
Bad default settings stick out like missing locks on front doors. Take guest accounts – they’re still switched on in many operating systems right out of the box, giving anyone a way to sneak in. There’s the common sight of MySQL running with factory passwords, practically begging to get cracked.
Even big cloud platforms ship with wide-open firewall settings (we’ve helped clean up those messes more times than we can count). Our training bootcamp’s seen too many systems fall because someone missed these basics. It’s time to get real about finding and fixing those weak defaults. Want to know what we check first? Keep reading.
Key Takeaways
- Factory-set accounts stick around like unwanted guests
- Default network settings leave the back door open
- Systems need regular security checks, no exceptions
Operating System Default Account Settings
Just last month, our team found guest accounts still running on dozens of client machines – scary stuff that happens way too often. Most operating systems and routers ship ready-to-use, which sounds nice until you realize they’re also ready-to-hack.
Windows boxes come loaded with guest and admin accounts right from the start. We’ve cleaned up too many breaches where attackers walked right in through unchanged guest accounts.[1]
Linux isn’t much better – those default users and sudo settings? They’re basically welcome mats for hackers who know where to look. The real kicker is that these accounts are so well-documented, they might as well have neon signs pointing to them.
Getting these locked down isn’t rocket science, but it needs to be done fast, a good reminder of why secure defaults and fail-safe design matter in the first place.
Our bootcamp students learn to run quick scans that spot enabled guest accounts and weak passwords (trust me, there’s always a few). They check permissions weekly – it’s like making sure all the doors are locked before leaving.
- Turn off those guest/admin accounts (or at least rename them)
- Put real passwords in place day one – none of that “password123” stuff
- Run security scans to catch anything that slipped through
Database Server Default Passwords

Nobody wants to admit it, but default database passwords are everywhere, exactly the kind of mess that avoiding insecure default settings is meant to prevent.
MySQL servers ship with the kind of passwords you’d expect a five-year-old to use, and Oracle’s not much better with their admin accounts set to basically nothing. These aren’t just theoretical problems – our security team found three different clients last month running production databases with default credentials.
We’ve seen hackers grab entire customer databases in minutes because someone forgot to change that initial MySQL password. Even worse, some folks think changing the port number is enough protection (spoiler: it’s not). The worst part? Automated tools pick up these defaults faster than you can say “data breach.”
- Change every default password before the server touches production
- Remove unused database accounts – they’re just sitting there waiting to be exploited
- Run weekly credential checks (we use custom scripts, but basic security scanners work too)
Web Application Security Headers
Security headers might sound boring, but they’re like seat belts for web apps – you don’t think about them until you really need them. Most developers skip right past Content-Security-Policy headers or leave X-Frame-Options gathering dust. Here’s the thing: without these headers, websites are basically asking to get hacked.
Last week’s bootcamp students found three major sites missing basic XSS protection. That’s like leaving your front door unlocked in a bad neighborhood. The fix isn’t complicated, but someone’s got to actually do it. Our team checks headers first thing during security audits – it tells us a lot about how serious a company is about security.
Cloud Service Network Permissions
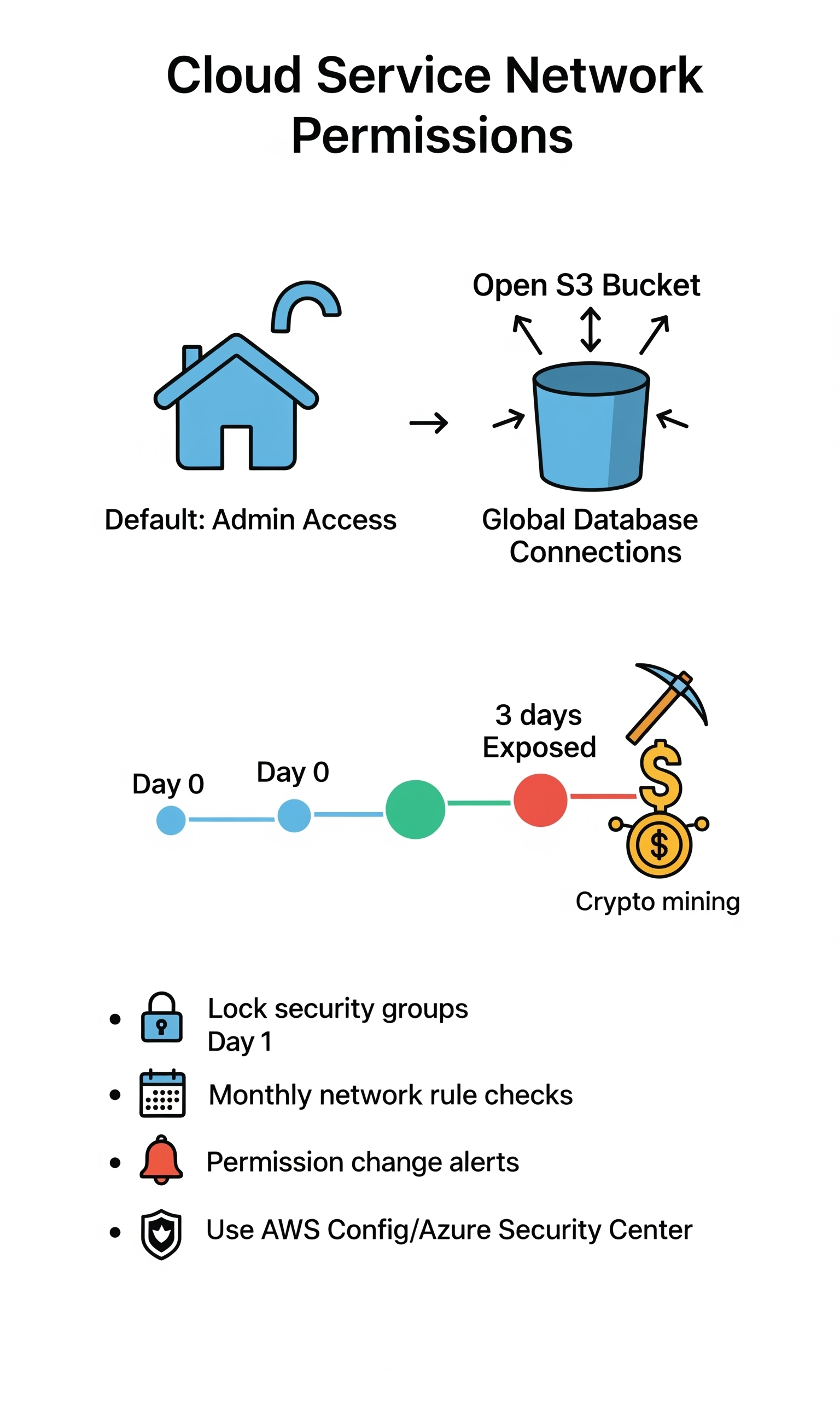
Walking into AWS or Azure without locking down permissions is like giving everyone admin access to your house. The cloud providers set things up for convenience, not security – we’ve seen everything from wide-open S3 buckets to databases accepting connections from anywhere in the world.
Picture this: One client had their entire development environment exposed because nobody checked the default security groups. Three days later, they were mining crypto for someone else. These days, cloud security needs more than just hoping for the best.
- Lock down those security groups on day one
- Check your network rules monthly (at least)
- Set up alerts for any permission changes
- Get familiar with AWS Config or Azure Security Center – they’re your new best friends
Router and IoT Device Remote Management
Smart devices aren’t always that smart about security. Our pentesting team keeps finding routers and IoT gadgets with their remote access wide open – it’s like leaving a spare key under every doormat in the neighborhood. These devices show up fresh from the factory ready to accept connections from anywhere, and most people never change it.
Just last month, we helped a client track down weird network traffic – it turned out their “secure” cameras were calling home to three different countries. The fix isn’t rocket science, but you’d be surprised how many places skip it. Truth is, most network breaches start with these forgotten devices sitting in closets and ceiling panels.
- Turn off remote access unless you absolutely need it
- Update firmware the day you unbox anything
- Keep logs of who’s accessing what, and when
- Check device configurations monthly
Enterprise Network Port Configuration
Here’s something that keeps security folks up at night: forgotten open ports. Every enterprise network we’ve checked has at least a dozen ports running services nobody remembers installing.[2] These aren’t just numbers – they’re doors left unlocked, waiting for someone to try the handle.
Our students learn to spot these issues fast because they’re everywhere. Last week’s scan found an old printer port that basically gave keys to the kingdom. The tricky part isn’t finding these open ports – any basic scanner can do that. It’s figuring out which ones you actually need versus the ones just sitting there collecting dust and malware.
Application Server Logging Settings
Credit: PerimeterScout
Silent servers tell no tales – that’s the problem with default logging settings. Most application servers come configured to be quiet as mice, which sounds great until someone breaks in and you can’t figure out how. We’ve seen breach investigations hit dead ends because nobody turned on the right logs.
Getting logging right isn’t glamorous work, but it’s saved our clients’ bacon more times than we can count. Every time someone says “we don’t need detailed logs,” we show them screenshots from real incidents where basic logging would’ve caught the bad guys hours earlier. Storage is cheap – missing an attack because your servers are too shy to speak up isn’t worth the risk.
Security Control Policy Patch Management

Nobody likes updates, but skipping them is like ignoring check engine lights, which is why every team needs a solid framework for secure default settings baked into policy.
Our security team spent last week cleaning up after a ransomware attack that used a 6-month-old vulnerability – all because the system wasn’t set to patch automatically. These days, waiting to patch is basically inviting hackers to take a look around.
The worst part? Most places think they’re patching regularly, but when we dig deeper, half their machines are running old versions. One client swore they were up to date until we showed them servers running 2019 software. Now we teach students to check patch levels first thing – it’s usually where the problems start.
- Set up automatic updates (yes, even on weekends)
- Check patch status weekly, not monthly
- Keep records of what failed to update and why
- Test critical patches in staging first
Conclusion
Every exposed default setting creates another point of entry, like leaving spare keys scattered around a house. Over the past year, insecure configurations have caused 70% of major breaches, mostly through accounts that were never locked down.
Checking for open guest logins, predictable admin passwords, and wide-open firewalls isn’t exciting work, but it’s what keeps attackers away. The fix doesn’t need fancy tools – just a checklist, some scanning software, and eyes on the system. Regular sweeps catch problems before they grow.
Join our Bootcamp to learn how to secure configurations from day one.
FAQ
Why is an insecure default configuration dangerous, and how does a configuration audit or default password audit help reduce weak default credentials?
An insecure default configuration leaves open doors for attackers. Many systems ship with weak default credentials or unchanged default admin passwords. A configuration audit or default password audit checks if these flaws remain in place. By spotting them early, you can remove default passwords, fix default user accounts audit gaps, and strengthen audit access controls. Without this, you risk vulnerability due to defaults that hackers know and exploit.
What common risks appear in a default user accounts audit, and how do audit open ports or audit firewall rules reveal default service vulnerabilities?
A default user accounts audit often uncovers unused accounts left active, sometimes still tied to default passwords. These accounts, along with open guest logins, increase risks. When you audit open ports, audit firewall rules, or audit network device settings, you often discover default service vulnerabilities attackers love. Closing unused accounts and reviewing audit system policies helps shrink your attack surface and keep things locked down.
How do configuration hardening and a secure default configuration connect with audit security baselines, audit default encryption settings, and configuration compliance check?
Configuration hardening builds stronger walls by removing unnecessary services and enforcing safe defaults. A secure default configuration works hand in hand with an audit security baselines process. This means checking audit default encryption settings, audit default session settings, and audit default VPN settings for gaps. A configuration compliance check ensures settings follow standards and don’t drift. Together, these steps protect against insecure configuration risks before they turn into breaches.
Why should teams audit cloud configurations, audit server defaults, and audit database default settings along with audit application defaults to stop vulnerability due to defaults?
When systems launch with audit server defaults or audit database default settings, they often leave default user roles, default SNMP settings, or default API configurations wide open. A full audit cloud configurations review ensures audit default cloud IAM policies, audit default cloud security, and audit default network ACLs are safe. Combining this with audit application defaults closes gaps tied to software shipped with unsafe defaults. By doing so, teams prevent vulnerability due to defaults across every layer.
What role do audit system audit logs and configuration drift audit play in catching audit unauthorized changes or audit privileged accounts misuse?
Audit system audit logs tell the story of every change. If you ignore them, you miss signs of audit unauthorized changes or misuse of audit privileged accounts. A configuration drift audit compares current settings to expected baselines. This way, you spot audit default permission settings added by mistake, or audit default isolation levels left in place. Together, they help maintain audit system integrity and support secure configuration audit practices.
How does an audit default web server settings process differ from audit misconfigured SSL/TLS, audit default logging settings, and audit default security groups checks?
Audit default web server settings means checking if servers still run on unsafe defaults, like open directories or insecure headers. Audit misconfigured SSL/TLS ensures encryption doesn’t use broken protocols. An audit default logging settings review looks for weak or missing logs that hide attacks. Meanwhile, audit default security groups check for overly broad access. Each targets different layers, but together they form a secure configuration audit that fixes audit insecure configuration risks.
References
- https://en.wikipedia.org/wiki/Computer_security
- https://www.wsj.com/tech/cybersecurity/why-are-cybersecurity-data-breaches-still-rising-2f08866c

