Smarter Ways to Managing Trust Relationships Systems
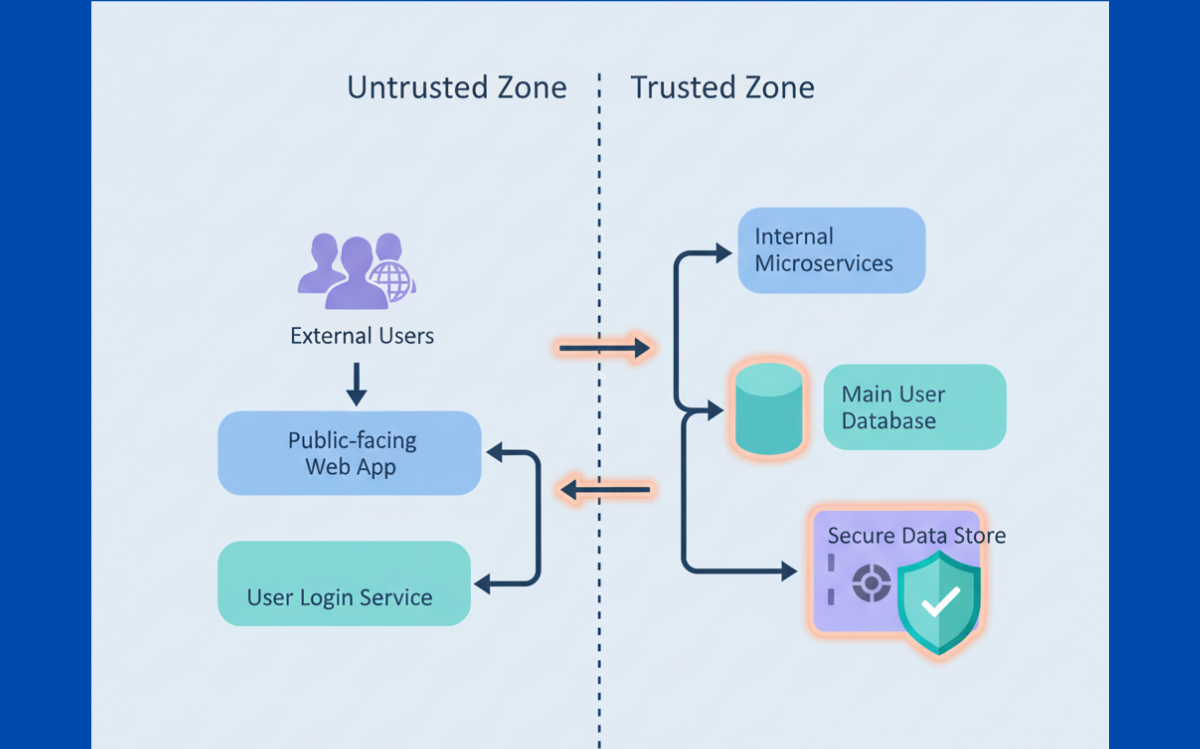
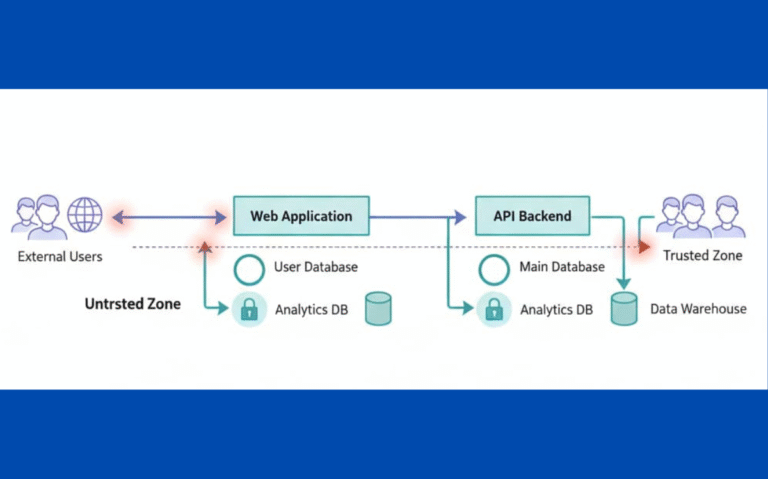
Trust relationships define which systems can access which resources, and under what conditions. In our secure development bootcamp, we see teams struggle not with the handshake itself, but with everything that happens after. We’ve watched devs wire up access between…

![Conceptual diagram of [validating data trust boundaries] - secure and unsecured data areas divided by a protective shield.](https://securecodingpractices.com/wp-content/uploads/2025/11/validating-data-trust-boundaries1-768x512.png)
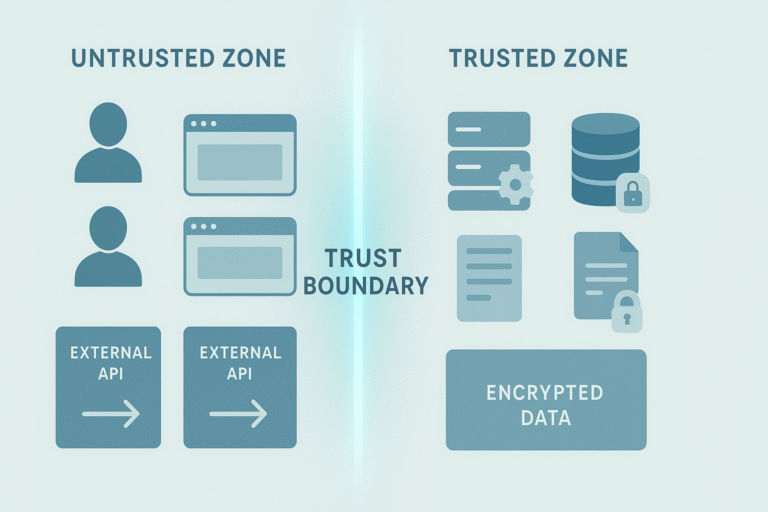
![Visualizing the security measures for [securing trust boundary crossings] between device, server, and database zones.](https://securecodingpractices.com/wp-content/uploads/2025/11/securing-trust-boundary-crossings1-768x512.png)