
Digital security’s like playing hide and seek in the dark – you never know what’s lurking until someone trips over it. Most companies stumble around blind until something breaks. That’s where these attack surface tools come in clutch, lighting up every corner hackers could squeeze through.
Teaching at our bootcamps, we watch students’ faces when they first run these scans. Pure shock. Every single time. These tools never sleep, always hunting for trouble spots before trouble finds them.[1]
Key Takeaways
- Those analysis tools never sleep – running day and night to catch new assets and spot weaknesses
- Each security tool’s got a specialty – network monitoring, web apps, cloud infrastructure
- Smart teams combine automated tools with hands-on testing, since that’s what attackers do too
Attack Surface and Why Does It Matter
Think of a company’s digital footprint like some sprawling mansion, except this one’s got countless entry points hiding in plain sight. The attack surface spans everything from public-facing APIs to cloud instances tucked away in forgotten corners.
As systems grow more complex, the number of potential weak spots multiplies, which is why teams need to understand how to minimize attack surface before things get out of hand.
Working with dev teams at our bootcamps shows just how messy this gets. Students dig into mapping exercises and there’s always this moment – that sharp intake of breath when they discover some ancient staging server still running, or an API endpoint nobody’s patched since last summer.
These overlooked assets give experienced security pros nightmares, which is exactly why we’ve made attack surface tools such a core part of our training program. They’re like having eyes on every door, window and crawl space, 24/7.
Core Functions of Attack Surface Analysis Tools
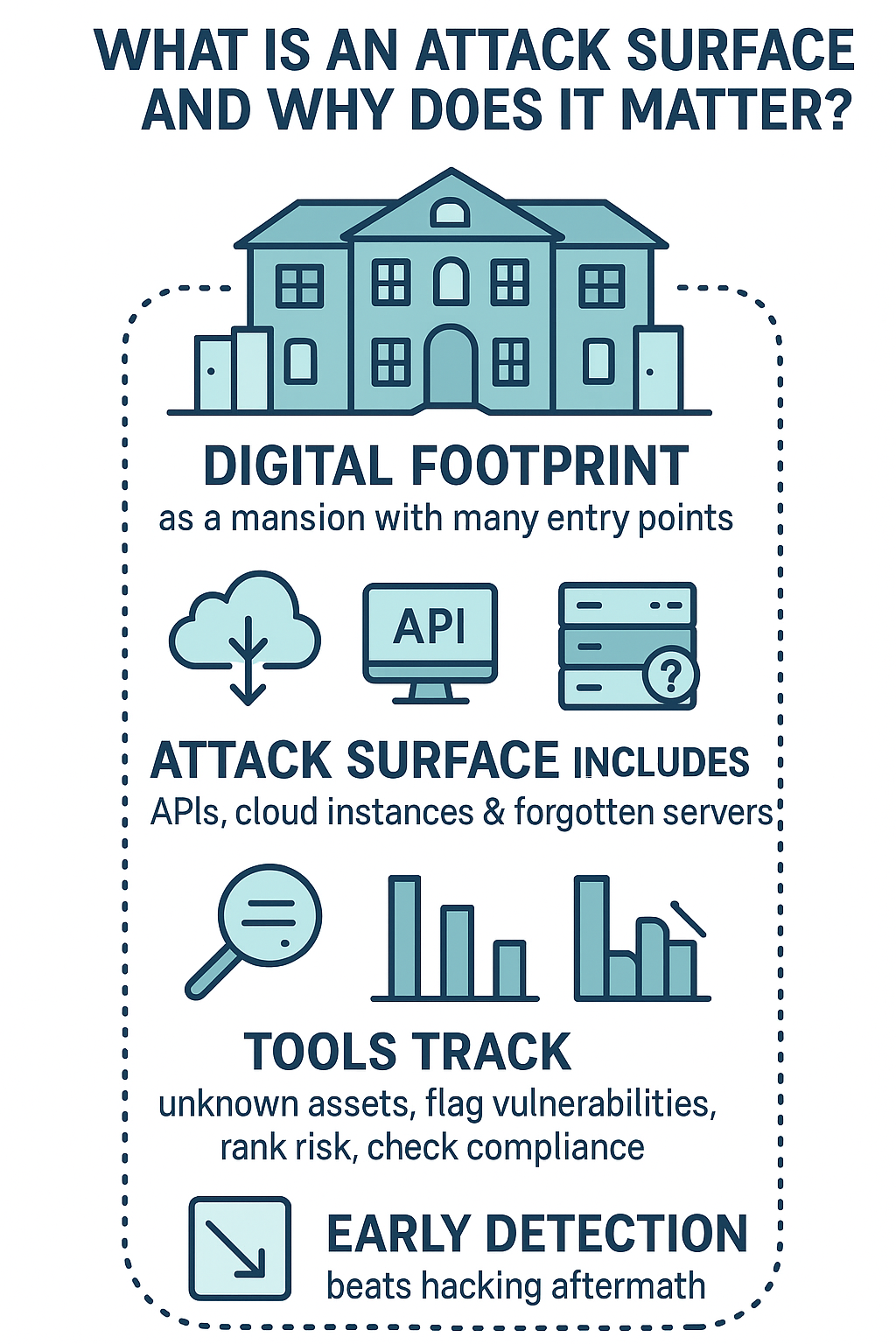
Watching these scanners do their thing in our hands-on labs, there’s a clear pattern to what they handle:
- Track down unknown assets (those dusty old servers everyone forgot)
- Flag vulnerabilities before attackers find them
- Rank issues by risk level
- Keep pace with evolving attack techniques
- Check compliance requirements
- Provide actionable fix recommendations
Experience shows there’s no substitute for catching these issues early. Way better than scrambling after hackers have already gotten in. The tools might not be perfect, but they’re essential for any serious security program. Our students learn this lesson pretty quick once they see what they’re up against.
Real-World Tools: The Good, The Bad, and The Buggy
After years of watching students encounter challenges navigating security tools. We’ve seen what works and what just wastes time. Some tools break, others confuse, but a few stand out as pure gold for teaching.
Network Stuff
Every class starts with network scanning tools that reveal traffic patterns, but students light up when they first see network traffic like attackers do.
Windows Watching
Became a permanent fixture in the curriculum after a scary close call. One of our evening classes spotted a Windows update gone wrong that left admin ports wide open. Now everyone runs it, no exceptions.
Finding the Holes
Professional scanners we’ve used in training cost real money, and they deliver immediate hands-on value. But Graduates reported immediate value and most send back stories about catching critical vulnerabilities their first week on the job.
Cloud Scanning
Cloud security’s a different beast entirely. Traditional tools just don’t cut it when servers appear and disappear every few minutes. The good scanning tools adapt fast – they have to, or they’d miss half the infrastructure by lunchtime.
Web App Testing
Teaching web security requires serious tools. The professional suite we use looks intimidating at first (seriously, who needs that many buttons?), but students get it eventually. Free alternatives work fine for basics, perfect for those first steps into proxy tools.[2]
Risk Scoring
Nobody’s got time to fix everything at once. Risk scoring helps students learn to prioritize – fix the server that’s actually on fire before worrying about that one deprecated cipher suite.
Internet Searching
Security search engines reveal uncomfortable truths. Three weeks ago, our advanced class found their company’s badge readers exposed online. That discovery led to some interesting conversations with their IT departments.
Always-On Monitoring
Continuous scanning catches problems before they become disasters. Our monitoring setup alerts faster than our coffee machine brews – and that thing’s pretty quick.
How We Use Attack Surface Analysis in Practice
Last month’s advanced class tackled a messy network assessment that really drove home what these tools can do. Started simple – just scans to map out the network. Students’ eyes got wide when they saw how many forgotten systems were still running.
During our training exercises, cloud assets appeared and disappeared quickly, demonstrating the need for continuous cloud monitoring..
Manual testing always tells the real story. The class split into teams, each performing penetration tests to find holes missed by automated scans. Some students really got into it, finding creative ways past the usual defenses. Nobody ever believes how many bugs hide in plain sight until they’ve done this themselves.
Setting up that dashboard for tracking everything took forever (students complained, of course), but it paid off big time. The project sponsors could actually see what was happening without drowning in technical details. Three weeks in, patterns started emerging – same old security problems kept popping up in new places.
Just goes to show how fast attack surfaces change, even in a controlled environment like ours. Tools help catch the obvious stuff, but nothing beats hands-on experience for spotting the weird edge cases that keep security folks employed.
Practical Tips to Maximize Attack Surface Analysis Effectiveness
- Don’t rely on one tool alone: Mixing different attack surface reduction techniques gives better coverage since each tool has strengths and blind spots.
- Keep Tools Fresh and Updated: The attack surface is always shifting. New threats pop up, and new devices or accounts get added. If our tools don’t stay updated with the latest signatures and settings, they’ll miss what’s really out there. Updating keeps them sharp and ready.
- Integrate with Threat Intelligence: Context matters. Knowing which vulnerabilities are actively exploited helps prioritize.
- Automate When You Can: Running scans all the time and setting up alerts lowers the risk of missing new weak spots. Automation keeps watch even when we’re not looking, so threats don’t slip past us.
- Include Manual Testing: Automated scans can miss subtle or business-specific risks. Penetration testing complements tool findings.
- Document and Track Remediation: Visibility into fixes ensures vulnerabilities don’t linger unnoticed.
- Engage Cross-Functional Teams: Attack surface touches IT, security, dev, and operations. Collaboration is key.
Attack Surface Analysis Tools: The Backbone of Cyber Risk Management
Credit: RSA Conference
In today’s world, digital stuff keeps piling up, and attackers keep getting trickier. That’s why these tools matter so much. They take what we can’t see and make it clear, turning blind spots into things we can actually track. Every time we use them, our sense of security gets sharper. They show us dangers we might have missed and help us plan smarter ways to stay safe.
If you’re serious about reducing your attack surface exposure, attack surface reduction best practices is a strong place to start, then evaluate your current tools and processes. Experiment with a few to see how they fit your environment. The goal isn’t to check a box but to build a habit of continuous awareness and improvement.
Conclusion
After running hundreds of security bootcamps, one thing’s crystal clear – you can’t secure what you don’t know about. Start simple: get a map of what’s out there, run those scans, and watch those access points like a hawk.
Our graduates always say the same thing – they never realized how many holes their systems had until they actually looked. Some basic scanning tools and a curious mind can spot trouble before it finds you. No fancy tricks needed, just consistent checking. Join our Security Bootcamp here
FAQ
How do attack surface analysis tools help map the attack surface and identify attack vectors?
Attack surface analysis tools study the full attack surface by scanning for attack vectors that hackers might use. These tools combine asset discovery, vulnerability scanning, and network scanning to reveal hidden entry points. By spotting exposed assets and attack points early, organizations can run real-time attack surface analysis and lower risks before attackers strike.
What role does attack surface mapping play in risk assessment and threat modeling?
Attack surface mapping shows the digital attack surface, including the internal attack surface, external attack surface, and even the physical attack surface. This map helps with risk assessment and threat modeling so teams know which attack surface weaknesses matter most. With this knowledge, risk prioritization and attack surface risk mitigation become easier to plan and carry out.
How can attack surface discovery tools detect shadow IT and cloud security gaps?
Attack surface discovery tools track both known and unknown assets, including shadow IT and cloud security misconfigurations. They often build a cloud asset inventory and detect authentication vulnerabilities, authorization weaknesses, and risks of data leakage. By linking continuous asset monitoring with attack surface monitoring, teams can uncover new attack surface exposure in real time and improve cyber risk management.
Why are penetration testing and security monitoring important for attack surface defense?
Penetration testing checks for attack surface vulnerabilities through simulated attacks, while security monitoring watches for live threats. Together, they reveal exposed assets, application profiling issues, and insider threats. When combined with compliance monitoring, firewall analysis, and endpoint security, these methods strengthen attack surface defense and help organizations spot reconnaissance in attacks before damage happens.
How do attack surface management tools support zero trust security and attack surface reduction?
Attack surface management tools bring together the attack surface assessment process, attack surface identification, and attack surface prioritization. They measure attack surface exposure, run attack surface testing, and support zero trust security with multi-factor authentication. Along with vulnerability assessment tools, patch management, and attack surface automation, these tools drive attack surface reduction and stronger cyberattack prevention.
Can attack surface visualization improve awareness of social engineering attack surface and phishing attack surface?
Attack surface visualization shows how entry points and user access points connect, including network interfaces and network topology. By mapping the social engineering attack surface and phishing attack surface, teams build attack surface awareness and detect weak spots in authentication or authorization. This makes attack surface mitigation and security audits more effective in defending against different attack surface attack types.
How does cloud-native attack surface relate to supply chain attack surface and microservice attack surface?
The cloud-native attack surface often expands through the microservice attack surface, cloud security risks, and cloud asset inventory gaps. The supply chain attack surface adds more entry points through third-party risk and exposed assets. With an attack surface framework and attack surface security controls, organizations can use vulnerability scanning, network port scanning, and attack surface detection to reduce attack surface exploitation risks.
References
- https://straitsresearch.com/report/attack-surface-management-market
- https://unit42.paloaltonetworks.com/cloud-network-scanning-traffic/

