
Network security boils down to something pretty straightforward – there’s a shrinking game happening between defenders and attackers. We’ve seen too many companies leave their doors wide open, and it’s not just about fancy tools.
Our training sessions show that basic stuff, like knowing what machines you’ve got and who can touch them, stops most attacks cold. Working with dev teams has taught us that good security isn’t rocket science – it’s about watching those entry points and closing them tight.
Key Takeaway
- Good firewalls stop most of the junk hitting networks
- Getting rid of old junk makes everything safer
- Watching who gets in (and keeping that list small) blocks most attacks
Network Firewall Exposure Reduction: Blocking Unauthorized Inbound Traffic
Basic security still works best. The fancy zero-day exploits make headlines, but most attacks just poke around looking for open ports. Every time students run their first network scan in our lab, they’re shocked at how much random traffic hits their test systems.
Setting up firewalls right isn’t glamorous work, but it’s one of the most effective attack surface reduction techniques companies can apply to block unauthorized inbound traffic. Our students learn pretty quickly that blocking everything breaks stuff, and allowing everything defeats the point.
Last month, a manufacturing client came to us after getting hit. Their network was wide open to “make things easier.” Three days of firewall rules later, attack attempts dropped off a cliff.
But firewalls can’t catch everything. Bad stuff hides in encrypted traffic, and insider threats just walk right through. That’s why we teach defense in depth – no single tool’s gonna save you.
VPN Gateway Access Control: Limiting External Access to Authenticated Users

VPNs seem simple until they’re not. Students roll their eyes when we spend two whole weeks on VPN setup, then they see what happens when it’s done wrong. A finance company hired us after their “quick” VPN deployment left their entire network exposed.[1]
The details matter with VPN security. Weak passwords, split tunneling left on, missing logs – we’ve seen every mistake possible. Sometimes twice. Our advanced class digs into the nitty-gritty: strong encryption (none of that outdated stuff), multi-factor auth (because passwords aren’t enough anymore), and audit logs that actually tell you what happened. Skip any of these, and you might as well leave the front door open.
Legacy Servers Decommissioning: Removing Outdated Systems from Public Networks
Old servers are like that broken-down car in someone’s front yard – everyone sees the problem, but nobody wants to deal with it. Working with dozens of companies through our bootcamp, these legacy systems keep showing up as the weak link. Half our incident response cases trace back to some forgotten server running Windows 2008 or an ancient Linux build.
Getting rid of old servers isn’t as simple as pulling plugs. Here’s what usually needs to happen:
- Track down all the old systems (harder than it sounds)
- Figure out what still depends on them
- Move critical stuff to newer platforms
- Deal with the inevitable “but we need that” arguments
When companies can’t kill old servers right away, we teach them to lock those systems down tight. Network segmentation helps – stick them behind extra firewalls, limit their connections, monitor everything.
One client saw the clear benefits of attack surface reduction when they cut their exposure by 60% just by identifying and containing legacy systems they couldn’t immediately remove.
API Endpoints Hardening: Disabling Unused Paths and Enforcing Authentication
APIs are everywhere now, and most devs don’t realize they’re leaving doors wide open. Our advanced security course spends three full days just on API attack surface management, that’s how serious this gets. Every week someone comes to class with horror stories about finding exposed endpoints nobody knew existed.
Real-world API security comes down to basics:
- Kill unused endpoints (they’re just waiting to be found)
- Lock down everything with proper auth
- Rate limit requests to stop automated attacks
- Watch the logs like a hawk
The teams we work with usually push back on API lockdown – until we show them how exposed they are. One quick scan typically finds dozens of forgotten endpoints. Adding API gateways and proper access controls isn’t exciting work, but it stops most attacks cold. When unusual traffic patterns pop up, those monitoring tools we helped set up catch problems fast.
Default Ports Minimization: Closing Unnecessary Network Ports
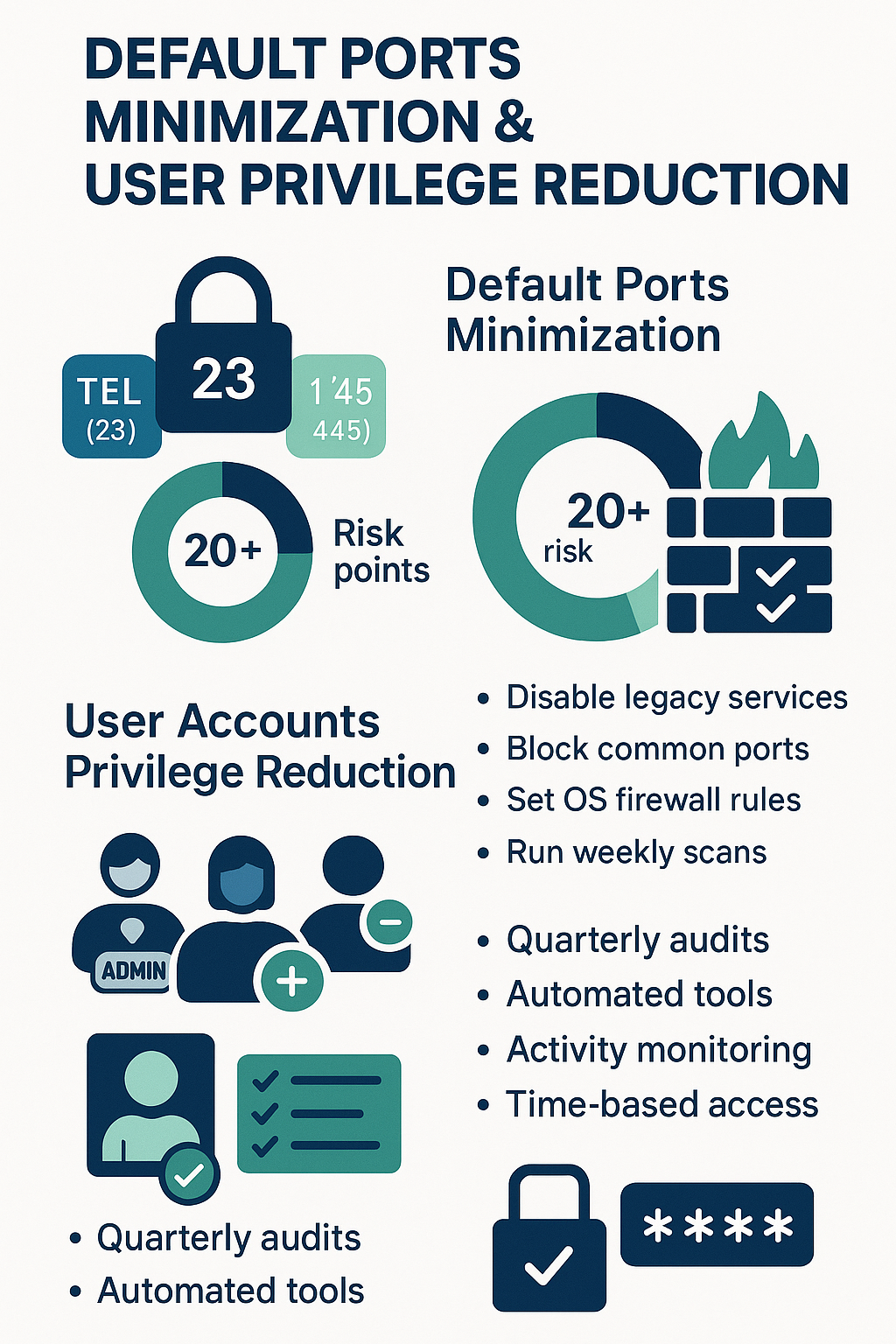
Network security starts with shutting the right doors. Open ports create pathways straight into a system, kind of like leaving windows unlocked in a house at night. In our bootcamp sessions, students learn that default ports like Telnet (23) and FTP (21) might as well be welcome signs for attackers.
The first step any developer takes is running a thorough port scan to spot what’s open. We’ve seen countless systems with 20+ unnecessary ports running – that’s 20 potential break-in points. Sometimes it’s as simple as:
- Disabling legacy services
- Blocking common targets (ports 21-23, 135, 445)
- Setting strict firewall rules at OS level
- Running regular automated port audits
Port security isn’t a one-and-done deal. Applications love to sneak in new open ports during updates, and developers don’t always catch them. Third-party software’s even worse about this. Our team runs weekly port scans, and there’s always something new trying to punch through the firewall.
Most attacks start with port scanning – that’s how they find the weak spots. By keeping only essential services running (and documenting why each one’s needed), developers make attackers’ jobs a lot harder. Regular maintenance checks help catch anything that slips through.
User Accounts Privilege Reduction: Implementing Least Privilege and Removing Stale Accounts
Walking into most companies, you’ll find a digital graveyard of user accounts. Former employees, contractors, service accounts – all sitting there with way too much access. Our bootcamp students are often shocked when they run their first privilege audit and find hundreds of dormant accounts still holding admin rights.
The principle of least privilege sounds simple enough: give people only what they need to do their jobs. But in practice, it’s tricky. Developers might need admin access during deployment but not day-to-day. Here’s what tends to work best:
- Regular account audits (at least quarterly)
- Automated privilege management tools
- Activity monitoring for suspicious access patterns
- Time-based access controls for temporary privileges
Security teams need to get creative with enforcement. We’ve seen great results using automation to flag accounts that haven’t logged in for 30+ days. The trickier part’s convincing managers that their teams don’t need permanent admin access.[2]
Multi-factor authentication’s become non-negotiable these days. Combine that with strict password rules and you’ve got a solid foundation. Our students learn to script these checks – it’s amazing how many privilege issues they catch in their first scan. The key’s making it a routine, not a one-time cleanup. Those forgotten accounts just keep coming back like weeds if you don’t stay on top of them.
Cloud Instances Visibility: Continuous Scanning for Exposed Services

Cloud environments move fast – too fast for manual tracking. One developer spins up a test instance, forgets about it, and suddenly there’s an exposed database facing the internet. Security teams see this pattern repeating across every organization they work with.
Our bootcamp students learn cloud security the hard way. We set up deliberately misconfigured environments and watch them discover:
- Untagged resources running wild
- Development instances left public
- Storage buckets with loose permissions
- Forgotten test environments eating budget
Continuous scanning isn’t just about finding problems – it’s about staying ahead of them. The tools keep getting better at spotting issues before they turn into incidents. Teams need real-time visibility into their cloud assets, especially when developers are pushing changes multiple times per day.
Compliance checks help, but they’re just part of the puzzle. We’ve learned to integrate cloud scanning with incident response plans. When something looks off, the system flags it immediately. Students practice responding to these alerts, learning to tell the difference between a dev testing something new and an actual security issue.
The cloud moves too quickly for annual audits or manual checks. Security needs to move at the same speed as development, catching problems before they turn into breaches. That’s why our training focuses on automated, continuous monitoring – it’s the only way to keep up.
IDS/IPS Systems Proactive Defense: Detecting and Preventing Intrusion Attempts
Credit: Cyberconnect
Think of IDS/IPS systems as digital security cameras with built-in bouncers. They don’t just watch – they act. During our bootcamp sessions, students often struggle to grasp why firewalls aren’t enough on their own. That understanding usually clicks when they see their first real attack pattern.
Setting up effective intrusion detection requires strategic placement. Most networks need sensors in several spots:
- Between internet and internal networks
- Around critical database segments
- Near development environments
- Monitoring internal traffic flows
False positives drive security teams crazy. We’ve seen whole departments tune out alerts because their IDS kept crying wolf about normal traffic. The trick’s finding that sweet spot between catching genuine threats and avoiding alert fatigue.[2] Our students spend hours tweaking rules until they get it right.
Network behavior analysis makes all the difference. Modern IDS/IPS systems spot patterns humans might miss – like that one workstation suddenly trying to connect to every IP in the subnet. Teams need to know what normal traffic looks like before they can spot the weird stuff.
Getting these systems to play nice with development workflows takes practice. The bootcamp teaches students to adjust detection rules for continuous deployment environments. It’s a balancing act between security and not breaking the build pipeline. When it’s done right, IDS/IPS catches the bad stuff while letting legitimate traffic flow smoothly.
Practical Advice to Start Shrinking Your Network’s Attack Surface
A network’s attack surface looks like Swiss cheese without the right defenses. Think about it: every port, app, and endpoint is another spot hackers might slip through.
Here’s what works: Keep track of every device and service (yes, even Bob’s ancient printer), lock down access with multi-factor auth, patch those holes fast, watch for weird traffic patterns, and get the team trained up. Like fixing a leaky boat – plug one hole at a time, but keep checking for new ones.
Want to solidify your defenses and make sure those holes are truly sealed? Join our Bootcamp now to master the art of robust, up-to-date security practices.
FAQ
How does attack surface reduction help with network security and cyber attack prevention?
Attack surface reduction is about shrinking the number of doors an attacker can use. By cutting down open ports, unused services, and weak apps, you strengthen network security. This directly supports cyber attack prevention because fewer attack vectors remain. Add tools like endpoint security, firewall rules, and vulnerability assessment, and you can minimize attack vectors before they cause harm.
What role do asset inventory and patch management play in reducing the threat surface?
Asset inventory shows you everything connected to the network, servers, apps, laptops, even forgotten printers. Patch management makes sure those assets stay updated, closing holes attackers might find. Together, they shrink the threat surface, making both the external attack surface and internal attack surface harder to exploit.
How does access control and the least privilege principle improve network segmentation and micro-segmentation?
Access control means only the right people get in, while the least privilege principle keeps their permissions as low as possible. When combined with network segmentation and micro-segmentation, this limits where attackers can move. Even if they break into one system, lateral movement prevention stops them from spreading deeper.
Why are multi-factor authentication (MFA) and secure configuration important for zero trust security?
Multi-factor authentication (MFA) makes it harder for stolen passwords to work. Secure configuration removes weak defaults and locks down system hardening. In zero trust security, you assume no one is trusted by default. So MFA and secure configuration work together to block compromised account protection issues before they escalate.
How can penetration testing and intrusion detection support exposure management and risk management?
Penetration testing shows how real attackers might break in, while intrusion detection watches for threats already knocking. Both feed into exposure management and risk management by giving you data on weak points. With that knowledge, you can prioritize vulnerability patching, attack vector elimination, and security monitoring for smarter defense.
References
- https://en.wikipedia.org/wiki/2023_MOVEit_data_breach
- https://www.researchgate.net/publication/260986622_False_Positives_and_Negatives_from_Real_Traffic_with_Intrusion_DetectionPrevention_Systems

