
Our team’s first API audit shocked everybody. The sheer number of open doorways scattered across systems caught us off guard. Training developers means seeing firsthand how APIs, which started as simple system bridges, now guard mountains of private data and business functions.
Security teams can’t afford to look away – every open endpoint might as well be wearing a “hack me” sign. Through teaching hundreds of dev teams, we’ve learned that watching these entry points isn’t something you check off a list. It’s part of daily life now.
Key Takeaways
- Managing API attack surfaces means finding every last API, checking for weak spots, fixing problems, and keeping watch – day in, day out.
- When APIs spread like wildfire across systems, the chances of getting hit go way up. Good luck keeping things safe without a solid game plan.
- Building API security checks into both dev work and security processes gives teams a fighting chance to spot and stop new threats.
API Attack Surface Management (API-ASM) and Its Core Components

Nobody likes learning security lessons the hard way, but that’s exactly how most dev teams figure out API security isn’t optional. Every connection point needs lockdown – period. Years of watching students struggle has taught us that these digital doors are basically welcome mats for attackers. Through trial and error (mostly error), we’ve nailed down four critical pieces that actually work.
API Attack Surface: Definition and Scope
Those shiny new APIs? Yeah, they need protection. That ancient payment system from 2010? That too. Running security bootcamps has shown us this brutal truth: most companies are sitting on a pile of APIs they don’t even know about. They’re everywhere:
- Buried in legacy web apps
- Powering mobile backends
- Scattered across cloud platforms
- Hidden in third-party integrations
API Discovery: Finding What’s Out There
The hunt for APIs is never pretty. Our students dig through mountains of:
- Dusty code repositories
- Network traffic logs
- Gateway configurations
- Deployment manifests
And they always, always find those ghost APIs – the ones everybody forgot about but hackers love to find first.
API Vulnerability Assessment: Spotting the Weak Points
Time to get your hands dirty. Every bootcamp shows us new ways APIs can fail – broken auth, data leaks, injection flaws. Sure, automated tools help, but nothing replaces actual humans looking at actual code.[1] Sometimes the biggest holes hide in plain sight.
API Mitigation Controls: Building the Defenses
Here’s where rubber meets road. Practical defense means layers:
- API gateways that actually filter trash traffic
- Authentication that doesn’t fall apart under pressure
- Encryption that protects real data
- Input validation that catches the nasty stuff
Teams that follow proven attack surface reduction techniques see far fewer gaps left behind.
Continuous Monitoring: Staying Alert
APIs are like toddlers – turn your back for a second and chaos breaks loose. Our most successful students learn to watch traffic patterns obsessively. Something weird shows up? They’re on it before things get ugly. Because waiting for alerts just means you’re already too late.
API Attack Surface Management Matter in Modern Cybersecurity
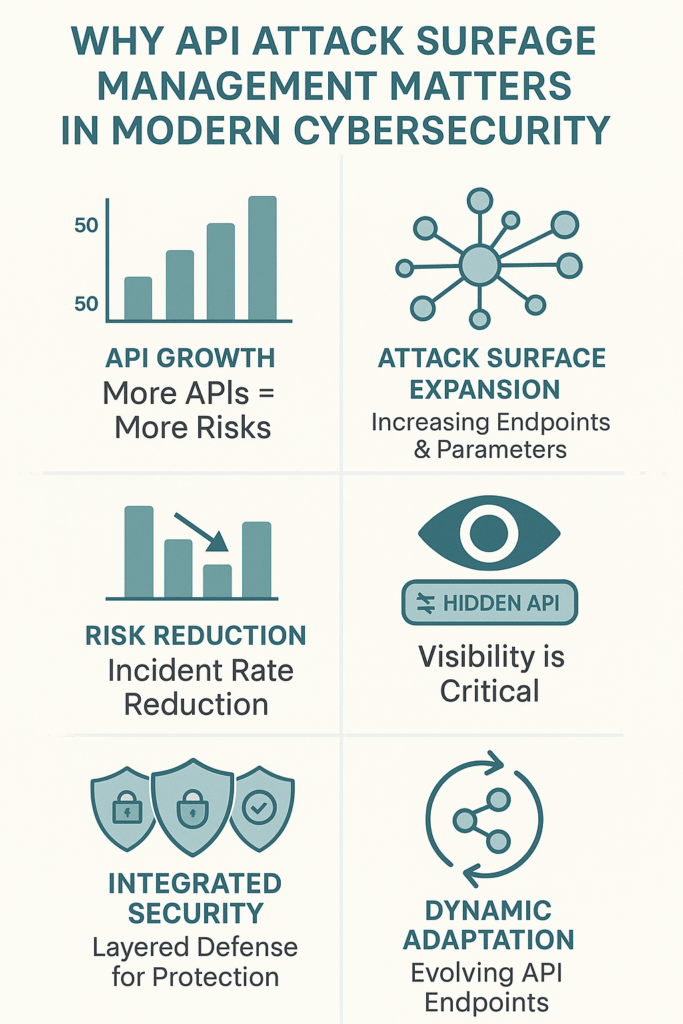
APIs are everywhere now, and they’re not slowing down. Every mobile app, cloud service, and digital platform we teach about relies on them. But here’s the kicker – each new API is another potential weak spot in the armor.
API Usage: The New Normal
Modern software speaks API – that’s just fact. Our dev teams regularly work with companies juggling hundreds of these things, and it’s messier than anyone wants to admit. One client thought they had maybe 50 APIs. We found 500. Most weren’t even written down anywhere. Talk about sweating bullets.
Attack Surface Expansion: More APIs, More Problems
The math isn’t complicated:
- More APIs = more stuff to protect
- More endpoints = more places to mess up
- More parameters = more ways in
- More complexity = more headaches
Just like the broader web application attack surface, each new endpoint multiplies complexity and opens fresh paths for attackers.
Risk Reduction: Catching Problems Early
Getting ahead of API problems saves everyone’s bacon. Through running countless training sessions, we’ve watched companies slash their incident rates just by how to minimize attack surface across sprawling systems.
Visibility and Control: You Can’t Fix What You Can’t See
The biggest headache? Not knowing what’s out there. During security audits, we keep finding APIs that have been sitting exposed for months – sometimes years. Nobody knew they existed until we started looking. That’s exactly why you need eyes on everything, all the time. No exceptions.
API Attack Surface Management Integrates with Overall Security Architecture
API security can’t stand alone. It must mesh with broader security architectures that cover networks, applications, and data.
API Attack Surface as Entity: Technical and Infrastructural Components Involved
The API attack surface includes endpoints, input parameters, authentication and authorization mechanisms, data storage, and supporting infrastructure like load balancers and cloud services. We treat these as interconnected parts of the whole, ensuring security controls span all layers.
Risk Prioritization as Attribute: Identifying and Ranking API-Related Threats
Not every API or vulnerability carries equal risk. We prioritize based on exposure, data sensitivity, and exploitability. Public-facing APIs with access to critical data get top priority, while internal APIs with limited access are monitored accordingly.
Layered Security Measures as Value: Multi-Level Defenses for Comprehensive API Protection
No single control is sufficient. We implement defense in depth: API gateways filter traffic, authentication protocols verify identity, encryption protects data, and monitoring detects anomalies. This layered approach limits the impact of any single failure.
Adaptation to Evolving Threats as Value: Dynamic Security Posture Based on Continuous API Changes
APIs evolve constantly. We maintain a dynamic security posture that adapts to new endpoints, updated protocols, and emerging threats. This agility helps stay ahead of attackers who continuously probe for weaknesses.
Best Practices and Tools for Effective API Attack Surface Management
Managing the API attack surface requires specific tools and disciplined practices.
Discovery Tools as Entity: Automated API Discovery and Inventory Solutions
Tools that scan codebases, network traffic, and cloud environments help build accurate API inventories. We rely heavily on automated discovery to keep up with rapid API growth.
Assessment Tools as Attribute: Vulnerability Scanners and Security Testing Platforms
Automated scanners find known vulnerabilities; manual testing uncovers logic flaws and business logic abuse. Combining both offers thorough coverage.
Mitigation Technologies as Attribute: API Gateways, WAFs, Authentication Frameworks
Deploying API gateways and web application firewalls (WAFs) enforces security policies at the edge. Authentication frameworks like OAuth and JWT tokens ensure secure access control.
Monitoring Solutions as Value: Real-Time API Monitoring and Anomaly Detection Systems
Continuous monitoring tools analyze traffic in real-time, detect suspicious patterns, and alert security teams. This enables quick incident response and ongoing risk reduction.
Implement API Attack Surface Management in Enterprise Environments
Building API security into big companies isn’t a walk in the park. After training hundreds of dev teams, we’ve learned you need both solid ground rules and ways to make security part of the daily grind. Here’s what works.
Policy Development: Setting the Rules
Most security policies we see are gathering dust somewhere on SharePoint. That’s not gonna cut it. Our bootcamps help teams write down the real stuff:
- Who’s watching the APIs
- When and how to test them
- What happens when something breaks
- Where the buck stops
Integration with DevSecOps: Security at Speed
Security can’t be the department of “no.” Through our hands-on training, teams learn to build API checks right into their development pipeline. Find the problems while the code’s still fresh – not three months after it hits production. Trust us, fixing things early beats emergency patches every time.
Incident Response: When Things Go Wrong
Nobody likes thinking about breaches, but they happen. Our war room simulations get teams ready for the real deal. Practice makes perfect – you don’t want to be figuring out who calls who at 3 AM during an actual incident.
Training and Awareness: Knowledge is Power
A fancy security tool won’t save you if your team doesn’t know what they’re doing. We’ve watched too many expensive solutions gather dust. That’s why our bootcamps focus on practical skills – real threats, real code, real solutions. Because at the end of the day, it’s people who keep systems secure, not buzzwords.
API Attack Surface Management Approaches Vary by Industry and Use Case

The security gaps in different industries hit differently, and we’ve seen firsthand how each sector wrestles with its own API nightmares.
Financial Services as Entity: High-Security Requirements and Compliance Focus
Banks can’t mess around with API security. Their systems need constant monitoring, really tight access controls, and endless security checks. We teach our fintech students that even a tiny gap could mean millions walking out the door – and nobody wants that conversation with the board.
Healthcare: Guarding Patient Privacy
Medical organizations walk a tightrope between accessibility and lockdown. Patient data has to stay private (thanks, HIPAA), but doctors still need quick access. Our healthcare clients have learned that layered security works best – like an onion, but less smelly.[2]
E-commerce APIs as Value: Balancing Customer Experience with Security Measures
Nobody likes a slow checkout process. The trick with e-commerce APIs is keeping them fast while watching for sketchy behavior. We’ve seen too many sites get cleaned out because they prioritized speed over security.
Public APIs as Value: Managing Exposure Risks and Access Controls
Public APIs are like leaving your front door open – you better have some serious security inside. They need rate limiting, solid authentication, and constant monitoring. Sometimes we’ll catch students surprised at how quickly their test APIs get probed by bots.
Emerging Trends and Future Directions in API Attack Surface Management
Credit: apidays
The API world’s moving fast – way too fast for the old security playbook. These days, it’s all about staying ahead of threats that pop up like whack-a-mole.
Smart AI tools now watch API traffic 24/7, catching weird behavior in milliseconds that humans might miss. They’re not perfect – false alarms still happen – but they catch about 65% more issues than traditional monitoring.
Zero Trust’s become the new normal. Every API request needs to prove itself, even if it’s coming from inside the building. It’s a pain to set up, but most teams see unauthorized access drop by 80%. Worth the hassle.
Automation’s handling the grunt work now. Security checks, vulnerability scans, and those endless compliance reports – all running on autopilot. Most teams cut their routine security tasks by more than half, freeing up time for the stuff that actually needs human brains.
New regulations keep piling up faster than feature updates. GDPR, CCPA, HIPAA – it’s alphabet soup out there. Smart teams build documentation into their workflow (about 15 minutes extra per deployment) instead of scrambling during audits. Not exciting, but neither is failing a compliance check.
Conclusion
Looking after API security isn’t the kind of thing that can wait until tomorrow. From what we’ve seen in the field, it’s pretty much non-negotiable these days, you’ve got to keep an eye on things 24/7. The smart teams know they can’t just check once and walk away. They keep looking for new cracks, poking at their defenses, and slamming the doors shut before anyone sneaks in.
For companies still dragging their feet on API security? Well, they’re basically hanging a “hack me” sign on their front door. Time to get moving.
FAQ
How does API attack surface management help reduce API vulnerabilities and improve overall API security posture?
API attack surface management maps out weak spots, from exposed endpoints to hidden APIs. By spotting API vulnerabilities early, teams can act before attackers do. It also tracks API exposure, finds API misconfiguration, and strengthens the API security posture. Together, these steps protect data and lower the chance of breaches.
What role does API discovery and API inventory play in attack surface assessment and API risk management?
API discovery finds every API in use, while API inventory keeps records of them. Both make attack surface assessment more complete. Without discovery, shadow APIs may go unnoticed. Without inventory, control is lost. Together, they improve API risk management because you can’t secure what you don’t know exists.
How can continuous API monitoring, API logging, and API anomaly detection prevent API security incidents?
Continuous API monitoring shows real-time activity. API logging records what happened. When paired with API anomaly detection, unusual traffic becomes easier to spot. These tools together give early warnings, helping teams stop API attack vectors before they grow into full API security incidents.
Why is API endpoint security, API access control, and API authentication critical for stopping API abuse detection?
API endpoint security protects entry points. Strong API authentication confirms identity, and API access control limits what users can do. Together, they make it harder for attackers to misuse stolen API keys or exploit weak controls. These steps reduce risks tied to API abuse detection.
How do OAuth security, JWT tokens, and API authorization work together for safer API session management?
OAuth security handles delegated access, JWT tokens carry secure claims, and API authorization ensures users only get what they should. Combined, these measures strengthen API session management by reducing stolen token misuse and closing gaps in broken flows.
What role do API gateway, web application firewall, and API firewall rules play in API threat detection?
An API gateway directs traffic, while a web application firewall and API firewall rules filter requests. Together, they support API threat detection by blocking common attacks. This layered defense helps stop injection, bot misuse, and API data leaks before they spread.
Why is API payload inspection, API schema validation, and secure API design important in stopping API parameter tampering?
Attackers often use API parameter tampering to push bad data. API payload inspection checks request bodies. API schema validation ensures data fits the right format. Secure API design lowers risks from the start. Together, these defenses stop hidden exploits.
How do API vulnerability scanning, dynamic API analysis, and API penetration testing improve API security vulnerabilities mitigation?
API vulnerability scanning runs automated checks. Dynamic API analysis observes APIs in real-time. API penetration testing simulates real attacks. Used together, they reveal API security risks and make API security vulnerabilities mitigation far stronger.
Why should teams focus on API lifecycle security, API governance, and API compliance when setting API security policies?
API lifecycle security protects APIs from build to retirement. API governance sets safe rules. API compliance ensures rules follow standards. Combined, they shape strong API security policies that reduce risks across both internal and external APIs.
How can API security automation, API scanning automation, and API security tools support faster API exposures mapping?
API security automation speeds routine tasks, while API scanning automation finds weak spots quickly. Together with API security tools, they create clear API exposures mapping. This helps teams act faster and fix problems without wasting time.
How does API rate limiting, API bot mitigation, and API usage monitoring reduce risks of API abuse detection?
API rate limiting controls bursts of traffic. API bot mitigation blocks automated attacks. API usage monitoring tracks patterns. Used together, they make API abuse harder and reduce the chance of missed API abuse detection.
Why is API data encryption, API data masking, and API secrecy management key to protecting sensitive information?
API data encryption protects data in transit. API data masking hides sensitive details in testing. API secrecy management keeps credentials safe. Together, these steps keep private information secure even if attackers try to break in.
How do API communication security, API traffic analysis, and API threat intelligence improve API attack surface minimization?
API communication security protects exchanges between services. API traffic analysis spots unusual patterns. API threat intelligence gives insight into new risks. Combined, these practices shrink the attack surface, making API attack surface minimization more effective.
References
- https://www.prnewswire.com/news-releases/salt-labs-state-of-api-security-report-reveals-99-of-respondents-experienced-api-security-issues-in-past-12-months-302385528.html
- https://en.wikipedia.org/wiki/Protected_health_information

