
Security threats overwhelm even seasoned developers, we’ve seen it firsthand at our bootcamp. But threat modeling isn’t as complex as most think. The real secret lies in getting the fundamentals right, our students start with secure coding basics before diving into advanced techniques. Through years of training developers, we’ve learned that frameworks like STRIDE work best when built on solid coding practices.
Think of it as assembling puzzle pieces: once the edge pieces (secure coding) are in place, the rest naturally falls into position. Want to learn our field-tested approach to identifying and neutralizing threats? Keep reading.
Key Takeaways
- Threat modeling helps identify and prioritize cybersecurity threats before they cause damage.
- Core steps include defining scope, system modeling, threat identification, risk assessment, and mitigation.
- Techniques like STRIDE and PASTA offer structured ways to analyze threats from different angles.
Why Threat Modeling Matters
The threat landscape isn’t just growing, it’s changing shape in ways that can catch you off guard. We once heard a stat that over 60% of data breaches stem from known vulnerabilities that weren’t addressed. Recent data reveal that exploitation of known vulnerabilities accounted for approximately 20 % of data breaches in 2025. (1)
That stuck with us because it shows how even small gaps can cause big headaches. If your team relies only on reactive fixes, you’re always one step behind attackers. That’s where threat modeling steps in. It’s a way to predict what might go wrong and prioritize your resources accordingly, instead of scrambling after an incident.
Threat modeling isn’t a silver bullet but a practice that guides your security efforts. When we combine it with secure coding practices, it creates a layered defense. Instead of patching holes one by one, you’re designing systems with security in mind from the start. This approach saves time and money, and frankly, a lot of stress.
- Helps identify vulnerabilities before attackers exploit them
- Focuses resources where they matter most
- Reduces chances of costly security breaches
What Is Threat Modeling?
Threat modeling is a proactive process to identify, understand, and address potential threats to your system or application. It’s like putting yourself in the attacker’s shoes to think about what could go wrong. The idea is to map out your assets, understand how data flows, and figure out where weak spots might exist. Another study found that 84 % of companies have high-risk vulnerabilities exposed on their external networks, many of which could be mitigated with straightforward patching. (2)
We’ve seen how this helps teams prioritize security work. Without a clear threat model, it’s easy to waste effort on low-risk areas while ignoring critical vulnerabilities. Threat modeling helps answer questions like: Which parts of the system are most valuable? What kinds of attacks are likely? How severe would the impact be? The answers guide your decisions on where to focus security investments.
Core Steps in Threat Modeling
Define the Scope
First off, you have to know what you’re protecting. Identifying system boundaries, key assets like data or hardware, users, and data flows is essential. Without this, you might miss parts of the system that attackers could exploit.
We always start here, before jumping into threat hunting or analysis, because it sets the stage for everything else. Understanding your system boundaries and assets is fundamental in the threat modeling process, helping you focus on what truly matters.
Define the Scope, Create a System Model, Identify Threats, Assess and Prioritize Risks, Develop and Implement Mitigations, Validate and Iterate, these are the key phases that make threat modeling effective. Each step builds upon the last to ensure a solid defense is in place from the start.
Embracing these fundamentals starts with an introduction to threat modeling mindset, which helps embed security throughout the development lifecycle.
Create a System Model
Once the scope is clear, visualizing the system helps everyone understand how components interact. We’ve found that simple diagrams like Data Flow Diagrams (DFDs) work wonders here. They show how data moves between parts of the system, where it’s stored, and who accesses it. UML diagrams can also help when you want to dive deeper into system design.
This model acts as a blueprint for identifying threats. Seeing the connections makes it easier to spot potential weak points or unusual data flows.
Identify Threats

Finding threats is where your team puts on the detective hat. Using methodologies or brainstorming sessions, you identify what can go wrong. One technique we’ve used successfully is Security Cards, a collaborative way to generate threat ideas by encouraging diverse perspectives. Applying the threat modeling for developers mindset means anticipating risks by thinking like an attacker, which makes identifying threats more effective.
Threat identification revolves around asking: What could go wrong? Which attacker profiles might target us? What attack vectors are most relevant? It’s a mix of creativity and analysis.
- Collaborate across teams to widen the threat perspective
- Use structured methods to avoid missing obvious risks
- Consider internal and external threat actors
Assess Risks and Vulnerabilities
Not all threats are equal. After identifying them, assessing the likelihood and impact of each helps prioritize. We rely on frameworks like CVSS (Common Vulnerability Scoring System) to quantify risk levels. This helps avoid the trap of over-focusing on unlikely threats or ignoring serious ones.
Risk evaluation balances technical vulnerability analysis with business impact. For example, a vulnerability exposing customer data is more critical than one affecting a rarely used feature.
Determine Mitigations
With risks prioritized, deciding how to respond comes next. Mitigations might include adding security controls, fixing code, accepting some risk, or transferring it through insurance or third-party services. We always encourage integrating secure coding practices early on, this reduces vulnerabilities before they reach production.
Mitigation isn’t a one-time fix but part of an ongoing process to improve your security posture.
Review and Iterate
Threat modeling isn’t set-it-and-forget-it. Systems change, new threats appear, and what seemed low risk yesterday might become urgent tomorrow. Regularly revisiting and updating your threat model keeps it relevant. We try to make this part of our development lifecycle so it doesn’t slip through the cracks.
Common Threat Modeling Techniques
STRIDE
Credit: Netsec Explained
STRIDE is a classic framework developed by Microsoft. It breaks down threats into six categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. By examining each category, you can systematically identify risks.
For example, when reviewing a web app, we used STRIDE to find spoofing threats where stolen credentials might allow unauthorized access. This method is straightforward and fits well for system or application-level threat identification.
PASTA (Process for Attack Simulation and Threat Analysis)
PASTA takes a different approach. It’s attacker-centric and aligns security with business objectives. It has seven steps, from defining business goals, analyzing assets, decomposing applications, to simulating attacks and analyzing risks. We’ve applied PASTA when working with financial services to understand the potential business impact of breaches.
It’s useful when you want to balance technical threats with what matters most to the business.
Attack Trees
Attack trees help visualize complex attacks by breaking them down into sub-goals and steps. Imagine mapping out how an attacker could compromise a database server. This method helps clarify attack paths and identifies where to strengthen defenses.
We found attack trees helpful when dealing with systems that have multiple layers or entry points.
Other Techniques
There are several other useful approaches:
- VAST: Good for scaling threat modeling in large environments.
- Trike: Focuses on risk scoring for prioritization.
- CVSS: Assesses severity of vulnerabilities.
- Security Cards: Encourages brainstorming to generate fresh threat ideas.
Summing Up Threat Modeling Techniques
| Technique | Description | Use Case | Key Benefit |
| STRIDE | Six threat categories | System-level threat identification | Covers common threat types |
| PASTA | Attacker-centric, business-aligned | Business impact-focused analysis | Prioritizes threats by business risk |
| Attack Trees | Visual attack path breakdown | Complex attack analysis | Identifies vulnerabilities clearly |
| VAST | Scalable threat modeling | Large, complex systems | Automates and scales process |
| Trike | Risk scoring | Prioritizing threats | Quantitative risk measurement |
| CVSS | Vulnerability scoring | Severity assessment | Guides remediation priorities |
| Security Cards | Collaborative brainstorming | Generating new threat ideas | Encourages creativity and coverage |
A Practical Look at Using Threat Modeling
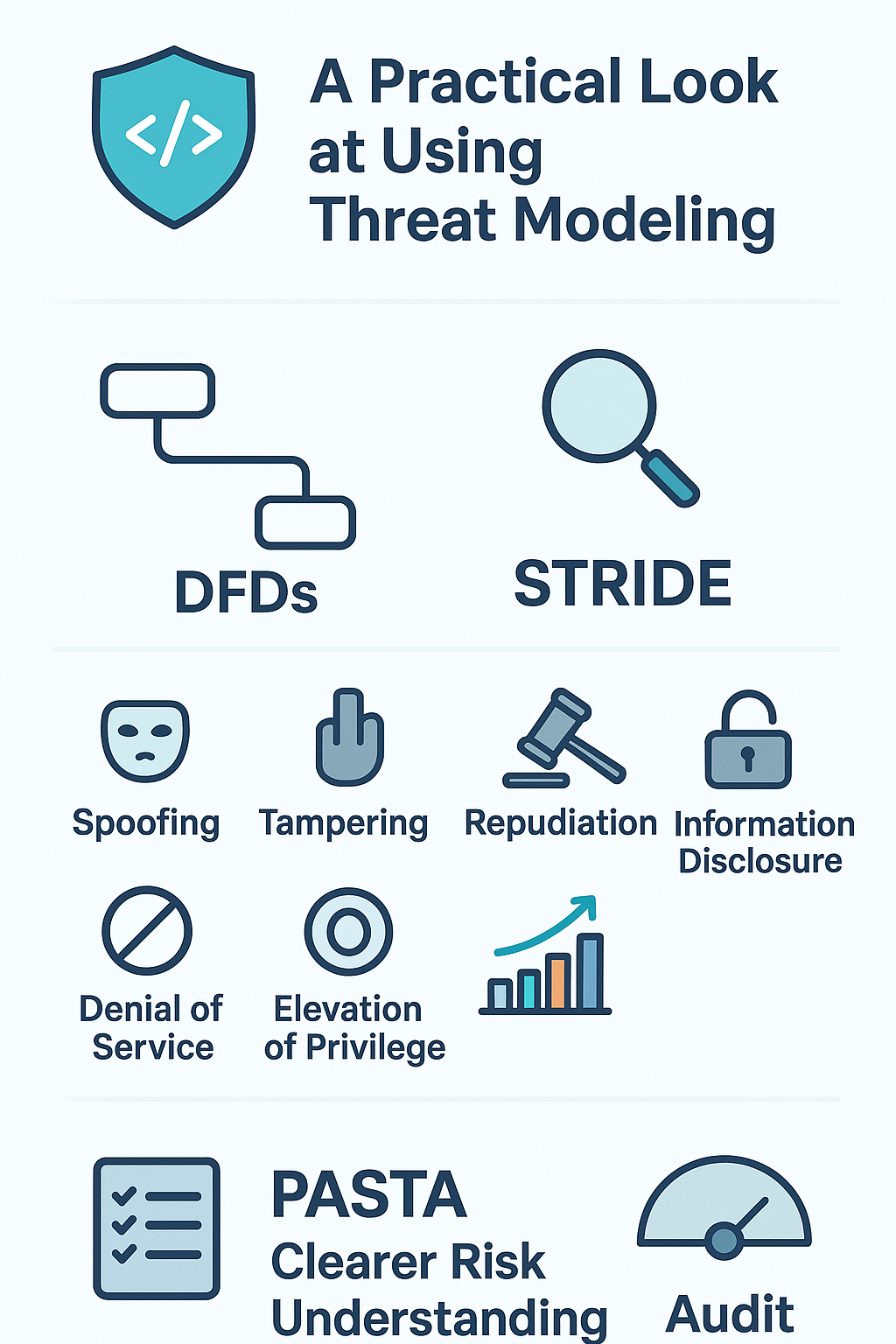
When our team first started threat modeling, it felt like an abstract exercise. But as we combined it with secure coding practices, we noticed fewer security gaps slipping through. For instance, by defining our scope clearly and using DFDs, we caught data flow issues early. Applying STRIDE helped spot common attack types, while PASTA gave us a broader business view.
Threat modeling also improves communication. Everyone from developers to management gets a clearer understanding of risks and priorities. It’s not just about technical controls but about aligning security with business needs. Plus, it makes audits and compliance checks less stressful.
FAQ
What is threat modeling and why is it important in cybersecurity?
Threat modeling helps you see your system through an attacker’s eyes. It’s a structured way to spot security vulnerabilities, understand attack vectors, and plan risk mitigation before problems happen. By using threat identification and system modeling, teams can create a clearer view of their security posture and prevent cybersecurity threats early.
Which techniques are most common in basic threat modeling?
Common techniques include the STRIDE methodology, PASTA framework, and attack trees. These help teams perform threat analysis and threat prioritization by breaking down threat scenarios and attacker profiles. Using these structured methods gives developers a better grasp of security controls and helps guide smart security design choices.
How do data flow diagrams and system modeling help in threat modeling?
Data flow diagrams and system modeling show how information moves through your system. They help find weak spots and security gaps in security architecture. When combined with vulnerability analysis and threat taxonomy, they create a strong foundation for understanding the threat lifecycle and building secure software development practices.
What role does risk assessment play in threat modeling?
Risk assessment helps teams weigh the impact of each threat event and decide where to focus defense. It includes risk evaluation, risk scoring, and business impact analysis. By linking these steps to threat mitigation strategies and security controls mapping, you can make better decisions that reduce overall security risk and exposure.
How can teams improve their threat modeling process over time?
Teams can refine the threat modeling process through regular security assessment, penetration testing, and security auditing. Adding threat intelligence, threat tracking, and incident response improves awareness of the changing threat landscape. Over time, this leads to stronger threat-driven development, better security framework alignment, and more reliable security by design.
Conclusion
Threat modeling is more than a security checklist. It’s a way to think like an adversary, understand your system deeply, and protect what matters most. We believe secure coding practices should always be the first step, building security into software from day one reduces vulnerabilities and makes threat modeling more effective.
By defining your scope carefully, creating clear system models, identifying and assessing threats, and iterating your approach, you set yourself up for stronger defense against cybersecurity threats. Techniques like STRIDE and PASTA provide proven frameworks to help you along the way.
If you’re ready to take threat modeling seriously, start small but stay consistent. Make it part of your development lifecycle and encourage your team to think proactively about security. The effort pays off when you prevent incidents rather than reacting to them.
Security is a journey, not a destination, and threat modeling is your map. Join the Secure Coding Practices Bootcamp to learn how to build secure software from day one through real-world, hands-on coding sessions.
References
- https://deepstrike.io/blog/vulnerability-statistics-2025
- https://www.getastra.com/blog/security-audit/cyber-security-vulnerability-statistics/

