Defining and Managing Trust Boundaries for Stronger Security
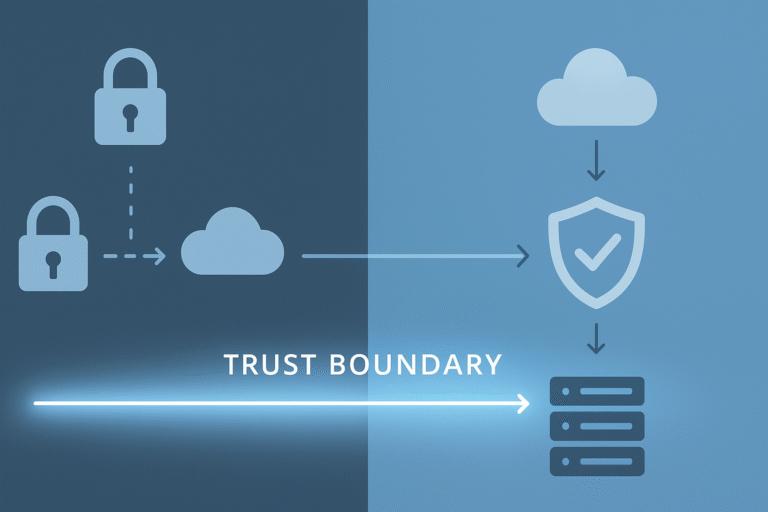
Trust boundaries mark the line where secure meets unsecure areas within software systems. These crossing points need special attention since they’re prime targets for attacks. While working with over 2,000 developers at our bootcamp, we’ve seen firsthand how proper boundary…
