
Any business operating a web application faces an expanded attack surface: real threat actors do attempt data theft or service disruption, not just theoretical risks. In our experience, effective threat modeling for web applications involves proactively identifying vulnerabilities that could be exploited by malicious actors, allowing us to secure our systems before any attacks occur.
Our team spends time with developers, showing them how to spot issues early rather than scrambling to patch holes later. When building apps securely from day one, problems naturally decrease. Want to learn how the pros handle web security? Keep reading.
Key Takeaways
- Threat modeling helps you visualize your application’s attack surface and prioritize threats.
- Secure coding practices are the first line of defense to prevent vulnerabilities.
- Using structured threat modeling frameworks like STRIDE guides systematic risk assessment and mitigation.
The Growing Threat Landscape for Web Applications
Web applications are tempting targets for attackers. The sheer number of attacks exploiting weaknesses like SQL injection or broken access control is staggering.
In one audit of 50 web applications, we observed that 61% had cross-site scripting (XSS) flaws, illustrating how prevalent this specific software vulnerability is in the application layer. Industry research shows a significant proportion of data breaches involve application vulnerabilities, recent reports estimate around 25% of all breaches are tied to applications. (1)
This leads to lost data, financial damage, and a tarnished reputation. We’ve seen projects where ignoring threat modeling cost dearly, fixing a breach after launch demanded months of work and huge expenses. According to recent breach data, the average cost of a data breach is ~US$4.88 million.
Threat modeling addresses this by forcing you to look at your system through an attacker’s eyes first. It’s a proactive approach that reduces risk and can save money by fixing issues early. An introduction to threat modeling helps teams develop this mindset, emphasizing visualization of risks and prioritizing defenses before vulnerabilities are exploited.
From our work with various development teams, we’ve learned that the goal of threat modeling is not to instill fear but to achieve clarity; understanding your application’s vulnerabilities allows for informed decisions on effective security measures.
Key Steps in Threat Modeling
1. System Understanding (Diagramming)
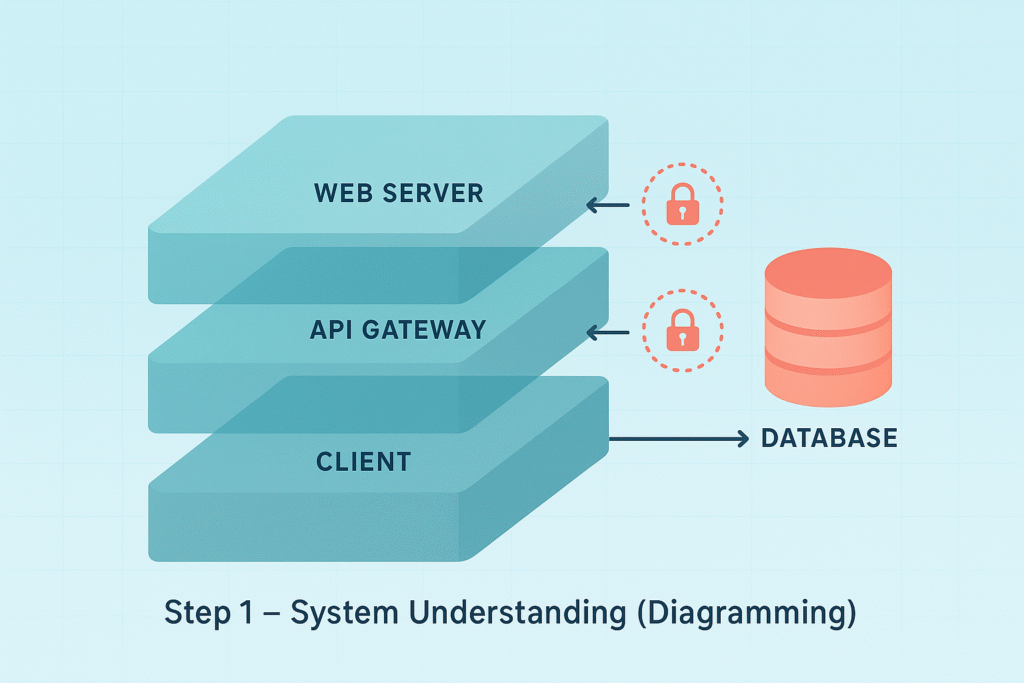
Start by documenting your system architecture as an entity: create data flow diagrams to represent components (web server, database, API gateway), their relationships and trust boundaries. Visual tools like data flow diagrams help you see how data moves through your app and where sensitive assets live. For example, in a typical e-commerce site, you’d chart connections between the user, web server, database, and payment gateway.
- Identify trust boundaries where data enters or leaves secure zones.
- Highlight critical assets like customer info or payment data.
- Understand dependencies on third-party services or APIs.
We’ve found that this step alone surfaces many hidden attack vectors. When you clearly see where data flows, it becomes easier to spot points vulnerable to interception or manipulation.
2. Threat Enumeration
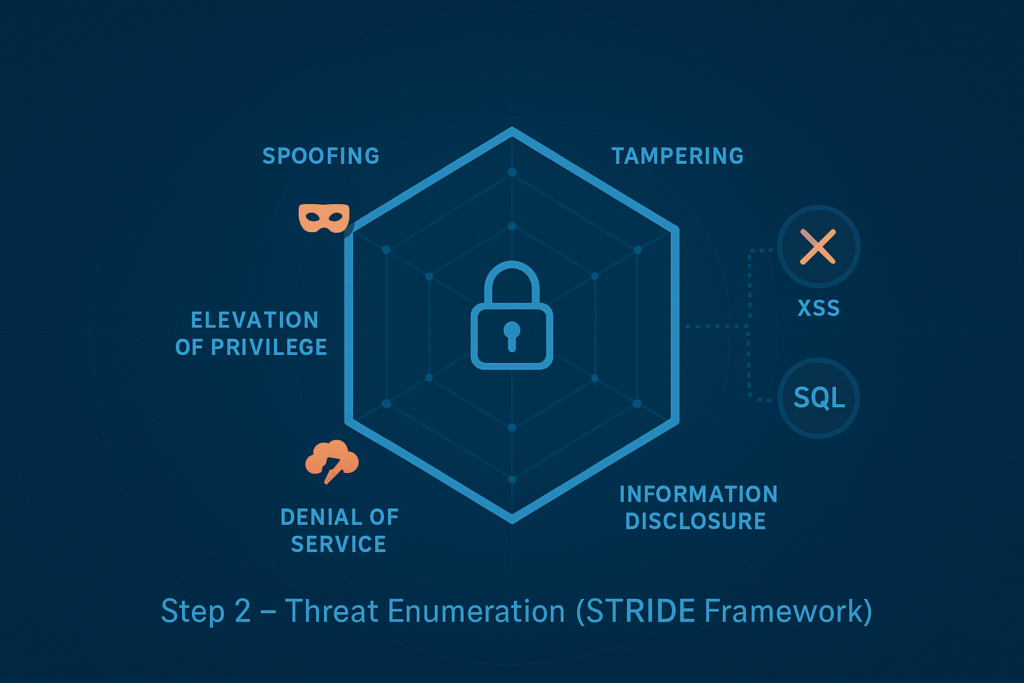
With the system architecture documented, enumerate threats using a structured threat modeling framework such as STRIDE (entity: threat modeling methodology) to classify each threat type, its root cause and mitigation strategy, covering:
- Spoofing identity
- Tampering with data
- Repudiation threats
- Information disclosure
- Denial of service
- Elevation of privilege
Cross-referencing these with the OWASP Top 10 highlights real-world vulnerabilities like cross-site scripting (XSS), SQL injection, or broken access control.
For example, SQL injection happens when attackers insert malicious code into input fields that aren’t properly sanitized. This can lead to full database compromise. Catching this during threat enumeration focuses your efforts on input validation and parameterized queries.
3. Mitigation Strategies
Here’s where secure coding practices come into play. Through years of working on secure development projects, we have emphasized that adopting secure coding practices is essential; many vulnerabilities originate from easily preventable coding errors that can be addressed early in the development cycle.
Sanitizing inputs, enforcing strict access control, and encrypting sensitive data aren’t just buzzwords, they’re essential safeguards.
After coding controls, look to infrastructure changes or additional security tools like web application firewalls and intrusion detection systems to add layers of defense.
- Prioritize fixes by risk level to tackle the biggest threats first.
- Document mitigation steps clearly for the team.
- Plan for ongoing updates as new threats emerge.
4. Verification
No security plan is complete without testing. In our professional experience, penetration testing is invaluable; it simulates real-world attacks on your application, rigorously assessing the effectiveness of your security controls. Automated vulnerability scanners catch known issues quickly, while manual code review can uncover subtle logic flaws.
Verification validates that your threat mitigation actually works. We’ve seen teams skip this and face costly surprises when attackers exploit overlooked weaknesses. Skipping verification is risky, studies show many vulnerabilities remain in production despite scanning. (2)
Threat Modeling Methodologies: A Comparison
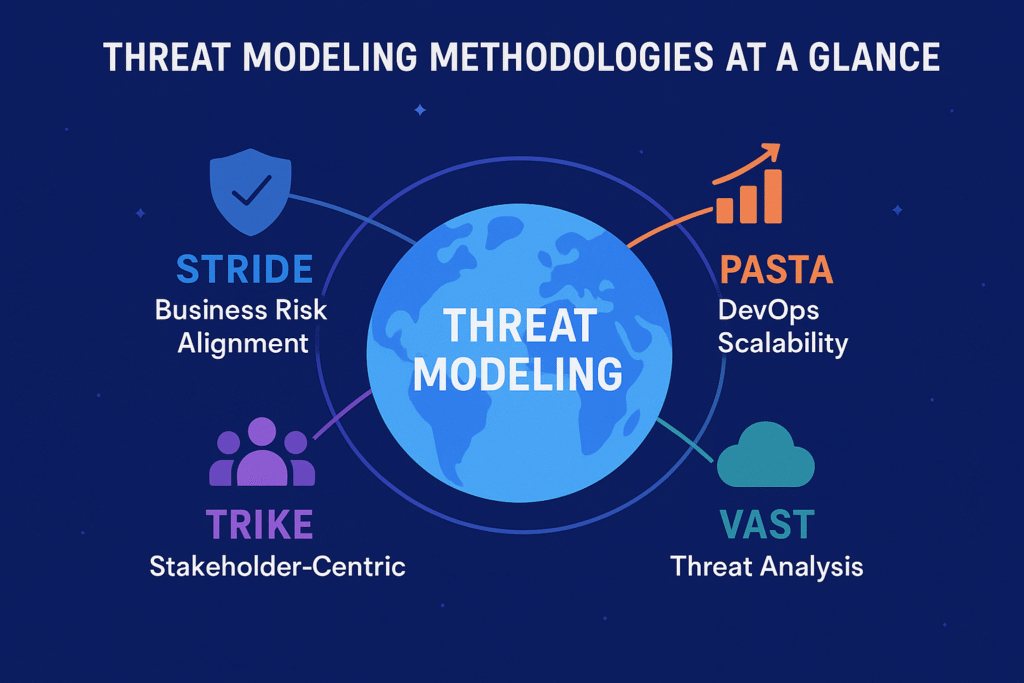
There are several frameworks to guide your threat modeling, each with its own focus. STRIDE (broad threat categories), PASTA (business-risk alignment), Trike (stakeholder-centric), VAST (for DevOps/enterprise scale)
STRIDE
Covers six broad threat categories, giving a thorough checklist of potential flaws. Great for teams wanting wide coverage early in development.
PASTA
Centers on business impact and risk, aligning security efforts with organizational goals. Useful when you need to justify security spending to stakeholders.
Trike
Focuses on risk management from the stakeholder perspective. Encourages collaboration across departments to ensure security fits everyone’s needs.
VAST
Designed for enterprises and DevOps, VAST scales threat modeling to many teams and continuous delivery pipelines.
| Methodology | Focus | Best For |
| STRIDE | Threat Categories | Broad threat coverage |
| PASTA | Risk & Business Alignment | Connecting security to business |
| Trike | Stakeholder Perspective | Cross-team collaboration |
| VAST | Scalability & DevOps | Integrating with development flow |
While STRIDE remains our preferred threat modeling framework for its simplicity (entity: STRIDE framework), other methodologies such as PASTA or VAST may offer different attributes like business-risk alignment or DevOps scalability, and their value lies in fit to your environment.
Bringing Threat Modeling Into Your Workflow
Credit: Arab Security Conference
We’ve found that threat modeling is an ongoing process; as applications evolve, continuously updating your threat model is crucial to adapt to new vulnerabilities and attack vectors. Utilizing simple threat modeling tools can help teams without dedicated security experts to manage this process more effectively, making security assessments accessible across all skill levels.
Because an application’s system architecture and attack surface change over time (entity: evolving architecture/attack surface), you must perform a threat model update regularly, attribute: versioning, review frequency; value: prevents new vulnerabilities
We recommend:
- Regularly revisiting threat models during development sprints.
- Integrating threat modeling with secure software development lifecycle (SDLC) practices.
- Pairing threat modeling with routine security testing and code reviews.
- Training your team on common threat vectors and mitigation tactics.
The payoff is a stronger security posture, fewer surprises from zero-day vulnerabilities, and easier compliance with security policies.
Practical Experience: Lessons Learned
From our own projects, the value of threat modeling became clear when we caught a critical authorization vulnerability before launch. The system allowed users to access restricted areas because of a misconfigured access control check. Without threat modeling, this flaw might have slipped through.
Applying secure coding practices alongside threat modeling also streamlined our risk mitigation. It’s one thing to identify a threat; it’s another to embed defenses so deeply they become routine. Code reviews focusing on security and automated scanning tools helped maintain that standard.
We noticed that teams embracing threat modeling early spend less time in firefighting mode later. It’s a mindset shift, from reacting to breaches to preventing them.
Strengthening Security with Secure Coding Practices
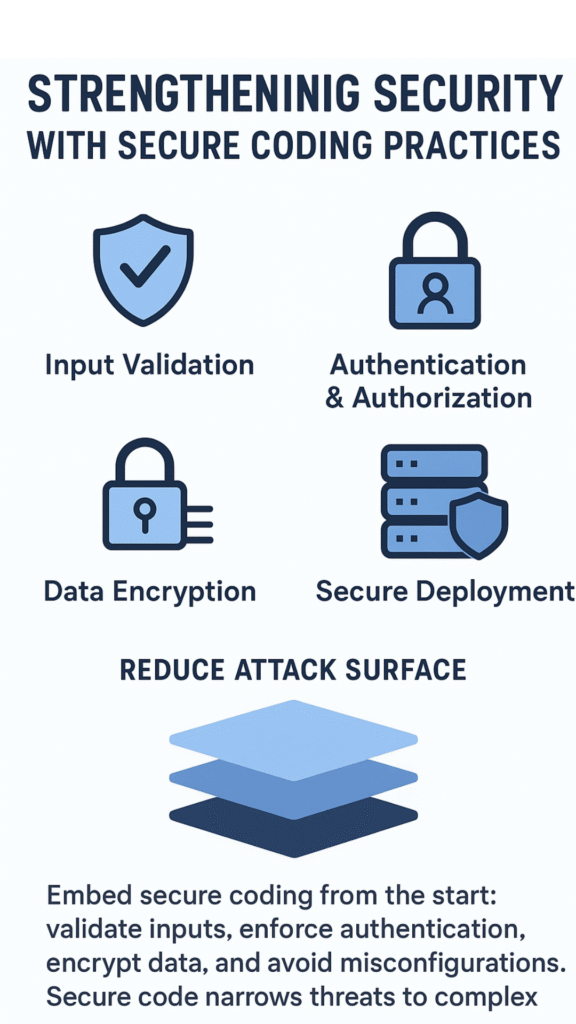
Too often, developers focus on functionality and leave security as an afterthought. We’ve learned that embedding secure coding practices from the start is crucial. These practices include:
- Validating and sanitizing all inputs.
- Implementing robust authentication and authorization checks.
- Encrypting sensitive data both in transit and at rest.
- Avoiding security misconfigurations in deployment environments.
Integrating these into everyday development reduces the attack surface and makes threat modeling more precise. When your code inherently resists common vulnerabilities, threat analysis zeroes in on the complex risks that remain.
FAQ
What is threat modeling for web applications and why is web application security important?
Threat modeling for web applications is a process that combines threat analysis, risk assessment and vulnerability identification to map the attack surface of your site or service. By doing this, you more clearly understand application threats, SQL injection or cross-site scripting (XSS) risks, broken access control and other threat vectors. Good web application security means you build secure design, apply secure coding practices and improve your security posture before a security breach happens.
How does the STRIDE framework help in threat modeling web applications?
The STRIDE framework helps in threat modeling web applications by giving you structured categories, spoofing, tampering, repudiation, information disclosure, denial of service and elevation of privilege, to spot common attack vectors. Using this kind of threat modeling frameworks alongside your system architecture, access control and authentication vulnerabilities lets you do threat prioritization, plan threat mitigation and link to risk management more effectively.
When should you update your threat model and how does it fit with secure software development?
You should update your threat model whenever your system architecture or application layer security changes, new APIs, cloud security shifts, or new endpoints, so the threat model update is in sync with your development flow. Knowing when to perform threat modeling ensures that security gaps are caught early and reduces costly fixes later in the development lifecycle.
Integrating it into secure software development ensures vulnerability scanning, code review, penetration testing, threat detection and security monitoring all reflect the latest changes. This keeps your security governance and incident response ready for evolving threat landscape.
How do you prioritise which threats to tackle first in web application threat modeling?
In threat modeling web applications you prioritise by combining risk assessment of likelihood and impact and mapping threat actors, insider threats or malware threats, as well as compliance requirements or business impact analysis. You assess security risk for attack surface elements (APIs, endpoints, network security, cloud security) and then apply threat prioritization so you focus your security controls, intrusion detection, secure coding and encryption vulnerabilities fixes where they matter most.
What is the role of security testing, penetration testing and vulnerability scanning in threat modeling web applications?
Security testing (including automated vulnerability scanning and manual code review) and penetration testing form an essential part of the threat lifecycle in threat modeling web applications. Once you’ve done threat documentation, threat modeling tools or frameworks and listed threat scenarios, you implement security controls, then verify via testing to detect zero-day vulnerabilities, security flaws, social engineering or API security issues. This loop of threat detection, threat hunting, risk mitigation and verification strengthens your overall system architecture and security audit readiness.
Conclusion
Threat modeling web applications is a practical, ongoing process that demands attention to detail and collaboration. It’s not about eliminating every risk, no system is perfect, but about understanding and managing those risks wisely. By combining thorough threat enumeration with secure coding practices and regular verification, you build resilience into your apps.
We’ve found that teams who embrace this proactive approach not only reduce the chances of costly breaches but also foster a security mindset that benefits the entire organization. So take the time to map your system, identify threats, prioritize mitigations, and verify results. Your web applications will be all the safer for it.
Ready to take your secure development skills further? Join the Secure Coding Practices Bootcamp, a hands-on, expert-led training that helps developers master real-world techniques like input validation, secure authentication, encryption, and safe dependency use. Build safer code from day one with practical guidance, labs, and certification.
References
- https://aimultiple.com/application-security-statistics
- https://www.contrastsecurity.com/reports/contrast-labs-application-security-intelligence-report-mar-apr-2020

