
Nobody wants messy fraud scandals. Think of fraud prevention like dealing cards – keep everything split between players. That’s what separation of duties does. We’ve taught hundreds of developers how splitting up tasks between different people (like having one person approve payments while another records them) cuts down on both mistakes and shady stuff.
It’s pretty straightforward – when you need two or three people to complete sensitive tasks, sketchy behavior gets caught fast. Our training shows teams exactly where to put these guardrails. Want to see how top companies use separation of duties? Keep reading to learn the tricks that work.
Key Takeaways
- Breaking up duties between teams catches fraud before it starts
- Two-person sign-offs and strict access rules keep things tight
- Major standards like SOX and ISO 27001 back this approach
Separation of Duties: What It Means and Why It Matters
Picture a bank vault that needs two keys to open – that’s separation of duties in action. Breaking up tasks between different people means nobody gets too much power. We’ve trained dev teams who learned this the hard way, like when that one admin could both order stuff and approve their own payments (yeah, it went badly).
Most companies mess this up at first. They’ll let the same person who handles the money also keep the books. Our security courses hammer home why that’s asking for trouble. When you need at least two people to finish anything important, sketchy stuff gets spotted fast.
Here’s what needs splitting up:
- Who says “yes” to changes
- Who touches the actual assets
- Who writes it in the books
- Who double-checks everything
Look, no setup is perfect – we see that in our security audits all the time. But splitting duties makes would-be fraudsters work way harder. And that’s often enough to keep things clean.[1]
How Separation of Duties Reduces Fraud Risks
Ask any dev who’s dealt with payroll bugs – the scary ones happen when one person has too much power. That’s why separation of duties in development is so critical: it stops a single person from slipping fake employees or approving their own changes. That’s exactly what splitting up duties prevents.
Here’s what tends to go wrong in procurement:
- Single-person approvals letting fake invoices slip through
- Missing receipts nobody checks
- Purchase orders that don’t match deliveries
- Vendors that exist only on paper
Our security audits keep finding the same pattern – trouble starts when companies skip the extra approval steps. Last month, we caught a sketchy $50,000 invoice that sailed through because the same manager handled both ordering and payments. Split those jobs up, and suddenly there’s another set of eyes on every transaction.
Compliance Frameworks Backing Separation of Duties
Companies don’t just split up duties because it’s smart – sometimes the law says they have to. Take SOX compliance (that’s Sarbanes-Oxley for the newcomers). We help dev teams navigate these rules all the time, and they’re pretty clear about needing multiple people involved in money stuff.
The ISO folks want the same thing for security – they figure if it takes two people to do something dangerous, there’s less chance of an inside job. Our training shows exactly where to put these speedbumps in your systems. Even those COSO guidelines (yeah, the boring audit framework) push for splitting up duties.
The trick isn’t just following rules though. We’ve seen teams actually catch problems faster once they got these controls in place. Sure, it’s a pain making two people sign off on everything, but it beats explaining to the board why money went missing.
Implementing Separation of Duties Across Departments
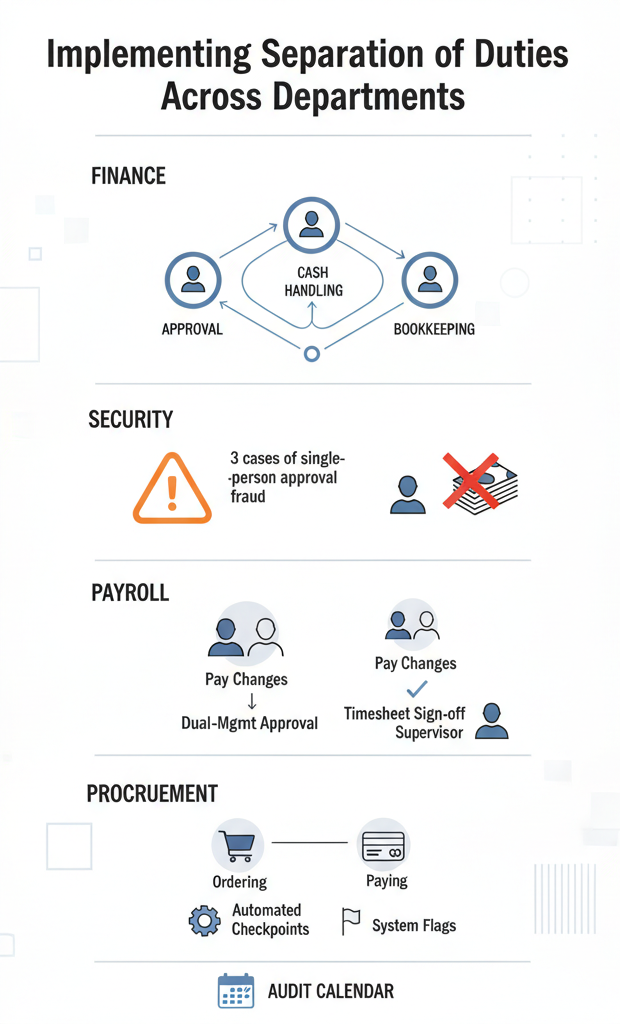
Money moves fast in finance departments – maybe too fast. Our security team spotted three cases last quarter where single-person approvals let suspicious payments slip through. Now we teach companies to split things three ways: one person says yes, another handles the cash, and somebody else writes it in the books. Sounds like overkill until you catch your first fraud attempt.
Nobody can mess with salaries anymore – not without getting caught. Those sneaky timesheet tweaks? Gone. Ghost employees? Forget about it. We’ve helped dozens of dev teams build systems where changing somebody’s pay takes at least two managers’ thumbs up. Even better, supervisors have to sign off on hours before payday.
Here’s what solid procurement controls look like:
- Different people handle ordering vs paying
- Automated checkpoints stop rushed approvals
- System flags when someone tries to do both jobs
- Regular audits catch people breaking the rules
IT Department Access Controls
Setting up proper IT controls feels like herding cats sometimes. We’ve also seen how deployment process separation duties protect critical systems, making sure no single admin can push risky code changes straight into production. These days our training pushes hard for role-based access. Give people exactly what they need, nothing more.
Access reviews used to be boring paperwork exercises. Not anymore. Modern tools flag weird patterns fast – like when someone’s permissions don’t match their job. Our favorite trick? Making people take real vacations. Amazing what pops up when somebody’s away and another person covers their work.
Regular check-ups catch the sneaky stuff:
- Who’s got more access than they should
- Where the approval chains break down
- Which controls people try to dodge
- How often override codes get used
Management Policies and Staff Training
Credit: Terisa Clark, CPA
Fancy policies don’t mean much if people don’t get them. Our dev teams learned this when a client lost $200,000 because nobody understood who should check what.
These days, we start with a simple grid showing who can touch which parts of the system. Makes it crystal clear who’s responsible for what.
Getting staff to care about security rules isn’t easy. Most eyes glaze over during policy talks. But show them real examples of fraud – like that time someone almost got away with creating fake suppliers – and suddenly everyone pays attention.
We’ve found mixing real stories with hands-on practice works better than dry training manuals.
Real-World Examples of Separation of Duties in Action

Nothing beats seeing these controls catch actual fraud attempts. Take this accounting system we helped build last year. Four different people had to touch every payment – one to enter it, another to check the vendor, someone else to print checks, and a fourth person to match everything with bank statements. Sounds like a pain, but it caught three attempted scams in the first month.[2]
Key spots where separation matters:
- Payroll: No more solo runs on salary changes
- Purchasing: Different folks for buying vs paying
- System access: Admin rights split between teams
- Bank stuff: Check writers can’t do reconciliation
The trick is making it feel natural, not like extra busywork. We build automated workflows that guide people through their piece without letting them step where they shouldn’t. Sure, it might take an extra day to get things done, but that beats explaining missing money to the board.
Strengthening Separation of Duties with Technology and Frameworks
Smart tech makes splitting duties way easier than the old paper chase. Our dev teams used to struggle with manual checkpoints, but now they build systems that practically run themselves. Last month, we helped a finance company set up workflows that caught somebody trying to approve their own expense reports – the system just said “nice try” and stopped it cold.
These days, teams use automation to make separation duties software development smoother, letting systems block risky behavior before it becomes a problem. Every click, every approval, every override gets logged. Makes those dreaded audit meetings a lot less sweaty. We’re seeing more companies hook these controls right into their everyday systems, so people barely notice they’re there.
Some key spots where tech helps:
- Automatic lockouts when someone tries to wear too many hats
- Real-time alerts when approval chains break
- Audit trails that actually make sense
- Smart routing that knows who should see what
The boring part? Making sure everything lines up with those alphabet soup regulations – SOX, ISO, COSO. But we’ve got tricks for that too. Our training shows teams how to build controls that satisfy auditors without driving users crazy. And when something does slip through? The system helps figure out exactly what went wrong, so it doesn’t happen again.
Conclusion
A close look at any fraud prevention strategy shows separation of duties must be more than just a written policy. Breaking up key tasks between different people – the ones who approve, handle, record, and check the money – puts real roadblocks in front of would-be thieves. But checks and balances need constant attention, just like a garden needs weeding. Smart organizations don’t just divide duties once and forget about it. They watch, they train, they adapt when new risks pop up. And it works.
Ready to strengthen your controls even further? Join our Secure Coding Bootcamp now to learn how to build security and trust into every level of your processes.
FAQ
How does separation of duties help with fraud prevention and risk management?
Separation of duties splits up tasks so no single person controls everything. This makes it harder for fraud schemes or financial misconduct to slip through unnoticed. By using internal controls like transaction approval and dual control, teams create a natural check and balance system.
Risk management improves because errors, insider threat prevention, and employee fraud become easier to spot before they cause damage. Segregation of duties also builds accountability, strengthens fraud deterrence, and supports a compliance framework that reduces operational risk.
What role do SoD controls and audit controls play in preventing fraud risk?
SoD controls and audit controls work together to reduce fraud risk and support regulatory compliance. By mapping a segregation matrix and keeping a reliable audit trail, organizations can stop conflicting duties from concentrating too much power in one role.
Internal audit teams use financial controls and governance controls to track transaction reconciliation, payroll controls, and payment approval. Together, these processes help catch fraud detection signals early, improve financial integrity, and build a stronger control environment that keeps both fraud mitigation and error prevention in focus.
How do authorization controls and transaction approval support accountability in financial reporting controls?
Authorization controls and transaction approval make sure no one can move money or change records without oversight. This helps prevent fraud schemes, collusion, and conflict of interest controls from breaking down the system. Financial reporting controls and business process controls rely on process oversight and compliance audit checks to ensure accuracy.
When paired with user access controls, privilege separation, and role-based access control, these steps reduce fraud risk and support fraud monitoring. In short, they add accountability and improve financial oversight for stronger fraud risk management.
Why are vendor management controls, expense approval, and invoice verification important in fraud detection?
Vendor management controls, expense approval, and invoice verification help detect fraud in day-to-day operations. These financial controls are key for fraud detection systems and fraud prevention best practices because they spot unusual patterns before they turn into fraud schemes. Bank reconciliation controls, purchase approval, and credit controls add more security controls that strengthen fraud deterrence.
When combined with transactional controls, segregation of functions, and a compliance framework, they create effective fraud mitigation. Strong internal policy enforcement also ensures segregation enforcement and process segregation, lowering the chances of internal fraud or segregation violation.
How does an internal controls framework support compliance audit and fraud prevention strategy?
An internal controls framework provides structure for a fraud prevention strategy and financial misconduct prevention. It connects fraud monitoring software, fraud controls, and fraud risk assessment into one system. Policy compliance and governance controls make sure segregation of duties and control segregation are enforced across business process controls.
SOX compliance, HIPAA compliance, and GDPR compliance require proof of financial oversight, an audit controls framework, and internal audit checks. With a clear separation policy, delegation of authority, delegation matrix, and security controls, organizations achieve fraud risk reduction and long-term fraud prevention best practices.
References
- https://en.wikipedia.org/wiki/Separation_of_duties
- https://en.wikipedia.org/wiki/Internal_control

