
The world of secure development turns on two critical things – where the bad guys might get in, and how they’ll do it. Every developer knows this truth: attack surfaces span the entire application like an open field, while attack vectors cut straight paths through weak spots.
We’ve watched countless teams stumble by mixing up these basics. Years of running security bootcamps showed that understanding this difference isn’t just theory – it’s the foundation for building applications that actually keep attackers out.[1]
Key Takeaways
- The attack surface means all the ways someone could break in; attack vectors are the actual paths hackers take.
- More entry points mean bigger risks – pretty straightforward stuff really.
- Good security needs both – closing off access points and watching for signs of attacks.
Attack Surface: Defining All Potential Entry Points in Cybersecurity

Nobody likes finding holes in their code, but that’s exactly what keeps systems safe. Teaching secure development means showing developers where their blind spots hide – and there’s always more than they expect.[2]
System entry points pop up everywhere, kinda like weeds in a garden. Through years of training developers, we’ve watched them discover vulnerabilities in the strangest places. Sometimes it’s the obvious stuff, like that one dev who left their AWS keys in a public GitHub repo (yikes). Other times it’s trickier, like third-party dependencies nobody’s thought about since installation.
Common weak spots we keep finding:
- Default admin passwords on production servers
- Unmonitored S3 buckets
- Debug endpoints left enabled
- Ancient WordPress plugins
- Shadow IT systems
Last week’s pen testing class found something wild – a client’s test environment had been quietly syncing with production data for months. Nobody noticed until our students started poking around. These things happen more than anyone wants to admit.
Security’s a moving target, sure, but that’s no excuse for sloppy habits. Regular audits might feel like busy work, but they’ve saved more projects than we can count, one of the big benefits of attack surface reduction that most devs only appreciate after a close call. Perfect security’s probably a pipe dream, but making attackers work for it? That’s just good business.
Attack Vector: Explaining Specific Methods of Cyber Exploitation
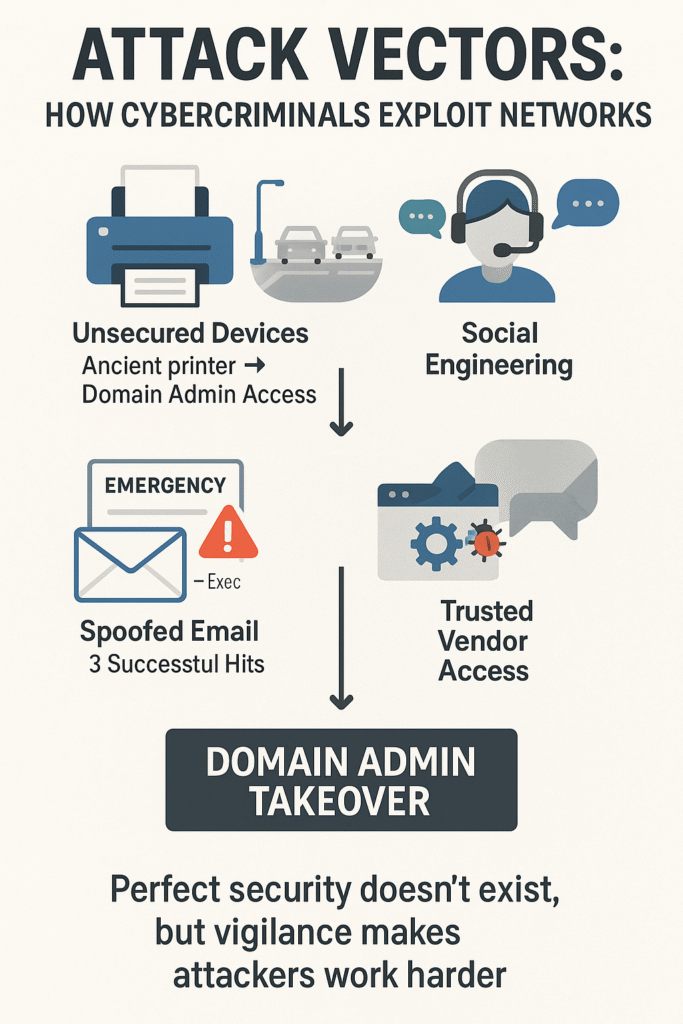
Finding new ways in – that’s what keeps security folks up at night. Teaching advanced security at bootcamp shows just how creative attackers get. Sometimes it’s not the fancy zero-day that gets you – it’s the cleaning crew propping open a secure door.
Last month’s pen testing class turned up some wild stuff. One team got domain admin access through an ancient network printer nobody remembered to secure. Classic stuff. Then there was that time during a red team exercise when dropping USB drives in the parking lot scored three hits before anyone raised an alarm.
Favorite tricks we keep seeing:
- “Emergency” emails from spoofed exec accounts
- Infected software updates (looking like the real thing)
- Sweet-talking the IT help desk
- Riding in through trusted vendor connections
Book learning’s fine, but nothing beats hands-on experience. That’s why our advanced modules throw students into the deep end. When ransomware encrypts production servers at midnight, nobody’s reaching for their textbook.
Eyes open, always watching – that’s what works. Sounds paranoid? Maybe. But after seeing dozens of networks get owned through the dumbest vectors, paranoid starts looking pretty smart. Perfect security doesn’t exist, but we can surely make the bad guys earn their paycheck.
Comparative Analysis: Contrasting Attack Surface and Attack Vector in Cybersecurity
Credit: TFiR
Most devs hit this wall pretty hard – telling attack surfaces from vectors. Seems like every bootcamp class starts with blank stares when we bring it up.
Picture a medieval castle (yeah, we use this example a lot). The attack surface covers every inch of those walls, every tower, and even the servants’ entrance nobody remembers. But the attack vector? That’s the specific crack in the wall where the enemy actually breaks through.
Key differences we’ve mapped out:
- Attack surface = your entire defensive line
- Attack vector = where the bad guys choose to strike
- Surface stays mostly stable
- Vectors change like the weather
Funny thing about risk – size doesn’t always matter. Some of our biggest client breaches came through tiny holes nobody noticed, while massive systems with tons of exposure stayed locked tight. Good defense beats big walls every time.
Two different defense strategies we teach:
- Surface work, like attack surface reduction techniques
- Vector blocking, which means watching for weird behavior and responding fast.
Real talk: yesterday’s training group caught this immediately when we showed them that it had been compromised. Sure, the whole CI/CD pipeline was exposed, but the attacker only needed that one unpatched plugin to get in. Makes the difference crystal clear, doesn’t it?
Dynamic Security Management: Integrating Attack Surface and Vector for Robust Defense

After running countless bootcamp sessions, one thing’s crystal clear – you can’t play favorites between attack surface and vector protection. They’re like two guards watching different doors.
Our scanning tools catch the obvious stuff, but strong defense needs more, adopting solid attack surface monitoring strategies keeps developers ahead of the sneaky blind spots that creep in over time. The bootcamp’s best practices include:
- Daily asset checks
- Weekly vulnerability scans
- Monthly security reviews
Strange thing about attack surfaces – they grow sneakier than most people think. One dev adds a test server, another opens a port, and suddenly there’s a mess. We’ve seen it happen dozens of times in our training scenarios.
Bad actors don’t sleep, and neither should security. These folks cook up new tricks faster than a short order chef. Last month’s security patch might as well be ancient history by now.
Smart resource allocation makes all the difference. Based on what we’ve seen in the field, organizations should:
- Lock down unnecessary access points first
- Build detection systems second
- Train everyone, always
Nothing beats hands-on experience for getting this stuff right. That’s why every bootcamp module includes real-world examples – they stick better than theory ever could.
Conclusion
Look, defense isn’t rocket science, it’s harder. After training hundreds of developers, we’ve learned that understanding the where (attack surface) and how (attack vectors) makes all the difference. Keep systems tight, patch the holes, and watch for the weird stuff.
Want better security? Start by knowing what you’re protecting. Map those entry points, train your people, and stay alert. Because in our experience, the best defense isn’t just about tools, it’s about making attackers work so hard they give up and move on.
Join our Secure Coding Bootcamp and start building defenses that actually hold.
FAQ
What is the attack surface vs attack vector difference in simple terms?
The attack surface is all the system attack points or exposure points that hackers might target, while an attack vector is the intrusion method or exploit technique they use to get inside. Think of the attack surface as every possible door or window, and the attack vector as the exact way they open one. Both matter for cybersecurity vulnerabilities, since knowing the attack surface helps reduce entry points, while knowing the attack vector explains the exploit method behind a security breach.
How do system vulnerabilities and cyber attack methods connect to attack vectors?
Attack vectors are tied to system vulnerabilities because they show the path hackers take. A phishing attack or social engineering vector tricks people, while a malware attack or ransomware attack sneaks in through a compromised device. Cyber attack methods often exploit software vulnerability or network vulnerabilities to break defenses. Each attack path shows a different hacking vector, like SQL injection or credential theft, making vulnerability management and attack vector prevention key to stronger cyber defense.
Why is attack surface reduction important for network security?
Attack surface reduction lowers cyber risk exposure by cutting down unnecessary penetration points and entry point exposure. A large digital attack surface, including network ports, cloud attack surface, or third-party vulnerabilities, makes intrusion easier. With attack surface assessment, attack surface scanning, and attack surface mapping, you see security loopholes before attackers do. Strong security controls, endpoint security, and attack surface management keep the security perimeter tighter, so cyber threat actors have fewer system attack points to target.
How can penetration testing and attack vector analysis improve cyber defense?
Penetration testing helps reveal attack surface intelligence by simulating cyberattack pathways and exploit methods. Attack vector analysis digs into threat vectors, showing attack vector examples like malware delivery, phishing vector, or social engineering vector. These tests expose security attack vectors and intrusion vector risks, giving insight into attack vector tactics and threat actor tactics. By studying exploit technique patterns and attack vector strategies, teams can do better vulnerability management, improve attack vector mitigation, and close dangerous security attack points.
What role do endpoint vulnerabilities and software attack vectors play in a security breach?
Endpoint vulnerabilities, like unpatched devices or compromised device risks, often serve as hacker entry point options. A software attack vector, such as vulnerability exploitation in outdated apps, can be used with malware vector or phishing attack delivery to trigger a security breach. Cyberattack vector threats like ransomware attack or credential theft ride these system attack surface weaknesses. When exposure points go unchecked, threat pathways multiply, raising attack vector risks. Attack vector detection and attack vector tools help stop exploit methods before they spread.
References
- https://en.wikipedia.org/wiki/Attack_vector
- https://www.hipaajournal.com/more-than-one-third-data-breaches-third-party-compromises/

