The defaults that ship with new tech are like unlocked doors, waiting for someone to walk in. Security teams see this mess daily – admin passwords still set to “password123,” ports left wide open, and data practically sitting on the curb. We’ve watched hackers slip through these gaps for years, turning minor oversights into six-figure nightmares.
Most vendors still ship their gear ready to plug and play, not ready to defend. Basic hygiene means scrubbing these settings clean before anything touches the network. Smart teams catch these risks early, saving countless hours of incident response later. Want to know exactly what to look for? Keep reading.
Key Takeaways
- Default settings practically roll out the red carpet for hackers
- Setting security-first configs stops most headaches before they start
- Regular checks and teaching your team beats playing catch-up later
Entities with Insecure Default Settings and Their Risks

The bootcamp’s security team keeps running into the same problems – default settings that might as well be open invitations to trouble. MySQL and PostgreSQL databases ship with root accounts that anyone could access, which we spotted during last month’s training exercises.
One student actually found a production database completely exposed to the internet, and man, the look on their face when they realized how deep they could go into the network.
Cloud platforms aren’t doing anyone any favors either. The number of exposed S3 buckets we’ve found during training sessions is just embarrassing. Major cloud vendors often default to public access, leaving sensitive data exposed where it shouldn’t be.
Here’s what the team typically finds during assessments:
- Databases with default credentials just waiting to be found
- OS installations running unnecessary legacy services
- Network devices still using passwords from the stone age
- Cloud storage configured like a public bulletin board
Every single issue here comes from real assessments our students have run, and they contrast sharply with secure default configurations examples that vendors should be following instead.
Attributes of Secure Configuration Practices
Security folks get a familiar look in their eyes when someone mentions default settings. At the bootcamp, students learn this on day one: factory passwords are like leaving keys in the car. Nothing complicated about it – strong passwords and two-factor everywhere. Simple stuff that stops most attackers dead in their tracks.
What actually works in practice:
- Nuke those default passwords first thing
- Set up two-factor (even when people grumble)
- Get strict with file permissions
- Kill unused services
Nobody likes hearing about “least privilege” until they see what happens without it. The training team watched it play out last spring when a temp worker’s overpowered account got compromised. The whole system got locked up.
These days, our students map out exact permissions for each role, building on secure by default principles that make hardening second nature.
Some of the best solutions come from automation. Scripts catch those misconfigurations before they turn into problems, and the monitoring picks up when someone accidentally exposes something sensitive. Better than pulling all-nighters manually checking settings during a crisis.
Values of Avoiding Insecure Defaults for Security Posture
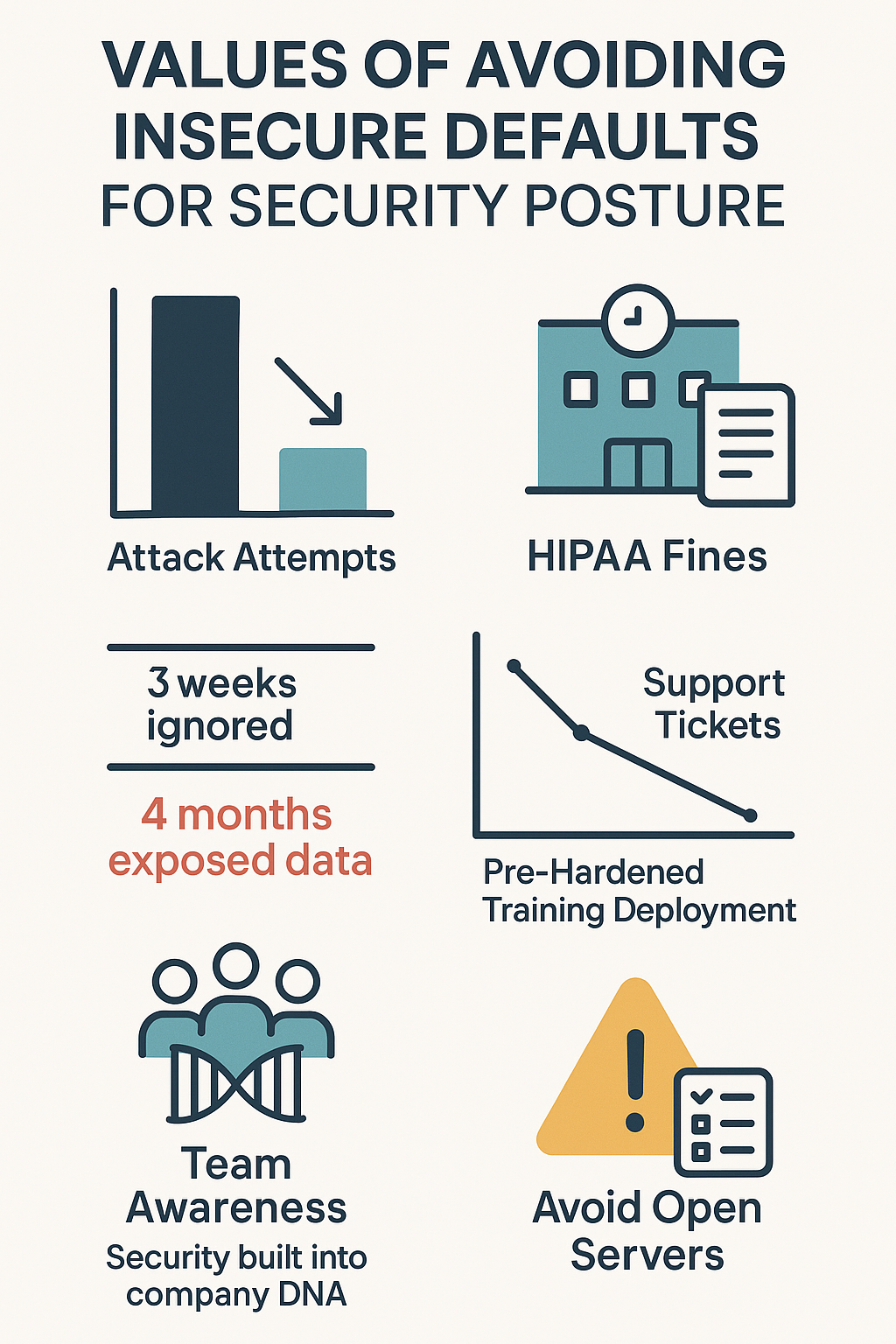
Basic math tells the story here – fewer ways means fewer breaches. Students who take default security seriously see attack attempts drop dramatically. Takes more work upfront, sure, but that beats explaining ransomware to the board.
A medical practice learned this lesson after ignoring three weeks of training recommendations about cloud security. Patient records sat exposed for almost four months. Those HIPAA fines would’ve covered a year of proper security training. Their story now serves as a wake-up call in week one of the bootcamp.
Setting up systems securely from the start just works better. Last quarter’s training deployment came pre-hardened – support tickets dropped through the floor, and new users picked it up faster than ever. That old argument about security making things harder? Doesn’t hold water when it’s done right.
Getting everyone to actually care about security takes work. The most successful graduates build this stuff into their company’s DNA – from new hire orientation through regular refreshers.
When teams understand why these settings matter, they catch the weird stuff before it becomes a problem. Nobody wants to be that person who left a server wide open because they didn’t check the config.[1]
Advanced Secure Deployment and Hardening Techniques
Credit: NameHero
Security consultants love their buzzwords, but at the bootcamp, students learn the brutal truth: start with everything off. Period. That mindset reflects secure defaults fail-safe design, where nothing is enabled until someone proves it’s needed.
Nothing gets turned on without someone proving they need it. Sure, deployment takes a bit longer, but that beats having your name in the headlines.
Basic security isn’t optional anymore – just ask last month’s class about their real-world audit. Every system needs encryption from day one, and those “we’ll fix it later” promises don’t fly. Student complaints about extra steps disappeared once they saw how many attacks their hardened systems blocked.
Some lessons from the trenches:
- Lock everything down by default
- Encrypt all traffic, always
- Firewall rules start at “deny all”
- No security shortcuts allowed
- Weekly config reviews
- Automated compliance tools
One of the junior devs in Tuesday’s class caught something odd, one of the contractors was still running their setup on factory settings. The monitoring caught it fast, but older setups might’ve missed it completely. That’s exactly why proper hardening matters.
Getting companies to take security seriously used to be rough. These days? Show them yesterday’s breach headlines. Now they’re finding weird configs before the instructors do.
Securing Systems by Avoiding Insecure Default Settings

The bootcamp’s incident response team has seen enough default-setting disasters to fill a book. Every week, students learn from real breaches where basic hardening would’ve stopped the attack cold. Those vendor-supplied passwords and unnecessary services? They’re basically welcome mats for hackers.
Most attacks start with the easy stuff – default credentials, open ports, and misconfigured permissions. The training program hammers this home with hands-on examples. Students spend their first week just finding and fixing default settings in test environments. It’s amazing how many security holes they discover.
Security isn’t about fancy tools – it’s about doing the basics right. Last week’s advanced class found three exposed databases using nothing but default searches. The company had great firewalls and expensive monitoring, but they’d skipped the fundamentals. That’s exactly why the course starts with hardening basics.
Real security starts with questioning every default setting. The best graduates make hardening part of their routine, checking configs as naturally as they check their code. Because at the end of the day, attackers don’t need sophisticated exploits when default passwords work just fine.[2]
Practical Advice for Avoiding Insecure Default Settings
Security doesn’t need fancy tricks – just consistent habits that work. Our team’s seen enough breaches to know: kill those default passwords day one, shut off anything you’re not using, and make everyone use two-factor auth. No exceptions.
Last month, a client almost got hit with ransomware because their backup system still had factory passwords. One afternoon of basic fixes saved them millions. Sometimes the boring stuff matters most. If you want to sharpen these habits, join the Secure Coding Bootcamp.
FAQ
What are insecure defaults and why do default credentials or a default admin password create a default password risk?
Insecure defaults often show up as default credentials or a default admin password left in place. These create a default password risk since attackers usually try them first. Once inside, they can change default system settings, explore default network configuration, or even break into insecure IoT device settings. Avoiding insecure defaults reduces your attack surface and helps keep your setup secure by default.
How does a security misconfiguration happen with default configuration vulnerabilities like default security settings or default device settings?
A security misconfiguration often comes from default configuration vulnerabilities, like leaving default security settings or default device settings unchanged. These insecure system configurations may also include default Wi-Fi settings security or default firewall settings. Each weak spot adds to the attack surface. Fixing them quickly helps create secure by default operations and makes attack surface reduction more realistic.
Why do disabled security features or insecure cookie settings matter with default HTTPS settings and default authentication settings?
Disabled security features or insecure cookie settings leave open doors for attackers. If you keep default HTTPS settings or default authentication settings, you risk insecure software defaults. Weak points like default session settings or default password reuse widen exposure. Checking for insecure default services or careless default logging settings helps close gaps and builds trust in your system.
How can default cloud configuration or default API keys create problems like default encryption settings or default access control flaws?
Default cloud configuration sometimes leaves default API keys, default encryption settings, or weak default access control in place. These default configuration vulnerabilities open the door for misuse. Attackers can also abuse default database settings, insecure software install defaults, or default cloud storage settings. To stay secure by default, update the default security policy, patch default system patches, and tighten default IAM policies.
What risks come with default admin accounts, default service accounts, or default user roles in insecure default services?
Default admin accounts, default service accounts, or default user roles often stay enabled after setup. These insecure default services allow attackers to bypass default security hardening or default password complexity checks. Even worse, default multi-factor authentication or default user authentication may not be turned on. Closing default access permissions, default security groups, and default registry settings lowers the risk of attack.
Why should default firewall rules, default VPN configuration, or default remote access be changed along with default SSH settings?
Default firewall rules, default VPN configuration, or default remote access often open paths attackers already know. Leaving default SSH settings, default network segmentation, or default open ports in place makes systems easy targets. Updating default content security policy, default cookie flags, and default system monitoring settings ensures your defenses are not stuck with insecure defaults that invite trouble.
References
- https://www.hipaajournal.com/healthcare-data-breach-statistics/
- https://en.wikipedia.org/wiki/Application_permissions

