Look, security doesn’t have to be rocket science. Most teams mess up by adding endless layers of protection that nobody understands or maintains properly. Been there, seen that disaster unfold. Instead, figure out what really needs guarding, maybe it’s customer data or your source code.
Set up basic barriers, check them like you check your email, fix what’s broken. We’ve watched small coding teams and big tech firms nail this approach. Stick around, we’ll show you the actual steps that work, minus the fancy buzzwords and complicated jargon.
Key Takeaways
- Over-engineering inflates costs and causes configuration errors, hurting security performance.
- A risk-based, simple design reduces complexity and improves usability.
- Regular review and balanced controls keep security agile and effective.
The High Cost of Over-Engineering

Last month, a client showed me their “ultra-secure” setup, a maze of security tools that actually made their system more vulnerable. Adding every possible security control sounds great on paper, but reality hits differently.
Organizations with fragmented stacks manage dozens of tools and face slower detection and containment; one analysis found stacks averaging 83 tools from 29 vendors correlated with longer time to identify and contain threats.[1]
Surveys show SOCs ignore 62% of alerts due to fatigue, highlighting how overload causes real risk. DBIR reports Errors (including misconfigurations) in 28% of breaches, a pattern that rises with complexity
- Over-engineered systems kill innovation speed.
- Users start bypassing security when it gets too annoying.
- Nobody can tell if you’re actually compliant anymore.
- Security isn’t about maxing out your defense stats, it’s about putting solid protection where it counts.
Risk-Based Approach: Prioritize What Matters
At our bootcamp, we drill this into every developer’s head: NIST recommends risk-based processes and least-privilege/least-functionality, design around what matters most before adding controls. You’ve got to think about what needs protecting and why. Map out where your crown jewels are, customer data, payment info, that sort of thing. Then figure out what happens if someone gets their hands on it.[2]
We learned this lesson training dev teams across different industries. Protecting internal lunch menus with the same intensity as credit card numbers? That’s just burning resources. Our students pick up this mindset quickly, it helps them build security that makes sense.
A solid risk-based strategy means:
- Putting your strongest controls where they’ll count most.
- Being smart about which risks you can live with.
- Spending your security budget where it matters.
Simplicity and Usability: Keep It Manageable
Credits: Steve Hook
Complex security systems fail because humans can’t handle them, period. Our training sessions constantly show this. When architects stack too many tools together, they create a mess nobody understands. Configuration mistakes pop up, everything slows down, and maintenance becomes a nightmare.
Through years of teaching secure coding, we’ve noticed that straightforward controls just work better. Teams actually follow the rules when they make sense. Take the least privilege, give people access to what they need, nothing more. This reflects the core of the keep it simple security principles that emphasize clarity and manageable controls. Simple idea, easy to grasp, hard to mess up.
Making security digestible means:
- Building controls anyone can understand.
- Avoiding tool overload, not every shiny new security product needs a home.
- Cutting out redundant security rules that just confuse people.
Secure coding fits perfectly here. Our bootcamp shows developers how to bake security into their code from day one. It beats trying to patch up holes later with complicated band-aids.
Balance Proactive and Reactive Measures
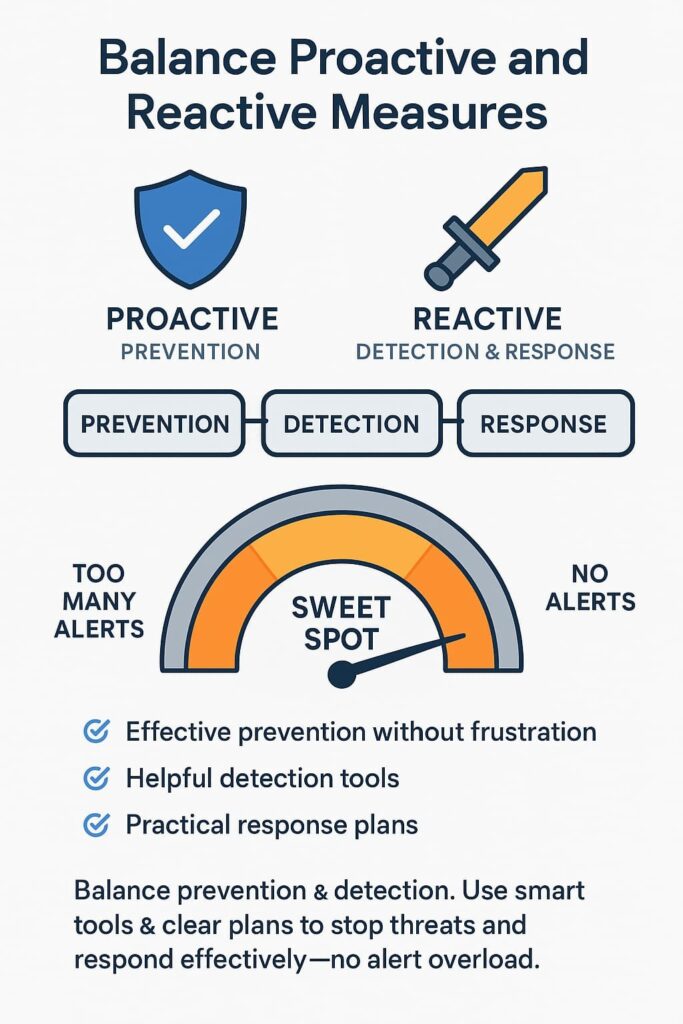
Security needs both a shield and a sword. Most teams we work with struggle because they’ve got too many reactive tools that don’t talk to each other. When something bad happens, they’re stuck playing detective instead of fixing problems.
In our courses, we teach teams to find the sweet spot between blocking threats and catching the ones that slip through. A tested game plan beats having fifty alerts screaming at you all day.
Finding that balance looks like:
- Setting up prevention that works without driving everyone crazy.
- Using detection tools that help rather than overwhelm.
- Creating response plans people can actually follow when things go wrong.
This approach echoes the importance of simplicity in security; balancing measures avoids overwhelming teams with complexity while strengthening defense.
Regular Review and Tuning: Stay Agile
Walking into a client’s security setup last week felt like entering a digital hoarding situation. Old firewall rules from 2019, duplicate tools running the same checks, and enough technical debt to make any dev cry. Security gets messy fast when nobody cleans the house.
Through teaching hundreds of developers, we’ve learned that regular security checkups catch problems before they blow up. Sometimes a security control that made perfect sense six months ago turns into dead weight. Our bootcamp teaches teams to schedule monthly audits, not the boring checkbox kind, but actual hands-on reviews.
Key moves to keep security lean:
- Trash controls that don’t pull their weight anymore.
- Tune your settings for speed and coverage.
- Roll with new threats without piling on extra junk.
Choosing the Right Tools
Picking security tools is like picking teammates, get it wrong and everything falls apart. After watching countless teams struggle with bloated security stacks, one thing’s clear: fancy features mean nothing if nobody uses them right.
Before pushing any new security tool at our bootcamp, we run it through real-world scenarios. Better to start with solid coding practices and smart design than throw money at shiny new products. Our students learn to build security from the ground up, not patch it on later.
Questions we ask before adding tools:
- Will this actually fix a real problem?
- Can the team use this without pulling their hair out?
- Does it play nice with our other security stuff?
Practical Advice: Avoiding Security Over-Engineering
Here’s what actually works in the field:
- Look at what could actually hurt your business, then fix that first.
- Make security so simple your junior devs get it.
- Mix prevention and detection, you need both.
- Check your security setup monthly, dump what’s not working.
- Pick tools that fit your team’s style.
Secure coding still sits at the heart of it all. Teaching developers to write secure code from day one beats trying to bolt on security later. Our graduates consistently build systems that need fewer band-aid fixes and run smoother.
The best security doesn’t look like Fort Knox. It looks like a well-oiled machine that adapts to new threats without breaking down. When teams focus on getting the basics right instead of chasing perfect security, they build something that actually works. This is a clear rebuttal to the complexity enemy of security, which shows how over-engineered defenses can backfire.
FAQ
How do I spot engineering risks before they slow my security team?
You can spot security over engineering early by watching for over engineered security systems that add complexity in cybersecurity without clear value. Look for unnecessary security controls, security control redundancy, and over engineering symptoms like rising security maintenance challenges or security performance impact.
Simple checks using risk-based security and lean security design help reduce noise and keep security system agility strong.
What’s the simplest way to keep security design balance without weakening protection?
Start with simplicity in security and security design principles. Focus on security threat focus, minimal viable security, and defense in depth only where it matters. Use security trade-off analysis, security resource allocation, and risk tolerance security to guide choices. This avoids complexity, lowers security overhead reduction needs, and reduces security configuration errors that come from too much complexity.
How can my team avoid unnecessary complexity in everyday security operations?
Teams avoid complexity by practicing security complexity reduction and security architecture simplification. Lean steps like security process streamlining, security tool consolidation, and clear security policy clarity stop security technical debt from growing. Use security lifecycle management and security operations optimization to cut bottlenecks and prevent security alert fatigue caused by confusing, overbuilt systems.
When does security cost optimization matter most in preventing over engineering?
Security cost optimization matters when security project management grows heavy with security design trade-offs that no longer match real risks. Look at security investment balance, security resource prioritization, and cost-benefit security analysis to guide decisions. This keeps security governance focused, supports adaptive security architecture, and avoids security innovation barriers that appear when too many layers slow work.
How do I keep security effective while still avoiding over engineered controls?
Use security effectiveness metrics, security performance metrics, and security by design to keep controls sharp. Pair them with security framework adoption, principle of least privilege, zero trust architecture, and minimal attack surface goals.
Add steady security patch management and security incident response planning. These risk-adjusted security steps prevent security system bottlenecks while keeping security usability and security team collaboration strong.
Conclusion
After training dev teams for years, we’ve noticed a pattern: the most secure systems aren’t the most complex ones. Fancy security setups often backfire, they cost more, break easily, and slow down incident response. Smart teams focus on protecting what matters, using straightforward controls that actually work.
Through our bootcamp’s secure coding program, we’ve seen that building security right the first time beats piling on fixes later.
Smart teams focus on protecting what truly matters, using clear, effective controls that actually work. From our Secure Coding Bootcamp, we’ve seen time and again: building security right the first time beats patching it later.
So take a look at your setup, could you simplify and still stay safe?
Join the Secure Coding Practices Bootcamp to learn how to build secure software from the start.
References
- https://www.techradar.com/pro/security-tool-bloat-is-the-new-breach-vector
- https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r5.pdf

