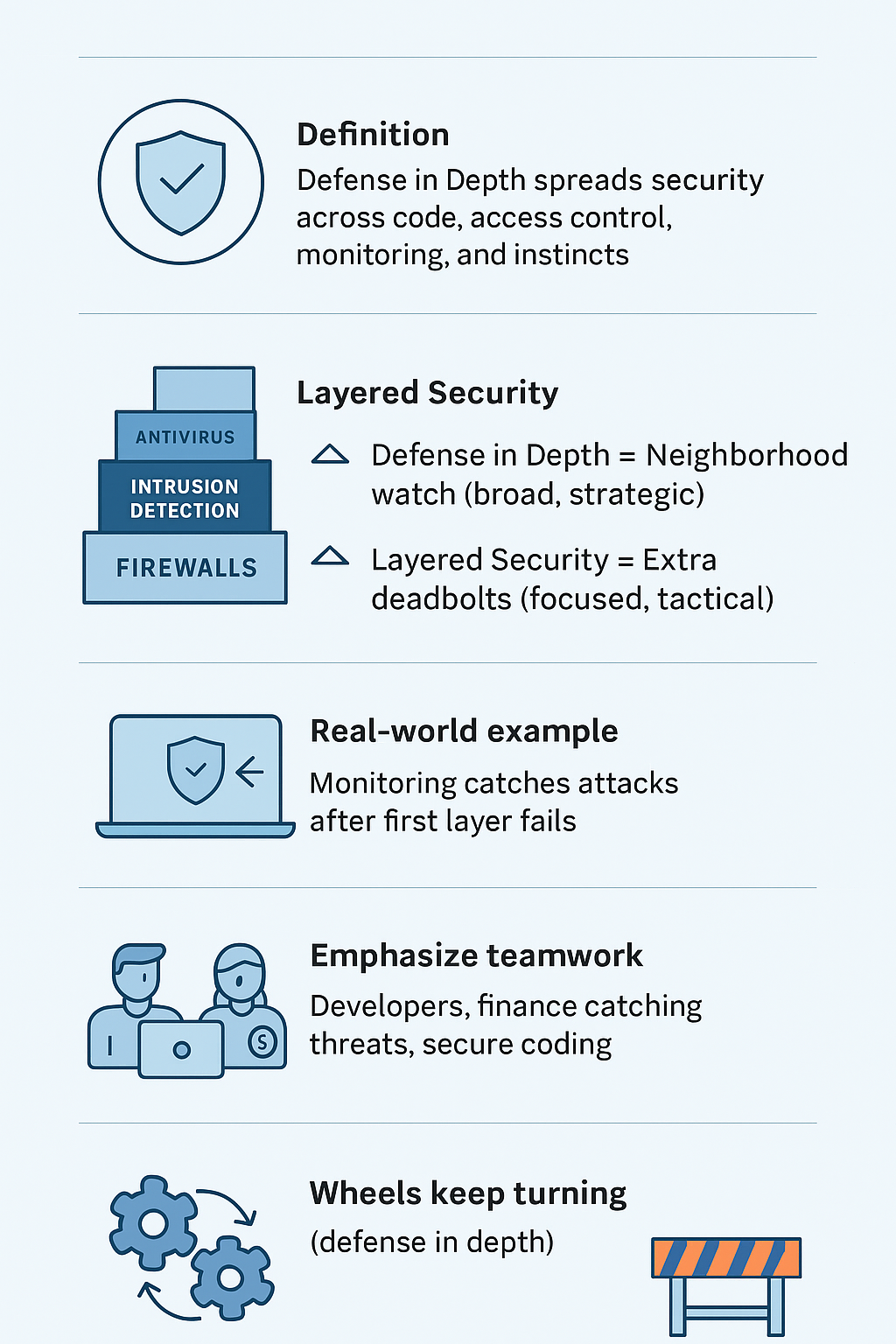
Stack security tools like building blocks – that’s the essence of layered security. Our students typically grasp this fast since it’s straightforward: multiple defensive barriers keep threats at bay.
Setting up usually starts basic: firewalls guard the entrance, intrusion detection watches for sketchy behavior, and antivirus scans incoming traffic. Each layer catches what slips through the others, all focused on one goal – keeping systems locked down tight.
This approach works great for smaller shops or specific vulnerable areas. Nothing fancy needed, and that’s exactly the point. Developers learn quickly that layered security isn’t trying to solve world peace – it just makes certain areas really tough to crack.
How Do Defense in Depth and Layered Security Differ Strategically and Operationally?
Teaching security concepts gets tricky, especially when students start confusing similar-sounding terms. Here’s what catches most folks off guard:
- Defense in depth works like a well-planned neighborhood watch
- Layered security’s more like adding extra deadbolts to your door
- One covers everything, the other’s focused on specific weak spots
- Real protection needs both, but in different ways
Our bootcamp students usually get it when we break down real-world scenarios. Take last month’s penetration testing exercise – the team with just layered security got breached because they focused only on network defenses. Our students learned this lesson the hard way last month – their monitoring system caught a nasty attack even after their first defense crumbled. That’s exactly what defense in depth’s supposed to do.
Building security isn’t just about fancy tools and blinking lights. Through our bootcamps, we’ve watched companies transform when everyone gets on board with security thinking. Like that time when Sandra from finance spotted a sketchy invoice, or when Mike’s team started writing code that actually stood up to pen testing.[2]
When (not if) systems crash, the benefits of defense in depth show up fast, it keeps the wheels turning while layered security just adds extra roadblocks.
How Do Defense in Depth and Layered Security Integrate in Practical Cybersecurity Frameworks?
Big security frameworks tuck layered security inside defense in depth – something that becomes crystal clear during hands-on bootcamp sessions. Those stacked security controls everyone obsesses over? Just part of the story. The full picture needs:
- Security rules written in plain English
- Building security that’s more than fancy badges
- Emergency plans teams actually remember how to use
- Eyes and ears that catch trouble early
The security desk hums along mixing standard tools with street-smart analysts. Sometimes those script kiddies sneak past the firewall (it happens to everyone), but there’s always someone watching or some process catching them red-handed.
The lightbulbs really start going off during week three of bootcamp. Students discover how classic firewalls mesh with modern app security, add some two-factor authentication, and suddenly the whole picture of applying defense in depth in web applications comes together.
How Can Organizations Enhance Security Posture Beyond Basic Defense in Depth and Layered Security?
Credit: Cybersecurity Training Expert
Look, defense in depth isn’t perfect – nothing is. But we’ve found some cool tricks teaching our students how to beef things up. Zero trust’s getting big now – basically treating everyone like they might be up to no good (in a professional way, of course). Those AI systems that spot weird behavior patterns? They’re pretty slick when they work right.
The human side trips everyone up though. We had this incident where all our fancy tech didn’t matter because someone clicked a sketchy link. That’s why we hammer home security awareness in every class. And disaster recovery? Man, nothing teaches that lesson like watching a team scramble after a breach.
Security’s gotta keep moving too. What worked last month might not cut it today. Our testing team’s always poking holes in things, running those vulnerability scans, trying to break in (legally, of course). Cyber creeps don’t sit still, so neither can we. Keeps us on our toes, keeps things interesting.
Conclusion
Look, we’ve seen it play out a hundred times in our training sessions – defense in depth isn’t just about throwing tools at problems. Think of layered security as just one piece of the puzzle. The real magic happens when everything works together: people watching each other’s backs, solid processes, and yeah, some decent tech too.
Want better security? Stop obsessing over fancy tools. Take a step back, figure out where you’re exposed, and build backup plans that actually make sense. Sure, it’s messy work, but that’s what keeps the bad guys guessing.
Join our Secure Coding Bootcamp to put defense in depth into action.
FAQ
How does defense in depth differ from layered security in a cybersecurity strategy?
Defense in depth and layered security both aim to protect systems, but they work in different ways. A cybersecurity strategy built on defense in depth adds security layers across people, processes, and technology. Layered security, on the other hand, often stacks tools like firewall protection, malware protection, and an intrusion detection system to block threats. Both approaches can use access controls, vulnerability management, and data encryption, but defense in depth connects everything into a bigger picture for risk mitigation.
Why is a multi-layered defense important for network security and endpoint security?
A multi-layered defense works because no single tool stops every attack. For network security, layers like network segmentation, firewall rules, and an intrusion prevention system reduce the attack surface. For endpoint security, tools like endpoint detection and response, patch management, and antivirus software help stop ransomware and advanced persistent threats. When tied together with identity and access management and user authentication, these layers improve data protection and lower the chances of security breaches.
What role do identity and access management and multi-factor authentication play in zero trust security?
Identity and access management makes sure the right people get the right access at the right time. Multi-factor authentication adds another wall to stop privilege escalation and protect sensitive data. In zero trust security, no user or device is trusted by default. Every login goes through user behavior analytics, access controls, and sometimes privileged access management. Together, these security controls shrink the cyber attack vector and strengthen the overall security posture against threats.
How do an intrusion detection system and anomaly detection help with threat intelligence and threat detection?
An intrusion detection system watches network traffic for unusual patterns, while anomaly detection looks for behavior that doesn’t match normal use. Together, they improve threat intelligence and early threat detection. When paired with forensic analysis, security monitoring, and security automation, they help a security operations center spot advanced persistent threats faster. This layered defense also supports incident response, security compliance, and threat containment, making it easier to keep a strong security framework in place.
Why are patch management and vulnerability scanning key to maintaining security best practices?
Patch management and vulnerability scanning close cracks before attackers exploit them. They play a big role in reducing cyber risk, improving cyber resilience, and keeping a strong security architecture. By fixing weak points, these tools support secure access, encryption protocols, and application security. They also protect operating system security, endpoint protection platforms, and mobile device management. Along with security auditing, business continuity, and disaster recovery, these practices improve the security posture and help avoid security incidents.
How does security governance connect with security policy and compliance in building a security framework?
Security governance sets the direction, while a security policy explains the rules everyone follows. Together, they guide security compliance and shape a larger security framework. This structure helps organize security layers like perimeter security, cloud security, and secure gateways. It also covers security segmentation, privilege escalation prevention, and secure access. Strong governance supports cyber resilience, risk mitigation, and attack surface reduction while preparing for disaster recovery and business continuity in case of security breaches or incidents.
References
- https://www.researchgate.net/publication/372762207_A_Study_of_The_Effectiveness_of_Code_Review_in_Detecting_Security_Vulnerabilities
- https://en.wikipedia.org/wiki/Computer_security

