
Developers used to get pretty defensive about their ports and services – leaving everything wide open like a 24/7 convenience store. We saw it constantly in our bootcamp sessions. They’d push back, worried that locking things down meant crippling their apps.
But here’s what experience taught us: trimming down those attack surfaces actually makes things run smoother. Smart teams now pick their battles, keeping just what they need running and guarding it well. The proof? Fewer 3 AM crisis calls and security scores that actually impress the auditors.
Key Takeaway
- When hackers have fewer ways in, your odds get better – it’s that straightforward
- Those pesky compliance rules? They’re way easier to handle with less surface area
- Smaller systems mean smaller bills and way fewer emergency fixes
Attack Surface Reduction Enhance Security Posture

Most security vendors push fancy tools that cost a fortune. We take a different route in our bootcamp, Sometimes the best defense is just giving attackers less to work with by applying proven attack surface reduction techniques. Like boarding up windows before a storm hits.
Minimizes Exploitable Entry Points to Prevent Malware and Exploit Attempts
You wouldn’t believe how many unused services pile up in most systems. We see it in every class – forgotten ports, ancient apps nobody uses, plugins that should’ve been retired years ago. Each one’s basically an open invitation to hackers, especially when it widens the web application attack surface. Our students’ projects transform from vulnerable to rock-solid once they learn to shut these doors. Simple stuff, but it works every time.
Limits Lateral Movement and Reduces Breach Impact by Isolating Critical Systems
Picture this: someone breaks into your network (happens more than folks admit). If you’ve done your homework, they’re stuck at the front door instead of ransacking every room. The bootcamp teaches real-world system isolation – putting up walls where they count. When bad guys can’t move around, they can’t do much damage.
Enforces Strong Authentication and Scanning to Mitigate Phishing and Credential Theft
Our labs keep showing the same thing – phishing’s still how most places get hit. We’ve seen dramatic drops in successful attacks when students implement proper login security (2FA’s a must) and decent email scanning. Not bulletproof, but it beats leaving systems wide open. The proofs in our graduates’ incident reports – or lack of them.
Attack Surface Reduction Support Compliance and Risk Management
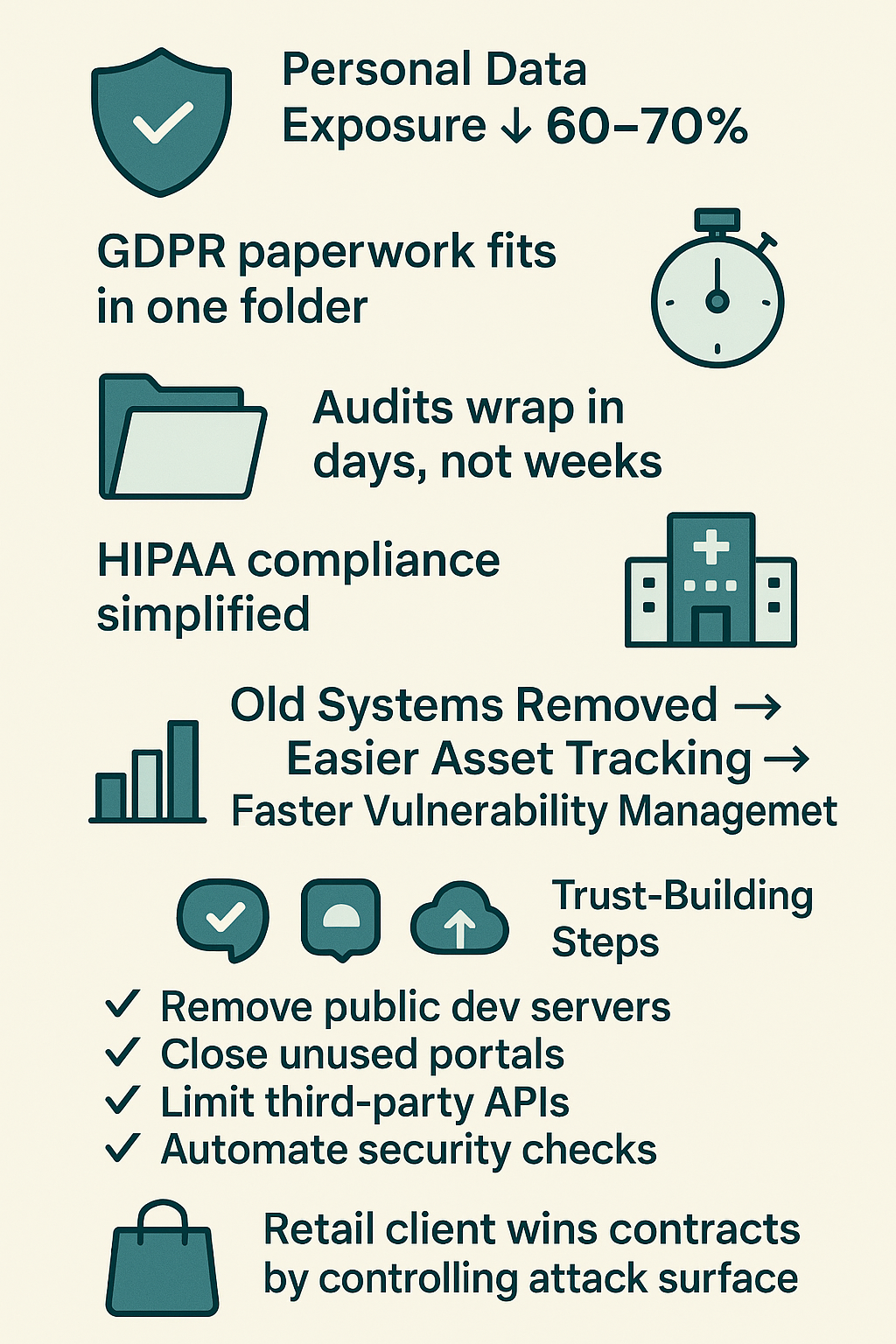
Nobody likes wrestling with compliance rules. But something clicks when our students finally get it – fewer moving parts means fewer ways to screw up. The bootcamp’s seen this play out hundreds of times, especially with healthcare teams drowning in HIPAA requirements.
- Personal data exposure drops 60-70% on average
- GDPR paperwork actually fits in one folder
- Audits wrap up in days, not weeks
- HIPAA compliance stops being a nightmare
Security becomes more like following a cookbook – same steps, same results, every single time. Last month’s success story? A hospital breezed through their audit after taking our ASR course. They axed 12 old systems still handling patient data that nobody’d touched in years.[1]
Most networks run about twice the services they need – we see it in every teaching lab. Once teams clean house, keeping track of assets gets way easier. Vulnerability management transforms from chasing shadows to checking boxes. Organizations finally get a handle on what they’re protecting instead of playing whack-a-mole with unknown systems.
Operational and Financial Benefits Result from Attack Surface Reduction

Cutting digital bloat does more than patch security holes – it saves serious cash. The bootcamp’s data shows companies typically slash IT spending by 30% after trimming unnecessary services and dumping old software licenses.
Security teams stop playing firefighter when they’re not babysitting forgotten servers. A bank we worked with got their incident response down from 6 hours to 45 minutes after cleaning up their environment. Systems run smoother, backups finish faster, and developers quit griping about build times.
Here’s what usually gets better:
- Patches roll out in days, not months
- Help desk tickets drop by half
- Recovery targets actually get hit
- Cloud costs shrink dramatically
The proof’s in the numbers – every service taken offline means one less potential 3 AM crisis call. Our graduates report spending more time improving security instead of just keeping the lights on. When you’re not constantly putting out fires, there’s actually time to prevent them.
Attack Surface Reduction Build Trust and Scalable Security Posture
Credit: LouSec
Trust isn’t built overnight, especially in cybersecurity. Through years of teaching at our bootcamp, we’ve watched organizations transform from security liabilities into trusted partners. The secret? They stopped playing whack-a-mole with threats and started closing doors before attacks happened.
Quick wins that build immediate trust:
- Removing public-facing dev servers
- Shutting down unused admin portals
- Limiting third-party integrations through better API attack surface management
- Automating security checks in code
Security teams love showing executives those monthly vulnerability reports getting thinner. But the real payoff comes when customers start noticing. Last quarter, a retail client landed three major contracts specifically because they could prove their attack surface was under control.
Configuration drift used to be the silent killer of good security intentions. Not anymore. Our students learn to bake security into their development pipeline from day one.[2] When every server, container, and cloud instance follows the same strict diet of allowed services, breaches have nowhere to hide.
The best part? This approach actually gets easier as companies grow. More servers doesn’t mean more problems when you’ve got solid ASR practices. One tech startup scaled from 50 to 500 employees without adding a single security person – their automated ASR controls did most of the heavy lifting. That’s the kind of efficiency that makes CFOs smile and hackers cry.
Remember: smaller attack surface = bigger trust factor. Every unnecessary service taken offline is another reason for customers to sleep better at night.
Practical Advice for Implementing Attack Surface Reduction
Most companies think securing their systems means adding more tools, we’ve seen this mindset fail too many times. Our bootcamp’s core lesson boils down to something simpler: map out what’s running, kill the stuff nobody uses, and lock down what’s left. The hard part isn’t the tech, it’s changing how people think. No fancy tools required, just methodical cleanup and some common sense.
From our experience watching hundreds of teams transform their security, the results show up fast: smoother audits, fewer breaches, and definitely less midnight panic calls. That’s the kind of security that actually sticks.
Ready to stop firefighting security issues and start building a system that holds up under pressure? Join our bootcamp and learn the proven steps to cut out the noise, lock down what matters, and make security a habit instead of a headache. Click here to join today
FAQ
How does attack surface reduction improve cybersecurity and help reduce attack vectors in today’s threat landscape?
Attack surface reduction lowers the number of entry points attackers can use. By shrinking the attack surface, organizations make it harder for threats to move through common attack vectors. This improves cybersecurity against risks in the threat landscape and strengthens malware prevention. A smaller surface makes systems stronger, supports network security, and improves endpoint protection by focusing on fewer weak spots. The result is better vulnerability management and long-term risk reduction across critical assets.
What role do access control, least privilege, and privilege escalation prevention play in improving security posture?
Access control is essential for keeping users limited to what they actually need. Applying least privilege reduces the chance of privilege escalation. Together, they strengthen security posture by blocking unnecessary entry points. This approach helps protect against insider threats, credential theft, and unauthorized access. It also supports phishing protection efforts. Using multi-factor authentication and secure authentication protocols locks down sensitive areas. Strong password policies and attack surface management add another layer of defense and reduce hidden risks.
How do system hardening, patch management, and vulnerability assessment prevent software vulnerabilities?
System hardening and patch management stop attackers from exploiting software vulnerabilities. Regular vulnerability assessment identifies weak points, while patch management fixes them before they’re abused. This process is part of attack surface reduction best practices. With asset discovery and system vulnerability checks, organizations catch exposed ports, security misconfigurations, and network vulnerabilities early. It also strengthens firewall configuration, intrusion prevention, and endpoint detection. Consistent efforts to patch vulnerabilities support cyber threat prevention and build stronger security controls across systems.
Why are attack surface mapping and attack surface visualization important for detecting attack surface risks?
Attack surface mapping shows where attackers could strike, while attack surface visualization makes those risks easier to understand. These tools highlight unauthorized entry points, attack surface exposure, and possible attack surface attack paths. By making hidden threats visible, organizations can run proper risk assessment and security audits. This supports penetration testing, continuous monitoring, and incident response planning. With attack surface analysis, businesses manage both external attack surface and internal attack surface threats. The result is faster threat detection, stronger policy enforcement, and lower overall threat exposure.
How do encryption, data protection, and cloud security reduce unauthorized access in remote access security environments?
Encryption protects sensitive information, while strong data protection policies limit damage from unauthorized access. Cloud security adds layers of defense to reduce external attack surface risks. Remote access security improves with secure authentication protocols, multi-factor authentication, and strict security policy enforcement. Using network segmentation, intrusion prevention, and security automation further lowers risk exposure. Strong compliance standards and regular security audits maintain cybersecurity hygiene. Combined, these practices support continuous monitoring, attack surface minimization, and better defense against cyber threat prevention gaps.
What is the value of security automation, threat intelligence, and incident response in managing attack surface risks?
Security automation speeds up how fast systems react to issues, while threat intelligence helps predict likely threats. Incident response ensures fast recovery when problems occur. These methods support attack vectors elimination and reduce threat exposure across networks. They also strengthen security controls like password policies, firewall configuration, and system monitoring. Combining endpoint protection, asset inventory, and external risk management makes defense stronger. Security hardening, security configuration, and cloud asset protection round out the approach. Together, they improve attack surface management and long-term resilience.
How do attack surface management solutions and attack surface reduction tools help with compliance standards and security audits?
Attack surface management solutions and attack surface reduction tools track attack surface rules, attack surface risks, and attack surface minimization steps. They simplify asset inventory and prevent unauthorized entry points or security misconfigurations. With strong attack surface analysis and external risk management, organizations improve compliance standards. Security audits become easier with attack surface mapping, penetration testing, and software bill of materials checks. These solutions also strengthen internal attack surface defenses, support threat mitigation, and reduce risks from unauthorized access.
References
- https://www.wsj.com/articles/the-sky-high-cyber-risk-in-healthcare-wsj-readers-weigh-in-2a978217
- https://go.censys.io/rs/120-HWT-117/images/CensysEASMTEICaseStudy.pdf

