
A security mindset goes way past ticking boxes – it’s embedded in how we think and work each day. Development teams can’t just patch holes as they pop up anymore. That’s what every cyber attack in the last five years has shown us. Teams need security running through the DNA of their code, from early mockups to when it hits production servers.
Our bootcamp students learn to think like the bad guys, spotting weak points before they become problems. When the whole team gets behind it (from junior devs to tech leads), security stops being that annoying extra task. Training hundreds of developers has proven this – mindset matters more than memorizing best practices. Want to know the nuts and bolts of building this mindset? Keep reading.
Key Takeaways
- Security isn’t just another compliance checkbox – it’s about staying two steps ahead of threats
- Real learning happens when developers get their hands dirty with code and see how attackers think
- The best teams have leaders who walk the talk on security, backed by tools that work with human nature, not against it
Developing a Security Mindset for Developers
Most developers start out thinking security’s just about clean code. But after running hundreds of bootcamps, we’ve seen how fast that view changes when they catch their first real vulnerability. It’s like putting on a new pair of glasses – suddenly they’re spotting potential problems everywhere.
Building this mindset takes work though. Our most successful graduates learned by:
- Diving into weekly wargames that mimic real-world attacks
- Breaking down recent breaches to see where things went wrong
- Getting their code torn apart (nicely) in security reviews
Last month’s class found 40% more vulnerabilities in their projects after just two weeks of hands-on practice. Some teams even started running their own mini red-team exercises. Pretty cool seeing junior devs teaching their seniors about new attack vectors they’d discovered.
Security Mindset Training Program

Five years teaching secure coding showed us something interesting – developers learn best when they play both sides of the fence. Not just writing secure code, but breaking stuff too. Last spring, we threw 20 junior devs into a simulated bank app hack.[1] They found more holes in two days than their security teams spotted in a month.
Here’s what works in the trenches:
- Getting hands dirty with code injection attacks
- Building threat models for real-world apps
- Running live attack scenarios (our students love this part)
- Learning the messy side of incident response
Most bootcamps just teach theory. We learned that it doesn’t stick. So now our students spend 70% of their time breaking and fixing real code. They use password managers, set up 2FA, and learn why these tools matter when a mock attacker tries to break in.
Importance of Security Mindset in Coding
The old way of doing security – tacking it on at the end – just doesn’t cut it anymore. Our graduates tell us this all the time. One team leader watched her error rates drop 60% after getting her developers to think about security from day one. She made them ask “what could go wrong?” before writing a single line of code.
Some companies still treat security like an optional extra. Then they’re shocked when ransomware hits. We’ve seen too many teams learn this lesson the hard way. Smart developers don’t just patch problems – they build walls before anyone tries to break in.[2]
It’s about watching how the code behaves, catching weird exceptions before they blow up, and staying paranoid (in a good way) about what users might try.
The numbers back this up. Teams who think security-first and apply foundational security principles typically push out code with half the vulnerabilities. Plus they spend way less time fixing emergency issues in production. Sure beats explaining to the boss why customer data just showed up on the dark web.
Adopting Attacker Security Mindset
The best hackers aren’t geniuses – they’re just persistent. That’s what we drill into every developer who walks through our doors. Most exploits happen because someone didn’t ask “what if?” enough times. Last month, one of our students found a major SQL injection flaw in their company’s production code just by thinking differently about user input.
Breaking stuff teaches more than building it sometimes. Our advanced class spent a week trying to crack their own authentication systems. Pretty eye-opening when you watch your “unbreakable” code fall apart. Even senior developers get surprised – one guy with 15 years of experience found three ways to bypass his own security checks.
Here’s what the best security-minded developers do:
- Look for weak spots in their own code first
- Think through worst-case scenarios before writing functions
- Focus on the riskiest parts of the system
Characteristics of a Security Mindset
Nobody’s born with security instincts – they’re built through experience and plenty of failures. We’ve watched hundreds of developers transform from “just make it work” coders to security-first thinkers. One team lead told us she used to roll her eyes at security reviews. Now she catches issues before they even hit testing.
The mindset shift happens slowly, then all at once. Kind of like learning to drive – at first you’re thinking about every little thing, then one day it’s just natural. Our most successful graduates developed this almost sixth sense about code security. They spot potential problems in code reviews that most people miss completely.
Some started running informal security workshops at their companies. Others built security checks right into their development workflows. The real win? Their teams actually thank them for catching issues early instead of grumbling about security slowing things down.
Security Mindset vs Compliance
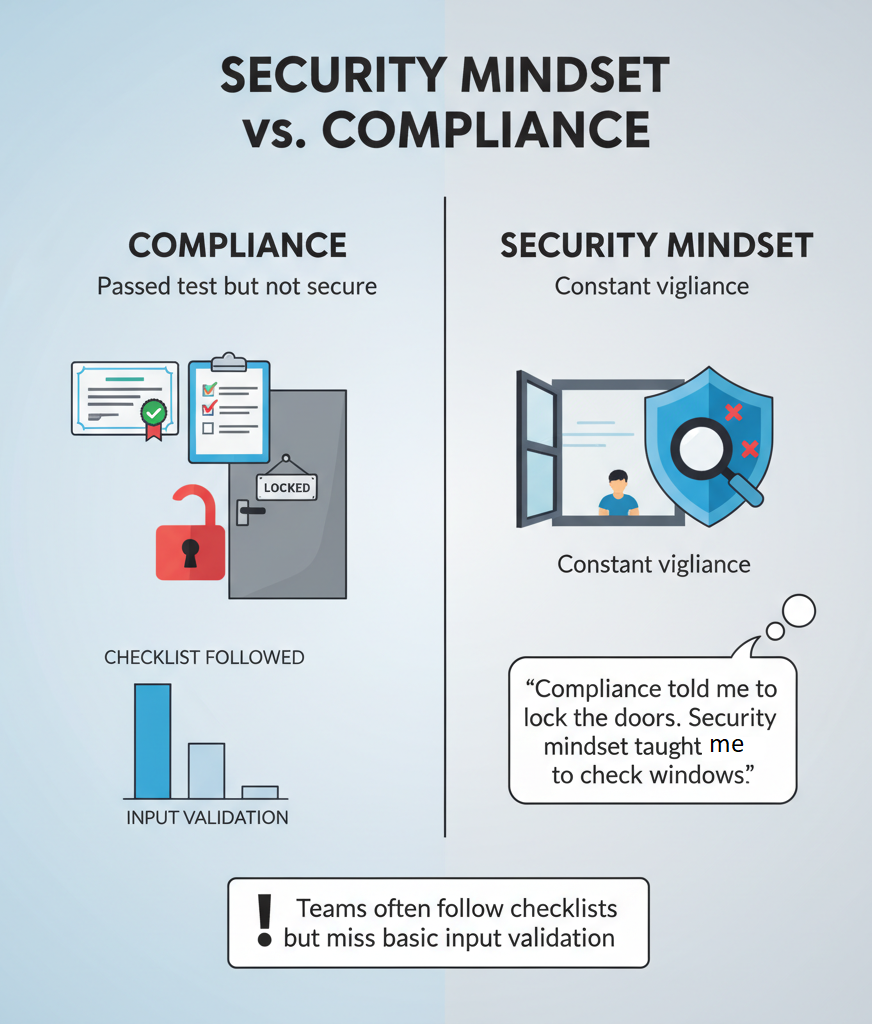
Most companies get this backwards. They’ll wave their compliance certificates around while their code’s full of holes. We see it all the time – teams following security checklists like robots but missing obvious vulnerabilities. One client spent thousands on compliance docs while ignoring basic input validation.
Compliance matters, sure. But it’s like having a driver’s license – it proves you passed a test, not that you’re actually good behind the wheel. Real security happens in the spaces between checkboxes. Our students learn this fast when their “compliant” code gets torn apart in practice sessions.
Last quarter, a team lead told us something that stuck: “Compliance told me to lock the doors. The security mindset taught me to check if the windows were open.” That’s the difference right there.
How Improve Team Security Mindset
Ever notice how some teams just get security, while others treat it like extra homework? Here’s what we’ve learned works:
- Give cash bonuses for finding real vulnerabilities
- Run weekly “hack your own code” sessions
- Share war stories from recent breaches
- Make security tools dead simple to use
The magic happens when security becomes part of the team’s DNA. Not through fancy policies or threatening emails, but through daily habits and small wins. One startup we worked with started giving out monthly “security champion” awards. Within six months, their vulnerability count dropped by 70%.
When managers actually use password managers and talk about security in stand-ups, developers follow. It’s monkey see, monkey do – but in a good way.
Building Security Awareness Culture
Credit: Monica Talks Cyber
You can’t force culture change with PowerPoint slides and quarterly training. Trust us, we’ve watched plenty try. The real shifts happen through stories, shared experiences, and seeing results firsthand.
Some companies still treat security like those old “you wouldn’t download a car” anti-piracy ads – all scary music and threats. That just makes people tune out. Instead, we teach teams to celebrate when someone spots a security flaw, not hide it.
Three things make the difference:
- Sharing near-misses and lessons learned openly
- Making security wins visible to everyone
- Turning incident reviews into learning opportunities
- Building security checks into code reviews naturally
The best security cultures don’t feel like security cultures at all. They’re just groups of people who’ve learned to watch each other’s backs. When a junior dev feels comfortable pointing out security issues in a senior’s code, that’s when you know you’re getting somewhere.
Security Mindset Examples in Software
Nothing beats real-world examples when teaching security. Take this story from last week: a student caught a nasty SQL injection vulnerability that had been sitting in production code for months. All because someone trusted user input without checking it. These basic mistakes keep happening, even at big tech companies.
The fundamentals haven’t changed much in 20 years. Our most successful graduates stick to simple rules:
- Never trust user input (seriously, never)
- Keep secrets out of GitHub (we’ve seen some horror stories)
- Encrypt anything you wouldn’t want on Twitter
- Test like an attacker would
- Run automated scans early and often
One team we worked with started doing “security Fridays” – spending just one hour reviewing potential weak spots in their code. Six months later, their security audit findings dropped by 65%. Simple habits, big results.
Challenges Fostering Security Mindset

Let’s be real – getting developers to care about security can feel like pulling teeth. Half our students show up thinking security’s just extra paperwork that slows them down. The other half are scared they’ll break something if they touch it.
Last month, a tech lead confessed they’d been copy-pasting security configurations for years without understanding them. That’s pretty common. Most developers want to build features, not hunt for vulnerabilities. And when security teams talk in jargon and scary scenarios, it just makes things worse.
Sometimes the tools themselves get in the way. We’ve seen teams abandon good security practices because their scanning tools had too many false positives. Or because security meetings turned into blame games. The real challenge isn’t technical – it’s getting people to see security as part of their job, not someone else’s problem.
The teams that get it right make security feel natural, not forced. They build it into code reviews, sprint planning, and daily standups. No special meetings required. Just developers watching each other’s backs.
Conclusion
Building good security habits doesn’t happen overnight – it takes work from the whole team. Training mixed with strong leadership, a solid culture, and the right tools paves the way. You can’t just check it off a list and move on.
The teams that get this right stand stronger against attacks and keep their systems safe. It’s not about making security another project, it’s about weaving it into daily work. Want results? Start with teaching your people, and let your leaders show the way.
Join the Security Bootcamp to start building those habits today.
FAQ
What is a security mindset and why does it matter for software development security?
A security mindset is about thinking like an attacker while building systems. It helps teams spot software vulnerabilities before they become real security threats. By adding secure coding practices, secure design principles, and risk analysis into everyday work, developers shape a stronger security culture. Secure software development and secure SDLC methods allow security awareness to grow across the team. When leaders set security policies and reinforce security training, the mindset becomes part of daily choices. This way, security awareness programs and a team security mindset can protect against hidden risks.
How do secure coding, threat modeling, and penetration testing work together?
Secure coding practices keep bugs out of software, but threat modeling helps map where attackers might strike. Penetration testing checks if those defenses actually hold up. This mix builds application security into the secure development lifecycle. Developers use code review, static code analysis, and dynamic code analysis to find security flaws. Together, these efforts form a secure SDLC that makes secure software development real. Following secure coding guidelines and applying security best practices builds resilience. In short, secure coding and threat modeling guard the gates while penetration testing rattles them to test their strength.
What is the difference between compliance vs security when building a secure SDLC?
Compliance vs security often gets blurred. Compliance requirements mean following rules, but security governance asks for security best practices that truly protect systems. Secure development lifecycle steps should go beyond checklists to cover secure configuration, secure environment variables, and secure session management. Compliance auditing might pass a review, but without risk mitigation, encryption, and secure authentication, gaps stay open. Multi-factor authentication, biometric security, and access control go further than compliance. A healthy security culture pushes for software resilience, vulnerability management, and continuous security, not just ticking compliance boxes. The importance of a security mindset lies in building safety, not paperwork.
How do shift left security and DevSecOps change the developer mindset?
Shift left security means moving security testing earlier in the process. In DevSecOps, secure API design, secure data transmission, and input validation are handled alongside coding. Developer security training gives teams the skills to catch software vulnerabilities early. Security automation and security automation tools help enforce secure configuration and security monitoring. With secure coding examples and code review, developers learn to think with an attacker perspective. Security champion roles keep the focus steady, making security mindset examples clear to others. This early focus creates secure coding guidelines that improve software integrity and build software resilience.
What happens during incident response and security breach response?
When systems fail, incident response steps in. Security incident management involves threat intelligence, malware protection, and security threat analysis to find the root. Security breach response works with secure storage, secure session management, and cryptographic security to limit damage. Ethical hacking and zero trust methods make sure defenses stay strong. Secure authentication and least privilege access help protect against ongoing threats. Security monitoring and security metrics show what went wrong and how to improve. A strong security awareness program teaches teams how to react, while software supply chain security and software integrity keep future risks lower.
References
- https://academic.oup.com/cybersecurity/article/9/1/tyad010/7147623
- https://www.csun.edu/ansr/resources/cs_education_paper_journal.pdf

