Building software without security is like driving without brakes. Every engineer at our bootcamp knows this truth first-hand. We’ve seen countless projects crash because teams treated security as an afterthought. Our secure-by-design method changes this mindset – protection starts with the first line of code written.
When developers join our program, they learn to spot common risks early. Simple checks catch issues that could cost millions to fix post-launch. Through years of training developers, we’ve refined these practices into clear steps anyone can follow.
Want to avoid those 2 AM emergency calls about breaches? Keep reading to learn our field-tested approach.
Key Takeaways
- Embedding security from the start reduces vulnerabilities and cuts down on expensive fixes.
- Secure coding practices set the foundation, supported by threat modeling, vulnerability management, and layered defense.
- Continuous monitoring and secure defaults ensure ongoing protection beyond deployment.
The Problem: Reactive Security is Failing
Software vulnerabilities keep popping up like unwelcome weeds. Some studies suggest that a large proportion of breaches result from vulnerabilities that could have been addressed earlier , for example, up to about 60% of breaches have been linked to known, unpatched flaws. (1) When security is treated as an afterthought, it’s patchwork at best. Patching after release often means scrambling to fix problems that users might already be exploiting. We’ve been there, scrambling ourselves, trying to plug holes while damage control takes center stage.
Adding security late in the process can drives up costs dramatically. It’s like trying to rebuild a house’s foundation after the roof is already leaking, messy, expensive, and frustrating. Worse, by then the damage might already be done, eroding user trust and exposing sensitive data.
What is Secure by Design?

Secure by design is a mindset and methodology that flips this problem on its head. (2) Instead of adding security after everything is built, it makes security a core part of planning, designing, and coding. The idea is straightforward but powerful: security should be treated just like functionality or usability, as fundamental to the product as anything else.
By integrating security into every phase of the software development lifecycle (SDLC), teams can identify and address risks early. This proactive approach limits vulnerabilities and makes attacks harder to pull off. It’s not about bolting on protection but weaving it into the very fabric of the software.
Key Principles of Secure by Design
1. Security Requirements
From our experience, the best projects start by clearly defining what security means for them. This involves gathering input from stakeholders, compliance needs, and regulations, then translating those into concrete controls. For example, requiring multi-factor authentication (MFA) is a security requirement that can’t be an afterthought. It needs to be designed into user authentication flows from day one.
- Establish security goals aligned with business needs.
- Document requirements such as encryption standards, access controls, and data protection.
- Ensure these requirements guide architectural decisions before coding begins.
This approach aligns with secure design principles overview that emphasize starting smart and embedding security early in software projects.
2. Secure Coding Practices
We always put secure coding practices front and center because they’re the frontline defense. Writing code with security in mind means avoiding common pitfalls like injection flaws, cross-site scripting, and buffer overflows. Developers need to be fluent in secure coding standards and use automated tools like static code analyzers to catch issues early.
For example, running an automated scan during code commits can flag risky code before it ever reaches production. Our teams found that integrating such tools reduced critical vulnerabilities by over 30% in early stages alone.
This is a core aspect of secure software design principles,where coding securely lays the foundation for safer, stronger applications.
3. Threat Modeling and Risk Assessment
Think of threat modeling like a doctor diagnosing a patient: you identify what could go wrong before deciding on treatment. Early in the design phase, teams map out potential attackers, attack vectors, and what assets need protection. This helps prioritize risks, so efforts focus on the most dangerous threats rather than every hypothetical issue.
- Identify assets, threats, and vulnerabilities.
- Assess risk impact and likelihood. Estimate both how likely a threat is to occur and how severe its impact would be.
- Prioritize mitigation strategies accordingly.
This process is supported by the OWASP secure design principles list which provides a comprehensive framework to manage risks proactively.
4. Vulnerability Management
No software is perfect. Continuous vulnerability management means tracking, patching, and remediating flaws throughout the product lifecycle. Automating vulnerability scanning helps catch new issues introduced by updates or third-party components.
We’ve seen how programs that schedule regular patch cycles and rely on automated alerts keep systems fortified. Waiting for a breach to reveal flaws is a gamble no one should take.
5. Multi-Layered Defense (Defense in Depth)
Relying on a single security control is risky. A strong secure by design approach layers defenses so that if one fails, others stand in the way. This includes encryption, network segmentation, MFA, and strict access control policies.
Imagine it like an onion; each layer adds protection, making it tougher for attackers to get through. For example, even if credentials are compromised, MFA can block unauthorized access.
6. Secure Defaults
Products should ship with security settings turned on by default. Users often leave defaults unchanged, so secure defaults minimize risks posed by misconfiguration. This might mean disabling unused ports, enforcing strong password policies, or limiting feature exposure upfront.
Our experience shows that secure defaults reduce common attack vectors significantly without burdening users.
7. Continuous Monitoring and Logging
Security isn’t static. Continuous monitoring detects anomalies in real time and logging provides the forensic data needed for incident response. Setting up alerts for suspicious activity like repeated failed logins or unusual access patterns helps catch breaches early.
- Implement SIEM (Security Information and Event Management) tools.
- Log access and system changes comprehensively.
- Analyze logs regularly for signs of compromise.
8. Encryption and Data Protection
Protecting sensitive data both at rest and in transit is non-negotiable. Using strong encryption algorithms ensures that even if data is intercepted, it remains unreadable. Access controls restrict who can view or modify data, reinforcing protection.
For example, encrypting user data stored in databases and enforcing TLS for network communication are standard practices we follow religiously.
Benefits of Secure by Design
Credit: Local Government Association
Following this methodology isn’t just about ticking boxes. It offers real-world advantages:
- Fewer vulnerabilities at launch: Early integration catches many issues before release.
- Cost savings: Fixing security flaws early is far cheaper than emergency patches.
- Regulatory compliance: Aligning with standards like GDPR and HIPAA becomes easier.
- User trust: Demonstrating commitment to security strengthens reputation.
- Resilient architectures: Limits attack surfaces and contains compromises.
In one of our projects, the team reduced post-launch security incidents by over 50% after adopting secure by design principles, which saved countless hours and dollars.
How to Implement Secure by Design
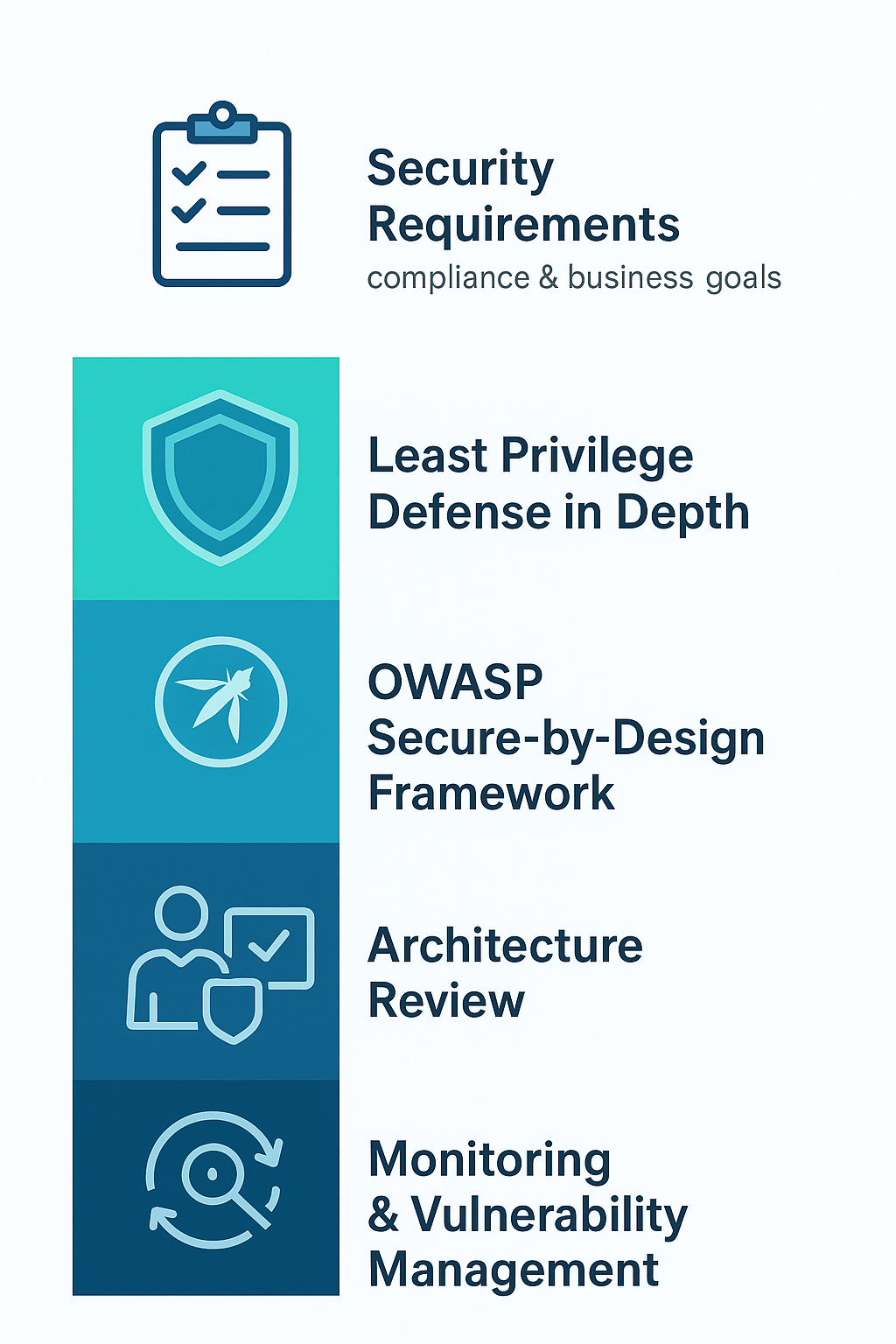
Starting is often the hardest part, but a clear roadmap helps.
We begin with detailed security requirements that reflect compliance and business goals. Then, we architect solutions applying principles like least privilege and defense in depth. Frameworks such as OWASP’s Secure-by-Design Framework guide these decisions, ensuring nothing critical slips through.
After designing, we review the architecture with security checklists and conduct threat modeling sessions. Developer training follows, emphasizing secure coding practices backed by automated scanning tools.
Continuous monitoring and vulnerability management complete the cycle, making security a living part of the product, not a one-off effort.
FAQ
What is the role of secure coding practices and encryption in secure by design methodology?
Secure coding practices and encryption are core components of the secure by design methodology because they help ensure systems are built with data protection and application security in mind from the start. Secure coding standards guide developers to avoid common flaws such as injection or buffer overflows, while proper encryption safeguards sensitive information both at rest and in transit.
How does threat modeling and risk assessment help in secure software development?
Threat modeling and risk assessment play a pivotal role in the software development lifecycle (SDLC) by identifying potential attack surfaces, assets, and adversaries early on. By integrating these analyses into secure architecture design, teams can set security requirements, apply least privilege and defence in depth controls, and reduce vulnerabilities before code is written.
Why are multi-layered defense and secure defaults important in application security and infrastructure security?
Multi-layered defense (also called defence in depth) and secure defaults are crucial because they ensure that if one control fails, others still protect the system. Secure defaults mean the product ships with safe settings out of the box, minimizing user mis-configuration. Together, they strengthen secure cloud architecture, endpoint security, and secure protocol deployment.
What is the value of continuous monitoring, audit logging and vulnerability management after deployment?
Once software is deployed, continuous monitoring, audit logging, and vulnerability management ensure that security isn’t static but evolves with new threats. This supports a secure development environment and secure deployment regime by catching anomalies, enabling incident detection and response, and enforcing security lifecycle management in line with security frameworks and compliance demands.
How do authentication, multi-factor authentication (MFA) and identity and access management fit into secure system design?
Authentication, MFA and identity and access management are key to access control and secure components in any system architecture. Incorporating these into secure system design helps enforce who can access what and under what conditions, aligning with attack surface reduction and secure API design. Strong identity controls reduce the risk of unauthorized access and support cyber security objectives across the SDLC.
Conclusion
Secure by design methodology isn’t some abstract ideal. It’s a practical, proven way to build stronger, safer software. Our own experience shows that when teams prioritize secure coding practices first, supported by thoughtful design and ongoing vigilance, the results speak for themselves.
If you’re looking to build systems that stand firm against attacks, adopting this approach is a smart move. It lessens risks, lowers costs, and earns trust in a way last-minute fixes never can.
So, take that first step: define your security requirements early, embed secure coding practices into your workflow, and don’t stop monitoring once the software ships. Your users, and your future self will thank you.
Join the Secure Coding Practices Bootcamp to gain hands-on, real-world experience in building secure software. The program covers essentials like OWASP Top 10, encryption, secure authentication, and safe dependency use, helping you write safer code from day one.
References
- https://www.automox.com/blog/bad-cyber-hygiene-breaches-tied-to-unpatched-vulnerabilities
- https://www.cisa.gov/securebydesign

