
Security settings don’t work like guesswork – they need teeth from the start. We see it every week in our bootcamp, when students run their first network scans and discover gaping holes that shouldn’t exist. Their test systems sit there with default passwords unchanged and ports wide open, just waiting for trouble.
Real companies learn this lesson the hard way, rushing to patch holes after attackers walk right in. Sure, frameworks like NIST CSF and ISO 27001 aren’t perfect road maps, but they give solid guardrails that work. Their baseline rules lock down access points and kill unnecessary services before they become problems. Want to see exactly how default settings make or break your security? Keep reading.
Key Takeaway
- Strong default settings cut down mistakes by giving teams a solid head start.
- Basic security guardrails should kick in the moment systems go live.
- Default configurations make it easier to follow security rules and meet compliance needs.
Picking Up the Basics: Framework Secure Default Settings Overview
Anyone who’s worked tech support knows the scary truth – what ships with a system matters more than what gets added later. You can’t count on everyone remembering to lock things down properly.That’s why we drill secure defaults and fail-safe design into our bootcamp students from day one.
Systems need to come pre-configured with tight security: unused stuff turned off, strong passwords required, data encryption ready to go.
We spend a lot of time in class showing how different frameworks handle this:
- NIST CSF locks things down the second you power up.
- CIS Controls come with preset rules that match their security checklist.
- ISO 27001 starts you off with need-to-know access only.
These layers of default protection shield systems before anyone can mess things up. It’s like having guardrails already installed on a mountain road – they’re there before you need them.[1]
NIST Cybersecurity Framework (CSF) Default Configuration

Every system starts somewhere, and NIST CSF makes sure it’s not rock bottom. The framework kicks in at startup, shutting down services nobody needs and closing ports that shouldn’t be open. Last month, our students found debug ports wide open on their test servers – common oversight that NIST’s rules would’ve caught right away. Most breaches we see come from stuff that should’ve been turned off from the start.
Basic protection means fewer ways in for the bad guys. Here’s what happens automatically:
- Services nobody asked for? Gone.
- Updates? They install themselves.
- Logging? Always watching.
Think of it like buying a car – you want the airbags already installed, not added later. NIST CSF builds in the safety features before anyone touches the system. Our bootcamp grads tell us this saves hours of manual hardening, plus it catches things humans might forget.
CIS Controls System Hardening Defaults
Nobody likes cleaning up other people’s messes. That’s why CIS Controls start with everything locked down tight. These rules match up with CIS Benchmarks (basically a security checklist on steroids). Guest accounts? Gone. Default shares? disabled by default. Registry locked down tight. We’ve seen these defaults cut security headaches in half during training exercises.
Most systems ship with way too many extra unnecessary components – demo accounts nobody needs, test code that shouldn’t be there, debugging switched on. CIS Controls strip all that away before day one. A student once found three different backdoors in sample code that came with their server. Not with CIS rules in place.
ISO/IEC 27001 Access Control Defaults
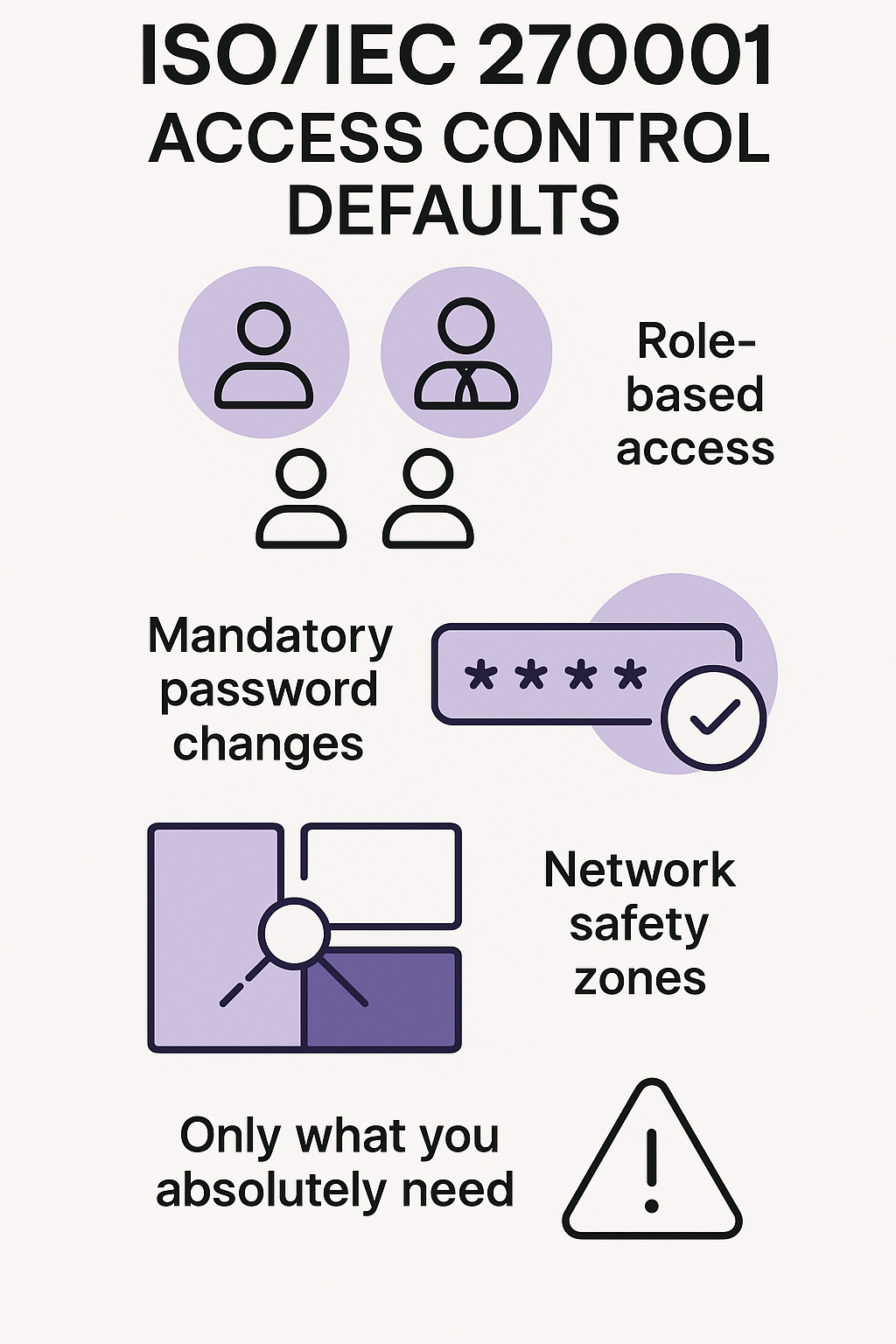
Getting access control right is like building a house – start with solid foundations or everything else falls apart. ISO 27001 keeps it simple: give people only what they absolutely need. No extras, no maybes. We learned this lesson the hard way when a junior admin with too much access accidentally wiped a production database.[2]
Students in our security courses always groan about strict permissions until they see what happens without them. ISO’s rules keep development stuff away from production (where it could really mess things up), and test environments can’t touch either one. Here’s what locks in automatically:
- Access based on job roles only
- Password changes you can’t skip
- Networks split into safety zones
OWASP ASVS Authentication Defaults
Setting up login security shouldn’t feel like rocket science, but plenty of teams still get it wrong. OWASP ASVS takes away the guesswork. From day one, it demands real passwords – none of that “password123” nonsense. Our bootcamp students often laugh when they learn about the passwords they used to think were “strong enough.”
The rules hit hard from the start:
- Passwords need uppercase, lowercase, numbers, and symbols
- MFA kicks in automatically for anything important
- Default credentials must change before first login
- Password storage uses modern hashing (no plain text allowed)
Every week we see another company in the news, breached because somebody left the default admin password unchanged. ASVS prevents these common oversights by design. One of our clients discovered their old system stored passwords in plain text – they couldn’t switch to ASVS standards fast enough after that wake-up call. The framework treats authentication like a foundation, not decoration you add later when you remember.
Security Benefits of Framework Secure Defaults
Nobody wants to be the person who forgot to lock the door. That’s exactly why these frameworks matter – they handle the basics so humans don’t have to remember everything.
During penetration testing exercises, our students consistently find fewer holes in systems using proper defaults, showing the clear benefits of a secure default posture. The difference shows up immediately in vulnerability scans.
Security teams sleep better knowing their systems start life with solid protection. Even if someone misses a step during setup or maintenance, the core security stays intact. Compliance folks love it too – makes their job way easier when they can point to standard configurations that match up with what auditors expect to see.
Trust comes from knowing you’ve covered the basics. Users feel better working with systems that don’t need constant babysitting to stay secure. It’s like having a car with airbags and anti-lock brakes built in – you might never need them, but you’re glad they’re there.
Practical Examples of Secure Default Settings in Frameworks
Credit: Code with Mark
Network defense isn’t rocket science. Most modern frameworks have preset security features that don’t need much fiddling – and that’s exactly how it should be. Here’s what secure defaults look like in action:
- Network and Protocol Security: Picture a house with all its doors locked. That’s how networks start – every port stays closed until someone deliberately opens it. No more Telnet (seriously, who still uses that?), no FTP. SSH’s the only way in, as it should be.
- Authentication and Credential Management: Gone are the days when “password123” cut it. These days, frameworks push back – they want multi-factor auth, they demand strong passwords (minimum 12 characters, special symbols, the works), and they’ll make users change temporary passwords right away. No exceptions.
- Application and Infrastructure Hardening: Our approach to firewalls is simple – block everything first, then open only what’s needed. Those WebDAV and TRACE methods? They’re disabled by default unless there’s a really good reason. Most web apps don’t need them anyway.
- Data Protection: Everything gets encrypted now – whether it’s sitting in storage or moving across networks. And those pesky .git folders that used to leak secrets? They’re automatically blocked from public view. Smart frameworks don’t just suggest these settings anymore – they enforce them from the start.
Frameworks and Guidelines Supporting Secure Defaults
The idea of “secure by default” isn’t new, but more people are paying attention now. Big guides and rulebooks remind us why it matters. OWASP says strong default settings are one of the first steps to safer systems. NIST gives clear instructions on implementing fail-safe defaults the moment a system starts.
The ISO/IEC 27001 standard makes sure access stays limited and controlled from the very beginning. Many company rules also say the same: start with secure settings for both apps and infrastructure.
We’ve watched what happens when teams follow these rules. Their systems start out safe, stay safe longer, and pass audits without so much stress.
Conclusion
Good security starts before anyone even logs in. The best systems, like those shaped by NIST, CIS, and OWASP, show up ready to go. Services are locked, access is limited, and data is already safe. You don’t have to chase leaks later, because the holes are closed from the start.
Most trouble in security doesn’t come from hackers being clever. It comes from settings left wide open, like doors without locks. But when the defaults are strong, the team spends less time fixing fires and more time building what matters. Getting it right on day one saves a world of mess.
Join the Secure Coding Practices Bootcamp to ensure your team starts with security best practices baked in, no catch-ups later.
FAQ
What are default security settings, and how do they help achieve a secure by default approach in framework secure default settings?
Default security settings play a big role in keeping systems safe from the start. They support secure by default practices by limiting unnecessary access and reducing weak points. A framework secure default settings approach uses default configuration security to lower risks before threats can spread. By focusing on secure default posture, organizations avoid relying on last-minute fixes and instead begin from a safer place.
Why do default password risks and default credentials vulnerability matter in framework secure default settings?
Default password risks and default credentials vulnerability are often the first targets for attackers. If a framework secure default settings strategy ignores them, systems become easy to break into. Security misconfiguration combined with weak login controls can open doors attackers don’t need to work hard for. Addressing these weak spots with default account security and stronger default login security makes the system safer.
How does secure software defaults reduce default service permissions and improve default system hardening?
Secure software defaults mean cutting down risky features that are often left open. With framework secure default settings, weak default service permissions can be locked early, improving default system hardening across devices. Default protocol security and default access control ensure services don’t run with too much power. Secure device configuration also helps limit default security flaws before they cause larger problems.
Why are default firewall configuration, default network settings, and default firewall rules important in secure default network policies?
Default firewall configuration and default network settings shape how information moves in and out of systems. If not done right, they can leave big gaps in security. Framework secure default settings highlight secure default network policies where default firewall rules stop unsafe traffic. Pairing this with default network hardening and default secure protocols gives stronger defense without slowing down daily operations.
How do default encryption settings, default security policies, and default security compliance affect framework secure default settings?
Default encryption settings and clear default security policies give structure to a framework secure default settings plan. Together they guide default settings audit steps and support default security compliance checks. This reduces default security risks, keeps sensitive data safer, and shows that default security governance is taken seriously. Default setting guidelines and default security frameworks also help teams stay aligned.
What role do default security baseline and default configuration management play in preventing default software vulnerabilities?
A strong default security baseline provides the starting point for safety. When paired with default configuration management, it helps avoid default software vulnerabilities and keeps systems reliable. Framework secure default settings benefit when default security updates and default security patches are applied regularly. Adding default security testing makes sure the baseline is solid and security principles are being followed.
References
- https://en.wikipedia.org/wiki/Default_password
- https://en.wikipedia.org/wiki/ISO/IEC_27002

