A bloated security system is like a security guard carrying too much gear, they’ll trip over their own feet. When networks get stuffed with endless tools and fancy add-ons, things get messy fast. Bob from IT struggles to patch servers because tool overload forces him to jump between multiple dashboards, slowing every step.
Sarah in SecOps misses critical alerts because high false-positive rates bury real signals, reducing her visibility into genuine threats. Meanwhile, hackers slip through the cracks while everyone’s busy untangling the mess. Had enough of the chaos? Stick around to learn how to clean up your security without leaving gaps.
Key Takeaway
- Complexity widens attack surfaces and raises risks.
- Simplifying security improves manageability and speeds response.
- Consolidation, automation, and network design cut complexity effectively.
The High Cost of Complexity in Cybersecurity

Security teams trip themselves up chasing the myth of “more tools, better defense.” We’ve watched countless organizations pile on security products like a nervous traveler over-packing for a trip. At our bootcamp, students often share stories about juggling 15+ security dashboards at their day jobs, a recipe for chaos. One banking client lost three security leads in six months as their tangled system architecture created unsustainable operational pressure.
Complex systems spawn problems everywhere:
- Alert fatigue drowns out real threats
- Updates break random integrations
- Teams waste hours switching between tools
- Training new hires takes forever
Nobody plans to build a messy security system. It happens gradually, tool by tool, each promising to fix something specific. But our experience shows these band-aid solutions create blind spots. When teams can’t see the whole picture, hackers find ways to hide in the noise.
Why Simplicity Strengthens Security
Stripping down bloated security reduces operational friction, making it easier for teams to detect anomalies and maintain configurations. Through hundreds of training sessions, we’ve proven that lean, focused security catches more threats. Last month, our students rebuilt a client’s security stack, cutting it from 12 tools to 4. Their detection speed improved dramatically because fewer tools meant clearer signals and faster triage. This approach perfectly captures the importance of simplicity in security, showing how trimming excess improves outcomes.
A simplified approach delivers real benefits:
- Fewer moving parts mean fewer things break
- Teams spot problems faster
- Updates roll out cleanly
- New team members get productive quicker
- Threat hunting becomes practical
Developers at our bootcamps build better code when security feels manageable. They’re more likely to follow secure practices when tools make sense. Simple security creates a foundation where good habits stick. Our graduates consistently report that streamlined environments help them catch vulnerabilities before deployment.
Actionable Steps to Reduce Security Complexity
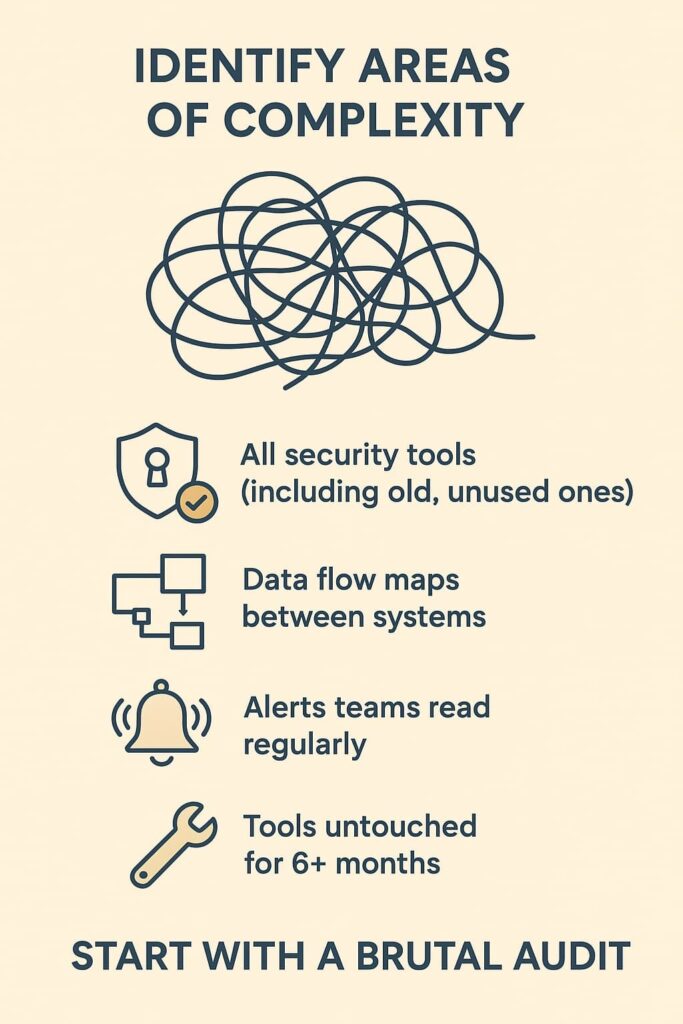
1. Identify Areas of Complexity
A security mess doesn’t happen overnight. Our training sessions regularly uncover security setups that grew like weeds, random tools tacked on whenever something went wrong. Last week, a student showed us their company’s security diagram, it looked like a bowl of spaghetti. Start with a brutal audit of what’s actually running in your environment.[1]
Take stock of:
- Every security tool (yeah, even that old IDS nobody touches)
- Where data flows between systems
- Which alerts teams actually read
- Tools nobody’s touched in 6 months[2]
2. Consolidate Security Tools
Nobody needs three different antivirus programs. We’ve helped dozens of teams clean up tool overlap, and the relief on their faces says it all. One healthcare client cut their security budget 30% just by dumping duplicate tools. Look hard at what each piece of software actually does.
Focus on:
- Finding swiss-army-knife platforms that handle multiple jobs
- Killing off one-trick-pony tools
- Picking solutions that play nice together
- Getting rid of anything that causes more headaches than it solves
3. Automate Security Processes
Our students waste hours on manual security checks that machines could handle better. Smart automation catches things humans miss. A bank we trained automated their vulnerability scans, they found 40% more issues and saved 15 hours weekly.
Start automating:
- Daily security scans
- Basic incident response
- Patch rollouts
- Log analysis
- Common alert investigation
4. Simplify Network Architecture
Credits: This Week Health
Messy networks give attackers too many hiding spots. Through hundreds of security assessments, we’ve seen how tangled networks turn minor breaches into disasters. One retail client rebuilt their network into clean segments, their incident response time dropped from days to hours.
Key changes needed:
- Split networks into clear zones
- Lock down connections between segments
- Know exactly what talks to what
- Keep critical systems isolated
5. Improve Visibility and Monitoring
Can’t fix what you can’t see. Our bootcamp graduates consistently report that better monitoring catches problems their old tools missed. We teach teams to build security dashboards that actually make sense, no more alert overload.
Must-haves for proper visibility:
- One place to see all security events
- Clear alert priorities
- Tested response playbooks
- Regular monitoring reviews
Remember, good security isn’t about having every tool – it’s about having the right ones and using them well.
Implementing Simplicity: A Practical Approach
Security cleanup isn’t a weekend project. Our bootcamp students often ask for quick fixes, but real change takes time. Last month, a dev team leader came to us frustrated with their messy security setup.
We helped them tackle one problem at a time, starting with their overcrowded tool stack. Three months later, their incident response time dropped by half. This illustrates the keep it simple security principle in action, focus on what truly matters and remove noise.
Pick your battles carefully:
- Start with whatever hurts most
- Fix one mess before moving to the next
- Keep checking that fixes actually work
- Don’t break what’s working just to simplify
How Our Approach Can Help Simplify Your Security
Most coding bootcamps throw security in as an afterthought. We’ve seen that mistake wreck too many projects. Security needs to be baked into code from day one, that’s why we drill secure coding basics until they stick. Through five years of training developers, we’ve proven that good habits up front beat bolt-on solutions every time. This highlights how simplicity improves security by making it easier to maintain, review, and deploy solid protections.
Teams who’ve gone through our program consistently report:
- Fewer emergency patches needed
- Cleaner code reviews
- Faster deployment cycles
- Better sleep at night
Simplifying Security: What You Need to Know
| Key Area | Action | Real Results |
| Find the Mess | Map out what’s actually running | A student found 6 unused security tools eating budget |
| Clean House | Merge overlapping tools | Banking client cut tool costs 40% |
| Work Smarter | Let machines handle repeatable tasks | Dev team saved 12 hours/week on security checks |
| Lock it Down | Split networks into zones | E-commerce site contained breach in 30 minutes |
| Watch Everything | One dashboard to rule them all | SOC team caught an APT others missed for months |
These aren’t theoretical benefits, they’re real wins from real teams who simplified their security through our program. Nothing fancy, just practical steps that work.
FAQ
How does the complexity of the enemy of security affect everyday users trying to stay safe online?
The complexity enemy of security shows up when security system complexity overwhelms people. Complex security architectures, multi-tool security complexity, and security visibility challenges make it easy to miss problems. This clutter raises human error security and complexity error rates.
When complexity increases vulnerabilities, users face more risk. Most people stay safer when they reduce complexity in cybersecurity and choose simplicity for security.
What steps can help reduce complexity in cybersecurity without weakening protection?
You can reduce complexity in cybersecurity by simplifying security and avoiding security tool sprawl. Security tool consolidation, integrated cybersecurity tools, and simplify security architecture help shrink the attack surface complexity. Clearer setups lower complexity security gaps and make threats easier to see.
These moves support complexity risk mitigation, strengthen security posture, and cut the security complexity cost that slows teams down.
Why do complex security architectures create hidden complexity security breaches over time?
Complex security architectures often hide complexity security challenges and complexity security failures. Complex network security, security configuration complexity, and complexity in secure configurations leave room for mistakes. Complexity and vulnerability management become harder, and complexity in intrusion detection slows response.
Over time, complexity leads to breaches because people can’t keep track of everything, especially with legacy system complexity or cloud security complexity.
How do cybersecurity complexity risks impact teams handling daily security operations?
Cybersecurity complexity risks create security operations complexity that drains teams. Security monitoring complexity, operational cybersecurity complexity, and cybersecurity staffing complexity make small issues harder to catch.
Complex system vulnerabilities pile up when complexity in identity management or complexity in compliance security slows work. Many organizations turn to cybersecurity simplification to keep focus sharp, cut fatigue, and improve cyber resilience through simpler routines.
What are practical signs that it’s time to simplify security architecture in a growing organization?
A growing team should simplify security architecture when cyber defense complexity and complexity in endpoint security keep rising. Watch for security incident response complexity, complexity in firewall management, and complexity in data protection taking longer each week.
If complexity in threat detection or complexity in access control slows decisions, or complexity and data breaches increase, it’s time for security complexity solutions and complexity security trade-offs that bring clarity back.
Conclusion
Security doesn’t need fancy bells and whistles to work. After training hundreds of dev teams, we’ve learned that cluttered defenses usually backfire. Each extra tool or config creates another spot where things break. Last week, a student’s company got hacked through a forgotten tool nobody maintained. Want to stop drowning in security chaos? Start by listing every security thing you’ve got running. Then ask, do we actually need this?
After training hundreds of dev teams, we’ve learned that cluttered defenses usually backfire. Every extra tool or config adds another point of failure.
Just last week, a student’s company got hacked through a forgotten tool nobody maintained.
Want to stop drowning in security chaos? Start by listing every security tool you’ve got running, then ask, “Do we actually need this?”
Join the Secure Coding Practices Bootcamp, a hands-on program that helps developers build secure software with clarity and confidence. No jargon, no fluff, just real-world skills that keep your systems safe.
References
- https://blog.barracuda.com/2025/06/02/new-global-business-research-security-sprawl-increases-risk
- https://www.guidepointsecurity.com/blog/diagnose-and-defeat-tool-sprawl/

