Software security shouldn’t be an afterthought, that truth stands after years of teaching secure development. Many of our boot-camp students arrive only after suffering security breaches which were avoidable. Embedding security into software demands familiarity with secure design patterns and coding practices designed to anticipate attacks before they occur.
Over seven years of running mock attack scenarios, we’ve seen how basic security oversights create easy entry points for malicious users. The good news? When developers integrate security early in the development cycle, threat surfaces shrink dramatically. But theory alone won’t cut it. Read on to discover battle-tested patterns that form the foundation of hack-resistant applications.
Key Takeaways
- Secure coding practices form the foundation for applying secure design patterns effectively.
- Core security principles like least privilege and defense-in-depth build resilient architectures.
- Practical design patterns such as input validation and secure error handling prevent common vulnerabilities.
The High Cost of Insecure Design
In software projects I’ve been part of, ignoring security early on always causes headaches later, sometimes severe losses. Data breaches don’t just hurt finances; they damage trust and reputation, often beyond repair. For example, studies show the average global cost of a data breach reached about US$4.88 million in 2024, factoring in detection, response and legal consequences.
These costs remind us why applying secure design patterns is critical. They aren’t just abstract ideas; they’re practical tools that help us avoid these pitfalls. By integrating security right from the start, we reduce vulnerabilities and build systems that can withstand attacks.
- Data breaches cause financial losses averaging $4 million per incident.
- Vulnerabilities often arise from poor design choices and coding errors.
- Incorporating security design patterns early can prevent these costly mistakes.
Understanding this sets the stage for why secure design patterns must be part of your software development approach.
Core Security Principles: The Foundation
Credit: Serket Studios
Secure design patterns rest on a set of core principles. We’ve found these principles guide everything we do when building secure systems, and they should be your starting point too. As documented in literature, the Principle of Least Privilege is foundational (see Gambo & Almulhem 2025).
Principle of Least Privilege
The idea here is simple but powerful: give users and system components only the access they absolutely need. This limits damage if an account is compromised. In one project, our database users were restricted to only specific tables relevant to their role. That meant even if an attacker gained access, the potential harm was limited.
This aligns well with secure design principles that emphasize minimizing privileges to reduce risk and improve overall system resilience.
Defense-in-Depth
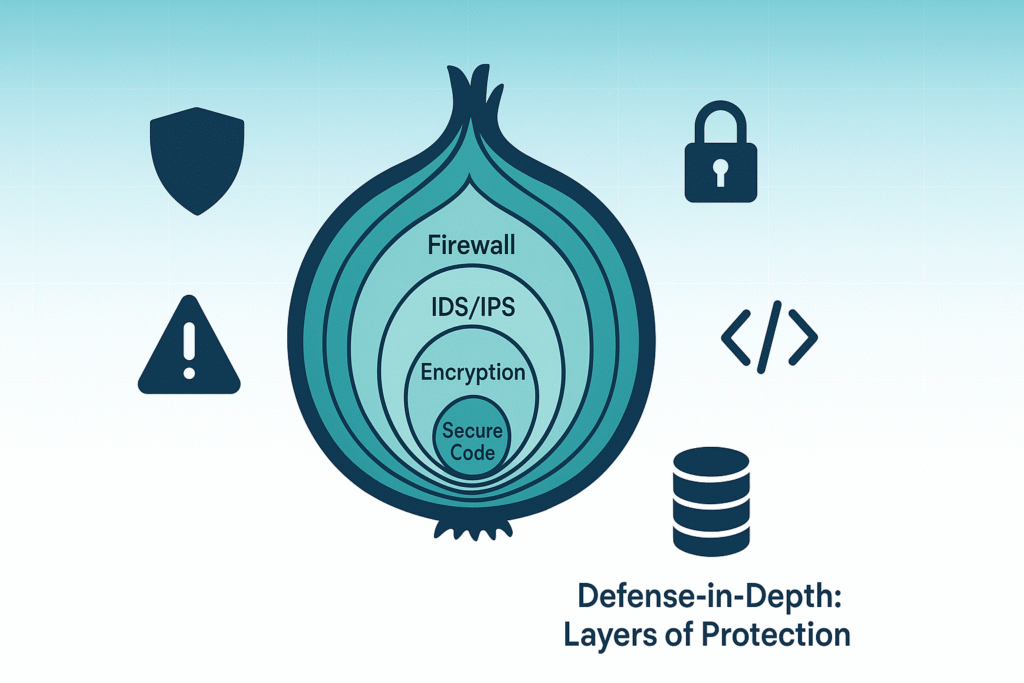
Imagine your system as an onion with multiple layers of protection. Firewalls, encryption, intrusion detection, all these layers overlap. If one fails, others still protect the system. We’ve seen this layered approach prevent breaches in environments where single-layer defenses would have failed.
This concept forms a cornerstone of secure software design principles, where overlapping controls ensure robust protection against evolving threats.
Zero Trust
No one is trusted by default, even inside your network. Continuous verification of identity and permissions is essential. This principle challenges old assumptions about “trusted networks” and forces us to build more secure authentication and authorization checks.
More than 80% of data breaches involved data stored in the cloud; many of these were caused by mis-configurations or design oversights in cloud environments. (1)
Secure Defaults
Systems should come configured securely out of the box. Many users never change default settings, so secure defaults protect them by default. We always check default configurations on new deployments to avoid exposing vulnerabilities inadvertently.
Minimizing Attack Surface Area
Reducing entry points means disabling unnecessary features and services. We regularly audit our systems to turn off anything not essential, shrinking the window attackers can exploit.
Complete Mediation
Every request for access must be checked, every time. This prevents unauthorized access based on outdated credentials or cached permissions.
Failing Securely
When failures happen, systems should default to secure states. This avoids exposing sensitive information during errors, a common oversight we’ve seen cause serious breaches.
Secure Design Focus Areas: A Holistic View
Security design isn’t just about code; it covers the entire environment. We focus on these areas to ensure a comprehensive approach.
Context
Understanding the application’s role and its data sensitivity is critical. We often perform threat modeling and business impact assessments to identify risks. This upfront work guides how we apply security controls throughout the system.
Research shows that mis-configurations (such as default settings or open ports) contribute significantly to breaches, one dataset found mis-configurations accounted for ~21% of error-related breaches. (2)
Components
Choosing the right libraries and third-party services matters. We always check licenses and maintenance status before integration. For example, integrating an outdated cryptographic library can undermine your whole security posture.
ProTip: Always verify third-party library licensing and update policies before use.
Connections
How your app communicates with other systems must be secure. We rely on HTTPS and proper data segregation to protect data in transit and avoid leakage.
Code
Implementing secure coding practices is non-negotiable. Input validation, secure authentication, cryptography, these are basics we never skip. Avoiding hardcoded secrets and keeping dependencies updated are equally vital.
Configuration
Secure deployment means enforcing least privilege, applying patches promptly, and planning incident response. We document and review configuration settings regularly to maintain secure defaults.
Key Secure Design Patterns: Practical Solutions
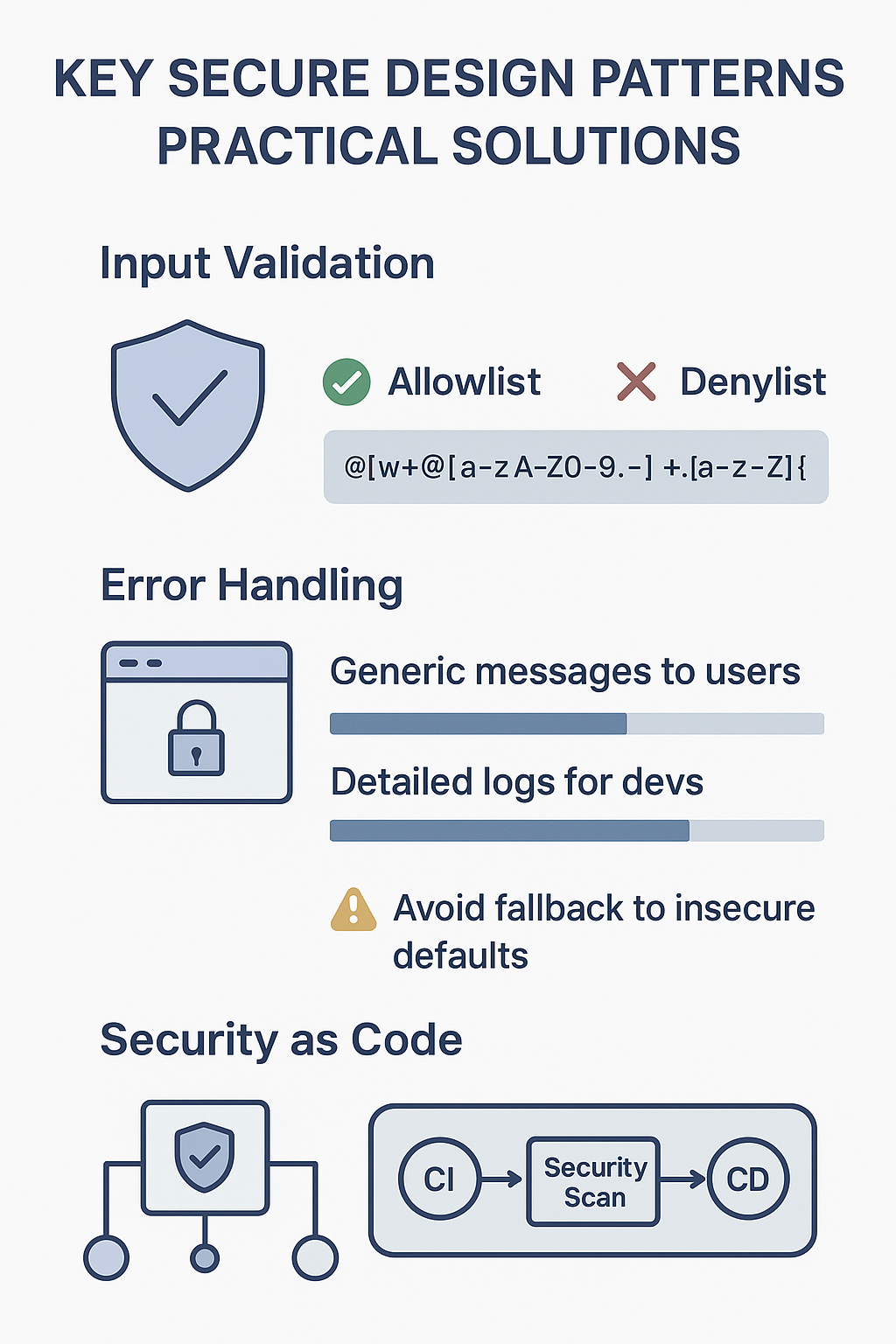
Now to the patterns themselves. These have helped us prevent common vulnerabilities time and again.
Input Validation
Before processing any data, validate it thoroughly. Use syntactic checks like format validation and semantic checks like business logic validation. We prefer allowlists over denylists because they’re more reliable.
For example, when validating email addresses, a regular expression that matches valid formats prevents injection attacks. This early validation stops malformed or malicious data from ever reaching sensitive subsystems.
Error Handling
Never expose system details in error messages. We always ensure users see generic messages, while detailed errors are logged securely for developers. This prevents attackers from gleaning system information that could aid an attack.
Also, error handling should never throw the system into an insecure state. We’ve seen cases where exceptions caused fallback to insecure defaults, something to avoid at all costs.
Security as Code
Automating security controls within the development pipeline strengthens enforcement. We integrate vulnerability scanning and policy checks directly into our CI/CD workflows. This way, security becomes part of the build process, not an afterthought.
Many teams find that adopting OWASP secure design principles helps structure these automated checks effectively, embedding security deeply in the software lifecycle.
TL;DR: Secure Design Pattern Summary
| Pattern | Description |
| Input Validation | Ensures data is properly formatted before processing, preventing injection attacks. |
| Error Handling | Prevents sensitive information leakage and ensures system stability during errors. |
| Security as Code | Automates security checks and policy enforcement throughout the development lifecycle. |
FAQ
What are the key benefits of using secure coding practices and design pattern security in software development?
Using secure coding practices together with design pattern security means you build systems with fewer flaws from the start. It helps stop issues before they show up in production, improves reliability, and supports software security architecture by embedding security in design. By focusing on secure software development early, you reduce costs for fixes later and build trust in your application.
How does threat modeling fit within a secure software lifecycle and application security design?
Threat modeling is a key step in a secure software lifecycle and application security design because it helps you identify risks up front. You map out how attackers might work, review your system’s architecture, and apply security by design principles. With threat modeling you can integrate security architecture patterns and secure design principles before coding begins, which reduces future vulnerabilities.
Why is the principle of least privilege design and access control patterns important in secure system design?
Least privilege design and access control patterns ensure that users and components only get the permissions they need, no more, no less. In secure system design this limits what attackers can do if they gain access. Using secure identity management, separation of duties design and authorization design builds architectures where faults don’t escalate, making the system more resilient.
What role do secure input validation security and secure session management play in secure design methodology?
Secure input validation security and secure session management are core parts of secure design methodology because they handle common attack points. Validating inputs helps stop injections and malformed data, while secure session management ensures user sessions aren’t hijacked or misused. Together they support secure software engineering and secure code review, making your system more robust.
How do security pattern library and security pattern benefits contribute to software vulnerability prevention and incident response design?
A security pattern library gives you reusable solutions like authentication patterns, secure deployment patterns and secure logging practices. This supports software vulnerability prevention and incident response design by letting you apply proven approaches rather than reinventing solutions. By integrating security pattern templates into your secure software architecture framework you achieve better security assurance design across the development lifecycle.
Conclusion
Applying secure design patterns is more than a checklist. It’s a mindset that shifts how we approach software development, from reactive fixes to proactive defense. Our own work has shown that when you embed secure coding practices and design principles early, the software is easier to maintain, less prone to vulnerabilities, and more trustworthy.
If you want to build software that stands strong against threats, start with these patterns. They help you focus on what matters, protecting data, controlling access, and maintaining integrity throughout the software lifecycle.
Next time you design a system, ask yourself: have I integrated these secure design principles? Are my components, connections, and code aligned with best practices? By doing so, you’re not just writing software, you’re crafting resilience.
By doing so, you’re not just writing software, you’re crafting resilience. Ready to take your skills further? Join the Secure Coding Practices Bootcamp to learn hands-on methods for applying secure design patterns and building safer, more resilient software from day one.
References
- https://mitsloan.mit.edu/ideas-made-to-matter/mit-report-details-new-cybersecurity-risks
- https://ico.org.uk/about-the-ico/research-reports-impact-and-evaluation/research-and-reports/learning-from-the-mistakes-of-others-a-retrospective-review/errors/

