
Every system has weak spots, and lately it’s been getting worse. Software teams that don’t patch their endpoints might as well leave their front door wide open – we’ve seen this happen more times than we can count. Our training bootcamp teaches developers how to spot these gaps before hackers do. The trick is pretty straightforward: lock down systems tight, stay on top of updates, and keep a close eye on who’s got access to what. It’s basic stuff, but you’d be amazed how many places mess this up.
We focus hard on real-world scenarios because that’s where the rubber meets the road. When a team lets their guard down, even for a minute, that’s usually when trouble starts.[1] Security isn’t just about tools and tech – it’s about building habits that stick.
Key Takeaways
- Getting rid of weak spots means less chance for hackers to break in
- Keep devices and cloud stuff locked down tight – patch updates, shut unused ports, limit who gets access
- Split up networks, automate security checks, and watch everything like a hawk
Attack Surface Reduction: Definition and Security Goals
What is Attack Surface Reduction?
Think of a building with way too many doors – that’s what most systems look like to hackers. We’ve spent years teaching developers how to spot these openings before the bad guys do. Sometimes it’s an old admin account nobody remembered to delete, or maybe it’s just some service nobody uses anymore. Our students learn pretty quick that making the target smaller means sleeping better at night.
Why Does This Matter?
Most security folks get stuck playing whack-a-mole with individual problems. But here’s what we’ve learned from training hundreds of developers – you’ve got to step back and look at the whole picture. When there’s fewer ways to break in, there’s less chance someone will. Simple math, really.
The Real Benefits
Almost every team that’s gone through our bootcamp comes back with the same story – their security headaches dropped like a rock. Instead of running around fixing problems, they’re actually making things better. Yeah, compliance is still a pain (nobody loves it), but it’s way easier when you’ve already closed most of the gaps.
Making It Work
Look, this isn’t rocket science. Lock down your systems (no extra services, tight configs), patch everything regularly, and don’t give people access they don’t need. We teach developers to build this stuff in from the start because fixing things later is just asking for trouble. For teams looking at proven attack surface reduction techniques, the basics—patching, minimizing services, and least-privilege access—work better than any shiny new tool.
Endpoint Devices and Cloud Infrastructure: Risk Factors and Best Practices
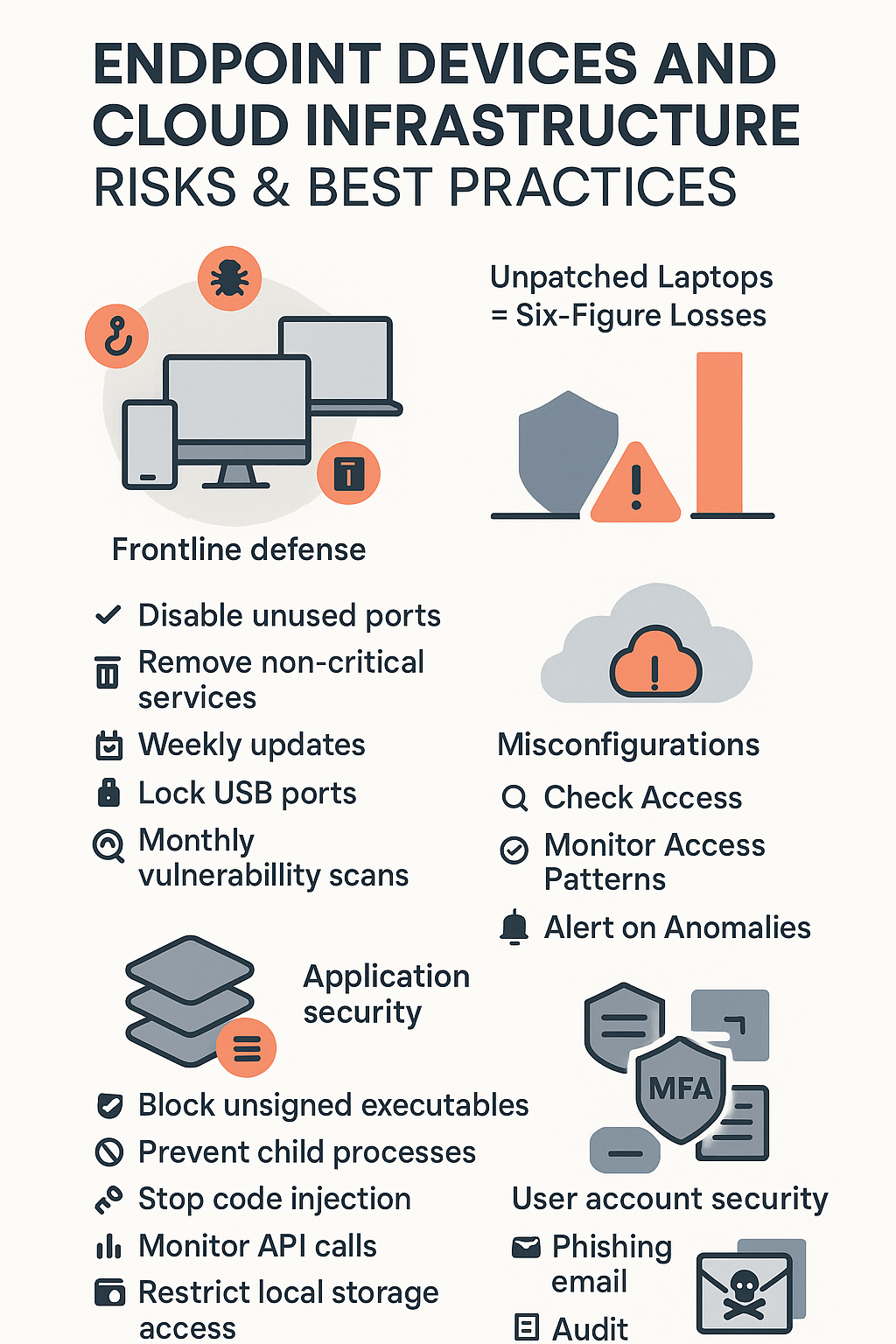
Every week our team sees the same story play out – endpoints getting hit first. They’re like the front line in a battle, taking fire from every direction: malware sneaking in through downloads, phishing emails that look legit (until they don’t), and direct attacks probing for weak spots. We’ve worked with dozens of companies where a single unpatched laptop led to six-figure losses. Even worse? Most of these breaches happened through vulnerabilities that had patches available months earlier.
Security updates can’t wait. Period. When our bootcamp students ask what to tackle first, that’s always the answer. Here’s what works:
- Kill unused ports (seriously, why’s that printer port still open?)
- Dump any service that’s not critical
- Get religious about those updates (weekly at minimum)
- Lock down USB ports if you’re not using them
- Run vulnerability scans (at least monthly)
The cloud stuff? That’s where things get messy. Every month someone leaves an S3 bucket wide open or forgets to check their API settings. Weak controls can expand the web application attack surface, giving attackers more ways to sneak in. Our training focuses hard on this because cloud security isn’t optional anymore – it’s survival.
Setting up proper cloud security isn’t rocket science, but it needs attention to detail. Start by checking who’s got access to what (you’d be shocked at how many admin accounts are floating around). Monitor everything – weird access patterns, unusual data transfers, configuration changes. When something looks off, it probably is. Teams who’ve gone through our program learn to spot these issues early, often saving their companies from those embarrassing “we got hacked” headlines.[2]
Applications and User Accounts: Weaknesses and Mitigation Approaches
Most developers don’t think about permissions until something breaks. Applications stack up privileges like a hoarder collects newspapers – just in case they might need them someday. But each extra permission is another potential crack in the wall. The real kicker comes from third-party libraries, those convenient bits of code that no one’s updated since 2019. When apps start talking to each other, passing data back and forth without much oversight, that’s when things get messy.
Good code reviews catch most of these issues, but automated scans pick up what tired eyes miss. Our bootcamp teaches developers that reducing the application attack surface starts with controlling permissions, updating third-party libraries, and enforcing ASR rules. Key defenses include:
- Blocking unsigned executables from running
- Preventing apps from creating child processes
- Stopping code injection attempts
- Monitoring API calls for suspicious patterns
- Restricting access to local storage
User accounts might seem straightforward, but they’re like catnip to attackers. Phishing emails still work way too often, and stolen credentials let attackers move through networks like they own the place. That’s where MFA comes in – not perfect, but it stops most attacks cold. Regular permission audits (yes, they’re boring, but they work) keep privilege creep under control.
Network Perimeter Management and Microsoft Attack Surface Reduction Rules
Open ports are like unlocked doors – and some networks look like Swiss cheese. Every unused service running at the perimeter is another potential way in. The developers coming through our program learn this the hard way during penetration testing exercises. Network segmentation isn’t just a buzzword – it’s the difference between a minor incident and a major breach.
Payment systems, customer data, and critical infrastructure each need their own isolated zones. Smart firewall rules and properly configured IDS/IPS systems catch the obvious stuff, but Microsoft’s ASR rules add essential controls for Windows environments. They’re particularly good at stopping the kind of attacks that slip past traditional defenses.
These rules do things like preventing Office apps from spawning dangerous processes or blocking credential theft attempts. Here’s what proper implementation typically blocks:
- Executable content from email clients
- Scripts from downloading payloads
- Raw disk access from unauthorized apps
- Process injection attempts
- Untrusted font loading
- Code running from USB drives
Real-world results show these controls work – organizations using them properly see significant drops in successful attacks. But like any security tool, they need regular tuning and monitoring to stay effective without getting in users’ way.
Asset Inventory, Patch Management, and Access Control Strategies
Security’s most basic rule still trips up even experienced teams – you’ve got to know what you’re protecting. After watching hundreds of organizations struggle with this, it’s clear that keeping track of assets isn’t just bookkeeping. Every forgotten server, overlooked cloud instance, or shadow IT application is a potential blindspot. The dev teams we work with often discover whole clusters of unknown assets during initial scans, and each one is a potential entry point for attackers.
Patch management sounds simple but gets messy fast. There’s always that one critical system that “can’t be taken down for updates,” or that custom application that breaks with every patch. But leaving systems unpatched is like leaving your front door unlocked because the lock sometimes sticks. Smart teams prioritize based on real risk:
- Critical vulnerabilities in internet-facing systems first
- Systems handling sensitive data next
- Internal systems with compensating controls last
- Legacy systems that can’t be patched get isolated
- Regular automated scans to catch what’s missed
Access control isn’t just about strong passwords anymore. Sure, we still need those, but proper privilege management and MFA are the real workhorses of modern security. The bootcamp participants who implement true least-privilege see immediate results – fewer incidents, better audit trails, and simpler compliance reporting.
Network Segmentation, Service Minimization, and Zero Trust Implementation
Network segmentation used to mean throwing up a few VLANs and calling it done. Now we’re seeing organizations implement true micro-segmentation, isolating individual workloads and applications. It’s more work upfront, but when (not if) something gets compromised, that extra effort pays off. The containment keeps attackers from turning a small breach into a disaster.
Every unnecessary service, unused port, or forgotten piece of software is another potential way in. We’ve seen organizations running services they haven’t used in years, just because nobody wanted to risk turning them off. Modern environments need regular cleanup:
- Document everything before removing anything
- Test in stages – don’t pull the plug all at once
- Monitor for dependencies you didn’t know about
- Have a rollback plan ready
- Keep detailed logs of what’s removed and why
Zero trust isn’t just another buzzword – it’s a fundamental shift in how we think about security. No more trusted internal networks where everything gets a free pass. Every request gets verified, every access gets logged, and nothing gets automatic trust just because it worked yesterday. It’s more work for everyone involved, but it’s where security has to go.
Automation, Cloud Security, and Continuous Risk Monitoring
Credit: Concept Work
How Does Automation Enhance Attack Surface Reduction? Embedding Security Testing in CI/CD Pipelines
Automating security testing in CI/CD pipelines allows early detection of misconfigurations, insecure code, or vulnerabilities before deployment. This proactive approach reduces risk from new software releases.
What Are Best Practices for Securing Cloud Services and APIs? Configuration, Encryption, and Managed Security Platforms
Securing cloud services requires proper configuration, encryption of data in transit and at rest, and managed security platforms that enforce policies. We’ve found that continuous monitoring of cloud activity is essential for spotting anomalies.
How Critical is Continuous Monitoring? Real-Time Threat Detection and Dynamic Risk Assessment
Continuous monitoring lets us detect threats and unauthorized changes in real time. Dynamic risk assessment helps adjust controls as new threats emerge. Without it, even the best defenses might fail due to delayed response.
Conclusion
Teams that stay on top of their patches, monitor and manage access, and segment networks are the ones who don’t make the headlines for the wrong reasons. Start small if needed, but start somewhere. Take stock of your assets, close obvious vulnerabilities, then keep watching. That’s how you stay ahead of the bad guys. Ready to take the next step? Join now!
FAQ
How does attack surface management connect with vulnerability management and a broader cybersecurity strategy?
Attack surface management maps every point where attackers might sneak in, while vulnerability management checks those weak spots for flaws. Together, they help teams see the whole picture. A solid cybersecurity strategy blends both, tracking open attack vectors, running risk assessments, and using security frameworks. It’s about shrinking exposure, spotting gaps, and keeping cyber defense ready before trouble hits. Without this combined approach, you risk blind spots where threats can slip through unnoticed.
Why are system hardening, network segmentation, and access control key to least privilege?
System hardening cuts away extra services, network segmentation keeps traffic in its lanes, and access control decides who can reach what. All of this supports the principle of least privilege, making sure people only get what they need. With multi-factor authentication added in, attackers have fewer paths. Together these practices shrink the attack surface, stop sideways movement, and improve your overall security posture without creating more headaches for everyday users.
How do patch management and software updates help with cloud security and API security?
Patch management and software updates close known holes in systems. When left undone, these gaps threaten cloud security and API security, where sensitive data often lives. Attackers love unpatched apps because they serve as open doors. By treating updates like routine maintenance, you keep defenses strong and secure configurations steady. Fresh patches support malware prevention, make breach prevention more reliable, and tighten protection across cloud workloads and API endpoints.
What role do endpoint protection, malware prevention, and intrusion detection play in asset inventory?
Endpoint protection guards devices, malware prevention keeps infections out, and intrusion detection watches for break-ins. But these tools only work well if you know what’s out there, which is where asset inventory comes in. You can’t protect what you can’t see. Pairing configuration management and continuous monitoring with asset discovery helps close gaps. This mix strengthens cyber hygiene, improves threat monitoring, and builds cyber resilience by cutting down blind spots.
How can security automation and zero trust security support attack mitigation and risk assessment?
Security automation speeds up response when attacks hit, while zero trust security removes the old idea of “trusted” zones. That means every login, request, or packet gets checked. Both approaches reduce errors, improve attack mitigation, and give clearer insight during risk assessment. When paired with security orchestration, behavioral detection, and security incident response, the system adapts fast. This layered setup builds stronger cyber resilience and keeps security technologies working together.
Why does security posture depend on network isolation, application whitelisting, and security policies?
Security posture shows how ready your defense is. Network isolation cuts off risky zones, application whitelisting allows only safe programs, and security policies guide behavior. Threat intelligence, penetration testing, and continuous monitoring add sharper insight. Each step reduces threat exposure and makes cyber defense stronger. This combination means attackers face more walls, fewer shortcuts, and tighter security compliance checks. Strong posture is less about perfection and more about steady threat reduction.
How do user access review and identity and access management connect with security auditing?
User access review checks if people still need their permissions, while identity and access management controls how they log in and what they reach. Security auditing then verifies that rules are followed. Add in privileged access management and you get even tighter control over sensitive systems. These practices prevent credential theft, lower insider risks, and improve privileged user monitoring. Done regularly, they help sustain compliance and shrink the attack surface.
How can ransomware protection, secure configurations, and endpoint detection and response work together?
Ransomware protection blocks encryption attacks before they spread. Secure configurations remove unsafe defaults, and endpoint detection and response watches for signs of compromise. Add behavioral detection and you’ve got early warning. Pair that with security orchestration for quick action, and you’re stacking defenses. This teamwork supports attack path analysis, suspicious activity detection, and overall breach prevention. It’s about layering security technologies so attackers face walls instead of open hallways.
Why are vulnerability scanning, attack surface visualization, and threat hunting part of threat modeling?
Vulnerability scanning shows weak spots, attack surface visualization maps how attackers might enter, and threat hunting actively looks for suspicious behavior. All three fit into threat modeling, which imagines how an attack might unfold. Security logs analysis, firewall rules, and network traffic analysis add even more detail. This mix helps security teams see attack paths in action, tighten cybersecurity controls, and practice smarter attack surface minimization for lasting threat reduction.
How do security patches, software removal, and configuration hardening strengthen cyber hygiene?
Security patches close holes, software removal clears out unused apps, and configuration hardening locks down risky defaults. These steps keep systems clean and reduce attack vectors. Cyber hygiene grows stronger with asset discovery, system baseline checks, and continuous monitoring. When tied to security frameworks and secure coding, they support cloud workload protection and endpoint hardening. This steady cleanup builds cyber resilience and keeps cyber defense one step ahead of attackers.
How do breach prevention and security governance tie into risk management and security technologies?
Breach prevention is about blocking attacks before they spread, while security governance sets the rules. Risk management weighs the possible damage against defenses. Security technologies, from data encryption to credential theft prevention, build the toolbox. Add security awareness training, security incident response, and threat intelligence, and you get a cycle that adapts. These combined practices drive threat reduction, reinforce attack surface minimization, and sharpen the long game of cyber resilience and defense.
References
- https://en.wikipedia.org/wiki/2017_Equifax_data_breach
- https://www.news.com.au/technology/online/security/juicy-customer-data-belonging-to-thousands-of-aussies-leaked-from-nine/news-story/ea3e93e6d543d677dd810589ad993af2

