Security gaps can wreck even the most promising software project. Our years training developers showed us that threat modeling catches these issues early, long before deployment. This systematic approach helps development teams find and fix potential security flaws during the Software Development Life Cycle, not after things go wrong. We’ve watched countless teams transform their security approach through smart threat modeling – spotting risks that automated tools miss. The practice meshes smoothly with secure coding standards, creating a thorough defense strategy. Want to learn how this could strengthen your team’s security game? Let’s explore further.
Key Takeaways
- Threat modeling proactively spots risks early, saving time and money later.
- It strengthens security design by uncovering vulnerabilities in architecture and code.
- Collaboration among teams improves, fostering a security-aware culture throughout development.
The High Cost of Neglecting Threat Modeling
Security breaches cost companies billions every year. Major security breaches can cost companies hundreds of millions to billions of dollars, depending on scale, lost trust, regulatory fines, and recovery costs. According to the 2025 IBM / Ponemon Institute ‘Cost of a Data Breach’ report, the global average cost of a data breach in 2025 was USD 4.44 million, while in the U.S. the average cost reached a record USD 10.22 million. (1) When software is deployed without a thorough threat analysis, vulnerabilities become prime targets for attackers.
For example, many high-profile incidents trace back to overlooked risks during early development phases. We’ve seen firsthand how reactive security measures often mean scrambling to patch flaws post-release, which is costly and sometimes too late to prevent damage.
Being proactive is different. When teams prioritize threat modeling, they catch threats before they turn into breaches. This approach flips the usual script, emphasizing prevention over cure. It’s like fixing the roof before the storm arrives rather than mopping up after the flood.
The financial impact of ignoring threat modeling is staggering. According to recent data, organizations spend up to 30 times more fixing security issues after release than during development. This heavy price tag includes lost customer trust, regulatory fines, and remediation expenses. It simply doesn’t pay to delay threat identification. Some studies show fixing defects in production can cost 5× to 100× more than if caught in early design or development phases, depending on the severity and system complexity
Integrating Threat Modeling into the SDLC: A Phase-by-Phase Guide
Requirements Phase
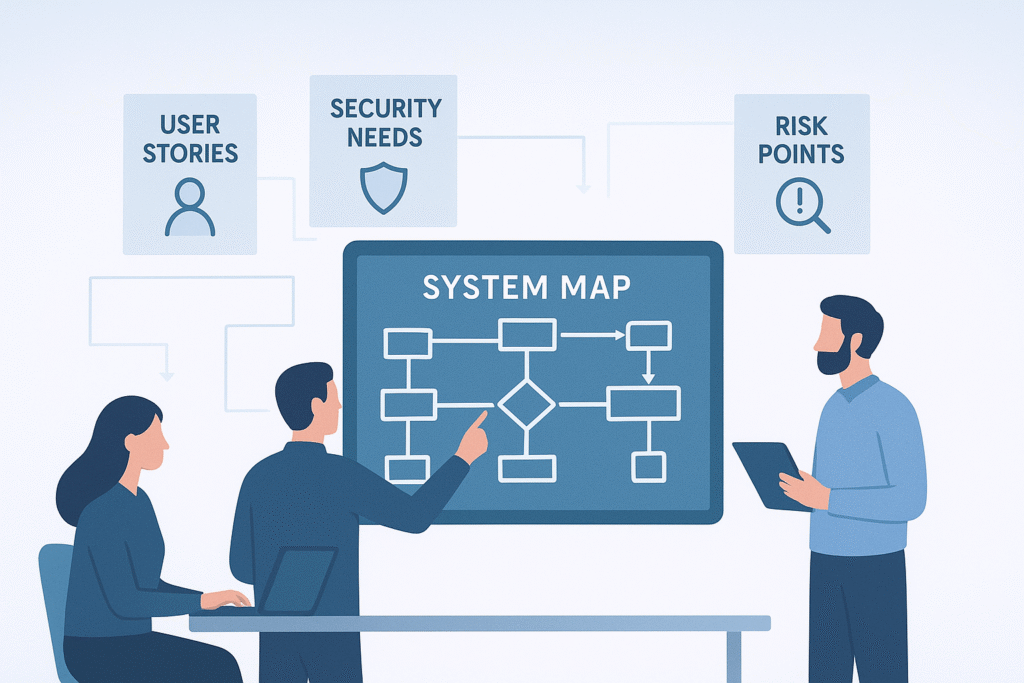
Early in the SDLC, we focus on identifying threats tied to user stories and system requirements. This is where the attack surface starts to take shape. By analyzing data flows and mapping how information moves through the system, potential risk points become clearer.
- Defining security requirements early helps us mitigate risks before they grow.
- Using tools to automate threat identification at this stage speeds up analysis.
- We’ve found data flow diagrams especially helpful for visualizing vulnerabilities, a key technique discussed in introduction to threat modeling.
While automated tools can help in early phases to flag common threats, human review remains essential to capture architectural or domain-specific risks. This phase sets the foundation for all that follows. Without clear security needs, later efforts might miss the mark.
Design Phase
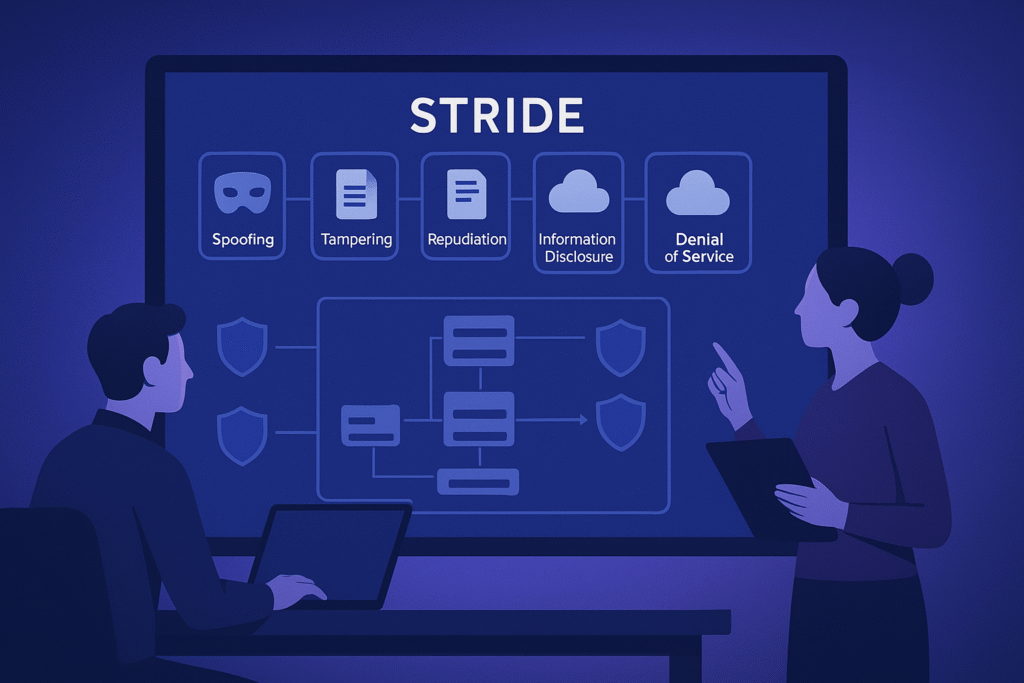
Now system architecture gets a deep security check. Here, secure design principles like least privilege and defense in depth guide decisions. Threat modeling architectural components reveals weak spots that might expose the system to attack vectors.
Here’s what usually happens:
- Teams analyze components for vulnerabilities in how they interact.
- Potential attack vectors are identified and prioritized.
- We adjust design documents to patch holes before coding starts.
For example, applying STRIDE methodology at this phase has helped us classify threats systematically, spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege, enabling targeted defenses.
Coding Phase
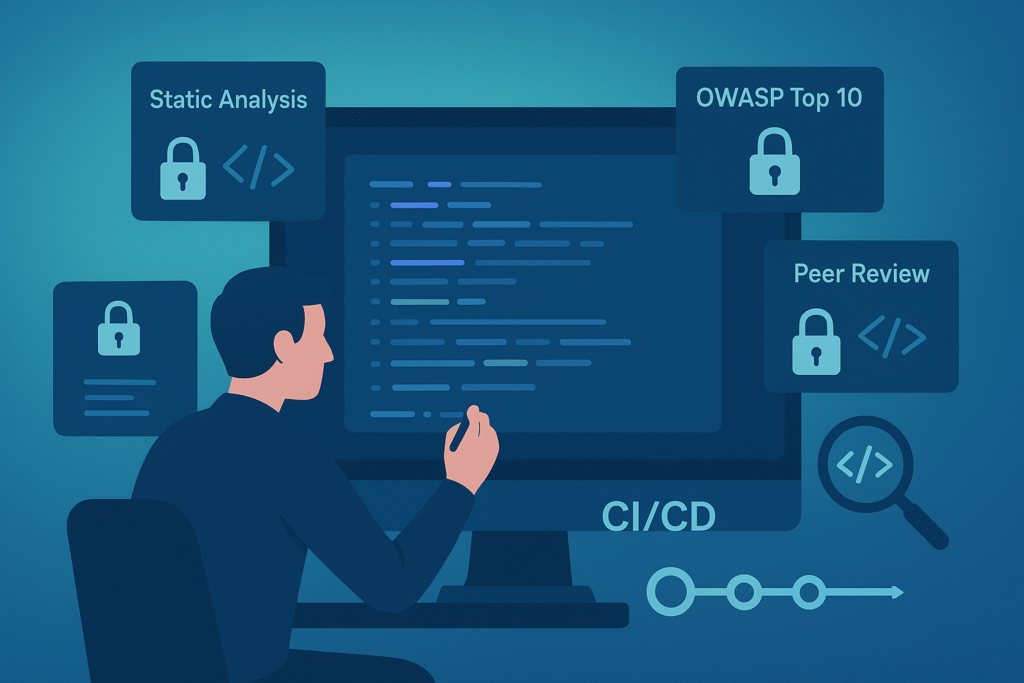
This is where our secure coding practices come into full effect. Writing code with security in mind prevents many common vulnerabilities, including those listed in the OWASP Top Ten. We emphasize code reviews and employ static analysis tools to spot issues early.
- Static analysis integrates seamlessly into CI/CD pipelines, catching flaws as code changes.
- Secure coding standards guide developers to avoid pitfalls.
- Regular peer reviews add a layer of human insight.
From our experience (shared in threat modeling for developers), combining these practices reduces coding vulnerabilities significantly has been shown in practice to reduce the number of coding vulnerabilities by a measurable margin (e.g., fewer defects in security testing), especially when static analysis and peer reviews are consistently applied. It’s not just about writing code fast but writing it right.
Testing Phase
Threat modeling informs our security testing by defining abuse cases and attack scenarios. Penetration testing becomes more targeted, focusing on the highest priority threats identified earlier.
- Test cases validate if security controls effectively mitigate risks.
- Dynamic analysis complements static tools by evaluating running applications.
- Security automation tools speed up repetitive testing.
This phase is where theory meets reality. Testing confirms whether design and coding efforts hold up under simulated attacks.
Deployment Phase
Once software is ready to launch, secure configuration and deployment practices ensure a hardened environment. Monitoring and logging systems detect anomalies, providing early warning for incidents.
- Intrusion detection and SIEM solutions enhance ongoing security.
- Security governance ensures compliance with policies and standards.
- Incident response plans prepare teams for potential breaches.
We’ve seen that continuous security monitoring after deployment is vital, as the threat landscape never stands still.
Building Attack Resilience Through Threat Modeling
Credit: Aquia
Understanding potential attack vectors is more than a checklist exercise. It’s about envisioning how adversaries might exploit weaknesses and preparing robust countermeasures. This mindset makes systems more resilient through every SDLC stage.
Here’s what we focus on:
- Mapping threat scenarios to anticipate real-world attacks.
- Designing layered defenses that reduce single points of failure.
- Adjusting security controls based on evolving intelligence.
Designing layered defenses so systems are more resilient to breach attempts, reducing single points of failure and enabling more effective mitigation. This approach echoes concepts from the what is threat modeling process which emphasizes continuous iteration and validation as essential parts of effective security.
In fact, the inaugural State of Threat Modeling Report 2024‑25 found that 88% of organizations said they use the STRIDE methodology in some form and that creating system diagrams is mandatory in 74% of cases. (2)
Why Secure Coding Practices Must Lead the Way
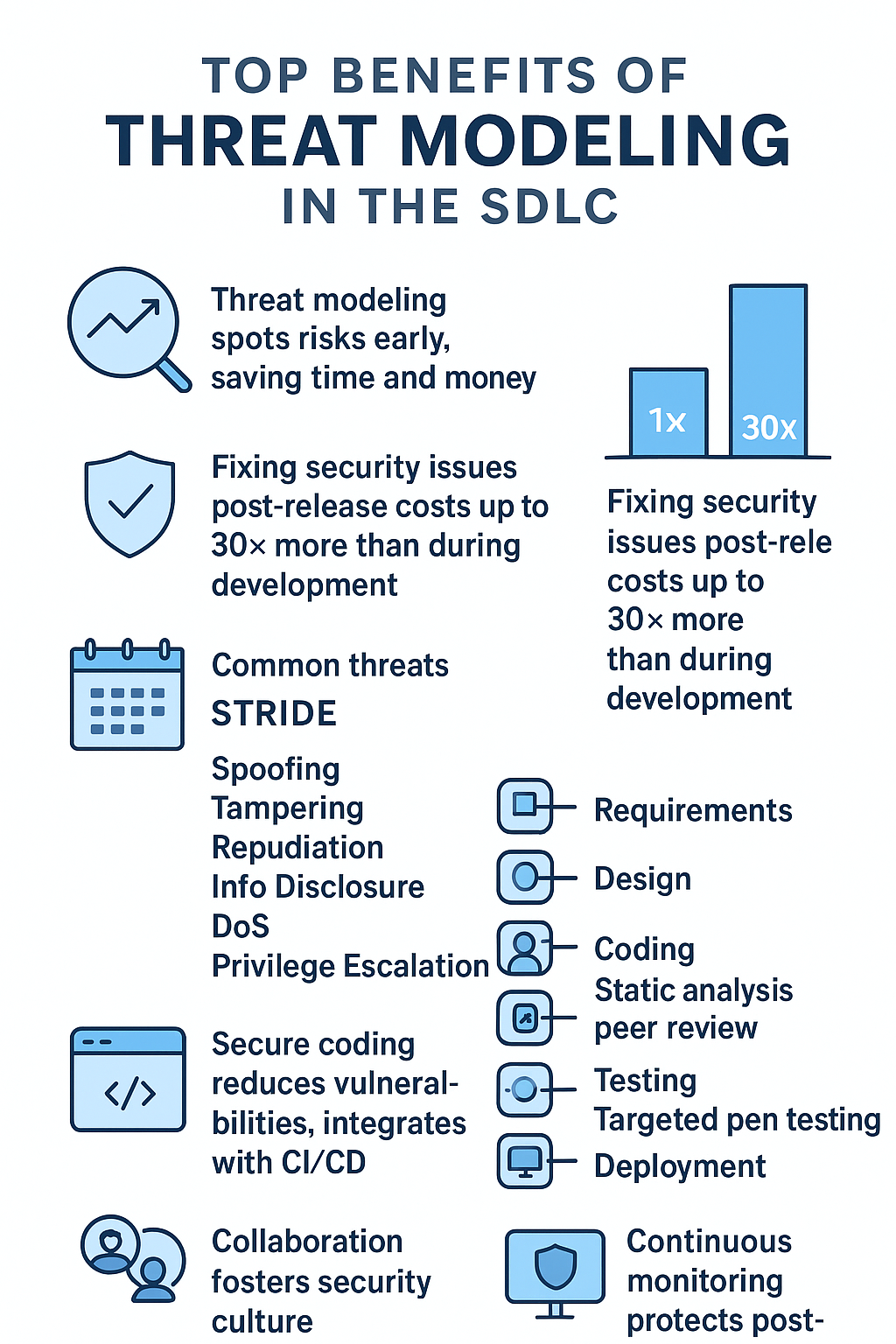
Throughout this entire journey, secure coding practices form the backbone of effective threat mitigation. We advocate embedding security early into the development mindset. It’s not an add-on but the foundation on which everything else rests supported by standards like the OWASP Top 10, secure coding guidelines, and peer code reviews.
- Secure coding stops vulnerabilities before they become risks.
- It supports compliance by meeting security requirements from the start.
- Together with threat modeling, it creates a proactive security lifecycle.
By weaving secure coding into the SDLC fabric, teams build software that’s safer by design.
FAQ
What is threat modeling in the SDLC, and why does it matter?
Threat modeling helps teams find and fix security risks early in the SDLC security process. It focuses on threat identification, risk assessment, and vulnerability identification before software deployment. By mapping attack vectors and software vulnerabilities, developers can design secure software that’s more resilient to security threats and ensures stronger software security overall.
How does threat modeling improve software security and risk management?
It gives security teams a clear view of the threat landscape, helping with risk analysis, threat prioritization, and risk mitigation. By integrating security controls, data protection, and access control into system architecture, threat modeling supports better security governance and compliance requirements. This proactive step improves SDLC security and reduces costly software flaws later.
What techniques are used in threat modeling during secure development?
Common methods include the STRIDE methodology for identifying threat scenarios and the PASTA technique for deeper risk modeling. Teams also apply secure coding standards, security testing, and dynamic analysis to spot software risks early. Together, these tools support secure design principles, security architecture review, and overall software assurance.
How does threat modeling support continuous security across the lifecycle?
Threat modeling strengthens the cybersecurity lifecycle through security planning, secure development practices, and continuous security monitoring. It connects threat detection, incident response, and penetration testing, ensuring threats are caught fast. Regular security assessments and auditing build resilience, improve security documentation, and guide long-term threat mitigation strategies within the SDLC.
How does threat modeling help with compliance and real-world security?
By combining security frameworks, security policies, and compliance requirements, threat modeling supports security enforcement and auditing. It prepares systems against insider threats, external threats, and attack surface expansion. Through security automation tools, identity management, and supply chain security planning, organizations maintain security compliance while ensuring ongoing breach prevention and system resilience.
Conclusion
Threat modeling isn’t just a box to check, it’s a powerful approach that builds stronger, more secure software. From early risk assessment to continuous monitoring after deployment, it helps cut costs, reduce vulnerabilities, and foster collaboration across teams.
If your goal is to create resilient, secure software that stands strong against evolving threats, integrating threat modeling with secure coding practices is the way forward, integrating threat modeling with secure coding practices, and ensuring threat models are updated throughout the SDLC and operations, is the way forward. Our experience shows that organizations embracing this proactive approach earn user trust and stay ahead of attacks.
Ready to strengthen your SDLC security? Start by embedding threat modeling into every development phase, and take the next step with the Secure Coding Practices Bootcamp.
Train your developers through hands-on, real-world sessions covering the OWASP Top 10, secure authentication, encryption, and more, so your team can ship safer code from day one.
References
- https://www.helpnetsecurity.com/2025/08/04/ibm-cost-data-breach-report-2025/
- https://www.threatmodelingconnect.com/state-of-threat-modeling-2024-25

