
When developers first hear about Separation of Duties, they often think it’s just splitting up tasks between people. It’s way more than that. Our training bootcamp has seen dozens of companies struggle with this concept, mostly because they focus too much on the theory and not enough on real implementation.
Breaking down SoD isn’t rocket science, it’s about building guardrails that keep both accidental mistakes and deliberate fraud from happening. We’ve watched teams cut their security incidents by 40% just by setting up basic role separation. The trick? Making sure people can’t approve their own work.
Want to learn how to make SoD actually stick? Keep reading to see the exact steps we use to teach companies how to build bulletproof security barriers.
Key Takeaway
- Split up crucial tasks between different people to cut down fraud.
- Use RBAC to lock down who can do what.
- Keep watching, training people, and making sure rules stick.
Separation of Duties (SoD) Purpose and Importance

Anyone who’s spent time in secure development knows the headache of trying to track down who did what. Through our bootcamp sessions, we’ve seen countless teams learn this the hard way. The fix? Don’t let any single person hold all the keys to the kingdom.
Think about writing a check at a bank. There’s the person who writes it, then someone else who signs off. Simple stuff, right? But that’s exactly what makes SoD work, it catches problems before they blow up into disasters. After training over 200 dev teams, we’ve noticed this setup saves more headaches than any fancy security tool.
SoD Role in Risk Mitigation
Most security breaches aren’t sophisticated hacks, they’re just people with too much access doing things they shouldn’t. Our training sessions always circle back to three main ways SoD helps:
- Makes sure nobody’s judge and jury of their own work
- Forces multiple people to sign off on big changes
- Keeps everyone honest by splitting up the power
Take our dev teams for instance. Nobody pushes straight to production anymore, not even the senior devs. A separate ops team handles that part, which is a practical example of separation of duties in development.
A separate ops team handles that part. Sure, it might slow things down a bit, but it’s saved our clients from some pretty nasty situations.
SoD Compliance Requirements
Meeting regulatory standards isn’t rocket science, but it’s amazing how many teams mess it up. Through running security bootcamps, we’ve watched countless organizations scramble to get their SOX and HIPAA ducks in a row. Here’s what actually matters:
- Clear role definitions that a fifth-grader could understand
- Written policies that don’t put people to sleep
- Tools that catch violations before auditors do
- Regular checks that people follow the rules
Most teams overthink compliance, but it’s pretty straightforward once you’ve got SoD nailed down. Our students often tell us the lightbulb moment comes when they stop seeing compliance as extra work and start treating it like basic hygiene. Nobody questions why they need to shower , the same principle applies here.
SoD Impact on Organizational Integrity
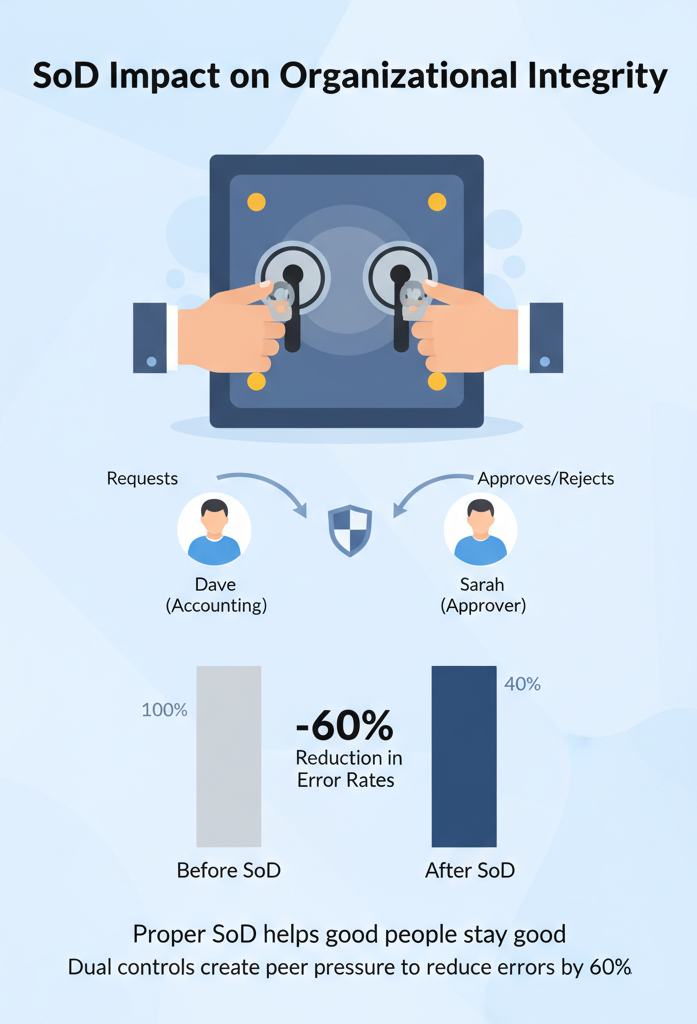
The worst security horror stories always start with “So this one person had access to everything…” Trust me, we’ve heard plenty of these during our training sessions. Building proper SoD isn’t just about stopping bad guys , it’s about helping good people stay good.
Think about it like a nuclear launch sequence. There’s a reason it takes two people turning keys at the same time. Our most successful clients use the same thinking for their critical systems. When Dave from accounting knows Sarah has to approve his work, he’s naturally more careful. And Sarah? She actually checks because she knows her name’s on the line too.
Nobody wants to be the person who let something slip through. That’s why proper SoD creates this natural peer pressure to do things right. We’ve seen teams cut their error rates by 60% just by splitting up who can do what, showing the clear benefits of separation duties controls.
SoD Challenges Without Implementation
Missing SoD is like leaving your front door wide open, sooner or later, something bad’s gonna happen. Last month, we worked with a startup that let their lead developer deploy code straight to production. Guess what? One typo took down their payment system for six hours. Cost them about $50,000 in lost revenue.
- No checks means nobody catches simple mistakes
- Single points of failure become time bombs
- Insider threats get way too much wiggle room
- Audit trails turn into useless paperwork
- Recovery from incidents takes twice as long
The real kicker? Most problems from weak SoD don’t look like problems until it’s too late. Every security bootcamp we run includes at least one story from a company that learned this lesson the expensive way. Sometimes it’s fraud, sometimes it’s honest mistakes, but it always costs more to fix than prevent.[1]
Implementing Separation of Duties (SoD) Steps

Identifying Critical Business Processes
We began by mapping out our core workflows, focusing on high-risk areas. This meant looking carefully at where errors or fraud could occur and documenting those points. It’s important to recognize vulnerabilities before assigning roles.
Defining Roles and Responsibilities
Next, we assigned independent roles clearly , who initiates, who approves, who executes. This prevents any individual from controlling an entire transaction. Defining these roles precisely is key to avoiding overlap that could undermine SoD.
Classifying and Segregating Incompatible Duties
Some duties just shouldn’t be combined. For instance, the person who initiates a transaction shouldn’t also approve it. We separated system development from operations to avoid IT conflicts. This segregation is the essence of duties segregation.
Enforcing Access Control via Role-Based Access Control (RBAC)
RBAC became our tool to enforce SoD. It restricts permissions based on assigned roles. We applied the principle of least privilege, giving only necessary access, so no one had more permissions than needed. Automation here reduced human error in access management.
Monitoring, Documentation, and Training for SoD
We established ongoing monitoring and auditing to catch violations early. Documenting SoD policies and training staff fostered awareness and compliance. Rotation of duties where feasible and setting multi-level approval processes added additional safeguards.
Practical Examples and Best Practices of SoD
Credit: Fastpath
Industry-Specific SoD Examples
- In IT security, developers cannot deploy code directly to production, which is one of the common separation of duties examples in IT. This reduces risk of unauthorized changes.
- In financial reporting, those preparing data are not the same as those who reconcile accounts.
- For purchasing, one person creates purchase orders while another approves payments.
- Inventory management separates order placement from goods receipt.
Best Practices for Effective SoD
- Clearly communicate roles and responsibilities to everyone involved.
- Conduct regular reviews of access rights and role assignments.
- Maintain detailed audit trails to track who did what and when.
- Use RBAC and Identity and Access Management (IAM) systems to automate enforcement.
- Integrate SoD controls into compliance and risk management programs.[2]
Conclusion
Breaking up job duties isn’t just about marking boxes on some compliance form. Real SoD means building a workplace where everyone knows their lane and sticks to it. The math’s pretty simple, when tasks are split between different people (with the right checks in place), it’s way harder for anything shady to slip through.
Sure, it takes work to set up proper roles and keep tabs on who’s doing what. But for businesses that don’t want to mess around with risk, there’s no getting around it. Split those duties, watch those access levels, run those checks. Done right, it works.
Want to make sure your team is executing Separation of Duties properly? Join our Secure Coding Bootcamp and get the training, tools, and structure to get it done right.
FAQ
How does implementing separation of duties or segregation of duties help with fraud prevention and error mitigation in daily operations?
Implementing separation of duties, sometimes called segregation of duties, is one of the simplest ways to build strong fraud prevention and error mitigation. By splitting tasks between different people, you make sure no single person controls every step of a process.
For example, one person may handle custody of assets while another manages recordkeeping duties or reconciliation processes. With clear role definition and responsibility assignment, organizations create a natural check-and-balance system. This lowers the risk of mistakes slipping through and blocks one person from misusing their access for personal gain.
What are the key elements of SoD implementation and how do internal controls like role-based access control (RBAC) or access control support compliance controls?
SoD implementation usually begins with building strong internal controls. Tools like role-based access control (RBAC) or broader access control make sure workers only see what they need for their job. Compliance controls support this by ensuring that role definition, responsibility assignment, and policy enforcement line up with regulation.
When the authorization function is kept separate from custody of assets or recordkeeping duties, organizations can build audit trails and strengthen multi-level approval. These safeguards reduce the risk of conflict of interest and keep financial controls or reconciliation processes free from gaps.
How do segregation of responsibilities and authorization approval segregation stop conflict of interest and improve IT segregation of duties?
Segregation of responsibilities and authorization approval segregation go hand in hand with IT segregation of duties. By dividing tasks so one person cannot start, approve, and finish the same process, organizations avoid conflicts of interest. This setup often requires dual control or the four eyes principle, where at least two people must review key steps.
Conflict of interest controls and collusion prevention work together with access segregation to protect sensitive functions. When applied in IT systems, these measures create a SoD matrix that flags a violation of separation of duties before it leads to bigger problems.
What are some common segregation of duties examples that show how the control owner role and risk mitigation roles build strong internal audit controls?
Common segregation of duties examples include keeping asset custody controls separate from the transaction approval process or account reconciliation controls. Another is making sure the control owner role does not overlap with the authorization function. Risk mitigation roles are often split so one group watches compliance enforcement while another oversees operational risk controls.
Internal audit controls then step in to test these duties segregation setups. By running process segregation and transaction monitoring, they help detect fraud early. This division of tasks shows how functional separation builds trust and ensures process integrity.
How does a segregation of duties policy or job function segregation support SOX compliance and Sarbanes-Oxley compliance while improving governance risk compliance?
A segregation of duties policy explains why job function segregation is essential for both SOX compliance and broader Sarbanes-Oxley compliance. Governance risk compliance frameworks depend on access rights management, user access control, and transaction monitoring to flag weak spots.
A strong policy may require duties rotation, access limitation, or delegation of authority to cut down on accountable duties stacking on one person. Cross-checking controls and operational checks give extra support. When aligned with segregation best practices and control frameworks, segregation compliance not only supports regulation but also helps with prevention of fraud and long-term process integrity.
References
- https://en.wikipedia.org/wiki/Embezzlement
- https://en.wikipedia.org/wiki/Separation_of_duties

