
Reducing the attack surface means cutting down the number of ways an attacker can get in, fewer doors, fewer risks. In this decade, every open port, exposed service, or unnecessary account is a potential entry point. That’s why trimming access, isolating systems, and locking down configurations matters far more than memorizing jargon.
Real security comes from practical steps developers can apply and see in action, not just theory. When teams learn to minimize exposure hands-on, the lesson sticks, and so does the protection.
Keep reading to explore attack surface reduction techniques that truly work.
Key takeaway
- Cut off what hackers can reach. It sounds simple, and in practice it really works.
- Know your system inside out, watch those doors, and keep things separated. Basic stuff that works.
- Regular security scans with solid tools – because predictable systems make easy targets.
Reducing Application Attack Surface
Apps these days are messy. They’re full of code chunks, API hooks, and those fancy third-party tools everyone loves using. Our security team spent way too many late nights mapping student projects, and there’s always something lurking in the corners. Like those test APIs nobody remembered to shut down – they’re just sitting there, practically wearing a “hack me” sign.
Nobody gets excited about cleaning up unused features, but here’s the thing: our advanced class built this API with ten endpoints when they only needed three. Seven extra ways in, just collecting dust and asking for trouble.
The thing that keeps hitting home in our bootcamp? Check your inputs, every single time. Forms, API calls, all of it. And yeah, debug mode’s great for testing – everyone knows that. But seeing production servers spitting out full error messages to potential attackers? Makes us cringe every time. Lock down those configs and move on to the next problem.
Attack Surface Reduction Best Practices
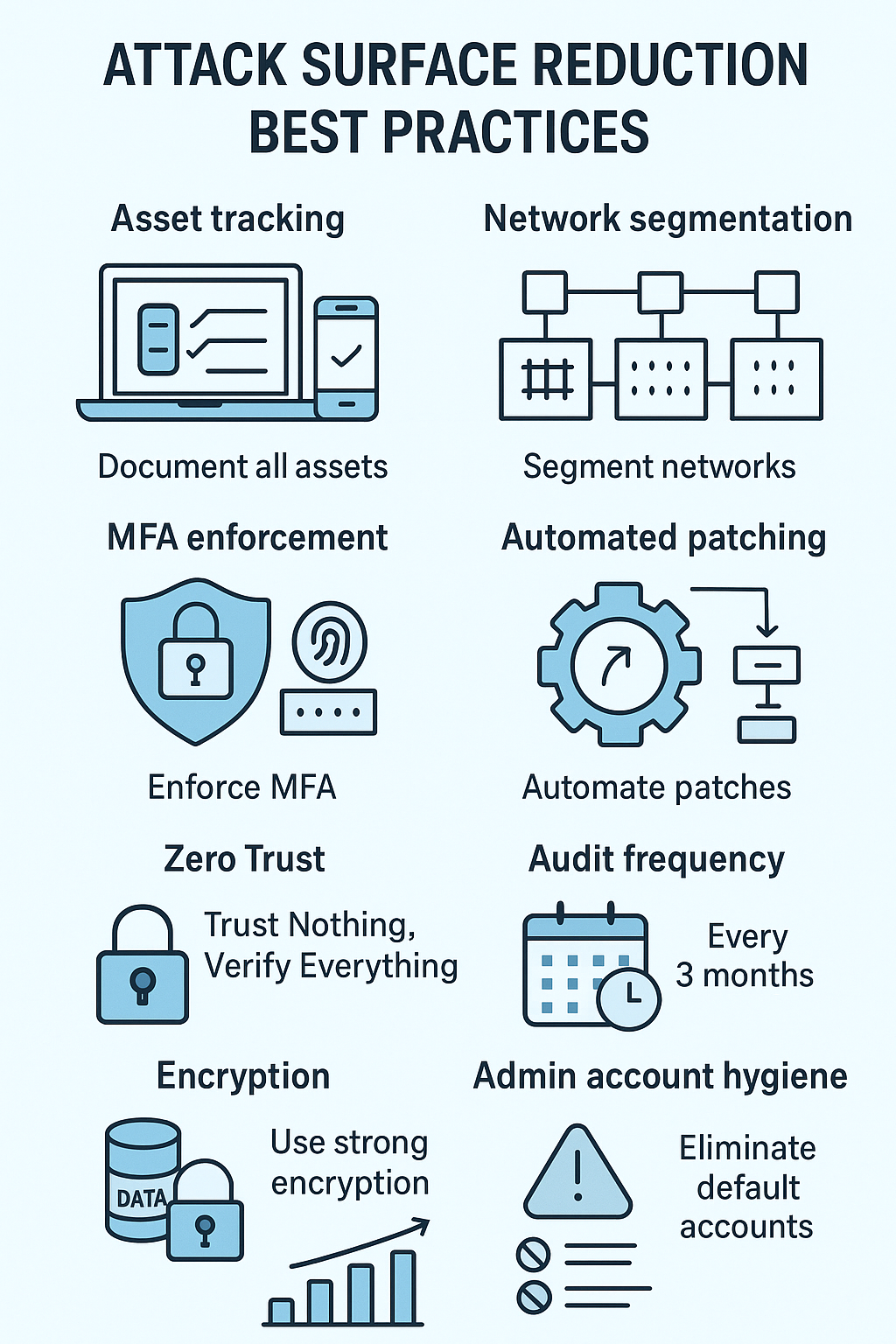
Security boots on the ground tell a different story than the glossy vendor presentations. Three years watching students fumble through basic asset tracking reveals an uncomfortable truth – most organizations don’t know what’s running on their networks. It’s not fancy, and it’s definitely not the kind of thing that wins innovation awards, but getting the basics right matters more than whatever new framework vendors keep promoting each year.
The fundamentals haven’t changed much, even if the threats have. These practices emerged from real-world failures, not marketing meetings, foundational security principles still guide the way:
- Document every asset that touches the network (yes, even the CEO’s personal iPad)
- Break systems into smaller, manageable chunks
- Give users exactly what they need – nothing more
- Push MFA everywhere you can, complaints be damned
- Set up automated patching with rollback plans
Network segmentation isn’t rocket science – it’s just good fencing. Students learn this lesson hard during attack simulations, usually after their “minor” breach turns into a complete network takeover. One compromised dev machine shouldn’t give attackers keys to the kingdom, but it happens all the time.
That whole “zero trust” thing people keep talking about? It’s actually pretty straightforward – trust nothing, verify everything. Sure, it’s a pain. Users hate typing in codes, and IT teams hate the extra work. But after watching malware tear through “trusted” networks in minutes, there’s really no alternative. The old “castle and moat” security model is dead, we just haven’t finished burying it yet.[1]
How to Minimize Attack Surface
No one wants to hear it, but there’s no magic bullet for security. Looking back at years of pen testing logs, the pattern’s pretty clear – complexity kills. Those dusty corners of the network, the stuff everyone forgot about? That’s where breaches start. The security teams that win aren’t the ones with the fanciest tools – they’re the ones who cleaned house first.
Basic steps still catch most problems before they start:
- Run full audits every three months
- Use strong encryption everywhere (at rest and in transit)
- Kill those default admin accounts
- Change default system names to something less obvious
- Get regular outside pen testing (quarterly if you can afford it)
Strong encryption’s like wearing a seatbelt – it won’t prevent the crash, but it might save your life. The pen testing teams love finding unencrypted data. Game over in minutes, sometimes seconds. Even mediocre encryption buys enough time to detect and respond. But good luck explaining that to management when budget season rolls around.
Config management bores people to tears, but that’s where the real fights happen. Default passwords stick around way too long. Test servers get forgotten in dark corners. Every single semester students find production systems still running on factory settings.
The worst part? These aren’t sophisticated attacks – just basic mistakes nobody caught. Strict baselines help, but only if someone’s actually checking. Those quarterly audits nobody wants to do? They’re the difference between a minor incident and front-page news.
Attack Surface Analysis Tools
Digital footprints keep growing, and frankly, most security teams can’t keep up manually. After spending way too many nights testing tools nobody asked for, some clear winners emerged. The right scanner mix helps teams spot problems across sprawling networks – from forgotten basement servers to those cloud instances developers spin up like coffee runs.
Free tools saved our budget (around $50k), and they work pretty well:
- Nmap for network scanning (yeah, it’s old but it works)
- OWASP ZAP for web testing
- Wireshark for traffic analysis
- Metasploit for vulnerability checks
- Custom Python scripts for specific needs
Network visualization changed everything. Put a decent mapping tool in front of an analyst who’s been staring at logs for months, and watch their eyes light up. Suddenly all those mysterious connections make sense – which machines shouldn’t talk to the internet, where the weird traffic goes, what needs fixing first.
The SIEM setup probably saved someone’s job. When weird stuff hits exposed services at 3 AM, people need to know fast. Correlation rules catch things humans miss, especially across different systems. Sure, there’s some noise, but better that than missing something critical.
Web Application Attack Surface
Teaching web security’s like showing new drivers all the ways they might crash – kinda depressing but necessary. The bootcamp students learn quickly after their first few disasters. Every form becomes a potential SQL injection, every cookie a target, every input field a possible cross-site scripting playground.[2]
The team mapped everything across a dozen training apps:
- Login flows and session management
- Form handling and input validation
- API endpoints and authentication
- File upload mechanisms
- Database connections
Cross-site scripting showed up in about 60% of student code reviews, usually where someone got lazy with input checks. Now developers and security folks actually talk to each other, catching most issues before they hit production servers.
Password rules caused the usual complaints until we showed everyone the attack logs – roughly 2,000 brute force attempts daily. Suddenly those special characters and MFA tokens made more sense. The API mess needed serious cleanup too. Students kept adding endpoints like they were handing out candy, but each one’s another attack vector. These days, new endpoints need real justification and proper security controls.
API Attack Surface Management
APIs have exploded in use but also in risk. Attackers target APIs because they often provide rich access to data and functions. We had to rethink how we secure APIs from the ground up.
Limiting API endpoints to only those essential minimized exposure. Input validation, authentication, and authorization became frontline defenses. We set up monitoring for anomalous API activity, looking for spikes or unusual patterns that might indicate attacks.
Patch management applies here too. Many API vulnerabilities stem from outdated components or libraries.
API attack surface management required continuous monitoring. Unlike traditional systems, APIs change rapidly, so we adopted tools that could automatically discover and assess new endpoints.
Benefits of Attack Surface Reduction
We saw the benefits firsthand. Reducing the attack surface improved our security posture, making it harder for attackers to find exploitable weaknesses. With fewer vulnerabilities, incident response became faster and more focused because we had fewer places to check.
Compliance with various security standards became easier. Regulators often demand strict controls over access and vulnerability management, and our reduced attack surface helped meet those requirements.
Cost savings followed naturally. Fewer breaches mean less money spent on remediation, legal issues, and downtime. Plus, managing a smaller, well-defined attack surface reduced operational complexity.
Network Attack Surface Reduction Examples
On the network side, we implemented VLAN segmentation to isolate sensitive environments from general user access. This prevented attackers from hopping across systems if they breached one area.
Unused network services and ports were disabled. It’s surprising how many devices still have open ports for services no one uses but attackers scan for constantly.
Firewalls and intrusion detection systems (IDS) were configured to block suspicious traffic actively. Encrypting all communications, especially remote access via VPNs, added layers of protection.
We also phased out legacy systems that couldn’t be securely patched or properly segmented, removing high-risk targets from critical zones.
Attack Surface Monitoring Strategies
Credit: Concepts Work
Monitoring is the glue that holds attack surface reduction together. We adopted continuous asset discovery to keep our inventory current. It’s easy for new devices or applications to slip in unnoticed.
Automated vulnerability scans ran regularly, flagging new risks. Real-time monitoring of network traffic and user behavior helped catch anomalies early.
Our SIEM system correlated events across the environment, providing alerts that cut through noise. We set up regular tests where friendly hackers tried to break in, just like real attackers would. These practice attacks showed us if our defenses held strong or if we had weak spots that needed fixing.
This proactive posture helped us identify and fix issues before attackers could exploit them.
Attack Surface vs. Attack Vector
Most security folks mix these terms up, but they’re different beasts entirely. Think of your house – the attack surface includes every window, door, vent, and pipe going in. It’s everything someone could possibly use to break in. And just like houses, networks have way more entry points than most people realize.
The vector’s method, how someone actually gets in. Maybe they sweet-talk their way through the front door, maybe they find an unlocked window in the back. In network terms, that’s your phishing emails, those SQL injections nobody caught, or that one API key someone posted on GitHub last month.
This stuff clicked during a nasty incident last spring. The surface was huge – about 300 endpoints, 50 cloud instances, and too many third-party integrations to count. But the vector? A single developer fell for a fake password reset email. One click, one compromised account, and suddenly everything was at risk.
These days the team treats them differently. Surface reduction means closing ports, removing old services, and limiting access points. Vector protection means watching for specific techniques – filtering emails better, checking code for injection flaws, monitoring for weird login patterns. Different problems, different fixes. Both matter.
Conclusion
Reducing the attack surface isn’t just a one-off fix, it’s an ongoing commitment. Our journey showed us something simple but big: you have to know every asset, cut off doors no one should use, split the network into safer parts, and keep watch all the time.
Picture your world like a fortress. If you close every gate you don’t need and guard the rest with sharp eyes, the walls hold strong. That’s how you keep out trouble and protect what matters most. Ready to take the next step in securing your “fortress”? Join the Secure Coding Bootcamp and elevate your defense strategy today.
FAQ
What is attack surface reduction and how do attack surface reduction techniques help minimize attack surface while improving security?
Attack surface reduction means shrinking the number of ways attackers can break in. Using attack surface reduction techniques, teams can minimize attack surface by shutting down weak spots like unused ports or old apps. This makes it harder for attackers to find a way inside. The goal is simple: the fewer openings you leave, the less chance of trouble. It’s a basic step in improving overall security because it keeps the focus on what really matters, cutting down risk before attackers even get close.
How does attack surface analysis differ from attack surface assessment, and when should you use attack surface monitoring or attack surface mapping?
Attack surface analysis is about studying every corner of your system to understand where weaknesses may live. An attack surface assessment digs deeper, measuring how serious those risks are. Meanwhile, attack surface monitoring keeps watch over changes in real time, and attack surface mapping helps visualize where possible attack paths exist. Teams often use them together: analysis and mapping to understand, assessment to prioritize, and monitoring to stay alert. This mix helps organizations stay ahead of threats instead of reacting too late.
Why are network attack surface reduction and endpoint attack surface both important in attack surface security and attack surface protection?
Network attack surface reduction lowers risk by locking down traffic and separating sensitive areas from casual use. Endpoint attack surface is just as important since laptops, phones, and desktops often act as attacker entry points. Together, they form the front line of attack surface security. Strengthening both improves overall attack surface protection, making it harder for intruders to slip in unnoticed. By reducing exposure on the network and at endpoints, organizations build a stronger and safer security posture.
What role do attack surface management tools and cloud attack surface management play in attack surface discovery and attack surface exposure?
Attack surface management tools help find and organize every digital asset, from apps to servers. Cloud attack surface management focuses on the fast-growing cloud environments many businesses now rely on. Both help with attack surface discovery by shining light on hidden risks, while also tracking attack surface exposure as systems change. Without these tools, it’s easy to overlook vulnerable assets. With them, teams can see the full picture and cut down on risks before attackers take advantage.
How does API attack surface management help reduce application attack surface and protect against API vulnerability or web application vulnerabilities?
API attack surface management tracks how apps talk to each other, spotting risks that might be invisible otherwise. It helps reduce application attack surface by finding weak API endpoints and tightening access. This is key in protecting against API vulnerability and common web application vulnerabilities. By watching APIs closely, teams can plug gaps before attackers use them. Strong API security, supported by API endpoint protection, lowers the chances of hidden risks sneaking past defenses and threatening larger systems.
What are attack surface best practices for using attack surface scanning tools, attack surface visualization, and attack surface identification?
Good attack surface best practices focus on clarity and action. Attack surface scanning tools are used to find new risks, while attack surface identification points out what’s at stake. Attack surface visualization turns this data into clear pictures, showing weak spots that might otherwise get lost. Using these together helps teams focus on the right fixes instead of getting lost in endless lists. The best practice is simple: discover, see, and fix, then repeat as systems evolve over time.
How can zero trust attack surface methods and attack surface reduction framework improve attack surface security posture through attack surface hardening?
Zero trust attack surface methods assume no user or device should be trusted by default, shrinking openings attackers might use. An attack surface reduction framework ties these ideas together into a repeatable plan. This supports attack surface hardening by making systems stronger and less exposed. Together, they sharpen attack surface security posture, lowering the chance that intruders can slip through unnoticed. Instead of relying on walls alone, these approaches build security into every layer, reducing risk at every step.
What is the difference between attack surface and attack vector, and how do attack vector types shape attack surface vulnerabilities?
Attack surface is the full set of doors and windows attackers might use, while attack vector definition explains the actual path an attacker takes. Attack vector types can include phishing, malware, or stolen passwords. These types directly shape attack surface vulnerabilities, since each vector needs an opening. Understanding the difference between attack surface and attack vector helps teams focus: shrink the surface to cut off opportunities, and study vectors to know how threats move. Both matter in building smarter defenses.
How can attack surface report and attack surface continuous monitoring support attack surface risk assessment and attack surface mitigation?
An attack surface report captures where risks stand at a moment in time. Pairing it with attack surface continuous monitoring helps track changes as systems shift daily. This pairing makes attack surface risk assessment more accurate and gives teams a base for attack surface mitigation. Without it, blind spots grow fast. With it, organizations get a living map of risks and can move quicker to close them. It’s about staying informed so you can act before attackers do.
What are the attack surface reduction benefits and challenges of following attack surface reduction rules in a real-world attack surface reduction strategy?
Attack surface reduction benefits include fewer entry points for attackers and stronger protection overall. Following attack surface reduction rules as part of an attack surface reduction strategy builds consistency. But challenges often arise: new tech, constant changes, and hidden vulnerabilities can open fresh gaps. Balancing rules with flexibility is key. The goal isn’t perfection but steady progress, keeping exposure low, risks in check, and security strong as systems and threats evolve in the real world.
References
- https://en.wikipedia.org/wiki/Security_awareness
- https://www.researchgate.net/figure/Percentage-probability-of-websites-vulnerable-by-different-class-of-cyber-vulnerabilities_fig1_279869021

