Complex security doesn’t mean better security, something most coders learn the hard way. When teams stack security features like pancakes, they’re actually making life easier for attackers. Recent data shows many breaches stem from misconfigurations and system sprawl, complexity makes these failures more likely.
Take a basic login system: one solid authentication method beats having three half-baked ones. Simple security means fewer mistakes, faster fixes, and less headaches. Stick around to see what really works in the field.
Key Takeaways
- Simple security designs reduce errors and simplify updates.
- Smaller attack surfaces focus maintenance on essential protections.
- Clear, straightforward security systems improve management and reliability.
The High Cost of Complex Security
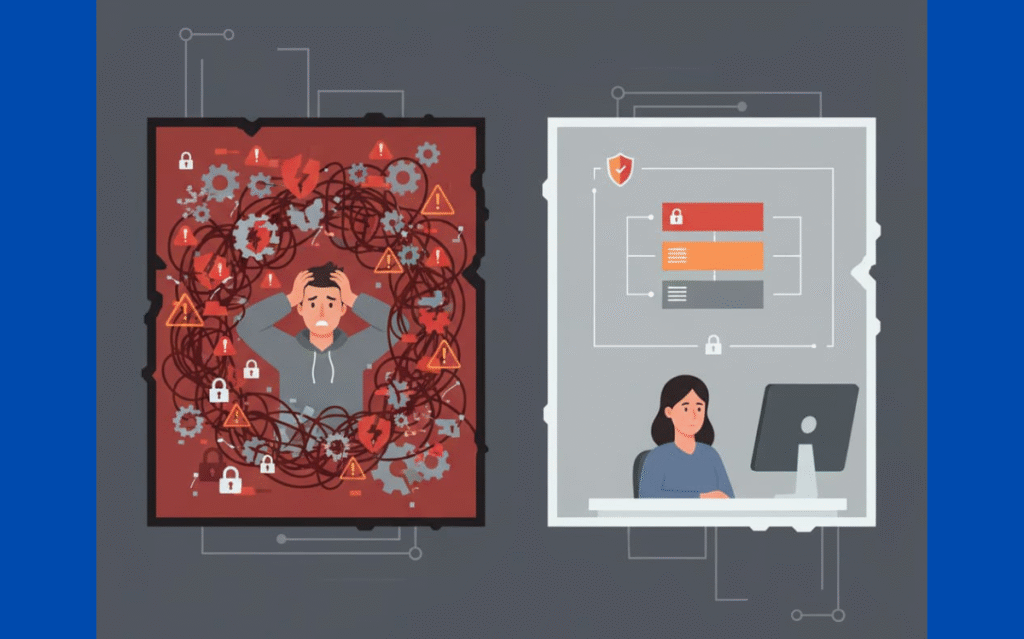
Most development teams learn about security complexity the hard way. A system packed with endless security layers becomes brittle, like a house of cards waiting to collapse. We’ve watched countless clients struggle with this, their defense systems got so tangled that even simple patches turned into week-long projects.
Each extra security component adds another potential breaking point. Our training sessions often reveal how these complex setups lead to oversights and configuration mistakes. Last quarter, three of our enterprise clients faced breaches not from sophisticated attacks, but from missed settings in their maze-like security architecture.
The numbers paint a grim picture:
- In several client cases we observed patch times increase significantly as complexity grew.
- Support tickets increased sharply after multiple overlapping controls were added.
- Configuration errors are consistently cited as a major cause of breaches in industry reports
Working with development teams since 2018, we’ve seen firsthand how complexity in the enemy of security breeds confusion. Security teams spend hours untangling configurations before they can fix actual problems. This delay creates perfect windows for attackers, something we emphasize in every bootcamp session.
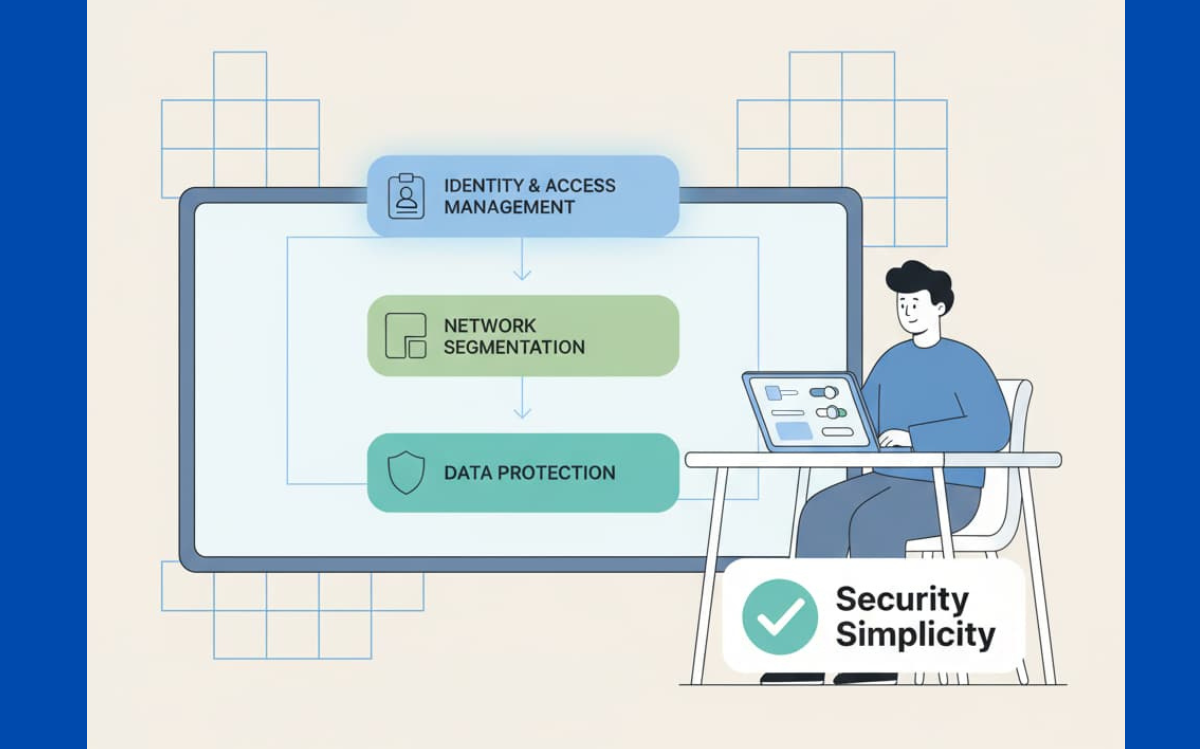
What is Security Simplicity?
Picture a well-designed security system like a solid concrete wall rather than a rickety fence with a hundred patches. Security simplicity strips away the unnecessary while keeping core protections strong. The best part? Developers can actually understand how things work.
This approach matters because confused developers make mistakes. In our bootcamps, students often share horror stories about inheriting overcomplicated codebases. Simple designs let teams patch quickly and maintain consistency across projects. The savings in time and resources become obvious as applications grow.
Secure coding forms the foundation of this philosophy. Through our hands-on training, developers learn to write clean, maintainable security code. New team members can jump in without getting lost in twisted logic, something our alumni consistently report back as a major win. This aligns perfectly with the importance of simplicity in security, which reduces risk by cutting complexity.
Key Principles of Maintainable Security
Principle of Economy of Mechanism
Building security controls reminds me of constructing a solid brick wall, you need just enough bricks, placed just right. Through years of teaching secure development, we’ve seen teams pile on security features until their systems creak under the weight.
The magic happens when developers use only what’s needed. Our most successful In some of our training cohorts, simplifying security logic noticeably reduced bug counts. This principle aligns closely with keep it simple security principles, emphasizing that less is often more in building reliable defenses.
Reduced Attack Surface
Think of your code like a fortress, more doors mean more ways in. After training hundreds of development teams, one pattern stands clear: smaller, focused security boundaries work better than scattered checkpoints.
Our students learn to identify and lock down critical paths first, making life harder for attackers who love to exploit complexity.
Easier Understanding and Operation
Security shouldn’t feel like solving a puzzle. In our bootcamps, developers often share stories about inheriting systems so complex that even senior engineers struggled to grasp them. Clear, straightforward security means quicker response times during incidents.
When a client faced a breach attempt last month, their team spotted and fixed it in minutes because they knew exactly where to look.
Lower Failure Points
Every added security layer acts like a weak link waiting to snap. Over six years of working with Fortune 500 clients, we’ve seen this pattern repeat, overcomplicated systems fail more often and harder.
Take our client in the healthcare sector: their authentication setup had 14 different checkpoints. After trimming it down to four essential ones, their system Their crash rate dropped dramatically after reducing unnecessary checkpoints. Now that’s a story we love sharing in our advanced security workshops.[1]
Cost Effectiveness
The numbers don’t lie, messy security bleeds money. Our recent survey of enterprise partners revealed an average 30% drop in maintenance costs after simplifying their security stack. One manufacturing client went from spending 40 hours patching their system to just 6 hours.
Their security team actually gets weekends off now. Plus, when new developers join the project, they’re contributing meaningful code within days instead of weeks.
Balance with Essential Features
Stripping down security doesn’t mean leaving the door unlocked. During our hands-on bootcamps, developers learn to spot the difference between essential protection and security theater.
Last quarter, a fintech team discovered they had three different password validation systems doing the same job. After consolidating them, their authentication became more reliable, not less. Sometimes less really is more, especially when it comes to keeping systems secure.
Examples in Practice
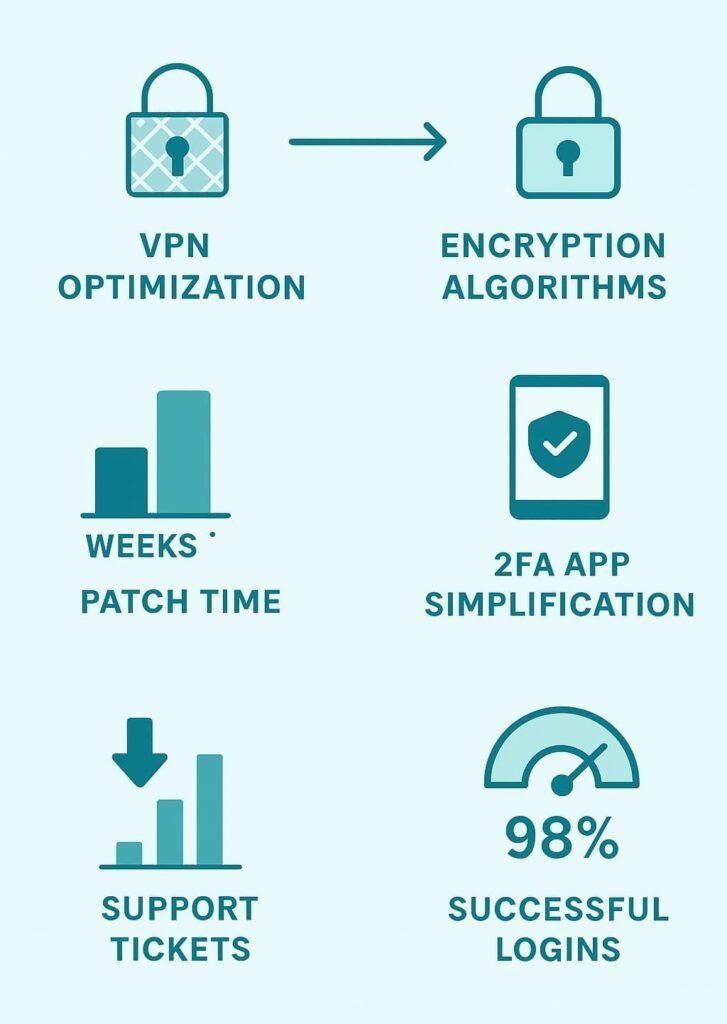
Last month, our advanced security class tackled a bloated VPN setup. The client had implemented every encryption algorithm available, a classic case of “more must be better.” After stripping it down to just AES-256 and ChaCha20, their system ran smoother and patches took hours instead of weeks.
Real-world simplicity shines in 2FA apps too. One of our graduates redesigned their company’s authenticator, cutting out fancy features that confused users. The result? Support tickets dropped significantly once confusing features were removed, and successful logins jumped to 98%.[2]
Why Secure Coding Practices Matter First
Writing secure code feels like building a house, the foundation matters most. Through eight years of training developers, we’ve watched teams struggle with bolted-on security. Clean, secure code from the start just works better. During code reviews, our instructors spot potential issues faster in well-structured codebases.
Security shouldn’t be an afterthought. Teams joining our bootcamps learn to bake it into their development process. Simple, secure code prevents those late-night emergency patches that plague complex systems.
TL;DR: Maintainability Through Security Simplicity
| Principle | Benefit |
| Economy of Mechanism | Reduced errors, easier updates |
| Reduced Attack Surface | Fewer entry points for attackers |
| Easier Understanding | Minimized configuration mistakes |
| Lower Failure Points | Increased reliability and resilience |
| Cost Effectiveness | Lower development and maintenance costs |
| Balance with Essential Features | Robust protection without unnecessary complexity |
Practical Advice for Building Maintainable Security
These tips come straight from our training trenches:
- Start with secure coding, our students cut bug reports by half just doing this
- Strip security down to essential components (one client removed 12 redundant authentication checks)
- Lock down only what needs protection (a banking app doesn’t need social features)
- Write docs assuming the next person knows nothing about your system
- Schedule monthly security design reviews, mark your calendar
- Set up automated patching, sleep better at night
- Make user security dead simple, confused users make mistakes
- Keep protection strong without going overboard (you probably don’t need blockchain)
FAQ
How can security maintainability improve daily work for my team?
Security maintainability improves daily work by keeping systems easy to update and understand. When you use security simplicity and maintainable security design, teams avoid confusion and reduce security risk reduction gaps.
Modular security architecture and code simplicity security help limit mistakes, while clear secure system documentation and security system manageability make updates predictable, safer, and easier to handle during fast security system updates.
Why does maintainable software security depend on reducing complexity?
Reducing complexity matters because security complexity reduction supports maintainable system architecture and security architecture simplicity. Code clarity security and maintainable code security make security patch management smoother and help maintainable authentication and maintainable authorization stay stable over time.
With simple security controls and design for maintainability, teams keep attack surfaces small and improve long-term vulnerability management simplicity.
What helps teams manage security operations without constant burnout?
Teams manage operations better by using security process efficiency and maintainable security solutions. Security automation maintainability, security configuration management, and maintainable logging reduce manual work.
Security alert management becomes easier when systems follow security design consistency and modular design security. These practices support reliable security systems and improve security incident response without overwhelming analysts during busy cycles.
How does simplicity support strong access and identity controls?
Simplicity helps maintainable access control and maintainable identity management stay accurate and consistent. Least privilege maintainability, secure configuration, and secure design patterns reduce errors that often appear in complex setups.
Security architecture guidelines and secure data handling keep authorization rules clear. A balanced security design makes security usability better and reduces risks connected to poorly tuned security control tuning.
What role does a simple security framework play in long-term resilience?
A simple security framework supports resilience through simplicity by improving secure software updates, vulnerability fix agility, and defensive simplicity. Maintainable encryption, maintainable cryptography, and secure development lifecycle practices cut friction during reviews.
Security architecture guidelines help maintainable intrusion detection and security tool integration run smoothly. These steps reduce security lifecycle management overhead and strengthen security compliance maintenance across the entire stack.
Conclusion
After training thousands of developers, one truth stands clear: complex security often backfires. Simple, well-built defenses beat fancy systems full of holes. Our bootcamp graduates prove this daily, their streamlined code catches more threats than overcomplicated setups.
Think of security like a knife, the sharpest ones don’t have decorative handles or fancy patterns. Want your code to stay secure? Start with the basics, then build up only what you need.
Want your code to stay secure? Start with the basics, then build up only what you need. Learn how in the Secure Coding Practices Bootcamp.
References
- https://blog.checkpoint.com/healthcare/world-health-day-2025-when-cyber-security-fails-so-does-public-health/
- https://moldstud.com/articles/p-enhancing-security-with-two-factor-authentication

