
The layers of security looked perfect on paper. Firewalls stacked up with intrusion detection, endpoint protection, and antivirus – a digital fortress that promised to keep the bad guys out. We’d seen it work at our bootcamp, watching students build these defenses piece by piece.
But reality hits differently. Organizations pile on controls until their networks crawl, costs spiral out of control, and insiders find clever workarounds. Teams struggle with the complexity of keeping everything in sync, even though multiple security layers remain essential for protecting modern networks.
Key Takeaways
- Too many security layers create a mess – policies clash, settings get mixed up, and mistakes happen.
- Small companies struggle with the price tag of multiple security tools, and sometimes more layers don’t help much anyway.
- Teams get too comfortable hiding behind their security stack, missing internal threats and forgetting to adapt when new attacks show up.
How Does Complexity Affect Defense in Depth Effectiveness?
Nobody warned us about the headache of managing five different security tools at once. “At the bootcamp, students often ask why we can’t just stack more layers for better protection. But trying to sync firewalls with gateways, antivirus, and two-factor auth is like herding cats. Our labs on defense in depth for developers show how different tools must work together instead of fighting each other.
Security teams face a harsh reality when these systems start fighting each other. The firewall blocks what the IDS wants to let through, endpoint security clashes with patches, and before you know it, there’s holes in what should be solid defense. A tiny mistake in user privileges (something we see students mess up all the time) can blow the whole thing wide open.
Keeping policies straight across all these layers isn’t just a tech problem – it’s a people problem too. Our monitoring team drowns in alerts from behavior tracking and network analysis. Even experienced pros struggle to keep everything working together smoothly, and that’s when the whole “layered defense” idea starts falling apart.
What Are the Cost Implications of Defense in Depth?
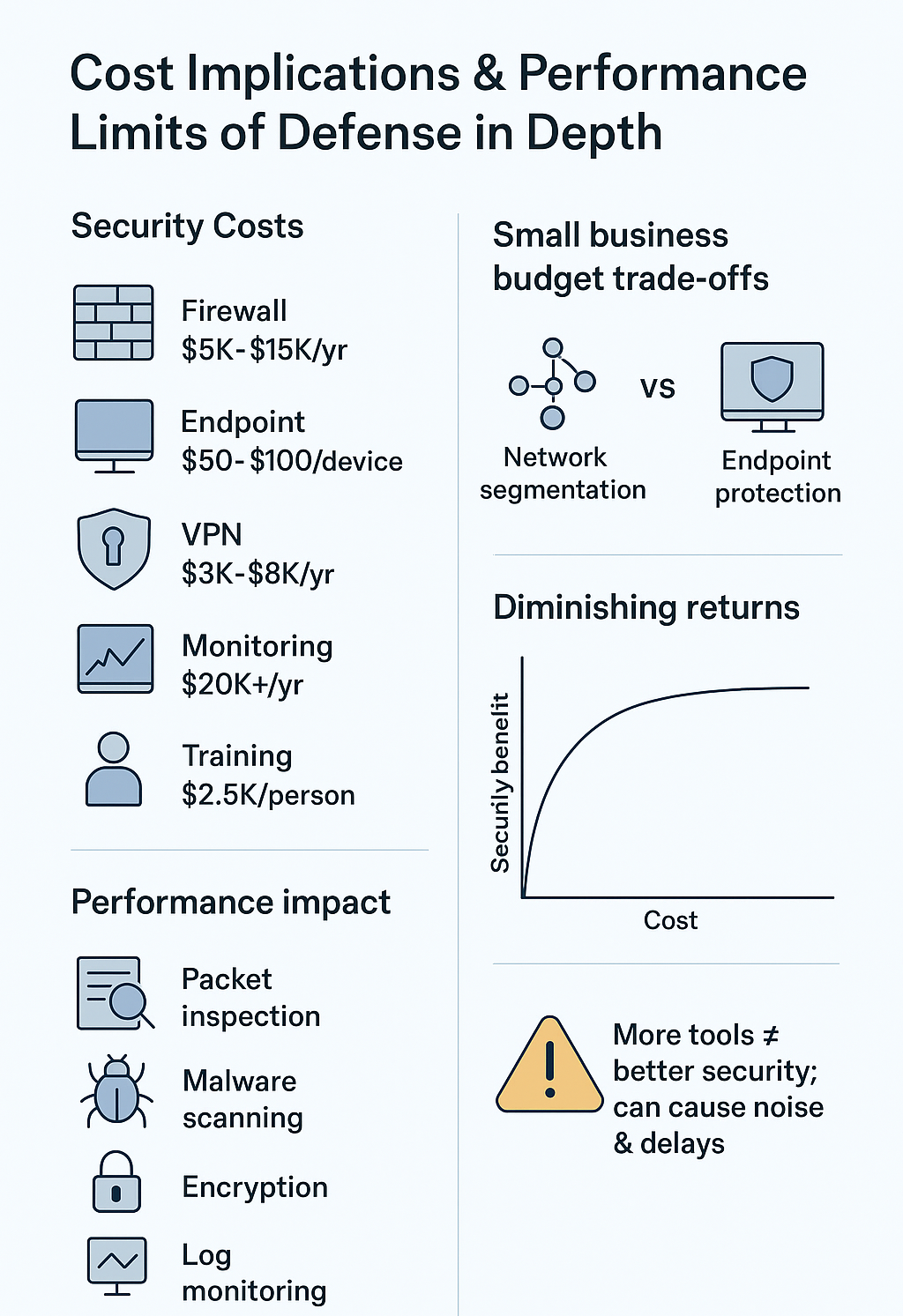
Money talks, and security costs scream. Our bootcamp students often arrive thinking defense in depth just means adding more tools. Then reality hits when they see the price tags. The basic security stack already stretches most budgets thin:
- Firewall licenses (usually $5,000-15,000 per year)
- Endpoint protection ($50-100 per endpoint annually)
- VPN solutions ($3,000-8,000 yearly)
- Security monitoring tools ($20,000+ annually)
- Training and certification ($2,500 per team member)
Small companies face impossible choices. They can’t match the security budgets of larger organizations, so they end up playing defense with half a deck.[1] Sometimes they’ll skimp on network segmentation to afford better endpoint protection, or stick with basic antivirus instead of springing for advanced threat detection. Which endpoint defense in depth measures actually reduce risks helps organizations avoid wasting money on overlapping tools.
The real kicker? Throwing more money at security doesn’t always buy better protection. We’ve watched organizations drain their budgets on overlapping tools that barely improve their security posture. It’s like buying insurance for your insurance – at some point, you’re just wasting cash.
Operating costs never stop either. Every security layer needs updates, maintenance, and someone who knows how to manage it. Training teams to handle multiple security tools costs time and money, and good security talent doesn’t come cheap. Sometimes the smartest move isn’t buying another security tool – it’s making better use of what you’ve already got.
How Do Diminishing Returns and Performance Impact Limit Defense in Depth?
The performance hit wasn’t obvious at first. Then the complaints started rolling in – systems dragging during busy hours, delayed communications, users getting timeout errors. Deep packet inspection and encryption, while necessary, put the brakes on everything. Our bootcamp students often notice it during their lab exercises when multiple security tools kick in at once.
Here’s what slows down most networks:
- Packet inspection at multiple checkpoints
- Real-time malware scanning
- Encryption/decryption processes
- Continuous log monitoring
- Multiple authentication steps
The reality check came when adding our third IDS didn’t make things any safer. It just created more noise, more alerts to chase down, and more chances for things to break. The students learn this the hard way – piling on security tools doesn’t automatically mean better protection. Sometimes it just means spending more money to make everything run slower.
Which Structural and Operational Challenges Affect Defense in Depth?
Security teams often fall into a dangerous comfort zone. With enough layers in place, they think they’re untouchable. That’s when the real trouble starts. Nobody checks the logs as carefully, patches slide, and those quarterly training sessions? They get pushed back again and again. We’ve seen it happen in countless organizations that come to us for help.
The insider problem doesn’t get enough attention either. Privileged users walk right past the perimeter defenses, moving through systems like they own the place – because technically, they do. Traditional security layers don’t do much when someone’s already inside with admin rights.
Integration between tools becomes a nightmare, especially when dealing with different vendors. Try correlating events across three different security consoles, each speaking its own language. The bootcamp labs demonstrate this perfectly – students struggle to piece together attack patterns spread across multiple systems.
Meanwhile, attackers keep evolving. They find new ways around defenses, exploit zero-days, and target the weak spots between security layers. Static defenses age like milk, and keeping everything updated turns into a full-time job. Organizations need to stay paranoid, assume they’re already breached, and plan accordingly.
How Do Incident Response and Security Perceptions Influence Defense in Depth?
When a breach did occur, the layered defense made the incident response more complex. Tracing the root cause meant sifting through logs from firewalls, network traffic analysis tools, endpoint monitoring, and user identity lifecycle management systems. Coordinating a response across teams responsible for various layers slowed down remediation efforts.
Moreover, the belief that layered defense equaled invulnerability led some decision-makers to undervalue complementary security practices. Training on phishing, enforcing strict password management, and deploying multifactor authentication sometimes took a backseat. This attitude increased vulnerabilities in human behavior and patch management.
Enhancing Defense in Depth Effectiveness Through Adaptive Practices
We learned fast that defense in depth only works if you keep watch all the time and have skilled people running it. Experts who knew how to split up networks, spot odd activity, and tie security tools together kept us from making mistakes and missing gaps.[2]
We also found that it wasn’t about stacking every tool we could find. Too many layers just slowed things down and cost more. Picking the right layers, the ones that stopped the biggest risks while keeping systems easy to use, gave us the best results. Implementing defense in depth works in practice showed us that careful planning matters more than tool quantity.
Automated tools emerged as lifesavers. Integrating unified threat management platforms enabled better event correlation and faster response times. Automation reduced the manual overhead that had bogged down our security team.
Sometimes the danger comes from inside, not just from outside hackers. Watching for unusual behavior and limiting who can reach the most important systems worked well with our other defenses. This holistic approach strengthened our security posture beyond just perimeter security.
Future-Proofing Defense in Depth Against Emerging Threats
Credit: security lab demo
To keep defenses relevant, we adopted a regimen of regular updates and adaptive security measures. Integrating threat intelligence allowed us to adjust defenses promptly as attack vectors evolved. We invested in adaptive authentication to respond to novel tactics dynamically.
Finally, we emphasized user training and cultivating organizational vigilance. People slip up, and that’s often how hackers get in. Teaching workers about risks and helping them build smart habits made a huge difference. When folks start thinking about security in their everyday jobs, the whole team gets stronger. Layered defenses need that human layer to truly hold strong.
Conclusion
Defense in depth looks great in textbooks, but real-world implementation is different. After years of teaching security at our bootcamp, we’ve seen how multiple layers can stop attacks cold, when they work right. But there’s no magic bullet here.
Each added layer brings its own headaches: more complexity, bigger bills, and constant upkeep. Smart teams find the sweet spot between solid protection and practical operations, focusing on what actually works rather than just piling on more security.
Ready to build that smart, practical security approach? Join our Bootcamp
FAQ
What are the main limitations of defense in depth even with strong passwords, antivirus software, and firewall rules in place?
Defense in depth sounds strong, but even with strong passwords, antivirus software, and carefully set firewall rules, gaps remain. Attackers often look for system vulnerabilities that slip past detection mechanisms. Human error mitigation is hard, and redundant security controls sometimes overlap without real benefit. The challenge comes when security policies look strong on paper but fail in practice. This leaves teams wondering how much cyber risk can actually be reduced and how much lateral movement prevention is realistic when facing today’s changing threat landscape.
How do network segmentation and a secure gateway fall short compared to intrusion detection systems or endpoint protection platforms?
Network segmentation and a secure gateway can reduce risks, but they aren’t perfect shields. Intrusion detection systems, endpoint protection platforms, and even VPN security can miss stealthy attacks. Without solid patch management and consistent OS security updates, attackers may still find cracks. In practice, layered defense creates complexity that slows incident response. Adding VLANs or advanced endpoint monitoring helps, but it can overwhelm teams with alerts. The truth is that perimeter security is not enough when attackers exploit user identity lifecycle management or weak privileged access controls.
Why can’t multifactor authentication, adaptive authentication, and single sign-on fully stop insider threats or identity and access management failures?
Even with multifactor authentication, adaptive authentication, and single sign-on, risks don’t disappear. Identity and access management can still break down when password management fails or when secrets management is mishandled. Privileged access management, endpoint privilege management, and even Zero Trust security can’t erase human mistakes. Security posture often weakens when user behavior analytics miss anomalies. The assume-breach mindset reminds us that response mechanisms matter as much as preventive controls. Insider threat protection remains difficult because authentication factors alone can’t guarantee that trusted users won’t misuse access.
How does data protection like data encryption, SaaS security, and securing cloud workloads still face limits in digital transformation security?
Data encryption, SaaS security, and securing cloud workloads strengthen data protection, but they face limits in digital transformation security. Breach detection, threat containment, and breach containment still lag when systems lack proper logging and alerting. Data confidentiality also depends on sound application security and network defense, not just encryption. Cloud environments introduce supply chain attack prevention challenges, especially when network segregation or secure developer tools are overlooked. Even with advanced threat intelligence and behavioral analytics, cyber attack resistance weakens if response mechanisms and security monitoring fall behind.
Why do cybersecurity layers, security integration, and security orchestration sometimes create more problems than they solve in a cybersecurity strategy?
Cybersecurity layers, security integration, and security orchestration aim to boost a cybersecurity strategy, but they can introduce new issues. Redundant security controls often overlap, adding noise without better threat remediation. Security automation may miss subtle anomaly detection or malware prevention. Complex network security solutions make incident response slower instead of faster. Cyber risk increases if access control and preventive controls aren’t balanced with detection mechanisms. A layered defense with too many tools can weaken cyber attack resistance, leaving blind spots in network traffic analysis, insider threat protection, and risk mitigation.
References
- https://www.csis.org/analysis/cost-cybersecurity
- https://www.ponemon.org

