
Security isn’t a one-size-fits-all kind of thing. A single lock won’t keep determined attackers out, that’s just reality. Smart developers know they’ve got to stack those defenses – good code practices, watching those external packages like a hawk, and keeping the servers locked down tight.
We’ve seen too many breaches where just one weak spot brought everything down. Our bootcamp students learn this the hard way: real security means building walls within walls. There’s no magic bullet, but there’s something powerful about knowing each layer makes breaking in that much harder.
Key Takeaways
- Security needs layers – from clean code to locked-down servers and trained developers
- Coders make or break security by managing code quality, dependencies, and staying up on best practices
- Building security into development catches problems early, keeps auditors happy, and helps users sleep better
What is Defense in Depth and Its Importance for Developers?
No one starts out thinking about defense in depth. Most bootcamp students come in thinking a strong password and SSL certificate will keep their apps safe. That mindset shifts fast when they see how attackers work – probing every little crack until something gives.
Defense in depth isn’t rocket science. Stack enough good security practices together and you make life really hard for attackers. We teach our students to think in layers: clean code first, then proper access controls, infrastructure hardening, the works. Because here’s the thing – perfect security doesn’t exist, but solid layers of “good enough” security do the job.[1]
For developers cranking out code day after day, this means going beyond just making things work. Our responsibility starts with catching basic stuff like SQL injection but goes way deeper. We’ve got to validate every input, lock down permissions tight, and always assume our code could be the weak link. Sure it takes more time, but beats explaining to the boss how attackers waltzed right in.
Which Security Layers Constitute Defense in Depth for Developers?
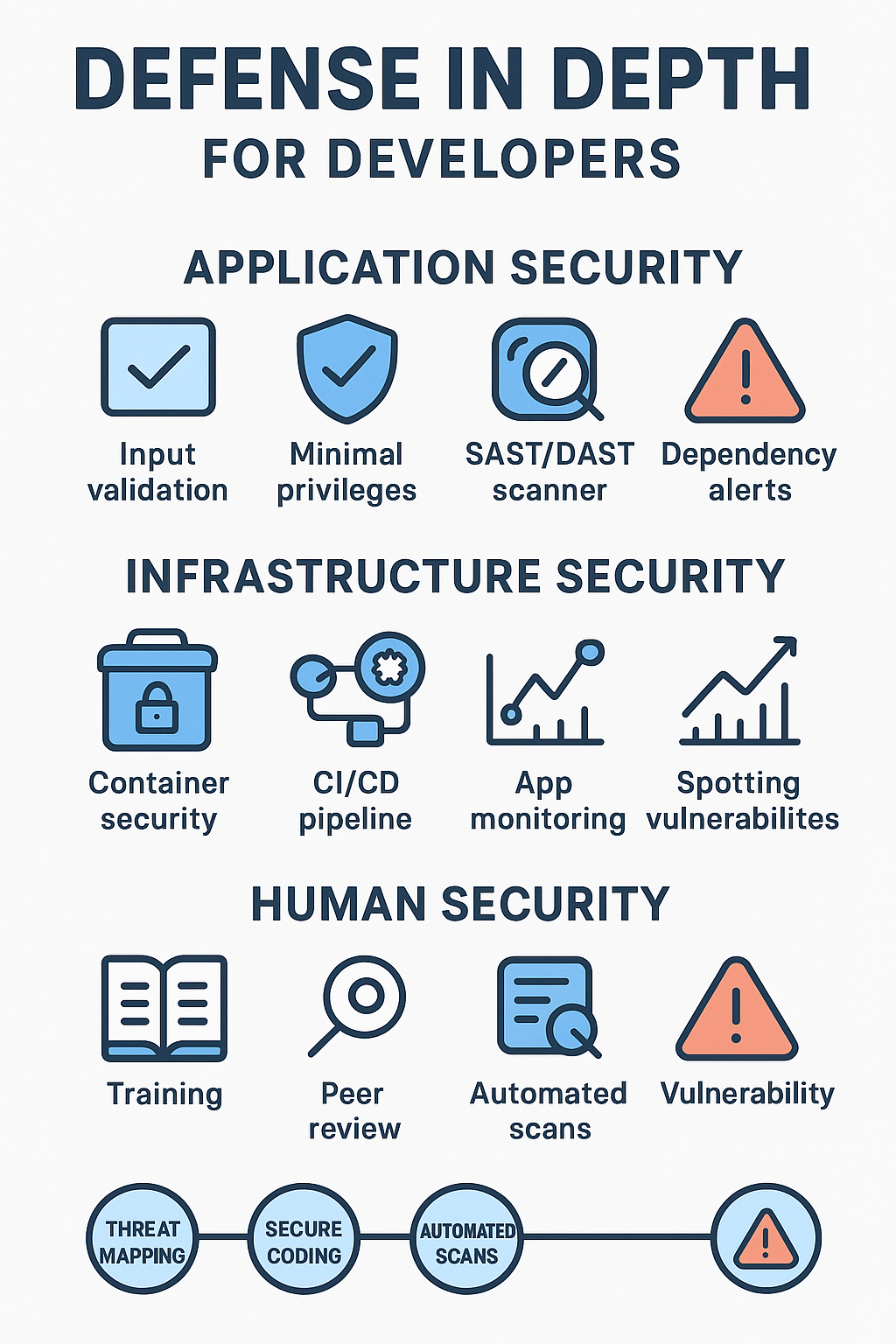
After teaching hundreds of students, we’ve seen how defense in depth clicks when developers understand where their code fits in the security puzzle. It’s not just about writing safer code, it’s about seeing the whole picture and creating defense in depth architecture that connects application, infrastructure, and human layers.
Application Security Layer and Developer Controls
The code level’s where developers live and breathe. Here’s what actually works:
- Clean input validation (because users type the weirdest things)
- Keeping code privileges tight and minimal
- Running those SAST and DAST scans (even if they’re annoying)
- Watching those dependencies like a hawk
Last month, one of our students caught a nasty SQL injection vulnerability during a routine scan. Better in testing than in production, right?
Infrastructure Security Layer and Developer Responsibilities
Anyone who thinks infrastructure is just for ops hasn’t been paying attention. Developers shape how apps run in production. Our students learn to:
- Lock down their containers
- Build security checks into CI/CD
- Keep an eye on their apps in production
Sometimes the best security catches come from watching how apps behave in the wild. That’s when the weird stuff shows up.
Human Security Layer and Developer Engagement
The human side trips up even experienced developers. Regular training isn’t optional anymore – threats change too fast. Our teams do security-focused code reviews that catch things automated tools miss. Nothing beats an experienced developer saying “hey, this looks fishy.”
You’d be surprised how often a fresh pair of eyes spots problems that slipped past everyone else. That’s why we push peer reviews so hard in our bootcamps.
How Do Developers Integrate Defense in Depth Within a Secure Development Lifecycle (SDLC)?
Good security’s like an onion, layers on layers, and developers need to focus on implementing defense in depth from the very first stages of the SDLC. Most students come in thinking they’ll just slap some security on at the end, but that’s not how it works in the real world.
We teach them to start with the basics: mapping out where attacks might come from, setting solid security requirements, and building guardrails into their code from day one.
The fun part starts when projects hit our test pipelines. Automated scanners catch the obvious stuff, but there’s always something that slips through. That’s why we drill students on secure coding standards until they dream of input validation. Some grumble about it slowing them down, but better slow and secure than fast and breached.
Post-deployment’s where theory meets reality. New vulnerabilities pop up daily, and those dependency scanners start lighting up like Christmas trees. Just last month, our monitoring caught a critical issue in a popular npm package – having response plans ready meant our students could patch and push updates before most folks even knew there was a problem.
Every bootcamp group learns this lesson: security’s not a one-and-done deal. It’s constant vigilance, regular updates, and always assuming something could go wrong. Because in production, it usually does.
What Benefits Do Defense in Depth Practices Provide to Developers and Software Systems?
Experience teaches hard lessons. After seeing hundreds of student projects, patterns emerge in what works and what fails. Multiple security layers might seem like overkill until that one critical bug slips through. Our advanced students get this – they’ve watched simple mistakes cascade into major headaches.
Early detection’s worth its weight in gold. Those automated security checks catch problems when they’re cheap to fix, not when they’re keeping ops teams up at night. Every semester, some hotshot tries to skip the security scans to save time. They learn pretty quickly why that’s a bad idea during our penetration testing weeks.
Compliance used to be an afterthought in development. Not anymore. These days, customers want proof that their data’s safe, and auditors want documentation. Having security built in from the start makes those requirements way easier to handle. One student project got picked up by a fintech company – their defense in depth approach sealed the deal.
How Are Authentication, Authorization, and Data Protection Applied in Defense in Depth?
Nobody likes dealing with access control, but it’s usually where apps fall apart first. Multi-factor auth and proper role management stop most casual attacks cold. Our students learn this stuff hands-on, usually after watching their “secure” projects get torn apart during security reviews.[2]
Basic auth isn’t enough anymore. Smart developers layer their defenses: strong password policies, session management, role-based access control. We’ve seen too many projects where one missed permission check let attackers see everything. These days, our advanced courses spend extra time on OAuth and JWT implementation – because that’s where real-world apps often go wrong.
Data protection trips up even experienced developers. Everyone knows to encrypt sensitive stuff, but doing it right takes practice. Last term’s projects showed the usual mistakes: hardcoded credentials, weak encryption, secrets in config files. Now we push hard for proper key management and secure vaults. The extra work pays off when students hit their first real security audit.
How Do Developers Collaborate with Other Security Layers and Teams?
Credit: Dr. Erdal OZKAYA
Defense in depth is a team effort. Developers team up with the network security folks to shrink the weak spots that hackers look for. That means things like building safer APIs and making sure the firewalls are set up the right way.
Once the app is running, we don’t leave it alone. Tools like Runtime Application Self-Protection (RASP) and Web Application Firewalls (WAF) stand guard next to our code, working hand-in-hand with endpoint defense in depth measures to block attackers before they break in.
They watch for bad traffic and shut it down before it causes real trouble. Collaboration with operations teams helps harden containers and cloud environments.
What Advanced Practices Enhance Defense in Depth for Developers?
Two practices stand out in my experience: software composition analysis and secure error handling.
Software Composition Analysis and Dependency Management
Third-party libraries are a double-edged sword. They speed development but can introduce vulnerabilities. Regularly updating dependencies and using trusted sources is vital. Automated tools that scan for known issues keep us informed and help us act fast.
Secure Error and Exception Handling
Proper error handling prevents sensitive information leakage. We code error messages to be user-friendly but vague on technical details. Secure logging captures necessary data for audits without exposing secrets.
Conclusion
Defense in depth isn’t just another buzzword – it’s about survival in today’s threat landscape. Every layer counts, from clean code to locked-down servers and trained developers. Our bootcamp students learn this fast, usually after their first security review tears their “perfect” code apart.
Sure, it takes more work to build those security layers, but it beats explaining to clients why their data got leaked. No single wall keeps everyone out, but stack enough good practices together and you’ve got something solid. Join the Bootcamp
FAQ
How does defense in depth help developers build safer apps, and why is layered security or multi-layer security important for a cybersecurity strategy?
Defense in depth stacks many protective layers so one mistake doesn’t sink the ship. Developers use layered security and multi-layer security to ensure that if one barrier fails, others still stand. A cybersecurity strategy with secure coding, intrusion detection system, endpoint security, and network perimeter security makes it harder for attackers to move. Each layer slows them down and gives defenders time to react. For developers, it’s about designing with safety at every level instead of trusting one wall or tool.
What role do secure coding and the secure software development lifecycle play in defense in depth for developers?
Secure coding is the first brick in the wall. The secure software development lifecycle gives developers a plan to build safety early. That means using security testing, security code review, and penetration testing tools to catch problems before release. Secrets management, dependency management, and supply chain security prevent hidden risks. Threat modeling, secure coding guidelines, and application vulnerability scanning stop flaws before users see them. In defense in depth, these practices form the foundation that supports higher security layers.
How do network perimeter security and endpoint security connect with intrusion detection system or intrusion prevention system in a layered security approach?
Network perimeter security sets the fence, while endpoint security guards each device inside. An intrusion detection system spots break-ins, and an intrusion prevention system blocks them in real time. Together, they form cybersecurity defense layers. Add firewall configuration, network segmentation, and application firewall rules, and the system works in sync. This mix isn’t perfect, but it slows attackers and keeps logs for review. For developers, the goal is building apps that fit into this security architecture without leaving open backdoors.
Why are identity and access management, multi-factor authentication, and role-based access control so critical for developers working with defense in depth?
Identity and access management ensures only the right people touch the right data. Multi-factor authentication adds another lock, making stolen passwords less useful. Role-based access control limits permissions to what’s needed. Developers must also use privileged access management and endpoint privilege management, since overpowered accounts are risky. Access control policies and password management tighten security further. Combined, these create strong barriers against insider threat mitigation and lateral movement prevention. In defense in depth, access control keeps attackers from moving freely.
How do encryption at rest and encryption in transit support data encryption and secure communication protocols in defense in depth?
Data encryption protects information from prying eyes. Encryption at rest keeps files safe on disk, while encryption in transit shields them on the move. Secure communication protocols, often used in cloud security or container security, make sure traffic can’t be read or changed. Cryptographic key management is crucial here, since weak keys mean weak locks. Developers using secure API design, application security, and secure configuration rely on these tools to follow data protection policies. In defense in depth, encryption ensures stolen data stays locked.
What part do vulnerability management and patch management play in a developer’s cybersecurity strategy?
Vulnerability management finds weaknesses, while patch management fixes them before attackers strike. Developers face patch vulnerability issues in libraries, so dependency management and software composition analysis are essential. Security automation and continuous security monitoring speed up the process. Add security audits, compliance standards, and security framework checks, and code stays healthier. For defense in depth, the goal is reducing exposure time so flaws don’t linger. Developers who practice proactive security build systems that are stronger and more resilient.
How can developers prepare for the modern cyber threat landscape, including advanced persistent threats, ransomware defense, and phishing prevention?
The cyber threat landscape keeps changing, with advanced persistent threats digging deep and ransomware defense now a daily concern. Phishing prevention and malware protection help, but they’re not enough alone. Developers should use security awareness training, anomaly detection, and breach detection to stay ready. Logging and monitoring, incident response, and security incident management make sure action is fast when things go wrong. Security best practices like secure authentication, adaptive security, and behavioral analytics make defense in depth stronger.
Why are security audits, threat intelligence, and continuous security monitoring important for defense in depth in secure DevOps?
Security audits show where gaps hide. Threat intelligence keeps teams aware of new attack methods. Continuous security monitoring ensures nothing slips through. In secure DevOps, these practices are supported by secure API checks, application firewall tuning, and security tooling. Security policies enforcement and security awareness training help close human risks. Security controls, security architecture, and proactive security measures all support adaptive security. For developers, this ensures secure DevOps pipelines follow security best practices while holding up against evolving threats.
References
- https://www.reddit.com/r/cybersecurity/comments/1fu1x7p/what_percentage_of_breaches_are_caused_by/
- https://worldmetrics.org/multifactor-authentication-statistics/

