
Hackers don’t give up after the first try – they keep poking around until something breaks. A single security measure might work today, but tomorrow’s threats need more muscle. Our training bootcamp’s seen plenty of real-world examples where layered defenses made all the difference.[1] When developers stack multiple security controls together (authentication, encryption, input validation), they’re building a tougher target. The approach isn’t fancy – we just make sure there’s always a backup plan when one layer fails.
Key Takeaways
- Building security in layers stops attackers from finding that one weak spot
- Smart developers combine firewalls, authentication, input checks, and data protection
- Multiple defenses make attacks harder while helping catch problems early
What is Defense in Depth in Web Application Security?
Most developers learn the hard way that relying on a single security tool is asking for trouble. Our training bootcamp shows defense in depth examples in cyber security so developers see how layered defenses hold up under real attacks. When one defense fails (and trust us, they do), the next one’s ready to stop the attack cold.
Nobody wants to admit it, but web apps are never 100% secure. That’s why experienced teams put barriers everywhere they can – at the network edge, inside the application code, around sensitive data, and in system logs. We’ve seen this work time after time in real projects.
The beauty of layered security? It drives attackers crazy. They might slip past one checkpoint but run straight into three more. Students in our bootcamp learn to build these security checkpoints at every level, because that’s what keeps production apps safe in the real world. When something suspicious happens, the team spots it fast and stops it faster.
Key Layers Implemented in Defense in Depth for Web Applications
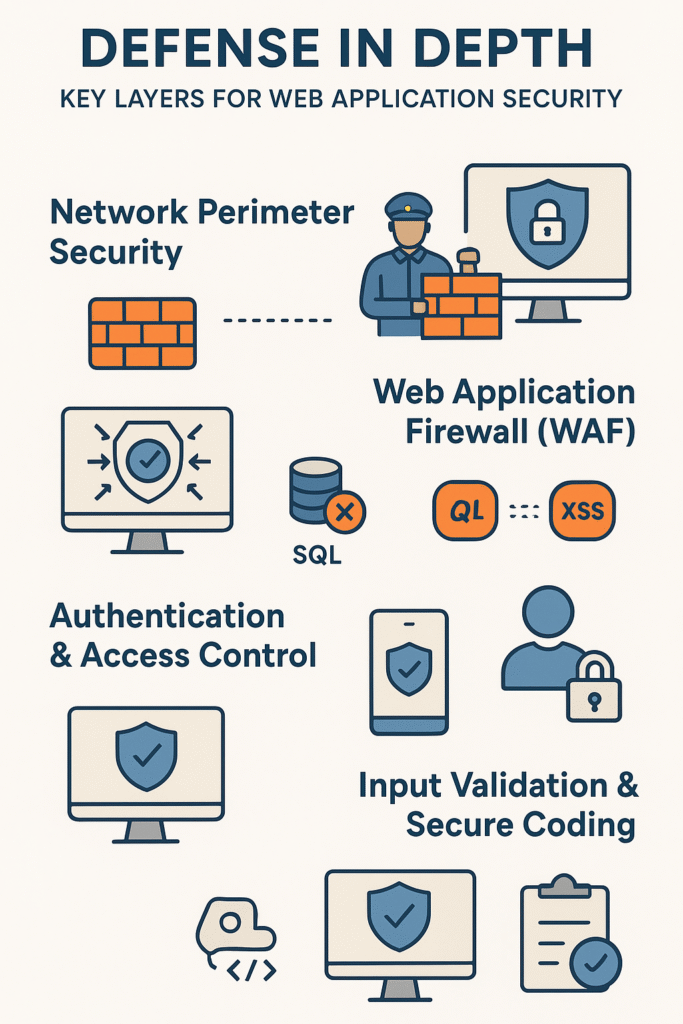
Most developers scratch their heads when starting with security layers. Here’s what actually works in the real world:
Network Perimeter Security: Firewalls and IDS/IPS
The first line of defense starts way before anyone reaches the app. Our bootcamp students learn to set up firewalls that act like bouncers at a club – checking IDs and turning away trouble before it starts. We’ve seen how intrusion detection systems catch the sneaky stuff too, jumping in automatically when something looks off. Not perfect, but it stops a lot of headaches before they start.
Web Application Firewall (WAF)
Getting closer to home, WAFs keep watch over web traffic. They’re pretty good at catching common attacks (SQL injection, XSS, that sort of thing) that somehow slip through. Most of our students are shocked when they see how many attacks their WAF blocks in just one day.[2]
Authentication and Access Control
Nobody gets in without a proper ID – that’s just common sense. Multi-factor authentication might annoy users a bit, but it works. We teach developers to lock down permissions tight, giving users only what they absolutely need. Seen too many breaches where hackers got in through accounts with way too much access.
Input Validation and Secure Coding
The code itself needs armor too. Smart developers check every piece of user input like they’re searching for contraband. Our training hits this hard – validate everything, encode output, and never trust user input. Yeah, it takes extra time, but beats explaining to the boss why the database just got dumped online.
Technical Controls and Practices for Defense in Depth in Web Applications
Time to dig into the nuts and bolts of what makes implementing defense in depth work.After training hundreds of developers, here’s what sticks:
Firewall as a Perimeter Layer
Setting up firewalls isn’t rocket science, but it needs attention to detail. We teach our students to think like security guards – watching traffic patterns, spotting the weird stuff. Hook up some intrusion detection, and now you’re cooking. The magic happens when these systems talk to each other, catching threats nobody saw coming.
Web Application Firewall (WAF)
WAFs are picky eaters – they inspect every HTTP request looking for trouble. Our students learn the hard way that configuration matters. Too tight, and legitimate users get locked out. Too loose, and hackers slip through. The sweet spot? Regular tweaks based on what’s actually hitting your servers.
Authentication Mechanisms
Passwords alone? That’s so 2010. Today’s apps need multi-factor auth, smart role management, and session controls that kick out idle users. We’ve cleaned up enough hacked systems to know – when someone breaks in, it’s usually through weak authentication. The fix isn’t complicated, just takes discipline.
Input Validation to Prevent Injection and Scripting Attacks
Every developer’s heard “never trust user input” – but seeing real attacks changes everything. Our bootcamp throws the nastiest injection attacks at student code until they get it right. Check everything that comes in, encode everything that goes out. Yeah, it’s extra work, but beats having your app show up on the news for the wrong reasons.
Data Protection and Monitoring Layers in Defense in Depth
Protecting data and continuously for threats are part of the core benefits of defense in depth that keep web applications resilient.
Encryption to Protect Data
Encryption safeguards data both while moving across networks and when stored. We use TLS/SSL protocols to secure data in transit, preventing interception. For data at rest, database encryption adds a critical shield, especially for sensitive information like user credentials and payment details.
Logging and Monitoring
Continuous monitoring of web traffic and application behavior helps detect anomalies quickly. Detailed logs capture who accessed what and when, which is invaluable for forensic analysis after an attack. In our operations, integrating logging with alerting systems allows us to react swiftly.
Endpoint Security
The servers hosting web applications need protection too. Antivirus software and endpoint detection and response (EDR) tools help identify malware before it causes harm. Regular patching is essential to fix vulnerabilities, something we schedule diligently to avoid easy exploits.
Incident Response Planning
Having a plan ready for incidents makes all the difference. Our team maintains clear procedures to contain breaches and recover systems. By linking monitoring alerts directly to incident response teams, we reduce downtime and damage.
Administrative and Physical Controls Complementing Technical Layers
Credit: Securely Built
Tech stuff’s great, but the human side of security keeps security pros up at night. After years of teaching developers, here’s what really matters.
Critical elements every security program needs:
- Regular staff training that doesn’t put people to sleep
- Written policies that people actually read and follow
- Physical security that works without driving everyone crazy
- Risk checks that catch problems before they blow up
Most breaches start with someone clicking something they shouldn’t. That’s why our bootcamp spends serious time on the human element. Security awareness can’t be some boring yearly video – it needs to stick. We run simulated phishing attacks, show real examples of social engineering, and make sure everyone knows what “normal” looks like. When developers understand why policies exist, they’re more likely to follow them.
Data centers need proper access controls and cameras watching the right spots. Our students learn this through real-world examples – like the time someone walked right past security with a fake badge. Regular risk assessments catch forgotten servers running old software or new cloud services nobody thought to secure. Yeah, compliance audits are a pain, but they often spot things everyone missed. And sometimes those boring reviews save your bacon when something goes wrong.
Conclusion
Look, there’s no magic bullet in web security, that’s the first lesson we drill into our students. Sure, firewalls catch some threats, authentication stops others, and input checks block the nasty stuff. But it’s the combination that really works. After training hundreds of developers, we’ve seen how layered security catches what single defenses miss. Doesn’t matter how good one lock is if the window’s wide open. That’s why defense in depth isn’t optional anymore, it’s just good sense.
Join our Secure Coding Bootcamp and learn how to build layered defenses that actually stand up to real-world attacks.
FAQ
How does applying defense in depth improve web application security?
Applying defense in depth means stacking multiple layers of web application security instead of relying on a single tool. For example, you can combine a web application firewall (WAF), intrusion detection system (IDS), and intrusion prevention system (IPS) with strong authentication and authorization. Add secure coding practices like input validation, output encoding, and session management, and you make it harder for attackers to break in. Even if one layer fails, another layer, such as encryption, patch management, or endpoint security, can stop the problem before it causes serious damage.
What role does layered security play in stopping common web threats?
Layered security helps defend against attacks like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). A WAF can filter harmful requests, while secure coding practices cover input validation and output encoding. Authentication, role-based access control (RBAC), and least privilege keep user access controlled. Extra steps like multi-factor authentication (MFA), encryption with TLS or SSL, and session management add strength. When you combine intrusion detection, incident response, and vulnerability management, you reduce the chances of denial of service (DoS), distributed denial of service (DDoS), or other attacks disrupting your webApp.
Why is network perimeter security not enough on its own?
Network perimeter security helps block unwanted traffic, but today’s attacks target far more than the edges. Hackers exploit weak authentication, poor session management, or missing SQL injection prevention. That’s why you need layered defenses, from encryption and patch management to endpoint security with antivirus or endpoint detection and response (EDR). Web application security adds a WAF, intrusion prevention system (IPS), and secure software development lifecycle practices like code review, code scanning, and fuzz testing. Together, these layers offer protection that perimeter defenses alone cannot deliver.
How can developers build safer webapps using secure coding practices?
Developers can apply secure coding practices by focusing on input validation, output encoding, and session management to lower risk. Adding brute force protection, rate limiting, and API security controls like API authentication, API authorization, and API encryption helps protect endpoints. Using dynamic application security testing (DAST), static application security testing (SAST), and fuzz testing within a secure software development lifecycle can catch issues early. Version control, code review, and patch vulnerability fixes also matter. Paired with encryption, TLS/SSL configuration, and least privilege, these practices make coding a key part of defense in depth.
How do organizations prepare for incidents even with strong defenses?
Even with encryption, endpoint security, and zero trust architecture in place, incidents still happen. That’s why incident response, incident management, and business continuity planning are critical. Security monitoring, security logging, and threat intelligence enable faster detection. Security awareness training helps teams recognize phishing detection and unusual behavior. User behavior analytics, privileged access management, and identity and access management (IAM) keep access under control. Regular penetration testing, vulnerability management, and risk assessment provide early warnings. These steps make sure a breach doesn’t turn into a crisis.
References
- https://www.cyber.nj.gov/guidance-and-best-practices/account-security/multi-factor-authentication/multi-factor-authentication-mfa-a-critical-step-for-account-security
- https://www.ibm.com/reports/threat-intelligence

