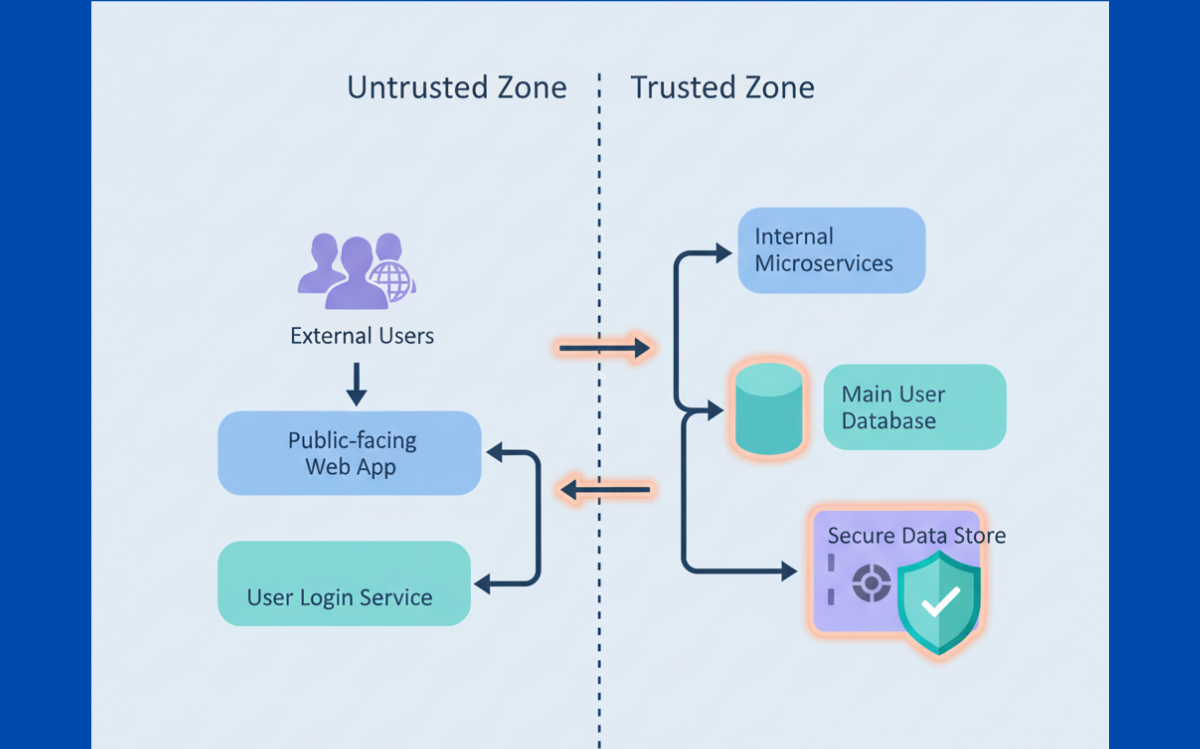
Trust boundaries are the invisible lines between things that trust each other and things that shouldn’t. A user’s computer trusts certain servers, but not others. Networks have zones, and one zone doesn’t automatically trust another. Without these lines drawn out, you’re guessing where attackers enter and where to put your strongest locks.
You miss the spots that matter most. Get them right, though, and suddenly your defenses have a shape. You know which doors need steel, which data needs guards, how an attacker might hop from one trusted zone into another. The real question: where does suspicion actually belong in your setup?
Key Takeaways
- Trust boundaries mark where trust changes in a system, revealing critical security points.
- Defining these boundaries helps prioritize risks and enforce access controls effectively.
- Proper boundary mapping supports compliance, reduces privilege escalation, and improves threat modeling accuracy.
Grasping What Trust Boundaries Really Are
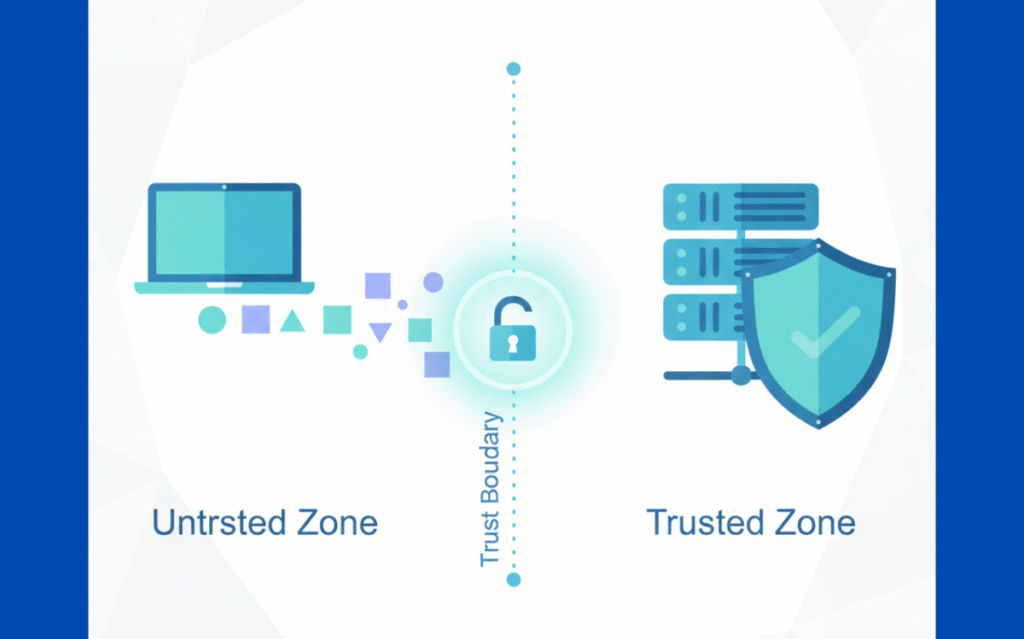
We’ve noticed something interesting when we work through threat modeling with students: trust boundaries aren’t some abstract concept. They’re the actual places where your system decides whether to believe what’s coming at it.
Picture data moving from a user’s laptop to a cloud server. That handoff point? That’s a defining and managing trust boundaries moment. The line gets drawn because one side (the user’s device) operates under different rules than the other side (the cloud infrastructure). These boundaries matter because attackers know exactly where to look. They hunt for those transition points where systems get lazy about verification.
Without mapping your trust boundaries, you’re essentially leaving doors unlocked without knowing it. The walls of your castle stay unmapped. We’ve seen countless systems fail because teams couldn’t answer a simple question: where does our trusted zone actually end?
Here’s what makes them worth your time:
- They show you where strict validation has to happen.
- They reveal your attack surface in concrete terms.
- They dictate how you should segment networks and control who accesses what.
Pinpointing and Defining Trust Boundaries
When we start threat modeling, identifying these boundaries comes first. We examine the system’s architecture and ask ourselves: where does the trust level shift? Your answer might look like this:
- Between an internal database and an external API that talks to it.
- Between admin users who can change everything and regular users who can’t.
- Between different microservices when some have higher privilege levels than others.
These shifts tell you everything. They’re where attackers concentrate their efforts because they’re where systems often stumble.
We think of it this way when explaining it to our students:
- Internal network versus external users hitting it.
- High privilege modules talking to low privilege ones.
- Cloud storage compared to servers sitting on your own premises.
Each boundary becomes a security checkpoint. Your data flows through potentially risky passages at these points, and you need to know every one.[1]
Managing Risk and Allocating Resources
Credits: CBT Nuggets
Once we map these boundaries, our security strategy actually gets focused. Understanding what are trust boundaries security helps us prioritize where to allocate resources. Not every part of a system carries equal risk or equal value. We’ve learned that trust boundaries show you where a breach would actually cause damage.
Focusing resources here means several practical things happen:
- We reduce exposure by tightening controls at crucial connection points.
- We stop wasting effort protecting low-risk areas that don’t matter much.
- We strengthen our overall position by addressing what attackers actually target.
Think about your home. You lock the front door because people use it. The basement window? Probably stays unlocked because nobody goes that way. Your system works the same.
Enforcing Security Policies at Boundary Points
When something crosses a trust boundary, you have to treat it as untrusted until it proves otherwise. This mindset shapes everything we teach about security policies at these crossing points.
Data coming over these lines needs rigorous checks. Authentication verifies who’s asking. Validation filters what they’re sending. Authorization confirms they’re allowed to do it.
Our approach relies on controls like these:
- Multi-factor authentication to confirm identities beyond doubt.
- Role-based access control that limits what each person can touch.
- Data validation at entry points that catches malicious inputs before they spread.
The rule we follow: assume everything crossing a boundary might be hostile. Injection attacks, privilege escalation, unauthorized access, they all start at these boundaries. Getting them right stops most of them cold.
Compliance Demands Clear Trust Boundaries
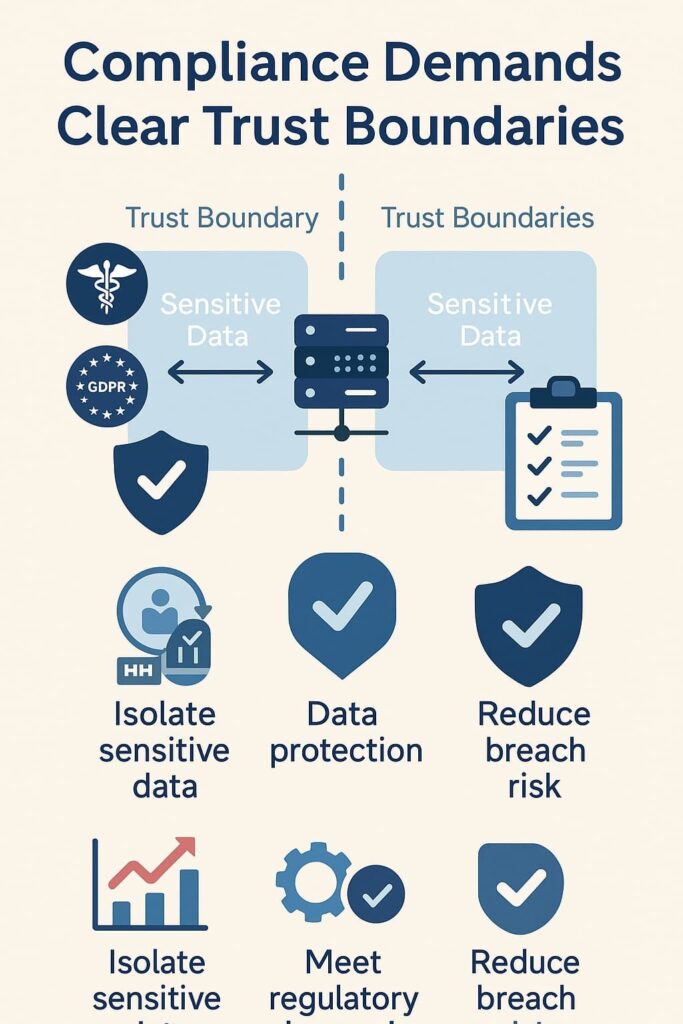
Regulators don’t mess around. HIPAA, GDPR, and similar frameworks all demand that organizations keep sensitive data separated and protected with purpose. Trust boundaries give you the framework to actually do this instead of hoping it happens.
When we help companies prepare for audits, the question auditors ask is simple: show us where your sensitive information lives and how you’re keeping it separate. Clear trust boundaries answer that question directly. You can point to your architecture and say, here’s where we enforce stricter controls, here’s where data gets handled differently.
The practical benefits stack up:
- Auditors see exactly how you’ve isolated sensitive data.
- Your policies align with what regulators actually demand.
- The chance of data leaking or getting accessed wrongly drops considerably.
Without these boundaries mapped out, compliance becomes a guessing game. Penalties follow. Breaches happen. The risk shifts from technical to financial fast.
Stopping Privilege Escalation by Isolation
Attackers love privilege escalation. They break into a low-access account and then hunt for ways to climb higher, grabbing more control as they go. We’ve watched this happen enough times to know it’s predictable, and trust boundaries are how you stop it.
When you isolate components and user groups based on privilege level, something shifts. Even if someone compromises one piece, they can’t just wander into the sensitive areas. The system makes them prove themselves at every boundary crossing.
What this actually looks like:
- One compromised section doesn’t give attackers free passage to everything else.
- Your system enforces strict checks whenever privilege levels change.
- Boundaries act like walls that limit how far an attacker can spread.
Think of a ship built with compartments. Water floods one section, sure, but the doors seal and the ship stays afloat. Your system needs that same structure.
Designing and Monitoring Secure Systems
Once you know where your trust boundaries sit, you can build architecture around them. Network segmentation, firewall rules, monitoring systems, all of it gets positioned at these critical points where trust shifts.
We’ve found that teams with clear boundaries catch attacks faster. They deploy their defenses smartly instead of spreading them thin. The payoff comes in detection speed and containment.
Concrete advantages emerge:
- You monitor those boundary points specifically for suspicious behavior.
- Anomaly detection catches unusual access patterns or data movements.
- Segmentation policies keep attackers from moving sideways through your network.
This thinking supports what security teams call zero trust architecture. Nothing gets assumed safe just because it’s inside. Everything crossing a boundary gets questioned.[2]
Sharpening Threat Modeling with Trust Boundary Mapping
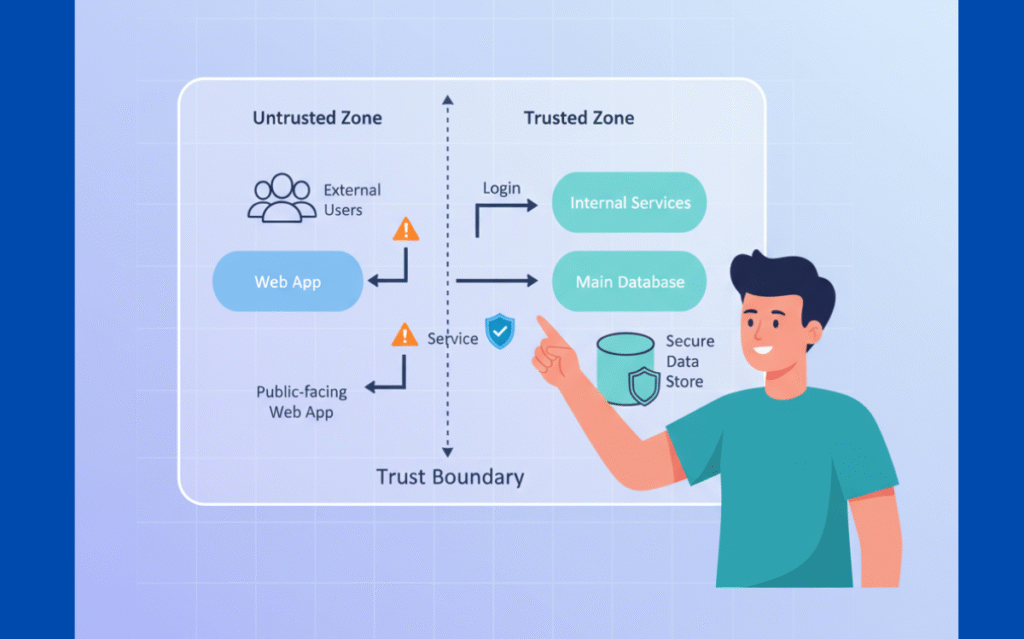
Identifying trust boundaries application through data flow diagrams becomes useful when you mark these boundaries clearly. We teach students to draw their systems and ask: where does trust level change? The answer shows you where threats cluster.
Boundary mapping transforms threat modeling from fuzzy thinking into something concrete. You’re not guessing anymore. You’re looking at actual transition points and asking what could go wrong there.
The structure helps with:
- Determining your actual attack surface instead of overestimating it.
- Spotting threats that happen specifically at boundary crossings.
- Ranking vulnerabilities by how much damage they could cause.
Teams that do this work upfront spend their security effort on things that actually matter. The rest becomes noise you can mostly ignore.
FAQ
Why do trust boundaries matter so much in threat modeling?
Trust boundaries help teams see where trust level transitions occur between untrusted vs trusted zones. They shape attack surface determination, data flow security, and access control boundaries.
When you map security zones clearly, you understand where threat actor targeting happens. Good threat modeling uses trust boundaries to guide mitigation strategies, risk management, and secure design principles across software architecture security.
How can trust boundaries reduce the risk of cross-boundary attacks?
Clear trust boundaries help stop cross-boundary attacks by defining privilege boundaries, authentication boundaries, and authorization controls. They mark data validation points and firewall segmentation paths that restrict movement across security zones.
When you enforce boundary security and zero trust architecture practices, you shrink the threat surface mapping and make it harder for external threats or insider threats to bypass controls or exploit weak segmentation policies.
What tools help teams understand trust boundaries in complex systems?
Teams often use data flow diagrams, boundary definition in DFD models, and security boundary mapping to visualize where data moves. These tools show microservices trust zones, API security boundaries, and cloud security boundaries.
They help identify attack vector identification points, supply chain attacks, and boundary access logs. Together, this supports boundary validation and boundary monitoring to improve incident response and governance risk and compliance.
How do trust boundaries support data confidentiality and integrity in cloud systems?
Trust boundaries guide data classification boundaries, cloud and on-premises boundaries, and segmentation policies that protect sensitive data zones. They reinforce identity and access management, multi-factor authentication, and role-based access control.
By shaping endpoint security boundaries, application layer boundaries, and data transmission security, they reduce breach impact. Strong trust boundaries also help teams meet compliance requirements with clearer security policy enforcement.
What role do trust boundaries play in long-term secure architecture design?
Trust boundaries shape secure network design, endpoint isolation, and secure coding boundaries. They help teams evaluate access rights, manage third-party integration risks, and prevent data leakage. Boundary hardening supports modular security design and segregation of duties.
When used with threat modeling frameworks, trust boundaries strengthen boundary trust model decisions and guide vulnerability prioritization, boundary crossing controls, and secure design principles for stable systems.
Final Thoughts on Importance Trust Boundaries Threat Modeling
Trust boundaries hold security together. They’re where trust shifts, and attackers aim there. Organizations mapping these boundaries catch problems early, stop privilege escalation, tighten access controls, and meet compliance demands. We see the difference in real systems, sharp threat modeling, deliberate defenses instead of scattered ones.
Start with your own setup. Where do trust boundaries actually sit? Are they defined clearly or buried somewhere? Chart them. Strengthen the controls sitting on them. Everything gets easier once you do.
If you want hands-on guidance in applying these practices directly in code, the Secure Coding Practices Bootcamp offers practical, developer-focused training to help teams build stronger systems from day one. Learn more or join here: Secure Coding Practices Bootcamp.
References
- https://www.bleepingcomputer.com/news/security/privilege-elevation-exploits-used-in-over-50-percent-of-insider-attacks/
- https://www.akamai.com/newsroom/press-release/microsegmentation-means-faster-incident-response-lower-insurance-premiums-for-organizations

