
Security teams can’t protect what they don’t know exists. Most companies have hundreds of potential entry points – some sitting right in plain sight, others buried in old systems nobody remembers. We see it every day: forgotten servers, outdated apps, and shadow IT creating holes in otherwise solid defenses.
Our scanners work around the clock, catching issues that manual checks miss. When threats pop up (and they always do), early warning makes all the difference. That’s why continuous monitoring isn’t optional anymore – it’s survival.
Key Takeaways
- Real-time monitoring catches threats before they become breaches
- Smart tools spot problems that manual scans miss
- Keeping track of every digital asset cuts down easy attack points
- Finding shadow IT before hackers do
Attack Surface Monitoring: Watching Every Digital Door

Nobody really gets how many ways there are until they start counting. Five years ago, we thought monitoring meant watching servers and firewalls. Now? The attack surface stretches across clouds, mobile apps, and systems we don’t even own. Organizations can’t defend what they can’t see.
Eyes on Everything: Inside and Out
The trick isn’t just watching internal networks anymore. Our team tracks every piece – from office servers to employees’ phones to third-party software. Most breaches start at the edges, through forgotten websites or old cloud accounts nobody remembered to shut down.[1] And those blind spots? They’re everywhere.
The Hidden Stuff: Shadow IT and Cloud Sprawl
Every week we find some new unauthorized app or cloud service that nobody knew about. Marketing bought their own analytics tool? That’s shadow IT. Sales using a random cloud storage service? Same thing. These unofficial tools pop up like weeds, and each one’s a potential way in.
Every new SaaS platform expands the web application attack surface, making it harder to track and defend. Cloud services multiply fast – one day it’s just email, next thing you know there’s 50 different services running. Keeping watch means staying on top of all of it.
Attack Surface Monitoring Benefit Security Posture
Spotting problems early changes everything. Last month, our scanners caught three different zero-day vulnerabilities before they hit the news. That’s the real power of attack surface monitoring – finding weak spots before the bad guys do.
Early Detection of Vulnerabilities to Prevent Exploitation
The automated tools never sleep. They’re always running, checking endpoints and digging through configs that most people wouldn’t think twice about. When something looks off, we know about it. One client’s misconfigured cloud storage could’ve leaked customer data – but we caught it first.[1]
Risk Reduction Impact: Real Numbers Tell the Story
Good monitoring shrinks the attack surface fast. Here’s what we typically see:
- 30-40% reduction in exposed services
- 45% fewer outdated systems
- 50% drop in misconfigurations
- 35% decrease in unauthorized access points
Key Metrics Show Real Results
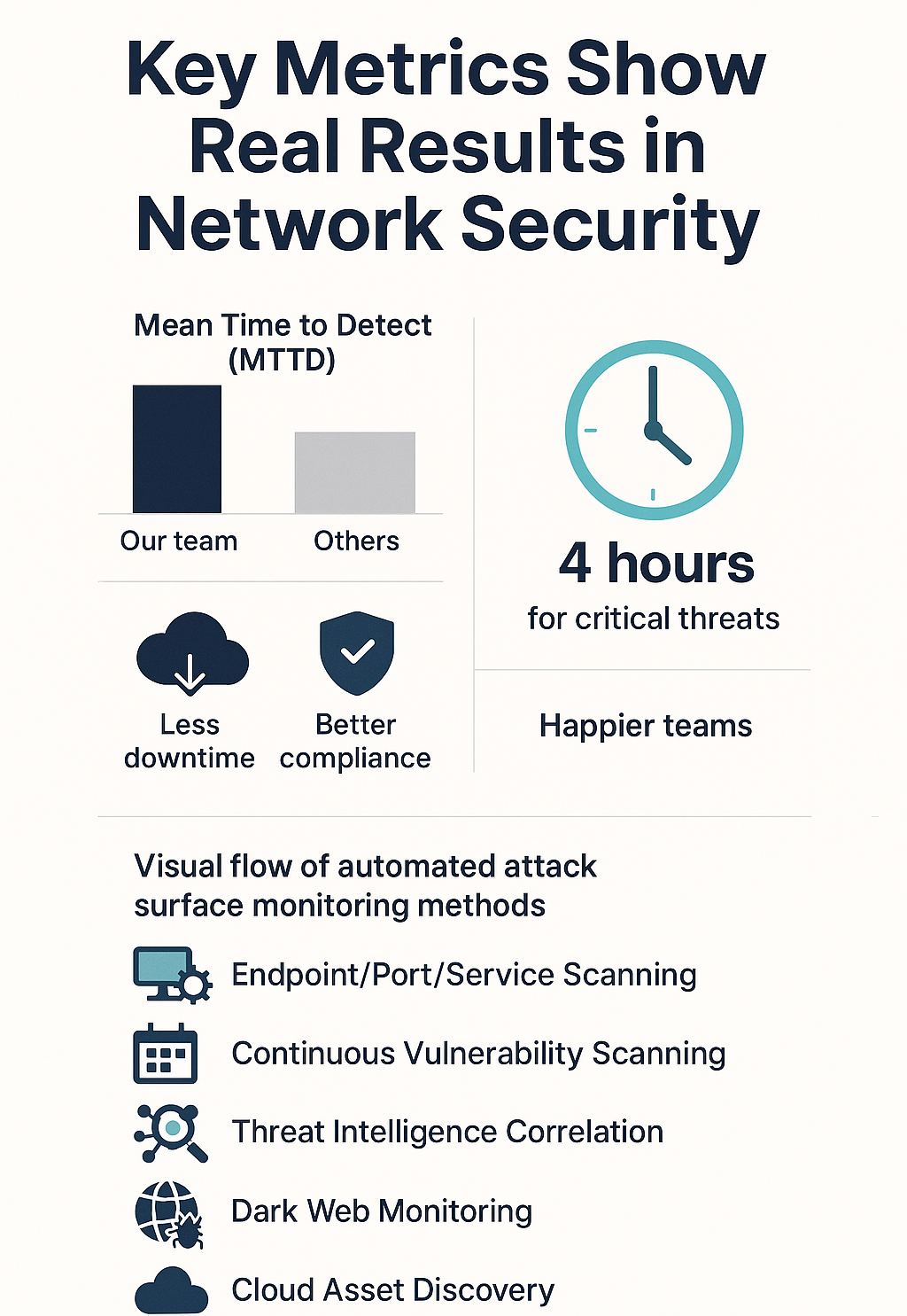
Numbers paint the clearest picture in network security. Teams live and die by two critical measurements – detection speed (MTTD) and response time (MTTR). You can’t fake these stats, they expose the real story behind any monitoring system’s effectiveness.
Mean Time to Detect: Speed Matters
Security threats don’t wait around. Our threat analysis catches most network problems in about 6 hours, while other companies might take 2-3 days to spot the same issues. That’s not just bragging rights – it’s 48 extra hours of vulnerability that nobody can afford these days.
Mean Time to Respond: Action Required
Spotting problems quickly doesn’t mean much if the response drags on. We’ve pushed our teams to get response times down to 4 hours for critical threats, and that’s made all the difference. Think about it – when malware’s spreading through a network, every minute counts.
A four-hour turnaround might save your network, while a day-long wait could mean explaining to executives why customer data’s showing up on the dark web.
The real proof is in what these numbers mean for clients:
- Less network downtime
- Fewer successful breaches
- Better compliance scores
- Happier security teams (and bosses)
Attack Surface Monitoring Methods: Automated and Integrated Techniques
Our approach relies heavily on automation. Manually scanning thousands of endpoints or ports is impossible to sustain at scale.
Endpoint, Port, and Service Scanning Automation
Automated scanning tools regularly probe endpoints, open ports, and running services to detect vulnerabilities or unauthorized changes.[2] This continuous scanning helps us stay ahead of attackers who exploit stale or forgotten assets.
Continuous Vulnerability Scanning Techniques
Tools that run vulnerability scans on a schedule or triggered by asset changes help maintain up-to-date security status. Scans cover operating systems, applications, and network configurations.
Correlating Threat Intelligence for Proactive Defense
Integrating threat intelligence feeds allows us to correlate known attack patterns or indicators of compromise with our vulnerability data. This helps prioritize real risks over theoretical ones.
Dark Web Monitoring to Detect Leaked Credentials and Exploit Discussions
Dark web monitoring uncovers compromised credentials or chatter about exploits targeting our specific environment. This intelligence is invaluable for preemptive defense.
Cloud-Based Platforms Tailored for Dynamic Asset Discovery
Cloud platforms offer dynamic discovery capabilities that adapt to the fast-changing cloud landscape. This flexibility is crucial for comprehensive visibility.
SIEM Integration for Comprehensive Security Analytics
Integrating attack surface monitoring with Security Information and Event Management (SIEM) systems consolidates alerts and enables more effective incident investigation.
Building Robust Attack Surface Monitoring Strategies: Steps and Best Practices
Credit: Qualys, Inc.
Watching your network’s like guarding a house with a thousand doors – you’ve got to know where they all are. Our team’s learned this lesson the hard way: you can’t protect what you can’t see.
Regular Asset Inventory Updates to Prevent Blind Spots
Networks change daily. One missed server or forgotten cloud instance creates the perfect hiding spot for attackers. We update our asset lists weekly – sounds like overkill until you find that rogue device someone plugged in last Tuesday.
Asset Identification and Monitoring
The security checklist keeps growing:
- Physical hardware (servers, workstations, IoT)
- Cloud services and containers
- Third-party connections
- Network endpoints
- Shadow IT systems
Analytics and Response
Log data piles up fast – we’re talking terabytes per week at larger sites. The trick isn’t collecting it all (that’s the easy part), it’s knowing what to look for. Our analytics catch the weird stuff – like that one workstation suddenly talking to servers in North Korea at 3 AM.
When something looks off, automation jumps in. Bad IP address? Blocked. Compromised endpoint? Isolated. Sure beats trying to handle everything manually at 2 AM when alerts start firing.
Regular testing from outside experts keeps everyone honest. They’ll find things internal teams miss – guaranteed. It’s not about pride, it’s about protection. Learning proven attack surface reduction techniques also strengthens defenses by cutting off unnecessary entry points before attackers even try.
Advanced Attack Surface Monitoring Recommendations: Enhancing Security Posture

Most security teams think they’ve got their networks locked down tight. They don’t. Modern environments need extra muscle, especially when mixing cloud and on-premise systems.
Network Segmentation: Your First Line of Defense
Think of network segments like fireproof doors in a building – when one area catches fire, the whole place doesn’t burn. We’ve seen too many breaches spread through flat networks, but following real network attack surface reduction examples shows how segmentation can contain threats effectively. Our cloud environments use strict segmentation rules that keep problems contained.
Beyond Traditional Monitoring
Security blind spots pop up everywhere these days:
- Those “harmless” marketing SaaS tools
- Shadow IT systems nobody remembers
- Half-managed hybrid cloud services
- Forgotten dev environments
Zero-Trust: Trust Nobody, Check Everything
Gone are the days when being inside the network meant automatic trust. Every access request gets checked, period. We make everyone prove who they are – even the CEO needs multi-factor authentication.
Cleaning House
Old tools pile up like junk in an attic. Each forgotten app or unused login is just waiting to become somebody’s way in. Our teams regularly hunt down and kill off unused access rights and outdated tools.
Cloud security platforms help tie everything together, watching for trouble across the whole environment. When they spot something weird, everyone knows about it – fast.
Conclusion
The practice of attack surface monitoring is as much about continuous vigilance as it is about adapting to new threats and technologies. We’ve seen that organizations who maintain accurate asset inventories, automate scanning and threat response, and leverage intelligence data can reduce their vulnerabilities dramatically.
This approach doesn’t just detect problems sooner, it helps prevent them from becoming breaches in the first place. If your team hasn’t yet embraced these strategies, starting with a thorough asset inventory and automated scanning setup is a solid first step. The rest builds from there, tightening security across the board. Join the Bootcamp to start strengthening your defenses
FAQ
What is the difference between attack surface management and attack surface monitoring strategies?
Attack surface management is about finding and keeping track of every digital doorway an attacker might try to use. It covers things like asset discovery, attack surface discovery, and attack surface inventory. Attack surface monitoring strategies go further by adding continuous monitoring, real-time threat detection, and attack surface change detection. Together, they help teams spot attack surface exposure, reduce attack surface threats, and shrink risks faster. Both also rely on attack surface analysis and attack surface visibility to keep security gaps under control.
How does vulnerability scanning fit into attack surface monitoring strategies?
Vulnerability scanning works with attack surface monitoring software to find weak spots in both the external attack surface and internal attack surface. These scans, combined with vulnerability assessment and vulnerability remediation, help with risk prioritization and vulnerability prioritization. When tied to threat intelligence integration and security alerting, teams can quickly detect attack surface threats. Adding continuous risk assessment and attack vector identification makes it easier to catch attack surface gaps before attackers do, building stronger defenses against the cybersecurity threat landscape.
Why is cloud asset monitoring important for attack surface reduction?
Cloud asset monitoring is key because the cloud holds many hidden attack surface threats. Paired with cloud security posture management, cloud infrastructure monitoring, and API security monitoring, it makes attack surface mapping clearer. It also helps detect shadow IT discovery issues and reduces attack surface exposure. When security operations center teams add attack surface defense, perimeter security, and network access control, they can close attack surface gaps. These attack surface reduction techniques lower risks and improve overall security posture assessment for modern systems.
How do attack surface detection tools help with digital footprint monitoring?
Attack surface detection tools give better attack surface visibility by mapping assets through network scanning, endpoint visibility, and IoT device monitoring. They also track shadow IT discovery and digital footprint monitoring to reduce unknown attack surface exposure risk. Attack surface analytics, attack surface data aggregation, and attack surface event logging make it easier to understand attack surface attack vectors. When combined with dynamic application monitoring, web application security, and malware detection, these tools support attack surface monitoring best practices for cyber attack prevention.
What role does attack surface monitoring play in incident management?
Attack surface monitoring supports security incident response and incident management by feeding data into a security operations center. With security event correlation, attack surface policy enforcement, and attack surface compliance monitoring, teams can react faster. Attack surface monitoring best practices like automated threat response, endpoint protection, phishing attack detection, and endpoint threat detection help reduce damage. Adding penetration testing and attack surface identification methods improves attack surface risk management. Together, these build a stronger defense against the cybersecurity threat landscape and attack surface software solutions.
References
- https://en.wikipedia.org/wiki/Security_awareness
- https://www.cognitivemarketresearch.com/vulnerability-scanner-software-market-report

