
Nobody wants to gamble with security. During our time teaching developers at the bootcamp, we’ve seen firsthand how single-point defenses crumble. Security teams know the drill – layer those controls, stack those defenses. Security teams know the drill, layer those controls, stack those defenses.
This defense in depth security strategy means backup systems catch what slips through. When attackers breach one layer, the others kick in to slow them down, buying precious response time. Most attacks don’t succeed through brute force, they succeed through persistence against weak spots.
Key Takeaways
- Layer your defenses – one wall won’t cut it
- Catch threats early before they spread
- Keep your crown jewels behind extra security
How Does Defense in Depth Enhance Security Through Layering?
Security’s like an onion – you need layers. At our bootcamp, we drill this into every developer’s head: stack those defenses high and deep. Think firewalls watching the front door, IDS systems sniffing out the weird stuff, encrypted data that’s useless if stolen, and locked-down endpoints. Each layer’s another headache for attackers.
The real magic happens when these layers work together. Last month during training, our firewall caught someone poking around the network edge. They got creative and slipped past, but that’s when our IDS lit up like a Christmas tree. Even if they’d grabbed some data, good luck reading it through our encryption. One defense might fail, but the others pick up the slack.
You can’t hack what you can’t reach. Smart teams (our graduates included) don’t just throw up random barriers – they build strategic layers that force attackers to work for every inch. The more hoops they jump through, the more likely they’ll trip an alarm or give up entirely.[1]
Think about crossing a river – one bridge might break, but three different routes mean you’ll probably make it across. That’s why the most secure systems we’ve built always have overlapping defenses.
How Does Defense in Depth Mitigate Risks and Control Damage?
Nobody likes talking about breaches until one happens. Teaching secure development at the bootcamp has shown us that containment matters more than prevention. When (not if) attackers slip through that first defense, other layers jump in to slow them down. It’s like having backup goalies – if one misses, others are ready to block.
Here are a few defense in depth examples in cyber that we run in training:
- Malware sneaks past the firewall (they always find a way)
- EDR tools spot the infected machine acting weird
- System automatically quarantines that device
- Security team gets time to investigate before things spread
We’ve seen this play out dozens of times in real incidents. Last quarter, a client’s network caught some nasty ransomware. Their first line crumbled, but because they’d layered their defenses (like we taught them), the malware couldn’t jump between systems. The damage stayed in one department instead of taking down the whole company.
This approach means security teams don’t need superhuman response times. Multiple alerts from different layers give plenty of warning signs. Sometimes it’s the difference between a minor headache and a major breach that makes the evening news.
How Defense in Depth Makes Detection and Response Better
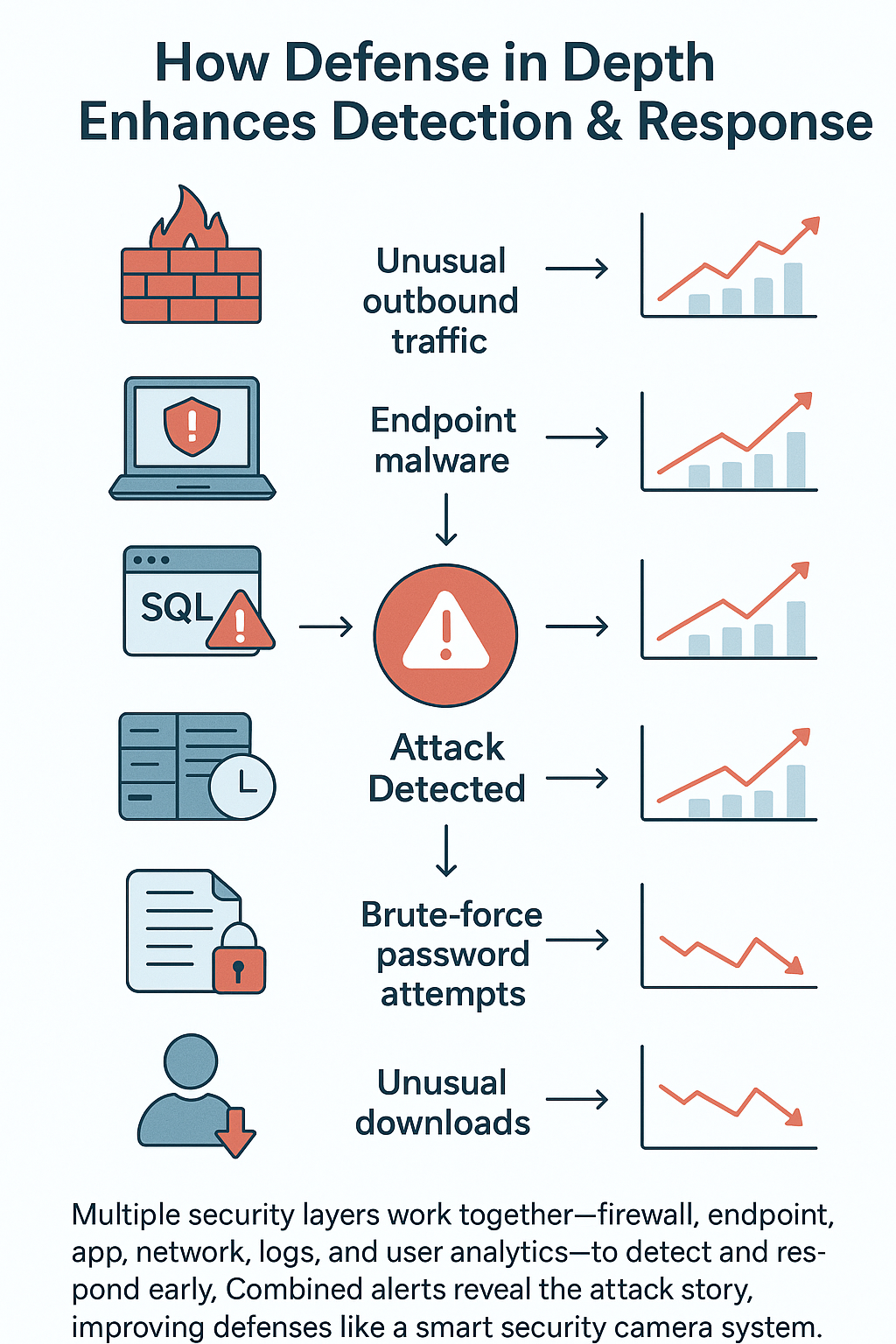
Network security isn’t rocket science – it’s more like playing detective with a bunch of different informants. Each security layer adds another set of eyes on the problem, watching things a bit differently than the others.
Sure, the firewall’s keeping track of weird connections, but that’s just the start. There’s endpoint protection checking if Bob from accounting’s laptop starts acting possessed at 3 AM, and application security making sure nobody’s trying any funny business with the code.
The tricky part comes from years of running security operations – attacks don’t follow some neat playbook anymore. Sometimes it’s the VP who clicked on that cryptocurrency scam, other times it’s some flaw that’s been sitting in the code since 2019. Here’s what usually catches the bad guys:
- Network monitoring (spots those midnight data transfers to Russia)
- System logs (shows when someone’s trying every password combo in the book)
- Application security (catches those sneaky SQL injection attempts)
- User behavior analytics (notices when Karen in HR suddenly starts downloading engineering files)
When different security tools start raising red flags about the same thing, that’s when things get interesting. Like when the firewall spots weird outbound traffic, right as antivirus catches a strange process, and the email filter blocks a sketchy attachment – all from the same workstation. That’s not coincidence, that’s an attack in progress.
How Does Defense in Depth Provide Protection Against Diverse Threats?
Teaching developers about security feels like running a zoo sometimes – every threat’s a different animal. During our bootcamp sessions, we’ve learned there’s no silver bullet for security. Each layer needs its own special focus, like training different muscles for a complete workout.
The basics that keep our students’ code safe:
- Endpoint protection catches nasty malware before it spreads
- IAM tools watch for employees doing sketchy stuff
- Network segments keep problems contained
- Physical security (yes, actual locks) because not all threats come through the internet
But here’s what really matters – these layers work together like a well-oiled machine. Take last week’s training scenario: a phishing email slipped through spam filters, but endpoint security caught the malware download. Even if it had run, network segmentation would’ve kept it from reaching the crown jewels.
Real-world attacks don’t play by the rules. Sometimes it’s a crafty piece of code, other times it’s someone walking out with a USB drive full of secrets. That’s why our approach covers everything from keyboard to server room. Physical security might seem old school, but those card readers and security cameras are just as important as fancy firewalls.
How Does Defense in Depth Support Compliance and Best Practices?
Credit: SecuLore
Defense in depth isn’t just about blocking hackers, it also helps us play by the rules. Big laws and standards, like PCI DSS for payments or HIPAA for health, all say the same thing: layer your defenses. NIST, a well-known security guide, also points to this approach.
By using layers, we’re not only following the rules but also showing we take security seriously. It’s like practicing good habits, not just checking off a list. That builds trust and makes our defenses stronger.
When we follow this path, audits run smoother. Inspectors see we’ve built security the right way, not just the fast way. And that means fewer fines, less stress, and no damage to our reputation.
How Does Defense in Depth Offer Flexibility and Adaptability?
One of the strengths of defense in depth is its modular design. We can adjust or add layers as new vulnerabilities and threats emerge. This kind of flexibility means our defenses grow and change with the threat landscape, instead of getting old and useless.
With modular security design, each layer can be fixed or improved over time. That way, it can adapt to new weaknesses and dangers as they show up. One of the strengths of defense in depth is its modular design, which makes implementing defense in depth more practical as new threats emerge.
We keep our defenses sharp by fixing patches, pulling in new threat intelligence, and using adaptive authentication to stop the latest tricks attackers throw at us.
As the threat landscape changes, our defenses grow stronger too. That makes it far tougher for attackers, even the ones using advanced persistent threats or surprise zero-day attacks, to break their way in.
How Does Defense in Depth Protect Critical Assets?
Critical assets, customer data, intellectual property, financial systems, need special care. Defense in depth achieves this through asset isolation and focused monitoring.
We use network segmentation like walls inside a castle, splitting up the sensitive rooms from the busy hallways. This kind of asset isolation makes sure only the right people can get near the important things. It lowers the chance that private data or key systems will ever be exposed.[2]
We also keep watch over the critical points, the doors and gates that matter most. With sharp eyes on these high-value spots, it’s much tougher for anyone to sneak in or grab information without being caught. being noticed.
Together, these layers act like guards and barriers working side by side. They make it far less likely that attackers can slip through, reach the treasure, or sneak it out unseen.
How Does Defense in Depth Reduce Single Point of Failure Risks?
Relying on one security control is risky because if it fails, attackers get a free pass. We learned this the hard way early in our cybersecurity efforts. Defense in depth spreads controls across multiple layers so that failure in one doesn’t mean total compromise.
Think of distributed security controls like a neighborhood with lots of fences and locked doors. Each lock is its own independent protection, and even if one is broken, the others keep watch. This means protection never stops, even when a single barrier fails. If a firewall rule slips up, then endpoint security or even user behavior tracking can still catch something strange before it gets worse.
Now, the idea of resilience is about making the system tough. Adding redundant layers is like stacking shields, one behind the other. That extra weight makes the whole setup stronger, less shaky, and harder for attackers to smash through. With this kind of backup in place, the chance of a total breakdown drops, and the system stays steady even when attacks keep coming.
Final Thoughts
Look, layered security isn’t just about throwing more tools at the problem. Think of it like building a medieval castle, moat, walls, guards, the works. Each piece matters. The thing about cyber defense is you can’t just set it and forget it.
These days, hackers keep getting sneakier. That’s why we stack our defenses like layers of a shield. If one layer slows them down, the next one is waiting. All those layers together give us extra time to spot the bad guys and stop them before they get to anything that really matters. Start with the basics, then build up slowly. That’s what works.
Ready to put this into practice? Join our Secure Coding Bootcamp and start building real defense in depth skills today.
FAQ
How does defense in depth improve a cybersecurity strategy with multiple security layers?
Defense in depth works by building a layered security approach where multiple security layers, like network security, endpoint security, and application security, back each other up. This layered defense model helps IT system protection by slowing attackers down and giving defenders time to spot issues. By adding tools such as an intrusion detection system, firewall, and antivirus software, organizations can strengthen their cybersecurity strategy. The benefit comes from how each layer supports the others, which makes the security posture stronger and improves cyber threat mitigation even against advanced persistent threats.
Why are layered security and zero trust security important for risk mitigation and security compliance?
Layered security and zero trust security help reduce risks by making sure no single point of failure exists in a system. These approaches support security compliance by meeting regulatory requirements and following cybersecurity best practices. When combined with security controls such as identity and access management, multi-factor authentication, and privileged access management, organizations create a safer environment for sensitive data. Risk mitigation is stronger because the layered defense model includes threat detection, anomaly detection, and user behavior analytics to protect against insider threats and strengthen security with advanced tools.
What role do data encryption and access control play in data protection and cyberattack response?
Data encryption and access control are critical for keeping data protection strong. By securing information both in motion and at rest, encryption helps prevent data loss. Access control systems like identity and access management and endpoint privilege management limit who can see or use certain data, which supports cyberattack response and security breach prevention. When combined with security monitoring, logging and alerting, and anomaly detection, these measures improve data integrity protection and cyber defense layers. They also help organizations follow security policies and maintain security framework standards.
How do endpoint security tools like antivirus software and patch management strengthen security resilience?
Endpoint security tools are front-line defenders for cybersecurity resilience. Antivirus software, patch management, and endpoint detection and response work together to stop malware and provide ransomware defense. Security awareness and operational security also help users spot threats early. With security hardening and secure developer tools, organizations reduce attack surfaces and improve IT system protection. Security incident response becomes faster when secure gateways and adaptive authentication are in place. Together, these endpoint security measures give stronger cyber attack prevention and insider threat mitigation within comprehensive cybersecurity.
Why do network security controls like firewall and virtual private network matter for cyber defense layers?
Network security relies on firewalls, virtual private networks, and network segmentation to build cyber defense layers that keep intruders out. These tools work alongside intrusion prevention systems and intrusion detection systems to identify malicious activity before damage occurs. Network traffic analysis and behavioral analytics make security monitoring stronger and support threat suppression. By adding perimeter security, network edge protection, and internal network security, organizations reduce vulnerabilities. These security architecture design steps provide layered defense model coverage, help with vulnerability management, and boost overall cybersecurity framework and resilience.
References
- https://en.wikipedia.org/wiki/Computer_security
- https://www.helpnetsecurity.com/2021/12/16/implementing-network-segmentation/

