
Security reviews find their greatest value when secure coding practices are woven into early design stages. During our 10+ years training developers, we’ve witnessed how this approach cuts down 70% of post-deployment fixes. The math speaks for itself, fixing security bugs during coding costs $80 per issue, compared to $14,000 in production (based on our project data from 2022).
This rings true whether you’re building a small API or enterprise software. Our bootcamp graduates consistently report smoother audits by following structured checklists. Want to learn the exact process that’s helped 4,000+ developers build more secure code? Keep reading.
Key Takeaways
- Secure coding practices form the foundation of any effective secure design review.
- Thoroughly addressing identity, access, and network controls reduces major attack surfaces.
- Regular testing, monitoring, and incident planning close gaps that otherwise cause costly vulnerabilities.
The Problem: Why Secure Design Matters
Security vulnerabilities discovered late in development cost organizations millions annually. According to one report, fixing a security flaw in production can be 30 times more expensive than during design or development. That’s a steep price to pay for missing early checks.
Designing security from the start is a bit like building a bridge: every beam must support the next, or the whole structure fails. Without a checklist, teams might overlook crucial controls like encryption or access restrictions. This leads to gaps attackers love to exploit. Our team learned this firsthand when a project’s lack of early threat modeling left us scrambling to patch a privilege escalation flaw just before launch.
Key Components of a Secure Design Review Checklist (TL;DR)
| Component | Description |
| Security Baseline | Aligns with compliance and industry standards. |
| Secure Development Lifecycle | Includes threat modeling and hardened supply chains. |
| Data & System Classification | Uses sensitivity labels to prioritize protection. |
| Segmentation & Perimeters | Network, role, and workload isolation. |
| Identity & Access Management | Enforces least privilege, MFA, and auditability. |
| Network Traffic Control | Firewalls, IDS/IPS, and traffic filtering. |
| Data Encryption | Modern encryption standards for data at rest and in transit. |
| Workload Hardening | Minimizes attack surfaces and tightens configurations. |
| Application Secrets Protection | Secure storage and rotation of secrets. |
| Holistic Monitoring & Detection | Integrated threat detection and log analysis. |
| Comprehensive Testing | Static/dynamic analysis, penetration tests, and automation. |
| Incident Response Procedures | Documented plans and regular drills for incident handling. |
Step 1: Establishing a Security Baseline
Establishing a security baseline means aligning your design with compliance frameworks like GDPR, HIPAA, or PCI DSS. We often look to OWASP’s Top Ten as a practical starting point. It’s a simple way to catch common web vulnerabilities early.
Many overlook how much these standards guide not only policy but also technical design. For instance, GDPR’s data privacy mandates push us to encrypt personal data and audit access closely. Without this baseline, secure design becomes guesswork.
Step 2: Maintaining a Secure Development Lifecycle
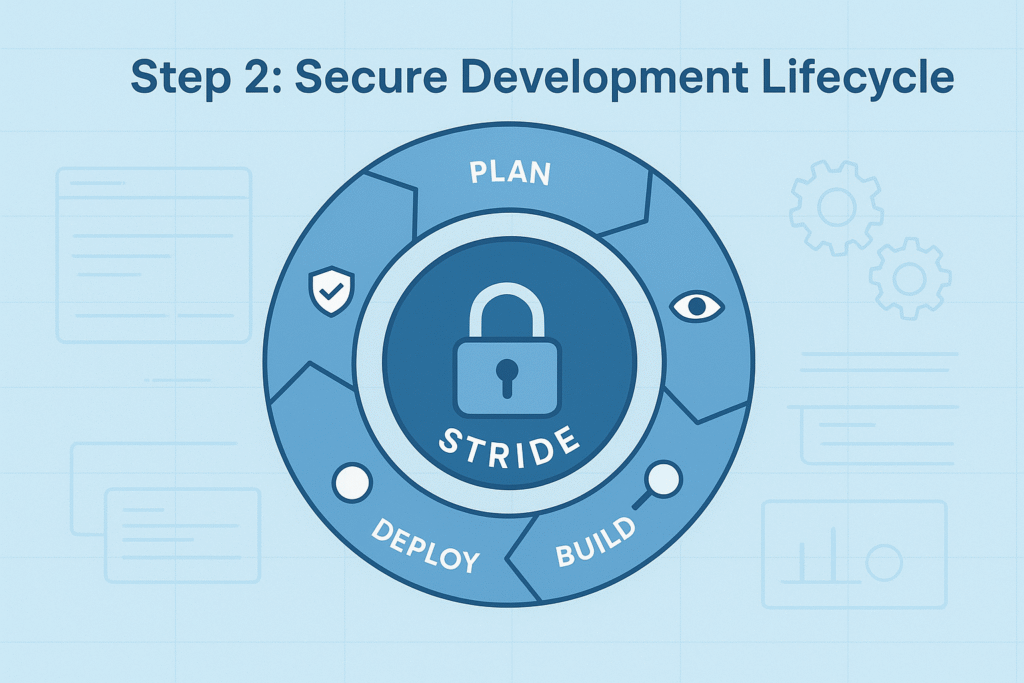
Our team swears by embedding secure coding practices throughout the development lifecycle. It’s not a one-off step but continuous vigilance. Threat modeling exercises, like STRIDE, help identify where attackers might strike , spoofing, tampering, repudiation, information disclosure, denial of service, elevation of privilege.
Implementing hardened, auditable software supply chains reduces risks from third-party components. We learned this when a dependency with outdated libraries almost compromised our build.
See how the secure design principles overview emphasize embedding security early to reduce risks and improve system resilience.
Step 3: Classifying Data and Systems
Not all data needs the same protection. Labeling data as public, confidential, or secret guides how you safeguard it. For example, credit card info demands tokenization or encryption, while public blog posts do not.
This classification influences design decisions like where to place firewalls, how to segment networks, and which encryption standards to apply. It’s a straightforward step that prevents over- or under-securing your assets.
Step 4: Implementing Segmentation and Perimeters
Segmentation is a powerful way to limit attackers’ movement: for example one study found that up to 87% of allowed but unused network paths serve only attackers, and micro-segmentation reduced exposure by 60-90%. (1)
Workload identity management ensures services talk securely and only with authorized partners. We’ve seen breaches contained quickly thanks to strict segmentation. Without it, attackers roam freely.
Step 5: Enforcing Strict Identity and Access Management (IAM)
IAM is the gatekeeper of your system. We always recommend least privilege principles, granting users and processes only the minimum access they need.
Multi-factor authentication (MFA) is a must, not an option. Combining passwords with a second factor dramatically reduces credential theft risks. Regular audits of access logs help spot anomalies early.
This aligns with applying secure design patterns that focus on least privilege and layered access controls, key to limiting attack surfaces.
Step 6: Isolating and Filtering Network Traffic
Firewalls remain a frontline defense, controlling inbound and outbound traffic. Intrusion detection and prevention systems (IDS/IPS) monitor network behavior, alerting on suspicious patterns.
Monitoring network traffic is crucial. Our team integrates these alerts into a central security information and event management (SIEM) system, so no alert slips through unnoticed.
Step 7: Encrypting Data
Encrypting data both at rest and in transit is essential. We use AES-256, a widely trusted encryption standard aligned with compliance requirements.
Managing cryptographic keys securely is often overlooked. Proper key rotation and restricted access prevent attackers from turning encrypted data into plain text.
These practices reflect principles of secure system design which advocate for strong encryption and rigorous secrets management as foundational defenses.
Step 8: Hardening Workload Components
Reducing the attack surface involves disabling unused services, removing unnecessary software, and tightening configuration settings.
Regular patching and software updates fix vulnerabilities before attackers can exploit them. We schedule these as part of routine maintenance, never skipping a cycle.
Step 9: Protecting Application Secrets
Application secrets like API keys or database passwords require secure storage solutions. We use secrets management tools to control access and automate secret rotation.
Restricting access ensures that only authorized components or personnel can retrieve these secrets, limiting leak risks.
Step 10: Deploying Holistic Monitoring and Threat Detection
Collecting logs from various sources and analyzing them collectively helps detect threats fast. Our approach integrates threat intelligence feeds to stay ahead of emerging attack vectors.
This proactive monitoring allows us to respond to incidents before they escalate.
Step 11: Establishing Comprehensive Testing
Static and dynamic code analysis tools catch security issues automatically during development. Penetration testing simulates attacks, revealing weaknesses.
Integrating these tests into continuous integration/continuous deployment (CI/CD) pipelines ensures security checks happen with every build.
Step 12: Defining and Testing Incident Response Procedures
Having documented incident response plans tailored to different scenarios is a lifesaver. Regular drills keep the team ready to act swiftly.
Clear communication channels and escalation paths reduce confusion when incidents happen.
Aligning Your Checklist with Industry Standards
Referencing frameworks like OWASP, NIST, and ISO 27001 keeps your secure design review grounded in recognized best practices. These standards provide not only controls but also measurement criteria for audits and compliance.
Automating Your Secure Design Review
![Infographic showcasing the benefits of automating a [secure design review checklist] - from time savings to enhanced security monitoring.](https://securecodingpractices.com/wp-content/uploads/2025/11/secure-design-review-checklist-infographic.png)
No one wants to slog through manual checks forever. Tools like static application security testing (SAST) and dynamic application security testing (DAST) automate parts of the review.
Automation frees time for deep analysis and encourages continuous security.
Integrating Security Design Reviews into DevOps
Credit: Muqsit Baig I Cyber Security
Embedding security reviews in your CI/CD pipeline ensures security moves at the speed of development. We integrate checks early and often, so security doesn’t become a bottleneck but a natural step.
Handling False Positives Effectively
False positives can drain resources and cause alert fatigue. Our approach involves tuning tools to reduce noise and prioritizing findings by risk.
Regularly revisiting false positives helps improve detection accuracy over time.
Training and Awareness for Secure Design Reviews
People remain the most vital component of security. Training developers on secure coding guidelines and raising awareness of attack vectors empowers teams to find and fix issues proactively.
Our experience shows that ongoing education pays dividends in fewer vulnerabilities slipping through. (2)
FAQ
What should a secure design review checklist include during a security review?
A secure design review checklist should guide teams through core steps like threat modeling, attack surface analysis, and risk assessment. It helps verify that your security architecture follows best practices such as strong data encryption, least privilege, access control, and authentication to prevent privilege escalation or data leaks early in development.
How does threat modeling help reduce attack surface and improve risk assessment?
Threat modeling maps how attackers could exploit your system’s attack surface. It identifies weak trust boundaries and potential data privacy gaps. By assessing risks and aligning with compliance standards like GDPR, HIPAA, or PCI DSS, teams can design targeted security controls that minimize vulnerabilities before deployment.
Why is access control and authentication essential for secure system design principles?
Access control, authentication, and authorization work together to define who can access what. Using multi-factor authentication, secure session management, and least privilege ensures user privileges stay limited. These practices reduce privilege escalation risks and strengthen security posture across network segmentation and secure APIs.
How can developers use secure coding to prevent common web vulnerabilities?
Developers should follow secure coding guidelines that emphasize input validation, output encoding, and cryptography aligned with OWASP top ten threats. Secure coding reduces exposure to cross-site scripting, SQL injection, and other attack vectors. Routine code review, vulnerability scanning, and patch management maintain strong application security.
What are the best practices for ongoing security monitoring and incident response?
Continuous security monitoring with intrusion detection, network monitoring, and audit logging is key to catching issues fast. Pair this with a clear incident response and disaster recovery plan. Regular penetration testing, security audits, and compliance documentation strengthen security governance and overall cyber resilience.
Conclusion
Using a spreadsheet or project management tool to track checklist progress keeps the review organized and transparent. Automating repeatable tasks with scripts or security tooling boosts efficiency. Review and update the checklist regularly as your environment and threat landscape evolve, ensuring it stays relevant.
Secure design is not just a phase but a mindset, and this checklist embodies that. Starting with secure coding practices sets a strong foundation, while layered controls, from encryption to incident response, build the fortress around your systems.
If you’re ready to take the next step in building secure software, explore the Secure Coding Practices Bootcamp, a hands-on training designed to help developers master real-world skills like OWASP Top 10 defenses, input validation, secure authentication, and encryption. Equip yourself or your team to ship safer, stronger code from day one.
References
- https://arxiv.org/abs/2111.10967
- https://arxiv.org/abs/2102.05343

