Security doesn’t need to be complicated. Most data breaches happen because someone piled on too many security tools, creating a mess that’s hard to watch over. The best defense? Put different parts of the network in their own corners, use strong passwords, and keep track of who goes where.
System admins who stick to these basics catch problems faster than those drowning in fancy tools and constant alerts. Need real examples of how this cuts down on headaches while keeping hackers out? Keep reading.
Key Takeaways
- Simple secure architecture relies on layered defenses and least privilege.
- Secure coding practices form the backbone of strong, manageable security.
- Clear trust boundaries and automation help maintain ongoing protection.
What is Simple Secure Architecture and Why Does It Matter?
Security designs work best when they’re stripped down to what matters. Complex defenses often create more problems than they solve, a lesson our training bootcamp has learned from years of teaching developers. We’ve seen countless projects fail because teams piled on security features until nobody could figure out what did what anymore.
Take cloud setups, where splitting servers into zones makes perfect sense. Customer-facing servers stay in public areas, keeping their hands off the private zones where sensitive data lives. Nothing fancy here, but this setup stops most attackers dead in their tracks.
The real magic of simple security comes from picking the right defenses, not the most defenses. Teams spot problems faster when they’re not drowning in alerts from dozens of security tools. Our students often tell us how much easier their jobs became once they stripped away unnecessary security layers.
This is a real-world example of how the importance of simplicity in security strengthens overall defense. Less really does mean more when it comes to keeping systems safe.
Key Principles of Simple Secure Architecture
Credits: IBM Technology
Layered Security
Our students learn quickly that good security works like an onion, multiple layers make attackers work harder. Networks split into zones, much like how our training labs separate practice environments from the core systems. Public-facing parts deal with users, while sensitive stuff stays tucked away in private areas. Between these, we set up checkpoints that filter out suspicious traffic.
Three reasons this approach works:
- Catches bad actors before they get far
- Makes hackers fight through multiple barriers
- Keeps damage contained if something breaks
This principle fits perfectly with keep it simple security principles, showing that well-layered but understandable defenses are more effective than complex, convoluted setups.
Least Privilege
Keys don’t belong in everyone’s hands. Over six years of teaching secure development, we’ve watched companies learn this lesson the hard way. Our approach? Give people exactly what they need, nothing extra.
That means the payment system stays far away from marketing emails, and the newsletter tool can’t peek at credit card numbers. When hackers break in (yeah, we’ve seen it plenty), they end up trapped in one small corner instead of running wild through everything.
Economy of Design
Most developers fall into the same trap, piling on security features like toppings on a pizza. But here’s the thing: every extra layer creates new ways things can break. Our students often show up wanting to use every security tool they’ve heard of.
After a few weeks in our labs, they discover that stripped-down systems catch more bad guys than the complicated ones. Simple security means fewer hiding spots for bugs. This clearly illustrates how complexity in the enemy of security can be mitigated by avoiding over-engineering and focusing on essentials.
Zero Trust (or Balanced Trust)
The security world loves extremes, trust no one or trust everyone. Reality sits somewhere in between. We teach our students to think like bank architects: vault-level security for sensitive data, regular locks for everything else.
Sure, the company blog needs protection, but probably not the same shields guarding payment info. Every connection still gets checked though, we’ve cleaned up too many messes that started with “we thought that server was safe.”
Examples of Simple Secure Architecture in Practice
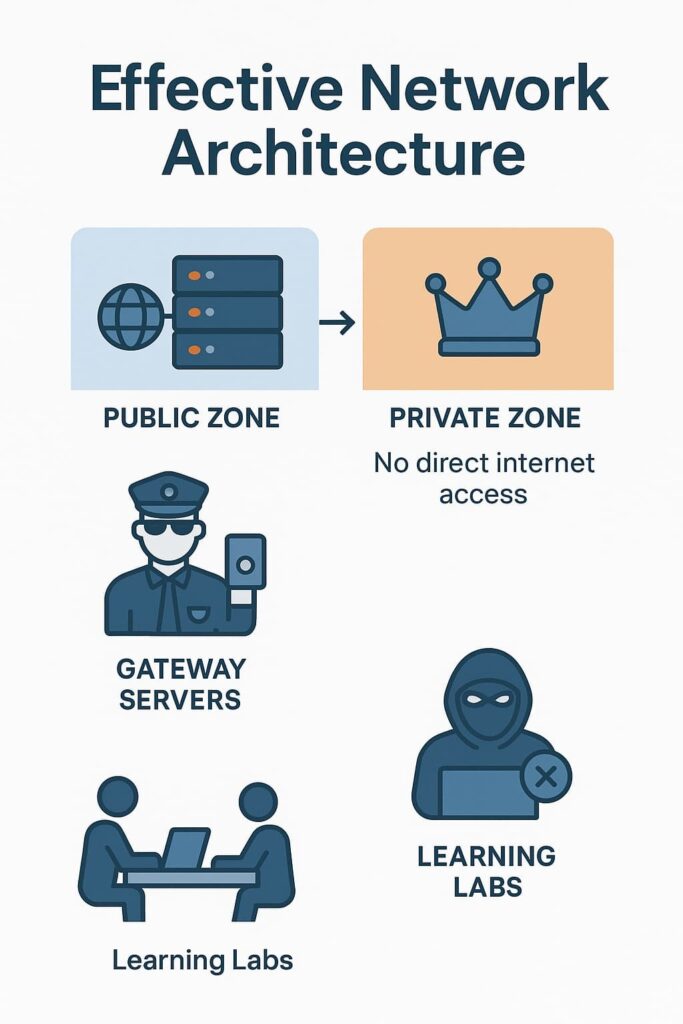
Network Architecture
After running hundreds of training sessions, we’ve found that network segmentation isn’t just theory, it works. Customer-facing servers stay in public zones, while the crown jewels hide in private areas where direct internet access can’t reach them. Our labs demonstrate this setup daily: students try to breach these barriers and learn firsthand why they’re effective.
Gateway servers act like bouncers at a club, checking IDs before letting anyone through. When hackers compromise one section, they find themselves stuck there, unable to reach other parts of the network. It’s not fancy, but it works.[1]
Authentication and Authorization
Most security failures we investigate trace back to weak identity checks. That’s why our courses hammer home the basics: solid OAuth implementation or IAM setups that actually verify who’s knocking.
Different roles get different keys, developers can’t touch production data, and marketing folks can’t mess with code deployment.
Secure Software Architecture
Writing secure code isn’t optional anymore. Through our bootcamps, developers learn to validate every input (because users type the strangest things), handle errors properly (no stack traces in production!), and avoid those tempting shortcuts that always come back to bite. We’ve seen too many projects rushed to production without basic security checks.
Each piece of the application gets its own sandbox to play in. Database handlers touch databases, email services handle mail, nothing gets extra privileges just because it’s convenient. Our students use tools like Vault for keeping secrets safe, because nobody wants their AWS keys showing up on GitHub again.
Microservices Design
Breaking down monoliths into microservices isn’t just trendy, it’s smart security. Each service runs in its own corner, with strict rules about who it talks to. Service meshes enforce these boundaries, making sure services don’t start gossiping about things they shouldn’t share.
When something looks fishy in the logs (and our monitoring catches a lot of fishy stuff), teams can track down the problem without digging through mountains of unrelated data.
Checklist for Implementing Simple Secure Architecture
Years of teaching security have shown us what matters most. Before touching any code, check these boxes:
- Map out where sensitive data lives and how it moves
- Give people just enough access to do their jobs (our students often mess this up at first)
- Stack security controls like layers of an onion
- Set up tools to watch for trouble automatically
- Keep checking and updating, what worked last year might not cut it now
Reinforcing Simple Secure Architecture
Bad code leaves doors wide open. Through our bootcamps, developers learn to lock these down: cleaning up user input, handling errors without leaking info, and avoiding those “I’ll fix it later” security shortcuts. We’ve seen too many breaches that basic secure coding could have stopped.
Network boundaries matter just as much. Our training labs split systems into zones, making students work with realistic setups where one compromised server can’t reach others. When someone finds a way through (and they will), good boundaries keep them from running wild.
Protecting secrets needs more than just hopes and prayers. Our students learn to use encryption properly, both for stored data and network traffic. Hardware security modules guard the really sensitive stuff, we’ve had companies tell us how this saved their bacon during breaches.
Breaking systems into tiny pieces might seem like overkill, but it works. Each component stays in its own bubble, with strict rules about who talks to whom. During exercises, we watch students try to hack these setups, it’s much harder when everything’s properly isolated.
Security tools help, but only if someone’s watching. Automated alerts catch weird behavior fast, giving teams a chance to stop trouble before it spreads. We’ve built this monitoring into our lab environments because real security means staying alert.[2]
FAQ
How can simple secure architecture help me build safer systems without adding noise?
Simple secure architecture reduces the minimal attack surface while keeping security by design easy to apply. Clear security boundaries, secure default configuration, and defense in depth work best when the design stays focused. Adding secure communication protocols, strong authentication architecture, and solid authorization architecture early in the process helps teams integrate systems safely without unnecessary complexity.
What secure architecture patterns should I consider when planning a new project?
You can evaluate secure architecture patterns such as zero trust architecture, layered security design, and secure network architecture. These patterns work well with microsegmentation security, network segmentation, and secure cloud architecture. Many teams also apply secure API design, secure microservices architecture, and secure container architecture to create strong isolation and containment while limiting the overall attack surface.
How do I build secure software design that remains simple as it grows?
Start with secure design principles and economy of design to keep your secure software design manageable. Use secure coding practices and a strong secure development lifecycle to prevent risky changes. Add secure session management, secure token design, encryption at rest, encryption in transit, and secure key management to protect data. Clear secure configuration management keeps the system stable over time.
What controls help balance security by design with smooth daily operations?
Controls such as identity and access management, role-based access control, attribute-based access control, and multi-factor authentication architecture help maintain protection without slowing teams down. Security automation architecture, security performance metrics, and adaptive security controls reduce bottlenecks.
With strong secure access management and secure remote access rules, your secure access architecture stays predictable and easy to operate.
How do I check if my simple secure architecture is working as threats evolve?
You can measure effectiveness through regular security risk assessment, threat modeling architecture, and security validation practices. Strong security logging design, secure logging and monitoring, and intrusion detection architecture support timely security incident management.
Security audit architecture, secure design review, and compliance-ready architecture help confirm that your security-first design and scalable security architecture continue to meet modern threats.
Conclusion
Building strong security doesn’t mean adding more layers, sometimes it means taking stuff away. Through teaching thousands of developers, we’ve learned that clear boundaries and basic protections catch more attacks than fancy tools. Split networks into zones, write code that checks for threats, and give people just enough access to do their jobs. When security gets too complicated, mistakes happen. Start with these basics, and build from there.
Segment your networks, write code that checks for threats, and give people just enough access to do their jobs. When security gets too complicated, mistakes happen.
Start simple. Build smart. Strengthen from there.
Learn how in the Secure Coding Practices Bootcamp.
References
- https://www.networkworld.com/article/4073808/the-business-case-for-microsegmentation-lower-insurance-costs-33-faster-ransomware-response.html
- https://www.itpro.com/security/74-percent-of-companies-admit-insecure-code-caused-a-security-breach

